Username or Email Address
Remember Me Forgot Password?
Get New Password


Case Study: Library Management System
- October 18, 2023

The Library Management System is a simple Python program that emulates the core functionalities of a library, including adding books, displaying the book catalog, lending books, and returning books. This case study presents a straightforward implementation of a library management system for educational and organizational purposes.
Objectives:
- To create a text-based library management system for managing a collection of books.
- To allow users to add books to the library catalog.
- To provide users with a list of available books.
- To enable users to borrow and return books.
Implementation:
The Library Management System consists of the following components:
- Library Class: The Library class serves as the core of the system and contains methods for adding books, displaying the catalog, lending books, and returning books. It uses a dictionary to store book information.
- Main Function: The main function initiates the library system and presents a menu to users for performing actions like adding books, displaying books, lending books, and returning books.

Case Study Steps:
- Launch the Library Management System.
- The system displays a welcome message, and the main menu is presented to the user.
- Add a Book (Option 1): Users can add books to the library catalog by providing the book’s title and author.
- Display Books (Option 2): Users can view the list of books in the library catalog.
- Lend a Book (Option 3): Users can borrow a book by specifying the title and their name. The system checks for book availability and records the borrower’s name.
- Return a Book (Option 4): Users can return a borrowed book by providing the book’s title and their name. The system verifies the book’s status and updates it.
- Exit (Option 0): Users can exit the library management system.
- The system processes user inputs, executes the chosen action, and provides appropriate feedback.
Conclusion:
The Library Management System presented in this case study offers a simplified way to manage a library’s book catalog. It is suitable for educational purposes and provides the core features necessary for a basic library system, such as adding, displaying, lending, and returning books. Further development could include features like due dates, user authentication, and storing book information in a database for a more comprehensive library management system.
Leave a Reply Cancel Reply
Your email address will not be published. Required fields are marked *
Name *
Email *
Add Comment *
Save my name, email, and website in this browser for the next time I comment.
Post Comment
Trending now


Home » Uncategorized » Designing a Robust Library Management System: From Concept to Reality
Designing a Robust Library Management System: From Concept to Reality
- Posted on September 15, 2023
- / Under Uncategorized
Introduction
In an era marked by the digital revolution, libraries continue to play a pivotal role in disseminating knowledge and fostering a love for literature. To ensure the efficient functioning of these sanctuaries of learning, a well-structured Library Management System (LMS) is indispensable. In our case study, we embark on a journey to design a comprehensive LMS, taking it from conceptualization to implementation. Our goal is to demonstrate the step-by-step process of transforming a high-level concept into a finely tuned database system, ready to serve the needs of a bustling library.
From Class Modeling to Database Modeling
Let’s walk through the process of developing a database schema from a class diagram to a conceptual ERD (Entity-Relationship Diagram), logical ERD, physical ERD, and the normalization steps. We’ll use a hypothetical case study for a library management system.
Case Study: Library Management System
Step 1: Class Diagram to Conceptual ERD
In the initial phase, we start with a class diagram that represents the high-level structure of our system. Here’s a simplified class diagram for our library management system:
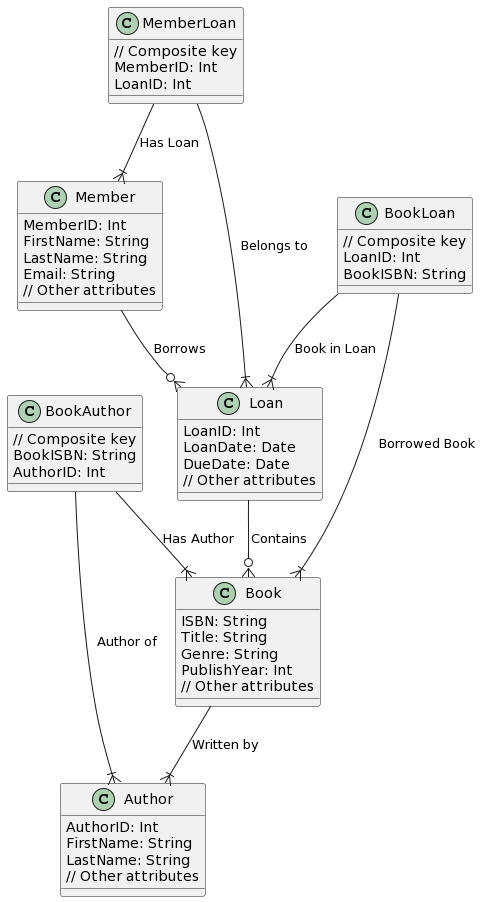
From this class diagram, we can create a conceptual ERD:
Conceptual ERD:
- A Book can be written by one or more Authors.
- A Member can borrow zero or more Books.
- A Book can be borrowed by zero or one Member (at a time).
Step 2: Conceptual ERD to Logical ERD
In this step, we refine the conceptual ERD by adding attributes and specifying cardinalities:
Logical ERD:
- Book (ISBN, Title, Genre, PublishYear, …)
- Author (AuthorID, FirstName, LastName, …)
- Member (MemberID, FirstName, LastName, Email, …)
- Loan (LoanID, LoanDate, DueDate, …)
- Cardinality: Many-to-Many
- Cardinality: One-to-Many (A member can have multiple loans)
- Cardinality: Many-to-Many (A loan can have multiple books)
Step 3: Logical ERD to Physical ERD
Now, we convert the logical ERD into a physical ERD by defining data types, primary keys, foreign keys, and any other constraints specific to the chosen database system (e.g., PostgreSQL, MySQL).
Physical ERD:
- Book (ISBN [PK], Title, Genre, PublishYear, …)
- Author (AuthorID [PK], FirstName, LastName, …)
- Member (MemberID [PK], FirstName, LastName, Email, …)
- Loan (LoanID [PK], LoanDate, DueDate, …)
- BookAuthor (BookISBN [FK], AuthorID [FK])
- MemberLoan (MemberID [FK], LoanID [FK])
- BookLoan (LoanID [FK], BookISBN [FK])
Step 4: Normalization
In this step, we ensure that the database schema is normalized to reduce data redundancy and improve data integrity. The tables are already in a reasonable state of normalization in the physical ERD.
Step 5: Database Schema Development
Finally, we implement the database schema in our chosen database system using SQL or a database modeling tool. Here’s an example SQL script to create the tables:
CREATE TABLE Book ( ISBN VARCHAR(13) PRIMARY KEY, Title VARCHAR(255), Genre VARCHAR(50), PublishYear INT, — Other attributes );
CREATE TABLE Author ( AuthorID INT PRIMARY KEY, FirstName VARCHAR(50), LastName VARCHAR(50), — Other attributes );
CREATE TABLE Member ( MemberID INT PRIMARY KEY, FirstName VARCHAR(50), LastName VARCHAR(50), Email VARCHAR(255), — Other attributes );
CREATE TABLE Loan ( LoanID INT PRIMARY KEY, LoanDate DATE, DueDate DATE, — Other attributes );
CREATE TABLE BookAuthor ( BookISBN VARCHAR(13), AuthorID INT, FOREIGN KEY (BookISBN) REFERENCES Book(ISBN), FOREIGN KEY (AuthorID) REFERENCES Author(AuthorID) );
CREATE TABLE MemberLoan ( MemberID INT, LoanID INT, FOREIGN KEY (MemberID) REFERENCES Member(MemberID), FOREIGN KEY (LoanID) REFERENCES Loan(LoanID) );
CREATE TABLE BookLoan ( LoanID INT, BookISBN VARCHAR(13), FOREIGN KEY (LoanID) REFERENCES Loan(LoanID), FOREIGN KEY (BookISBN) REFERENCES Book(ISBN) );
This script defines the tables, primary keys, foreign keys, and their relationships as specified in the physical ERD.
In conclusion, this case study illustrates the process of designing and implementing a database schema for a library management system, starting from a class diagram and progressing through conceptual, logical, and physical ERDs, normalization, and finally, the database schema development.
In this case study, we have meticulously outlined the development of a Library Management System (LMS) using a holistic approach that covers every phase of the process. Beginning with a high-level class diagram, we progress through the creation of a conceptual Entity-Relationship Diagram (ERD), a logical ERD, and finally, a physical ERD with a fully normalized database schema.
We’ve explored the intricacies of each stage, illustrating how the design evolves and adapts to meet the real-world requirements of a library management system. The resulting database schema is robust, efficient, and capable of handling the complexities of tracking books, authors, members, and loans in a library setting.
This case study serves as a comprehensive guide for anyone involved in the design and development of database systems. It highlights the importance of starting with a solid conceptual foundation, refining it logically, and meticulously translating it into a physical database schema. The ultimate goal is to create a system that not only meets the needs of the organization but also maintains data integrity and reduces redundancy.
In conclusion, “Designing a Robust Library Management System: From Concept to Reality” provides valuable insights into the world of database design and development, offering a clear roadmap for transforming an abstract idea into a practical, efficient, and fully functional database system.
Leave a Comment Cancel reply
You must be logged in to post a comment.

- Visual Paradigm Online
- Request Help
- Customer Service
- Community Circle
- Demo Videos
- Visual Paradigm
- YouTube Channel
- Academic Partnership
Library Management System (LMS) Database: Case Study Analysis
95 Pages Posted: 9 Oct 2022
GPDCM Jayasekara
University of Plymouth; NSBM Green University Town
Date Written: September 7, 2022
A library service wants to create a database to store details of its libraries, books, and borrowers. Details include the following: A book has a unique ISBN number, a title and one or more authors. The library service may own several copies of a given book, each of which is in one of the service’s libraries. A given library contains many books, and to distinguish different copies of the same book a library assigns a different copy-number to each of its copies of a given book; the price that was paid for each copy is also recorded. Every library has a unique name and is either a main library or a branch library. A main library may have zero or more branch libraries and every branch library is a branch of exactly one main library. A borrower has a name and a unique ID code. A borrower can have many books on loan, but each copy of a book can only be on loan to one borrower. A borrower could borrow the same book on several occasions, but it is assumed that each such loan will take place on a different date. The main operation and the details are included here & the developers can suggest some new options and services for the above system. To implement the new and advanced options you can assume any database related structures and constrains.
Keywords: Library, DB, SQL, ER, Database, System
Suggested Citation: Suggested Citation
Chamoth Madushan Jayasekara (Contact Author)
University of plymouth ( email ).
Plymouth United Kingdom 0701245270 (Phone)
NSBM Green University Town ( email )
Pitipana - Thalagala Rd Homagama Sri Lanka 0701245270 (Phone)
Do you have a job opening that you would like to promote on SSRN?
Paper statistics, related ejournals, data science, data analytics & informatics ejournal.
Subscribe to this fee journal for more curated articles on this topic
Information Curation, Management & Organization eJournal
Libraries & information technology ejournal.
- Computer Science
- Information Science
- Library Management
Library Management System (LMS) Database: Case Study Analysis
- January 2022
- SSRN Electronic Journal

- University of Plymouth
Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
UML diagrams for library management system
- Case Studies »
- UML diagrams for library management... »
Library Management System
Read the following documents/reports to understand the problem statement, requirements and other necessary things related to the Library Management Application: Doc1 , Doc2 , Doc3 , Doc4 , Doc5 , Doc6
- 1 Use case diagram
- 2 Class diagram
- 3 Sequence diagram
- 4 Collaboration diagram
- 5 Statechart diagram
- 6 Activity diagram
- 7 Component diagram
- 8 Deployment diagram
Use case diagram
Email address:
Class diagram
Sequence diagram, collaboration diagram, statechart diagram, activity diagram, component diagram, deployment diagram.
How useful was this post?
Click on a star to rate it!
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.
Related Posts
- UML diagrams for ATM application
- Introduction to Rational Rose
- UML diagrams for railway reservation system
- UML diagrams for document editor
- UML Diagrams for Online Banking System
- UML Diagrams for Online Book Shop
- Use Case Diagrams
- Object diagrams
- Overview of UML
- « Previous Post
- Next Post »
37 Comments
You can follow any responses to this entry through the RSS 2.0 feed.
- « Older Comments
This is all diagram super thanks for the content
yaaaa for for mind blocking it is very helpful
Hello startertutorials.com webmaster, Your posts are always a great source of knowledge.
May I ask if you can provide the corresponding PlantUML for scientific research
Dear startertutorials.com webmaster, Your posts are always informative.
from where could i find UML diagrams on the image search engine???

You have to Google for that. I don’t think they will be available. Better search for search engine diagrams and modify them for image search engine.
Thank You very very much for the diagrams. They were very helpful and up to the mark.
You are welcome 🙂
very usefull information
Thanks for the diagrams. They are very helpful.
You are welcome Hassaan
yes extremely helpful information
easy understood for diagram
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
design-a-library-management-system.md
Latest commit, file metadata and controls, design a library management system, let's design a library management system.
We'll cover the following:
System Requirements
Use case diagram, class diagram, activity diagrams.
A Library Management System is a software built to handle the primary housekeeping functions of a library. Libraries rely on library management systems to manage asset collections as well as relationships with their members. Library management systems help libraries keep track of the books and their checkouts, as well as members’ subscriptions and profiles.
Library management systems also involve maintaining the database for entering new books and recording books that have been borrowed with their respective due dates.

Always clarify requirements at the beginning of the interview. Be sure to ask questions to find the exact scope of the system that the interviewer has in mind.
We will focus on the following set of requirements while designing the Library Management System:
- Any library member should be able to search books by their title, author, subject category as well by the publication date.
- Each book will have a unique identification number and other details including a rack number which will help to physically locate the book.
- There could be more than one copy of a book, and library members should be able to check-out and reserve any copy. We will call each copy of a book, a book item.
- The system should be able to retrieve information like who took a particular book or what are the books checked-out by a specific library member.
- There should be a maximum limit (5) on how many books a member can check-out.
- There should be a maximum limit (10) on how many days a member can keep a book.
- The system should be able to collect fines for books returned after the due date.
- Members should be able to reserve books that are not currently available.
- The system should be able to send notifications whenever the reserved books become available, as well as when the book is not returned within the due date.
- Each book and member card will have a unique barcode. The system will be able to read barcodes from books and members’ library cards.
We have three main actors in our system:
- Librarian: Mainly responsible for adding and modifying books, book items, and users. The Librarian can also issue, reserve, and return book items.
- Member: All members can search the catalog, as well as check-out, reserve, renew, and return a book.
- System: Mainly responsible for sending notifications for overdue books, canceled reservations, etc.
Here are the top use cases of the Library Management System:
- Add/Remove/Edit book: To add, remove or modify a book or book item.
- Search catalog: To search books by title, author, subject or publication date.
- Register new account/cancel membership: To add a new member or cancel the membership of an existing member.
- Check-out book: To borrow a book from the library.
- Reserve book: To reserve a book which is not currently available.
- Renew a book: To reborrow an already checked-out book.
- Return a book: To return a book to the library which was issued to a member.
Here is the use case diagram of our Library Management System:

Here are the main classes of our Library Management System:
- Library: The central part of the organization for which this software has been designed. It has attributes like ‘Name’ to distinguish it from any other libraries and ‘Address’ to describe its location.
- Book: The basic building block of the system. Every book will have ISBN, Title, Subject, Publishers, etc.
- BookItem: Any book can have multiple copies, each copy will be considered a book item in our system. Each book item will have a unique barcode.
- Account: We will have two types of accounts in the system, one will be a general member, and the other will be a librarian.
- LibraryCard: Each library user will be issued a library card, which will be used to identify users while issuing or returning books.
- BookReservation: Responsible for managing reservations against book items.
- BookLending: Manage the checking-out of book items.
- Catalog: Catalogs contain list of books sorted on certain criteria. Our system will support searching through four catalogs: Title, Author, Subject, and Publish-date.
- Fine: This class will be responsible for calculating and collecting fines from library members.
- Author: This class will encapsulate a book author.
- Rack: Books will be placed on racks. Each rack will be identified by a rack number and will have a location identifier to describe the physical location of the rack in the library.
- Notification: This class will take care of sending notifications to library members.

Check-out a book: Any library member or librarian can perform this activity. Here are the set of steps to check-out a book:
Return a book: Any library member or librarian can perform this activity. The system will collect fines from members if they return books after the due date. Here are the steps for returning a book:

Renew a book: While renewing (re-issuing) a book, the system will check for fines and see if any other member has not reserved the same book, in that case the book item cannot be renewed. Here are the different steps for renewing a book:
Here is the code for the use cases mentioned above: 1) Check-out a book, 2) Return a book, and 3) Renew a book.
Note: This code only focuses on the design part of the use cases. Since you are not required to write a fully executable code in an interview, you can assume parts of the code to interact with the database, payment system, etc.
Enums and Constants: Here are the required enums, data types, and constants:
Code Snippet:
Account, Member, and Librarian: These classes represent various people that interact with our system:
BookReservation, BookLending, and Fine: These classes represent a book reservation, lending, and fine collection, respectively.
BookItem: Encapsulating a book item, this class will be responsible for processing the reservation, return, and renewal of a book item.
Search interface and Catalog: The Catalog class will implement the Search interface to facilitate searching of books.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
ER diagram of Library Management System
ER Diagram is known as Entity-Relationship Diagram, it is used to analyze the structure of the Database. It shows relationships between entities and their attributes. An ER Model provides a means of communication.
The Library Management System database keeps track of readers with the following considerations –
- The system keeps track of the staff with a single point authentication system comprising login Id and password.
- Staff maintains the book catalog with its ISBN, Book title, price(in INR), category(novel, general, story), edition, author Number and details.
- A publisher has publisher Id, Year when the book was published, and name of the book.
- Readers are registered with their user_id, email, name (first name, last name), Phone no (multiple entries allowed), communication address. The staff keeps track of readers.
- Readers can return/reserve books that stamps with issue date and return date. If not returned within the prescribed time period, it may have a due date too.
- Staff also generate reports that has readers id, registration no of report, book no and return/issue info.
Follow given link to build a Web application on Library Management System .
Below is the ER Diagram for Library Management System:
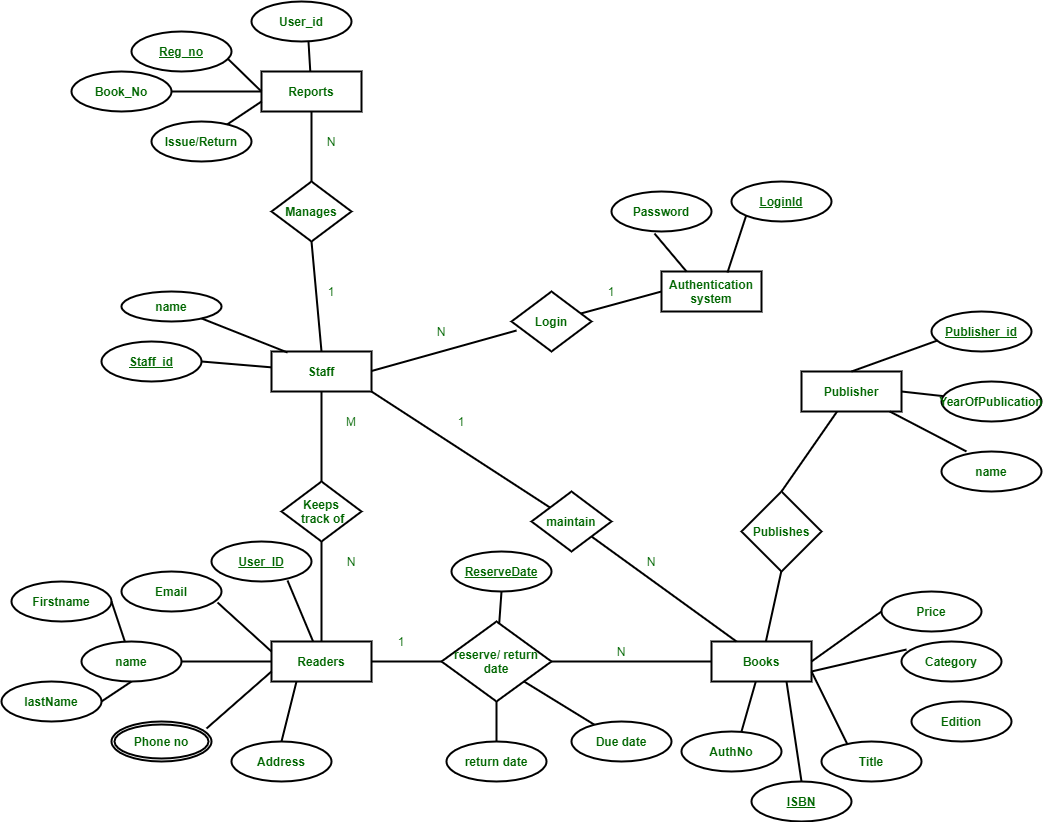
ER Diagram of Library Management System
This Library ER diagram illustrates key information about the Library, including entities such as staff, readers, books, publishers, reports, and authentication system. It allows for understanding the relationships between entities.
Entities and their Attributes –
- Book Entity : It has authno, isbn number, title, edition, category, price. ISBN is the Primary Key for Book Entity.
- Reader Entity : It has UserId, Email, address, phone no, name. Name is composite attribute of firstname and lastname. Phone no is multi valued attribute. UserId is the Primary Key for Readers entity.
- Publisher Entity : It has PublisherId, Year of publication, name. PublisherID is the Primary Key.
- Authentication System Entity : It has LoginId and password with LoginID as Primary Key.
- Reports Entity : It has UserId, Reg_no, Book_no, Issue/Return date. Reg_no is the Primary Key of reports entity.
- Staff Entity : It has name and staff_id with staff_id as Primary Key.
- Reserve/Return Relationship Set : It has three attributes: Reserve date, Due date, Return date.
Relationships between Entities –
- A reader can reserve N books but one book can be reserved by only one reader. The relationship 1:N.
- A publisher can publish many books but a book is published by only one publisher. The relationship 1:N.
- Staff keeps track of readers. The relationship is M:N.
- Staff maintains multiple reports. The relationship 1:N.
- Staff maintains multiple Books. The relationship 1:N.
- Authentication system provides login to multiple staffs. The relation is 1:N.
Please Login to comment...
Similar reads.
- DBMS-ER model
- Library Management System
- How to Get a Free SSL Certificate
- Best SSL Certificates Provider in India
- Elon Musk's xAI releases Grok-2 AI assistant
- What is OpenAI SearchGPT? How it works and How to Get it?
- Content Improvement League 2024: From Good To A Great Article
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Development of an Online Integrated Library Management Information System: Case Study “University of Gitwe”

Abstract— Automated Information System is a software application which often provides a major impact on the universities’ social and economic satisfaction as it consists of various aspects of the educational process, automates administrative and business activities and financial management, assists in decision-making by supporting information flow within the university. UG-LMIS (University of Gitwe Library Management Information System) is a library automation web application, a sub-module of the University of Gitwe’s Integrated Management Information System (UGIMIS), a web-based and an online application automating the whole university’s management. UG-LMIS was designed for the University of Gitwe to replace its existing manual record-keeping system. The new system controls the following information; student information, the catalog of books, track of issues and return of books, book searching and tracking, e-mail services, notice about book issue status, reporting capabilities, etc. These services are provided in an efficient and cost-effective manner with the goal of reducing the time and resources currently required for such tasks. UG- LMIS is a UMIS with great user interface designs, more performance enhancements, and many of enriched modules. It works for a big deal to bring value to the words ‘care’ and ‘comfort’ in this higher learning scenario. Besides, UG-LIMS is endowed with an advanced feature as it is a part of the university website, it can be accessed online anywhere at any time.
RELATED PAPERS
Natural Sciences Engineering and Technology Journal
shernahar tahil
Tilca Magnolia
BAMIDELE ITUNU ADEOLA
Namrata Rai
IAEME Publication
Abukari Aziz
Ellia Shafira
JOURNAL OF CRITICAL REVIEWS
Abdul Cader Mohamed Nafrees
International Journal of Scientific Research and Management
Teguh Herlambang
GAZARI OSMAN
Research Publish Journals
Iyortsuun Ngumimi Karen
Mahipal Sharma
ANALYSIS AND DESIGN OF LIBRARY MANAGEMENT SYSTEM
Chibuike I . Uzoagba
IOSR Journal of Computer Engineering
Ahmed Aliyu
PROFICIENT AUTOMATED LIBRARY MANAGEMENT SYSTEM(PALMS): A NEW MODEL FOR PUBLIC LIBRARIES OF PAKISTAN.
syed Mohammad Aqil Burney
International Journal of Scientific Research in Computer Science, Engineering and Information Technology
aniket bhoyar
DESIGN AND IMPLEMENTATION OF ONLINE MANAGEMENT INFORMATION SYSTEM (A STUDY OF COMPUTER SCIENCE DEPARTMENT, IMO STATE POLYTECHNIC, UMUAGWO
Raphael Onuoha
Alina Petrushka
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Case Studies
In 2014 and 2015, 10 public libraries from across the country took part in an extensive, 18-month training to learn the Harwood Institute's Turning Outward approach and put it to use in their communities.
Known as the Libraries Transforming Communities (LTC) Public Innovators Cohort , these libraries spent countless hours talking to community members, learning about their aspirations and concerns, and developing action plans to help their communities reach their full potential.
While the LTC initiative ended in December 2015, the libraries' work continues.
Read more about some of their stories in the following case studies. Download the complete set of LTC case studies [PDF].

Columbus (Wis.) Public Library: Innovative Solutions to Bridging Community Divisions [PDF]
For much of its history, Columbus was a rural community, but today it is quickly becoming a commuter town. Feeling the effects of this rapid change, the Columbus Public Library joined the Libraries Transforming Communities (LTC) initiative to learn how to add more value in the community beyond being a lender of books. Not only has Columbus Public Library built a stronger reputation as an institution that can help solve community challenges, but its director—a newcomer to the community—has become a stronger, more credible community leader in the process. Read more...

Hartford (Conn.) Public Library: Building on a Foundation of Success ... and Going Deep to Go Broad [PDF]
Hartford Public Library has a long history of community engagement. Through the Libraries Transforming Communities (LTC) initiative, the library has deepened that work. Using new training they received from The Harwood Institute through LTC, library staff members reached out to people in an underserved part of town where many people were disengaged. Based on what they learned from residents, library staff have undertaken efforts to improve relationships between residents and important institutions in the neighborhood. As a result, Hartford Public Library is playing an even stronger role as a critical asset to the community and trusted convener. Read more...
Los Angeles (Calif.) Public Library: Two Paths, One Destination: Culture Change in a Major Library System [PDF]
The Los Angeles Public Library, a massive library system with a service area of 3 9 million people, joined Libraries Transforming Communities (LTC) to generate new ways to deepen their connection to community and help people in communities address issues that mattered to them. The local LTC team started by focusing their work at the Van Nuys Branch, the idea being that if they could demonstrate the power and effectiveness of implementing their training through LTC, it would create a model that could be replicated in other areas of the system. The team saw initial success, but staff changes required them to reevaluate their plans. The team has been working on an alternative strategy that is built on training personnel at all levels across the system to plant the seeds of change and shift the institutional culture. Read more...

Red Hook (N.Y.) Public Library: One Small Win Creates Huge Ripples of Change [PDF]
The Libraries Transforming Communities (LTC) team from Red Hook Public Library used their training to engage residents in their small town. They learned people were frustrated that problems in their community—even obvious ones—often went unaddressed. The only stoplight in town, which didn’t work properly, was emblematic of their concerns and came up in many discussions with residents. The LTC team took action and brought officials together to figure out how to fix the problem. This seemingly small act sent a signal to the community that it was possible to make things happen, which has led to people stepping forward to work together on other issues that are keeping Red Hook from being more livable and connected. The library is playing a central role in convening these groups and has become a model for how other organizations want to work in the community. Read more...

Spokane County (Wash.) Library District: Building an Organizational Culture that Puts Community First [PDF]
Spokane County Library District joined the Libraries Transforming Communities (LTC) initiative in part to deepen the transformative work they had begun with a strategic planning process. Staff at the library used their training through LTC to focus not only on how they could build stronger relationships with the community and add more value as a library, but also how they could embed in the library a culture that put the community at the center of decision-making. During the two years of LTC, library staff members have become involved in a variety of initiatives to improve the community based on what they have learned from engaging residents. Additionally, library leaders have taken important steps to embed this new way of working into their talent management efforts. Read more...
Share This Page

Eastern African Journal of Humanities and Social Sciences Journal / Eastern African Journal of Humanities and Social Sciences / Vol. 3 No. 1 (2024) / Articles (function() { function async_load(){ var s = document.createElement('script'); s.type = 'text/javascript'; s.async = true; var theUrl = 'https://www.journalquality.info/journalquality/ratings/2408-www-ajol-info-eajhss'; s.src = theUrl + ( theUrl.indexOf("?") >= 0 ? "&" : "?") + 'ref=' + encodeURIComponent(window.location.href); var embedder = document.getElementById('jpps-embedder-ajol-eajhss'); embedder.parentNode.insertBefore(s, embedder); } if (window.attachEvent) window.attachEvent('onload', async_load); else window.addEventListener('load', async_load, false); })();
Article sidebar.

Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License .
Main Article Content
Analysis of change management facilitation for library system migration in academic libraries in kenya: a case of moi university, eldoret, janeth koskei.
Implementing organizational change is one of the most fundamental challenges for leaders and other stakeholders responsible for the organization's improvement and sustainability and academic libraries which exist in an unprecedented environment of change, managing change arising chiefly from internal and external technological factors is a major concern. Change management studies often propose the use of managerial practices to facilitate the management of organizational change processes. Despite increased development of change management best practices and empirical evidence showing the success of change initiatives, the literature estimates the failure rates of organizational change initiatives to be high and yet, there is no single-full proof strategy for organizational change management. Hence, more research is needed to model change processes, track the progress of major organizational change efforts, and document their effectiveness. This study set out to examine ways in which academic libraries can ease the transition from one library system to another, with emphasis on change management practices so as to provide insights and recommendations of a change approach that would ensure minimal disruption for all the stakeholders. Four key models including Kurt Lewin’s, McKinsey 7s, Kotter’s theory, and ADKAR change model framed the research. In this case study, a qualitative research design was adopted, and 37 staff were purposively selected from Moi University library to be interviewed. Semi-structured individual interviews were used to collect data and a thematic analysis technique was used in the analysis. The study established that change management in academic libraries is not only peripherally adopted but is also occasioned by failure to understand the dynamics of the intended change initiatives and inadequate dedicated resources and infrastructure for the library system migration. Implementing change more successfully during library system migration requires clear understanding of the triggers of change, resources required to deliver the change, the risks involved, and the people affected, strategies to implement change, and the expected outcomes. Well-defined change management processes and practices determine successful change implementation during a library system migration.
AJOL is a Non Profit Organisation that cannot function without donations. AJOL and the millions of African and international researchers who rely on our free services are deeply grateful for your contribution. AJOL is annually audited and was also independently assessed in 2019 by E&Y.
Your donation is guaranteed to directly contribute to Africans sharing their research output with a global readership.
- For annual AJOL Supporter contributions, please view our Supporters page.
Journal Identifiers

Cisco Talos Blog
How multiple vulnerabilities in microsoft apps for macos pave the way to stealing permissions.
- Cisco Talos has identified eight vulnerabilities in Microsoft applications for the macOS operating system.
- An adversary could exploit these vulnerabilities by injecting malicious libraries into Microsoft's applications to gain their entitlements and user-granted permissions.
- Permissions regulate whether an app can access resources such as the microphone, camera, folders, screen recording, user input and more. So if an adversary were to gain access to these, they could potentially leak sensitive information or, in the worst case, escalate privileges.
- This post also provides an overview of the macOS security model and illustrates how vulnerabilities within macOS applications could be exploited by adversaries to steal app permissions.
Cisco Talos recently conducted an analysis of macOS applications and the exploitability of the platform's permission-based security model, which centers on the Transparency, Consent, and Control (TCC) framework.
We identified eight vulnerabilities in various Microsoft applications for macOS, through which an attacker could bypass the operating system’s permission model by using existing app permissions without prompting the user for any additional verification. If successful, the adversary could gain any privileges already granted to the affected Microsoft applications. For example, the attacker could send emails from the user account without the user noticing, record audio clips, take pictures or record videos without any user interaction. Microsoft considers these issues low risk, and some of their applications, they claim, need to allow loading of unsigned libraries to support plugins and have declined to fix the issues. Here is the list of vulnerabilities Talos discovered with their Talos IDs and corresponding CVEs:
| Talos ID | CVE | App name |
|---|---|---|
| CVE-2024-42220 | Microsoft Outlook | |
| CVE-2024-42004 | Microsoft Teams (work or school) | |
| CVE-2024-39804 | Microsoft PowerPoint | |
| CVE-2024-41159 | Microsoft OneNote | |
| CVE-2024-43106 | Microsoft Excel | |
| CVE-2024-41165 | Microsoft Word | |
| CVE-2024-41145 | Microsoft Teams (work or school) WebView.app helper app | |
| CVE-2024-41138 | Microsoft Teams (work or school) com.microsoft.teams2.modulehost.app |
Before delving into the details of our findings, it is crucial to comprehend Apple's macOS permission security model. We will concentrate on the different components associated with the research campaign we executed and use the Microsoft vulnerabilities as a case study.
Understanding Apple's macOS permission security model
The security policy of most operating systems is, by default, based on Discretionary Access Control (DAC). This provides only minimal protection against exploited software or malware that runs with user or root privileges.
Apple's macOS is designed to safeguard users against malicious software and breaches of privacy. Beyond the standard DAC policy, access to certain resources is further secured by TCC, which governs how applications can access sensitive user data and system resources.
Below is an indicative, though not exhaustive, list of the capabilities of the consent-based permission model utilized by macOS.
TCC and data protection
TCC enforces a policy that requires applications to obtain explicit user consent before they can access protected resources such as contacts, calendars, photos and location, ensuring that users maintain direct control over their personal information and the accessibility of their data to applications.
TCC operates in conjunction with entitlements, which are a set of capabilities required for an app's functionality. Developers choose these entitlements from a selection provided by Apple, and although only a subset of all possible entitlements is available for general use, the most powerful ones are reserved exclusively for Apple's own applications and system binaries.
When an application with specific entitlements initially asks for the use of a specific capability, a permission pop-up appears.
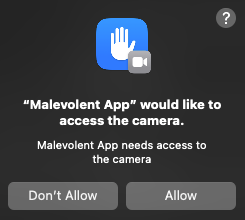
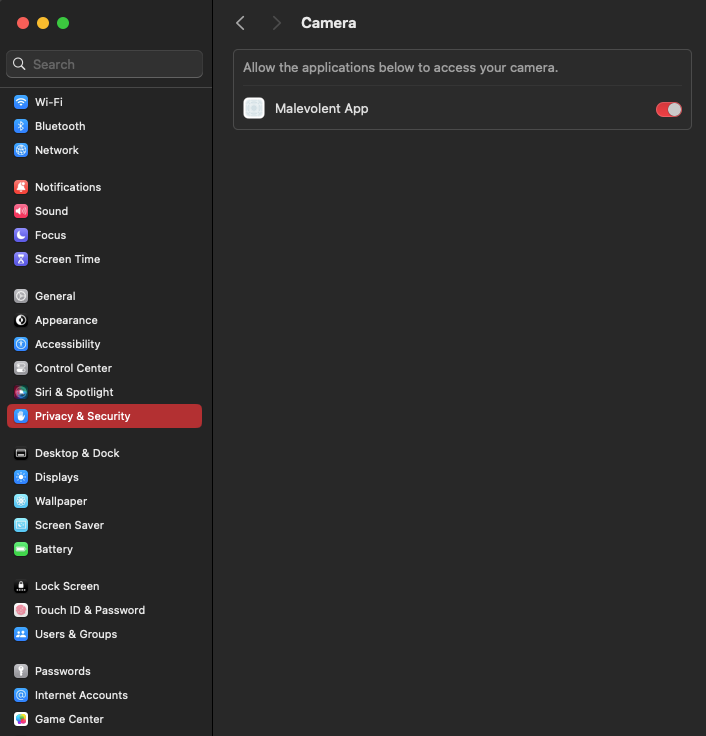
The image above shows an example of such a permission prompt: “Malevolent App” would like to access the camera. The user must decide whether to allow camera access or to deny it. This decision is then logged in the TCC database.
Once the user has made their choice, any future camera-related request from the “Malevolent App” will be governed by the recorded decision in the database. This system effectively enables users to control and be informed of the privacy-sensitive actions an application intends to carry out. The necessary user interaction is what enables users to prevent malicious applications from performing sensitive actions such as recording a video or taking pictures.
A user can later verify this permission within the “Privacy & Security” section of the macOS “System Settings.” There, a list of permissions can be found, including Camera, Microphone and Location Services.
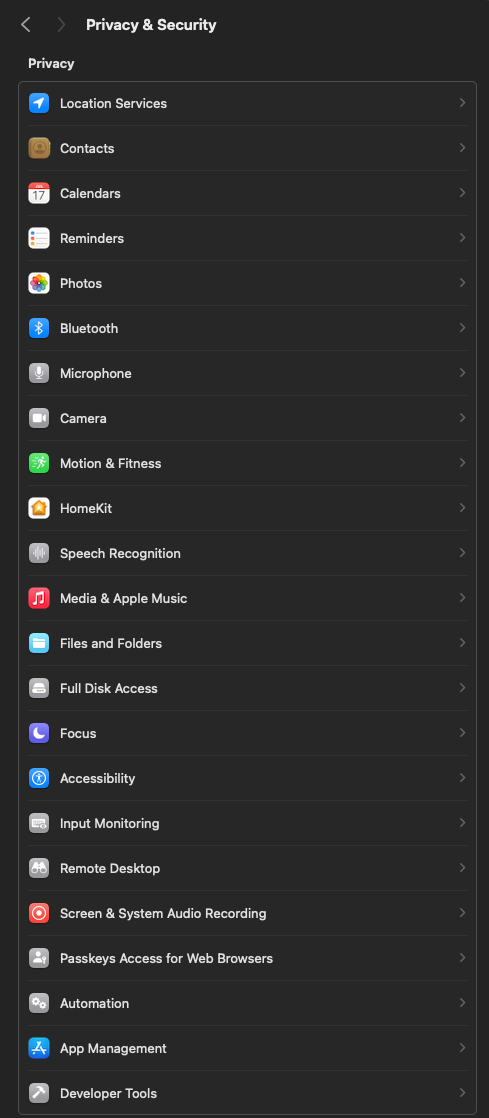
For example, following the user's decision regarding the previously mentioned pop-up, the Camera permission category under the “Privacy & Security” settings would show the “Malevolent app” listed among the applications that have been granted camera access. Here, the user also has the option to enable or disable permissions.

Code injection
Apple's macOS includes security measures to guard against code injection, a tactic often employed by malware, in which an attacker seeks to insert malicious code into legitimate processes to access protected resources.
To counter this risk, sandboxing is required for apps distributed through the Mac App Store. Sandboxing is designed to restrict access to resources and data; a sandboxed app can only access the resources it has explicitly requested through entitlements, and access to some of those resources is further protected by a user consent pop-up similar to the one previously shown.
For example, a sandboxed app will prompt the user for camera access only if it has the com.apple.security.device.camera entitlement set to true . If this entitlement is not present, the app won't be allowed camera access, and consequently, the permission pop-up won't even appear.
A closer look - reading the entitlements
You can obtain general information about an application or a binary's entitlements by running the following command:
For a notarized app—a designation indicating that the app has been checked by Apple's automated service for malicious components, even if it is not present in the App Store—it is required to enable hardened runtime.
While the sandbox is designed to limit potential impacts from a resource and data perspective, the hardened runtime is focused on making the application more resistant to exploitation. For instance, it includes by default a series of protections that aim to prevent various classes of attacks, particularly those related to code injection. Under the hardened runtime, applications performing higher-risk actions such as just-in-time (JIT) compilation or loading untrusted libraries must explicitly declare these capabilities through entitlements.
In fact, the hardened runtime enables library validation by default, which restricts the loading of libraries to those signed by the application's developer or Apple. If an application needs to disable this behavior, typically to import plug-ins, the developer must explicitly set the com.apple.security.cs.disable-library-validation entitlement to true.
The sandbox and the hardened runtime features can work together to provide enhanced protection. This approach can sometimes lead to what may appear like duplication of entitlements. For instance, consider a sandboxed application that also utilizes the hardened runtime and needs microphone access; in this case, you'll find two separate entitlements for the microphone – one for the sandbox and another for the hardened runtime:
A closer look - hardened runtime and library validation disabled
The output above shows the codesign output for the Microsoft Teams app at the time of our reporting. This app is sandboxed, as indicated by the com.apple.security.app-sandbox entitlement, and it has also hardened runtime enabled, evident from the flags=0x10000(runtime) in the line that begins with “CodeDirectory.” Despite the application being both sandboxed and utilizing the hardened runtime, the presence of the com.apple.security.cs.disable-library-validation entitlement indicates that the application is permitted to load third-party libraries without performing signature validation.
Library injection
The research campaign conducted is primarily focused on the ability to inject a library and exploit the permissions or entitlements of other applications. Library injection, also known as Dylib Hijacking in the context of macOS, is a technique whereby code is inserted into the running process of an application. macOS counters this threat with features such as hardened runtime, which reduce the likelihood of an attacker executing arbitrary code through the process of another app. However, should an attacker manage to inject a library into the process space of a running application, that library could use all the permissions already granted to the process, effectively operating on behalf of the application itself.
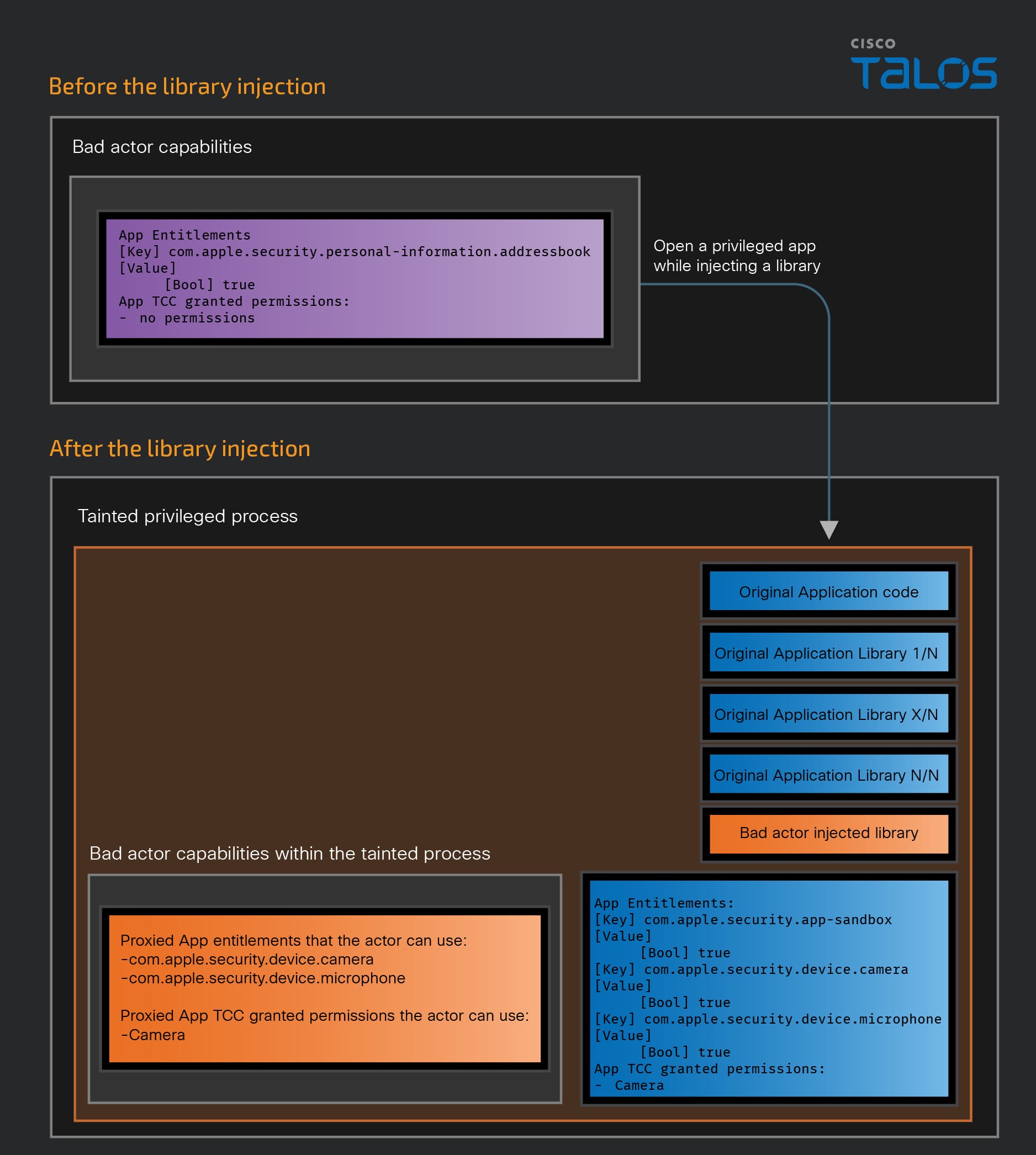
The graphics above illustrate what we have explained. Essentially, the bad actor possesses a set of capabilities on their own. By opening a more privileged app and injecting a malicious library, the bad actor gains the capabilities of the exploited application. The attacker then accesses these new capabilities through the exploited app.
Least privilege principle
Within the context of a sandboxed app or an app with hardened runtime enabled, even simply requesting permission to access one of the “privileged” resources (such as the camera, microphone, or location) requires the app to possess specific entitlements. Many entitlements are linked to resources, indicating the application's intention to use a particular resource.
The following snippet is an example of entitlements from the “Microsoft Teams” application. These three entitlements authorize the application to request permission to use the camera and the microphone:
Entitlements also facilitate the implementation of the principle of least privilege. Apps are only granted access to the resources that are necessary for their proper function, which reduces the potential impact of a compromised app. This approach narrows the attack surface and limits what an attacker can achieve if they manage to exploit an app. In addition, some entitlements enable various security features by default. If needed, developers must deliberately opt out of these features by adding specific entitlements, as was previously shown with the hardened runtime and the com.apple.security.cs.disable-library-validation entitlement.
The implications of Apple’s permission model
Apple's macOS features a layered security model, including TCC and entitlements, aimed at protecting users' privacy and maintaining system security. TCC manages application access to personal data and system privileges, requiring explicit user approval before granting access.
Despite its strength, the macOS security model isn't foolproof. Elevated permissions given to applications could be hijacked, potentially turning these apps into conduits for unauthorized access to sensitive resources.
The effectiveness of TCC depends on applications responsibly handling the permissions they receive . If a trusted application is compromised, it might be manipulated to abuse its permissions, allowing attackers to perform actions without user knowledge. For instance, if a video chat app with camera and microphone access is exploited, it could be forced to record without alerting the user.
This situation points to a key aspect: macOS trusts applications to self-police their permissions . A failure in this responsibility leads to a breach of the entire permission model, with applications inadvertently acting as proxies for unauthorized actions, circumventing TCC and compromising the system's security model. This highlights the importance for applications to implement robust security measures to avoid becoming vectors for exploitation.
Case study: Microsoft applications for macOS
During our research, we discovered that many of Microsoft's macOS applications employ hardened runtime, a feature that enhances security. However, they also have the com.apple.security.cs.disable-library-validation entitlement active, which can be potentially risky.
Even though hardened runtime guards against library injection attacks and the sandbox secures user data and system resources, a malware might still find ways to exploit certain applications under specific conditions. If successful, this would allow the attacker to assume the application's entitlements and permissions. It's important to note that not all sandboxed applications are equally susceptible. Typically, a combination of specific entitlements or vulnerabilities is required for an app to become a viable attack vector.
The vulnerabilities we're addressing are relevant when an application loads libraries from locations an attacker could potentially manipulate. If the application has the com.apple.security.cs.disable-library-validation entitlement, it allows an attacker to inject any library and run arbitrary code within the compromised application. As a result, the attacker could exploit the application's full set of permissions and entitlements.
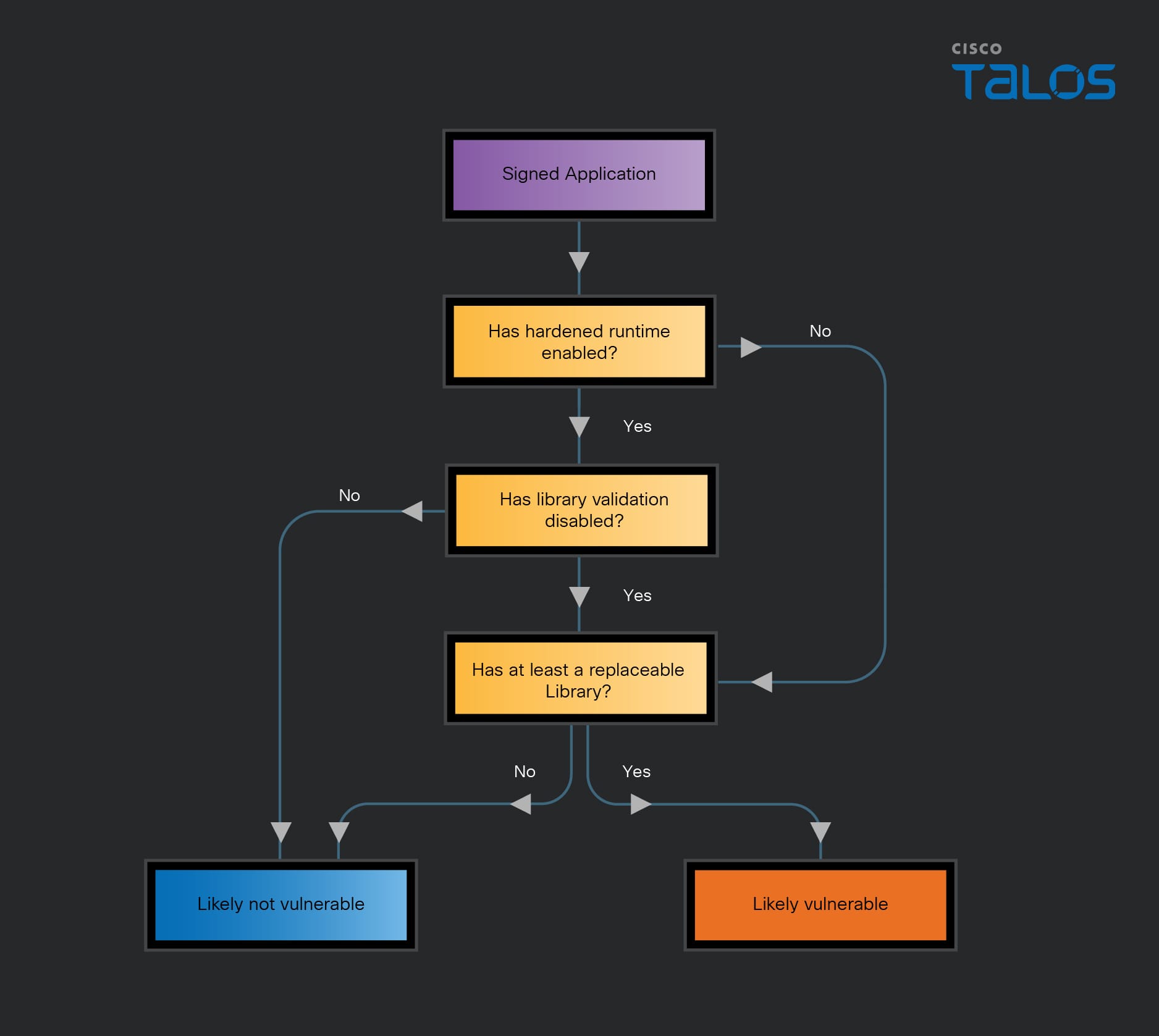
The flowchart above, even though not exhaustive, describes a simple schema to check if an app is potentially vulnerable to library injection. Many cases are not caught by this flowchart.
We are going to examine two groups of apps: One that exhibits numerous similarities in terms of their vulnerabilities and another that possesses unique characteristics, partly because two of the apps are helper apps, among other specific features.
The first group is “Microsoft Office apps”:
- Microsoft Word
- Microsoft Outlook
- Microsoft Excel
- Microsoft OneNote
- Microsoft PowerPoint
The second group is “Microsoft Teams apps”:
- Microsoft Teams (work or school) the main app
- Microsoft Teams (work or school) WebView.app
- Microsoft Teams (work or school) com.microsoft.teams2.modulehost.app
For each group, we are going to show why the apps are vulnerable and describe the implications.
Microsoft Office apps
Although the Office apps are distinct from one another, they share a common characteristic: They are all hardened runtime apps that include the following entitlement:
This effectively indicates that the security protection provided by the hardened runtime, which guards against the hijacking of dynamically linked libraries, is disabled. As a result, all the office apps permit the loading of unsigned dynamic libraries. This poses a security concern because a malware could exploit the apps' permissions without proper authorization.
For example, consider the entitlements for Microsoft Outlook at the time we reported its vulnerability:
$ codesign -dv --entitlements - "/Applications/Microsoft Outlook.app"
The other Office apps are different, but they all share both the hardened runtime feature and the com.apple.security.cs.disable-library-validation entitlement, which is set to true .
If an attacker manages to inject a malicious library, they could utilize all the entitlements and permissions of the apps.
Typically, the only replaceable libraries are the ones with relative import. Below is a portion of the imports from the Microsoft Outlook app:
The @rpath entries attempt to use all the paths defined as LC_RPATH in the binary's load commands:
For instance, in the case of Microsoft Outlook , there is only one LC_RPATH that uses @loader_path/../Frameworks . The LC_RPATH specifies the search paths for dynamic libraries and can potentially be:
- @executable_path: This refers to the path containing the executable
- @loader_path: When used in a binary, this behaves the same as @executable_path, but when used in a dynamic library (dylib), it refers to the directory where that library is located.
Therefore, in this case, for an executable, the path is relative to the executable itself. The other Office apps have similar relative imports.
To modify an application, already executed once, located in /Applications, a specific entitlement is required. However, it is possible to circumvent this requirement by copying and modifying the application in another folder, such as /tmp.
Given that there are some relative imports and the entitlement to disable library validation is present, all the Microsoft Office apps are vulnerable to library injection attacks.
All Microsoft Office apps share several common features, but their entitlements differ. This means that the impact of injecting a library into one of the apps varies depending on which specific app is compromised. Generally speaking, if an app has already been granted certain permissions, an attacker exploiting the app could access restricted resources without any further user interaction.
For example:
All apps, except for Outlook, can send an Apple event to Microsoft Outlook to dispatch an email without any user prompt. Essentially, the attacker is capable of sending emails without user interaction.
All apps, except for Excel, have the ability to record audio, some can even access the camera.
The attacker can extract keychain entries belonging to the UBF8T346G9.com.microsoft.identity.universalstorage access group using any of the apps.
Microsoft Teams apps
The Microsoft Teams (for work or school) app is similar to Microsoft Office apps in its vulnerability to library injection. However, what sets it apart is that within the app, there are helper applications that are also susceptible to this vulnerability. Nonetheless, one of these helper applications does not have any relative imported libraries.
Similar to the Microsoft Office suite, these three apps are vulnerable to library injection attacks. This is because, despite having hardened runtime enabled, all three possess the com.apple.security.cs.disable-library-validation entitlement, which is set to true .
Microsoft Teams (work or school)
Microsoft Teams (for work or school), hereafter referred to simply as Teams, has numerous entitlements. The entitlements for the Teams app at the time of this report were as follows:
$ codesign -dv --entitlements - "/Applications/Microsoft Teams (work or school).app"
Similar to other Microsoft Office apps, Teams possesses several entitlements and relative imported libraries. However, the main difference from the other apps is that if a user has installed Teams, it is likely that the app has already been used, which means that camera and microphone permissions have probably already been granted. An attacker capable of injecting a library into Teams would almost certainly be able to access the camera and microphone without triggering any pop-up notifications using Teams as its proxy.
com.microsoft.teams2.modulehost.app
One of the helper apps for Microsoft Teams, previously known as com.microsoft.teams2.modulehost.app , has been renamed to “Microsoft Teams ModuleHost.app” in the latest release. This module had the following entitlements:
$ codesign -dv --entitlements - "/Applications/Microsoft Teams (work or school).app/Contents/Helpers/com.microsoft.teams2.modulehost.app"
This app has multiple relative imports. Although it only has three entitlements, the helper app can utilize some entitlements of the main app. This could potentially enable an attacker to take photos, record audio, exfiltrate data and perform other unauthorized actions.
WebView.app
WebView.app, one of the helper apps for Teams, had the following entitlements at the time we reported the issue:
$ codesign -dv --entitlements - "/Applications/Microsoft Teams (work or school).app/Contents/Helpers/Microsoft Teams WebView.app"
Similar to the previous helper app, this app had only three entitlements. Despite this, the helper app can still request audio recording permission, as it inherits some entitlements from the main app.
A distinctive feature of this helper app is that it does not use relative imports:
This creates a problem from the perspective of an attacker. Indeed, by following the flowchart above concerning the assessment of whether an app is vulnerable to library injection attacks, we would conclude that it is “Likely not vulnerable.” However, the relative imports used by the app are not the only means to load a library. In fact, the app itself utilizes dlopen with a relative path. This is not revealed in the app's static dependencies. Here is a snippet of the app's code:
The code above essentially constructs the <WebView executable path>/../Frameworks/Microsoft Edge Framework.framework/Versions/122.0.2365.103/Microsoft Edge Framework path and utilizes dlopen to load the Microsoft Edge Framework library, subsequently calling the ChromeMain function. Since the application is dynamically loading a library, the behavior closely resembles that of loading a library through a relative import, which makes this app vulnerable to library injection.
Conclusions
The macOS security model offers enhanced protection that goes beyond the capabilities of standard DAC policy systems. It notifies users whenever an application attempts to access sensitive data or privacy-related resources. Moreover, macOS includes specific features that prevent dynamic library injection, thereby effectively neutralizing an entire category of vulnerabilities. Although no system is without flaws and new vulnerabilities may arise, this framework plays a significant role in reducing them and heightening user awareness of application behavior.
Our research centered on applications vulnerable to library injection, a scenario enabling a malware to exploit the entitlements and permissions already granted to a vulnerable app.
We used Microsoft apps as a case study. Each of these applications had hardened runtime enabled, together with the com.apple.security.cs.disable-library-validation entitlement. Microsoft considers these issues low risk. Nevertheless, of the eight applications we reported, the following four were updated by Microsoft and no longer possess the com.apple.security.cs.disable-library-validation entitlement and are therefore no longer vulnerable to the scenario we described:
- Microsoft Teams (work or school) com.microsoft.teams2.modulehost.app, now renamed Microsoft Teams ModuleHost.app
However, the remaining four applications remain vulnerable:
The vulnerable apps leave the door open for adversaries to exploit all of the apps' entitlements and, without any user prompts, reuse all the permissions already granted to the app, effectively serving as a permission broker for the attacker.
Microsoft appears to use the com.apple.security.cs.disable-library-validation entitlement for certain apps to support some kind of “plug-ins.” According to Apple, this entitlement allows the loading of plug-ins signed by third-party developers. Yet, as far as we know, the only “plug-ins” available to Microsoft's macOS apps are web-based and known as “Office add-ins.”
If this understanding is correct, it raises questions about the necessity of disabling library validation, especially if no additional libraries are expected to be loaded. By using this entitlement, Microsoft is circumventing the safeguards offered by the hardened runtime, potentially exposing its users to unnecessary risks.
It's also important to mention that it’s unclear how to securely handle such plug-ins within macOS' current framework. Notarization of third-party plug-ins is an option, albeit a complex one, and it would require Microsoft or Apple to sign third-party modules after verifying their security.
MacOS could also introduce a user prompt, akin to the resource permissions in TCC, enabling users to decide whether to load a specific third-party plug-in. This would provide a more controlled means of granting access without broadly compromising security.
Share this post
Related content, multiple vulnerabilities in tp-link omada system could lead to root access.
Affected devices could include wireless access points, routers, switches and VPNs.
Talos releases new macOS open-source fuzzer
Compared to fuzzing for software vulnerabilities on Linux, where most of the code is open-source, targeting anything on macOS presents a few difficulties.
Dissecting a complex vulnerability and achieving arbitrary code execution in Ichitaro Word
Research conducted by Cisco Talos last year uncovered multiple vulnerabilities rated as low severity despite their ability to allow for full arbitrary code execution.
A Case-Study of Metoclopramide Prescription Error : A Grim Reminder
- Brief Report
- Open access
- Published: 22 August 2024
- Volume 48 , article number 78 , ( 2024 )
Cite this article
You have full access to this open access article

- Florent Wallet 1 ,
- Charlotte Doudet 2 ,
- Alexandre Theissen 3 ,
- Arnaud Friggeri 4 , 5 &
- Charles-Hervé Vacheron 1 , 6 , 7
The integration of Computerized Provider Order Entry (CPOE) systems in hospitals has been instrumental in reducing medication errors and enhancing patient safety. This study examines the implications of a software oversight in a CPOE system : Metoclopramide had a concentrated formulation (100 mg) delisted (and then not manufactured) in 2014 due to safety concerns. Despite this, the CPOE system continued to accept prescriptions for this formulation because it was not removed from the medication library by the pharmacist. The objective of our study was to describe this specific prescription error related to an outdated the medication library of the CPOE. We analyzed all metoclopramide prescriptions from 2014, to 2023. Our findings showed that errors involving 100 mg or more dosages were relatively rare, at 2.98 per 1000 prescriptions (34 errors in 11,372 prescriptions). Notably, 47.1% of these errors occurred during on-call shifts, and 68% of these errors led to actual administration. These errors correlated with periods of higher nurse workload. The findings advocate for the integration of dedicated pharmacists into ICU teams to minimize medication errors and enhance patient outcomes, and a proactive medication management in healthcare.
Similar content being viewed by others
Prescribing error at hospital discharge: a retrospective review of medication information in an irish hospital.

The incidence and severity of errors in pharmacist-written discharge medication orders
The impact of a hospital electronic prescribing and medication administration system on medication administration safety: an observational study.
Avoid common mistakes on your manuscript.
Brief Technical Report
The integration of Computerized Provider Order Entry (CPOE) systems in hospitals represents a significant step towards enhancing patient safety. Their adoption has been synonymous with a marked reduction in medication errors. However, it is worth noting that with the implementation of CPOE, we are also witnessing the emergence of new, unique types of errors [ 1 ]. These errors, though present, have their incidence and implications not fully documented in current medical literature. Metoclopramide, a drug primarily prescribed for the prevention and treatment of nausea and vomiting, is frequently used in intensive care settings. Conventionally, it is available in 10 mg ampoules, with dosage recommendations spanning from 10 to 30 mg per day. In France, until 2014, a more concentrated formulation of metoclopramide (100 mg ampoules) was available. This formulation was used for managing nausea and vomiting in patients undergoing chemotherapy or radiotherapy and was not used in the ICU setting. It was, however, delisted (and therefore not manufactured) from the French market in 2014 owing to concerns about its benefit-risk profile [ 2 ].
Remarkably, a software oversight in our CPOE (IntelliSpace Critical Care and Anesthesia ® , Phillips, Amsterdam) dedicated to our ICU, and used for the physician prescription still accepted prescriptions for the 100 mg metoclopramide formulation. This loophole was due to a lack of update of the medication library of the CPOE by the pharmacist, left room for errors, particularly if the prescribing physician was not adequately vigilant : indeed, a physician who wishes to prescribe ‘one ampoule’ of metoclopramide could choose an ampoule containing 100 mg of metoclopramide. Therefore this led to a prescription error were the physician could prescribe one or two ampoule of metoclopramide 100 mg (i.e. 100 or 200 mg). On the 29/08/2023, this error was detected by a physician and corrected in the medication library of our CPOE by the pharmacist.
We therefore reviewed all metoclopramide prescriptions from 12/02/2014 to 29/08/2023 in a French university Intensive Care Unit (ICU). No exclusion criteria were applied. Our findings revealed that prescribing errors, were relatively infrequent, accounting for 2.98 per 1000 prescriptions (34 errors from a total of 11,372 metoclopramide prescriptions). A closer look revealed that 47.1% of these errors took place during on-call shifts (between 6pm to 8 am). Additionally, 68% ( n = 23) of these prescription errors led to an administration of metoclopramide (informatic confirmation of administration). It was evident from our study that errors coincided with periods when nurses faced a higher workload, especially compared to standard on-call periods, since the validation of the metoclopramide was associated with a higher NEMS (Nine Equivalents of nursing Manpower use Score) for the patient (mean NEMS 6.75 ± 3.87 vs. 12.5 ± 7.13, p value of the Wilcoxon test < 0.001). Briefly, the NEMS is a well validated tool to estimate the nurse workload per ICU patient based on care required, ranging from 0 (low workload) to 66 (high workload) points [ 3 ].
No adverse events (such as extrapyramidal syndrome or cardiovascular disorders) were reported in relation to metoclopramide inappropriately high dosage. This can be explained by the nurse correcting the dosage during the administration, or due to metoclopramide broad therapeutic window [ 4 ]. However, this serves as a grim reminder of the potential consequences that could arise from similar oversights with high-risk medications. This is especially true for drugs like catecholamines or sedatives, where the margin for error is minimal and the stakes are significantly higher. The same caution applies to drugs with a wider therapeutic margin but with the potential for severe adverse drug events, such as insulin or opioids.
An important aspect of this study that warrants further discussion is the direct correlation between the workload of nursing staff and the incidence of medication errors. Our findings notably revealed that a substantial proportion of these errors occurred during on-call shifts, a time typically characterized by increased workload and reduced staffing levels. This correlation is more than coincidental; it highlights a systemic issue in healthcare settings where the workload and staffing ratios significantly impact the likelihood of errors. The complexity of these tasks, combined with a high patient-to-nurse ratio, can lead to a heightened risk of errors. This situation is exacerbated during on-call hours when fatigue and reduced vigilance further impair their ability to catch and correct potential errors [ 5 ].
Most importantly, this observation confirms the growing evidence that pharmacists are a crucial part of the ICU team, emphasizing the need for a dedicated pharmacist in each ICU unit [ 6 ]. The role of a pharmacist in the ICU is specialized, contributing significantly to patient safety, and it requires specific qualifications for ICU pharmacovigilance [ 7 , 8 ]. In this instance, a pharmacist dedicated to this specific ICU’ would have update the medication library by removing the incorrect metoclopramide formulation in 2014. Alternatively, by reviewing the medications of patients admitted to the ICU, this error could have been avoided and likely would not have persisted for nearly 10 years.
In conclusion, while CPOE systems have been instrumental in enhancing patient safety, our study reveals that technological solutions alone are not sufficient. There is a pressing need for a holistic approach that addresses the human factors in healthcare, such as nursing workload and interdisciplinary collaboration. By recognizing and addressing these factors, we can significantly reduce the incidence of medication errors and, consequently, improve the overall quality of patient care in ICU settings [ 9 , 10 , 11 ]. Furthermore, an ICU pharmacist managing these CPOE systems would optimize interventions to prevent prescription errors. Such interventions could include restricting prescriptions, issuing alerts about incorrect dosing or drug interactions, and enhancing the overall appropriateness of medication use [ 12 , 13 ].
This study thus sheds light on the need for more robust workload management strategies in healthcare settings. Adequately staffing shifts, particularly during high-risk periods like nights and weekends, and ensuring reasonable patient-to-nurse ratios are essential steps in mitigating medication errors. Additionally, providing support systems such as regular breaks, adequate rest periods, and mental health resources can significantly reduce fatigue-related errors.
Data Availability
No datasets were generated or analysed during the current study.
Brown CL, Mulcaster HL, Triffitt KL, et al (2017) A systematic review of the types and causes of prescribing errors generated from using computerized provider order entry systems in primary and secondary care. J Am Med Inform Assoc JAMIA 24:432–440. https://doi.org/10.1093/jamia/ocw119
Article PubMed Google Scholar
Spécialités fortement dosées en métoclopramide - Rappel de lots - ANSM: Agence nationale de sécurité du médicament et des produits de santé. https://archive.ansm.sante.fr/S-informer/Informations-de-securite-Retraits-de-lots-et-de-produits/Specialites-fortement-dosees-en-metoclopramide-Rappel-de-lots . Accessed 27 Oct 2023
Reis Miranda D, Moreno R, Iapichino G (1997) Nine equivalents of nursing manpower use score (NEMS). Intensive Care Med 23:760–765. https://doi.org/10.1007/s001340050406
Article CAS PubMed Google Scholar
Ell C, Braun J, König HJ, et al (1985) Pharmacokinetic studies of high-dose metoclopramide with and without forced diuresis. Klin Wochenschr 63:572–574. https://doi.org/10.1007/BF01733203
Rogers AE, Dean GE, Hwang W-T, Scott LD (2008) Role of registered nurses in error prevention, discovery and correction. BMJ Qual Saf 17:117–121. https://doi.org/10.1136/qshc.2007.022699
Article CAS Google Scholar
McKenzie C, Spriet I, Hunfeld N (2024) Ten reasons for the presence of pharmacy professionals in the intensive care unit. Intensive Care Med. https://doi.org/10.1007/s00134-023-07285-4
Lee H, Ryu K, Sohn Y, et al (2019) Impact on Patient Outcomes of Pharmacist Participation in Multidisciplinary Critical Care Teams: A Systematic Review and Meta-Analysis. Crit Care Med 47:1243–1250. https://doi.org/10.1097/CCM.0000000000003830
Leili M, Nikvarz N (2023) Evaluating the role of clinical pharmacist in the detection and reduction of medication errors in a specialized burn unit. Burns J Int Soc Burn Inj 49:646–654. https://doi.org/10.1016/j.burns.2022.04.013
Article Google Scholar
Smetana KS, Flannery AH, Gurnani PK, et al (2023) PHarmacist avoidance or reductions in medical costs in CRITically ill adults rounding with one SERVICE compared to two or more services: PHARM-CRIT-SERVICE. JACCP J Am Coll Clin Pharm 6:1000–1007. https://doi.org/10.1002/jac5.1798
Naamneh R, Bodas M (2024) The effect of electronic medical records on medication errors, workload, and medical information availability among qualified nurses in Israel– a cross sectional study. BMC Nurs 23:270. https://doi.org/10.1186/s12912-024-01936-7
Article PubMed PubMed Central Google Scholar
Leviatan I, Oberman B, Zimlichman E, Stein GY (2021) Associations of physicians’ prescribing experience, work hours, and workload with prescription errors. J Am Med Inform Assoc JAMIA 28:1074–1080. https://doi.org/10.1093/jamia/ocaa219
Pontefract SK, Hodson J, Slee A, et al (2018) Impact of a commercial order entry system on prescribing errors amenable to computerised decision support in the hospital setting: a prospective pre-post study. BMJ Qual Saf 27:725–736. https://doi.org/10.1136/bmjqs-2017-007135
C Q, T DR, T VN, et al (2019) Development and implementation of “Check of Medication Appropriateness” (CMA): advanced pharmacotherapy-related clinical rules to support medication surveillance. BMC Med Inform Decis Mak 19:. https://doi.org/10.1186/s12911-019-0748-5
Download references
Acknowledgements
Benjamin BERTHET for his help in data Collection.
None to disclose.
Open access funding provided by Hospices Civils de Lyon.
Author information
Authors and affiliations.
PHE3ID, Centre International de Recherche en Infectiologie, Service d’Anesthésie Réanimation – Médecine Intensive, Institut National de la Santé et de la Recherche Médicale U1111, CNRS Unité Mixte de Recherche 5308, École Nationale Supérieure de Lyon, Université Claude Bernard Lyon 1, Centre Hospitalier Lyon Sud, Hospices Civils de Lyon, Lyon, France
Florent Wallet & Charles-Hervé Vacheron
Service de pharmacie, Centre Hospitalier Lyon Sud, Hospices Civils de Lyon, Lyon, France
Charlotte Doudet
Anesthésie - Réanimation Chirurgicale Clinique Saint François, Pierre-Bénite, France
Alexandre Theissen
Département d’Anesthésie Réanimation, Centre Hospitalier Lyon Sud Hospices Civils de Lyon, Pierre-Bénite, France
Arnaud Friggeri
Faculté de Médecine Lyon Est, CIRI, Centre International de Recherche en Infectiologie (Equipe Laboratoire des Pathogènes Emergents), Inserm, U1111, Université Claude Bernard Lyon 1, CNRS, UMR5308, Lyon, France
Service de Biostatistique - Bioinformatique, Hospices Civils de Lyon, Pôle Santé Publique, Lyon, France
Charles-Hervé Vacheron
Centre Hospitalier Lyon Sud Hospices Civils de Lyon, Service d’anesthésie- réanimation, 165 chemin du Grand Revoyet, Pierre-Benite, 69495, France
You can also search for this author in PubMed Google Scholar
Contributions
CHV, FW wrote the first draft of the manuscript CD, AT, AF reviewed the manuscript critically.
Corresponding author
Correspondence to Charles-Hervé Vacheron .
Ethics declarations
Ethical approval.
Not applicable.
Competing Interests
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Wallet, F., Doudet, C., Theissen, A. et al. A Case-Study of Metoclopramide Prescription Error : A Grim Reminder. J Med Syst 48 , 78 (2024). https://doi.org/10.1007/s10916-024-02099-3
Download citation
Received : 20 November 2023
Accepted : 10 August 2024
Published : 22 August 2024
DOI : https://doi.org/10.1007/s10916-024-02099-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Medication error
- Patient safety
- Nurse workload
- Find a journal
- Publish with us
- Track your research
Multi-Objective Transportation System Optimization Using Agent-Based Simulation—A Study of Cordon- and Mileage-Based Congestion Pricing
New citation alert added.
This alert has been successfully added and will be sent to:
You will be notified whenever a record that you have chosen has been cited.
To manage your alert preferences, click on the button below.
New Citation Alert!
Please log in to your account
Information & Contributors
Bibliometrics & citations, view options, recommendations, combinatorial auction-based pricing for multi-tenant autonomous vehicle public transportation system.
A smart city provides its people with high standard of living through advanced technologies, and transport is one of the major foci. With the advent of autonomous vehicles (AVs), an AV-based public transportation system has been proposed recently, which ...
Efficient market mechanisms and simulation-based learning for multi-agent systems
A preference-based, multi-unit auction for pricing and capacity allocation.
We study a pricing and allocation problem of a seller of multiple units of a homogeneous item.We consider a setting where buyers expect fairness in the allocation of the units.We present a semi-market mechanism in the form of an iterative ascending-bid ...
Information
Published in, publication history.
- Research-article
Contributors
Other metrics, bibliometrics, article metrics.
- 0 Total Citations
- 0 Total Downloads
- Downloads (Last 12 months) 0
- Downloads (Last 6 weeks) 0
View options
Login options.
Check if you have access through your login credentials or your institution to get full access on this article.
Full Access
Share this publication link.
Copying failed.
Share on social media
Affiliations, export citations.
- Please download or close your previous search result export first before starting a new bulk export. Preview is not available. By clicking download, a status dialog will open to start the export process. The process may take a few minutes but once it finishes a file will be downloadable from your browser. You may continue to browse the DL while the export process is in progress. Download
- Download citation
- Copy citation
We are preparing your search results for download ...
We will inform you here when the file is ready.
Your file of search results citations is now ready.
Your search export query has expired. Please try again.

IMAGES
COMMENTS
The purpose of this study is to design and implement an integrated Library Management System (LMS) to improve the efficiency of library operations and enhance the user experience for patrons.
The Library Management System is a simple Python program that emulates the core functionalities of a library, including adding books, displaying the book catalog, lending books, and returning books. This case study presents a straightforward implementation of a library management system for educational and organizational purposes. Objectives:
3.1 Introduction | Synopsys for Library Management System Project. A Library Management System (LMS) is a software application that simplifies and automates the operations of libraries. It is a complete system for managing library duties such as purchases, member management, monitoring, storing, and circulation.
Case Study: Library Management System. Step 1: Class Diagram to Conceptual ERD. In the initial phase, we start with a class diagram that represents the high-level structure of our system. Here's a simplified class diagram for our library management system: From this class diagram, we can create a conceptual ERD: Conceptual ERD:
A use case diagram in UML helps to show the various ways in which a user could interact with a system. For a Library Management System, the use case diagram helps visualize the interactions between users (actors) and the system's functionalities (use cases). This diagram provides a clear, simplified way to understand how the system operates ...
In this chapter, we present the library management system case study and briefly discuss the results. We considered a library management system that is composed of four components to provide users with the main library services. These services are covered by test cases designed to build component test models as well as the acceptance test model.
Lecture 17 Software Engineering. 1.5 Adding Books to the Library. There are two cases to consider: -where the book is completely new to the library; -where the book is another copy of a book that is already in the library. We have two schemas to capture these two situations: -AddNewBook; -AddAnotherCopy.
By use case. CI/CD & Automation DevOps DevSecOps Resources Topics. AI DevOps Security Software Development View all Explore. Learning Pathways White papers, Ebooks, Webinars Customer Stories Partners Open Source GitHub Sponsors. Fund open source developers The ReadME Project ...
Every library has a unique name and is either a main library or a branch library. A main library may have zero or more branch libraries and every branch library is a branch of exactly one main library. A borrower has a name and a unique ID code. A borrower can have many books on loan, but each copy of a book can only be on loan to one borrower.
LMS Database: Case Study Analysis. By: GPDCM Jayasekara. Databeses Analysis. GPDCM Jayasekara 2022. 2. Case Overview. A library service wants to create a database to store details of its libra ...
UML diagrams for library management... Library Management System. Read the following documents/reports to understand the problem statement, requirements and other necessary things related to the Library Management Application: Doc1, Doc2, Doc3, Doc4, Doc5, Doc6.
The Library Management System (LMS) is a computerized platform that aims to streamline and automate the daily operations of a library. This case study examines the implementation and utilization of an LMS at the NOWA Educational Centre, a private educational institution in Nigeria.
We have three main actors in our system: Librarian: Mainly responsible for adding and modifying books, book items, and users. The Librarian can also issue, reserve, and return book items. Member: All members can search the catalog, as well as check-out, reserve, renew, and return a book. System: Mainly responsible for sending notifications for overdue books, canceled reservations, etc.
The Los Angeles Public Library serves the largest population of any library system in the nation, more than 3.9 million people, through a Central Library and 72 branches. The library district serves a large percentage of non-native English speakers, as well as some of the United States' wealthiest and poorest residents.
Library Management System-case Study - Free download as Word Doc (.doc / .docx), PDF File (.pdf), Text File (.txt) or read online for free. The document describes a proposed library management system for a university. The system aims to automate and computerize the library to make it easier for students, faculty, and administrators to access library information and resources.
SCHOOL LIBRARY MANAGEMENT SYSTEM Case Study Problem analysis. The system analyst is required to: i). Identify & understand the problem. ii). Find out much about the existing system (whether manual or computerised) in order to come up with a good & relevant proposal for the new system.
CASE STUDY- Library Management System - Free download as Word Doc (.doc / .docx), PDF File (.pdf), Text File (.txt) or read online for free. This document outlines various UML diagrams for a library management system, including use case, activity, class, state, collaboration, sequence, component, and deployment diagrams. The diagrams model key processes and components involved in issuing and ...
Library Management System Case Study - Free download as Word Doc (.doc), PDF File (.pdf), Text File (.txt) or read online for free. Library Management System Case Study for students of Software Engineering in Second Year B.Sc. Computer Science and B. Sc. Information Technology
A use case diagram in UML helps to show the various ways in which a user could interact with a system. For a Library Management System, the use case diagram helps visualize the interactions between users (actors) and the system's functionalities (use cases). This diagram provides a clear, simplified way to understand how the system operates and wha
Computer Science and Engineering Vol.8, Issue.2, pp.65-76, April (2020) E-ISSN: 2320-7639 Development of an Online Integrated Library Management Information System: Case Study "University of Gitwe" Gatete Marcel1*, UWIZEYIMANA Faustin2 1,2 Computer Science Department, University of Gitwe, Ruhango, Rwanda * Corresponding Author: gtmrclnl ...
Case Studies. In 2014 and 2015, 10 public libraries from across the country took part in an extensive, 18-month training to learn the Harwood Institute's Turning Outward approach and put it to use in their communities. Known as the Libraries Transforming Communities (LTC) Public Innovators Cohort, these libraries spent countless hours talking ...
In this case study, a qualitative research design was adopted, and 37 staff were purposively selected from Moi University library to be interviewed. Semi-structured individual interviews were used to collect data and a thematic analysis technique was used in the analysis. ... Implementing change more successfully during library system migration ...
Case study: Microsoft applications for macOS. During our research, we discovered that many of Microsoft's macOS applications employ hardened runtime, a feature that enhances security. However, they also have the com.apple.security.cs.disable-library-validation entitlement active, which can be potentially risky.
This study demonstrated an integrated web-based healthcare delivery system to forecast future hospitalizations. Developing such systems was not covered enough in the literature, and the goal is to help other healthcare organizations to use the study as a reference to develop their own systems in the future with forecasting models that best fit ...
Case Study of library management system - Free download as Word Doc (.doc), PDF File (.pdf), Text File (.txt) or read online for free. The unified library application system allows library members to reserve and borrow books online from anywhere in the world. It globalizes the traditional library system by enabling online reservations, book issues, returns and payment of dues.
The integration of Computerized Provider Order Entry (CPOE) systems in hospitals has been instrumental in reducing medication errors and enhancing patient safety. This study examines the implications of a software oversight in a CPOE system : Metoclopramide had a concentrated formulation (100 mg) delisted (and then not manufactured) in 2014 due to safety concerns. Despite this, the CPOE system ...
Congestion pricing policies are increasingly being considered to aid in congestion management and transportation funding in urban areas. This article presents a case study of the optimization of congestion pricing policy design using the Berkeley Integrated System for Transportation Optimization (BISTRO), an open-sourced transportation planning and decision support system (DSS) that uses an ...