A powershell script for activating an eligible role assignment in Azure AD
By Anatoly Mironov
Recently my role assignments in Azure AD were switched from permanent to eligible ones. This is part of PIM - Privileged Identity Management, you can read more about it on MS Docs:
- Start using Privileged Identity Management
To activate your eligible assignment you can use Azure Portal, Graph API, and PowerShell. The activation in the portal and Graph API is described on MS Docs:
- Activate my Azure AD roles in PIM
My roles within Privileged Identity Management in Azure Portal
I created a simple powershell script for activating my eligible roles quickier when I need it. There are two variants of this script:
- a generic one, that can be run by anyone
- a “shortcut” version that can be created for a specific account, a specific role, to make it even quicker.

A generic version
This version fetches the assignments you have, tenant id (resourcid), your account id (objectid, subjectid), and then it activates your desired role. Some parts can be made even more generic, but the key thing here is that you can adjust it and run for any account.
Shortcut version
This version assumes that you already know all the ids, by running the generic version or by looking it up in Azure. When you know those ids, you can skip many calls to Azure AD, which makes activation quicker and you can start working on your task rather than surfing around to activate your role in Azure.
Save it as a script and run it when you need it. Much quicker. One important note, though: Please be aware that it still can take time to fully activate (propagate) your role, especially SharePoint Administrator, often a couple of minutes. But instead of clicking around, run the script and go grab a cup of coffee, when you’re back, you are good to go.
Security Note. Automating role activations is not less secure. You still have to log in to Azure AD using MFA (I hope you have it) even when you run the script.
- administrator
All about Microsoft 365
Generate a report of Azure AD role assignments via the Graph API or PowerShell
A while back, I published a short article and script to illustrate the process of obtaining a list of all Azure AD role assignments. The examples therein use the old MSOnline and Azure AD PowerShell modules, which are now on a deprecation path. Thus, it’s time to update the code to leverage the “latest and greatest”. Quotes are there for a reason…
The updated script comes in two flavors. The first one is based on direct web requests against the Graph API endpoints and uses application permissions, thus is suitable for automation scenarios. Do make sure to replace the authentication variables, which you can find on lines 11-13. Better yet, replace the whole authentication block (lines 7-36) with your preferred “connect to Graph” function. Also make sure that sufficient permissions are granted to the service principal under which you will be running the script. Those include the Directory.Read.All scope for fetching regular role assignments and performing directory-wide queries, and the RoleManagement.Read.Directory for PIM roles.
The second flavor is based on the cmdlets included as part of the Microsoft Graph SDK for PowerShell. As authentication is handled via the Connect-MGGraph cmdlet, the script is half the size of the first one. And it would’ve been even smaller were it not for few annoying bugs Microsoft is yet to address.
In all fairness, switching to the Graph does offer some improvements, such as being able to use a single call to list all role assignments. This is made possible thanks to the /roleManagement/directory/roleAssignments endpoint (or calling the Get-MgRoleManagementDirectoryRoleAssignment cmdlet). Previously, we had to iterate over each admin role and list its members, which is not exactly optimal, and given the fact that the list of built-in roles has now grown to over 90, it does add up. On the negative side, we have a bunch of GUIDs in the output, most of which we will want to translate to human-readable values, as they designate the user, group or service principal to which a given role has been assigned, as well as the actual role. One way to go about this is to use the $expand operator (or the – ExpandProperty parameter if using the SDK) to request the full object.
While this is the quickest method, the lack of support for the $select operator inside an $expand query means we will be fetching a lot more data than what we need for the report. In addition, there seems to be an issue with the definition of the expandable properties for this specific endpoint, as trying to use the handy $expand=* value will result in an error ( “Could not find a property named ‘appScope’ on type ‘Microsoft.DirectoryServices.RoleAssignment'” ). In effect, to fetch both the expanded principal object and the expanded roleDefinition object, we need to run two separate queries and merge the results. Hopefully Microsoft will address this issue in the future (the /roleManagement/directory/roleEligibilitySchedules we will use to fetch PIM eligible role assignments does support $expand=* query).
Another option is to collect all the principalIDs and issue a POST request against the /directoryObjects/getByIds endpoint (or the corresponding Get-MgDirectoryObjectById cmdlet), which does have a proper support for $select . A single query can be used to “translate” up to 1000 principal values, which should be sufficient for most scenarios. With the information gathered from the query, we can construct a hash-table and use it to lookup the property values we want to expose in our report. Lastly, you can also query each principalID individually, but that’s the messiest option available.
Apart from role assignments obtained via the /roleManagement/directory/roleAssignments call, the script can also include any PIM eligible role assignments. To fetch those, invoke the script with the – IncludePIMEligibleAssignments switch. It will then call the /v1.0/roleManagement/directory/roleEligibilitySchedules endpoint, or similarly, use the Get-MgRoleManagementDirectoryRoleEligibilitySchedule cmdlet. Some minor adjustments are needed to ensure the output between the two is uniform, which includes the aforementioned issue with expanding the navigation properties. But hey, it wouldn’t be a Microsoft product if everything worked out of the box 🙂
Here are some examples on how to run the scripts. The first example uses the Graph API version and no parameters. For the second one, we invoke the – IncludePIMEligibleAssignments parameter in order to include PIM eligible role assignments as well. The last example does the same thing, but for the Graph SDK version of the script.
And with that, we’re ready to build the output. Thanks to the $expand operator and the workarounds used above, we should be able to present sufficient information about each role assignment, while minimizing the number of calls made. The output is automatically exported to a CSV in the script folder, and includes the following fields:
- Principal – an identifier for the user, group or service principal to which the role has been assigned. Depending on the object type, an UPN, appID or GUID value will be presented.
- PrincipalDisplayName – the display name for the principal.
- PrincipalType – the object type of the principal.
- AssignedRole – the display name of the role assigned.
- AssignedRoleScope – the assignment scope, either the whole directory (“/”) or a specific administrative unit.
- AssignmentType – the type of assignment (“Permanent” or “Eligible”).
- IsBuiltIn – indicates whether the role is a default one, or custom-created one.
- RoleTemplate – the GUID for the role template.
Now, it’s very important to understand that this script only covers Azure AD admin roles, either default or custom ones, and optionally eligible PIM-assignable roles (do note that the PIM cmdlets/endpoints do not cover all custom role scenarios). Apart from these, there are numerous workload-specific roles that can be granted across Office 365, such as the Exchange Online Roles and assignments, Roles in the Security and Compliance Center, site collection permissions in SharePoint Online, and so on. Just because a given user doesn’t appear in the admin role report, it doesn’t mean that he cannot have other permissions granted!
In addition, one should make sure to cover any applications (service principals) that have been granted permissions to execute operations against your tenant. Such permissions can range from being able to read directory data to full access to user’s messages and files, so it’s very important to keep track on them. We published an article that can get you started with a sample script a while back.
9 thoughts on “ Generate a report of Azure AD role assignments via the Graph API or PowerShell ”
- Pingback: Reporting on Entra ID directory role assignments (including PIM) - Blog
This script is very nicely written, however the output of the Powershell Graph SDK version is incorrect (I didn’t check the other).
If I am eligible to activate a role I’ll be in the eligible list. However once I activate the role, my activated role assignment will show up in the list of role assignments from “Get-MgRoleManagementDirectoryRoleAssignment”. The output of that command doesn’t include a ‘status’ property. Your script assumes that if there’s no ‘status’ then the assignment is permanent, however that’s not accurate. So every eligible user who has activated a role shows up twice in the output of your script – once as as eligible for the role and once as a permanent assignment.
I came across your script because I’m trying to accomplish a similar task. My goal is to enumerate all the users who have eligible or permanent role assignments. I think the answer may be that if a user is in the eligible list, and also in the role assignment list, for the same role, then you can assume that the role assignment came from activation, but that doesn’t really seem very satisfactory.
Thanks Matt. The script is a bit outdated by now, I don’t even know if it runs with the “V2” Graph SDK. I’ll update it at some point 🙂
To further address your comment – neither the Get-MgRoleManagementDirectoryRoleAssignment nor the Get-MgRoleManagementDirectoryRoleEligibilitySchedule cmdlet returns sufficient information in order to determine whether a given (eligible) role assignment is currently activated. You can get this information via Get-MgRoleManagementDirectoryRoleAssignmentScheduleInstance, should be easy enough to add to the next iteration of the script.
Hi, thks for your great work. do you know why i dont see the eligible assignements ?
Seems they made some changes and you can no longer use $expand=* on the /v1.0 endpoint. Try using /beta, should work there. I’ll update the script when I get some time.
I’ve updated the script, let me know if you are still having issues.
Awesome, thank you very much.
Merci merci merci !!! Thanks thanks thanks !!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .

How To Add Azure AD Roles Using PowerShell With PIM
If you recall a while back we published an article to Get PIM Role Assignment Status For Azure AD Using Powershell , and today we’re going to build on top of that to add Azure AD Roles Using PowerShell
The goal here is to eliminate adding people using the Azure portal and use a method that’s more scalable and automatable. Because who doesn’t love automation right? The script I’m going to share with you today leverages the concept of just in time access using Azure AD Privilege Identity Management (PIM) .
Requirements
In order for the script to run successfully you will need to have the following in place.
- Azure AD P2 License for PIM Use
- Privileged Role Administrator -or Global Administrator to grant permissions
- AzureADPreview Powershell Module
Powershell 5+ would be preferred and I want to emphasize the AzureAdPreview Module (not AzureAD) as this has the commands we’re looking for.
Script Parameters
Userprincipalname.
Specify the UserPrincipalName for the user you want to add roles for.
Specify the RoleName you want to add. Tab-Completion is enabled to ensure roles are accurate.
By default it will use the TenantId from your current session. If you’re connected to a multi-tenant, you can specify the tenant here.
DurationInMonths
Set how long you would like to add the role for. Default is 48 months (4 years)
TicketNumber
Add a ticket number if needed for auditing purposes. “Justification” can also be used in lieu of “TicketNumber”
Add Azure AD Roles Using PowerShell With PIM Eligible Assignment
Now that we know what’s needed, let’s move on to the actual script.
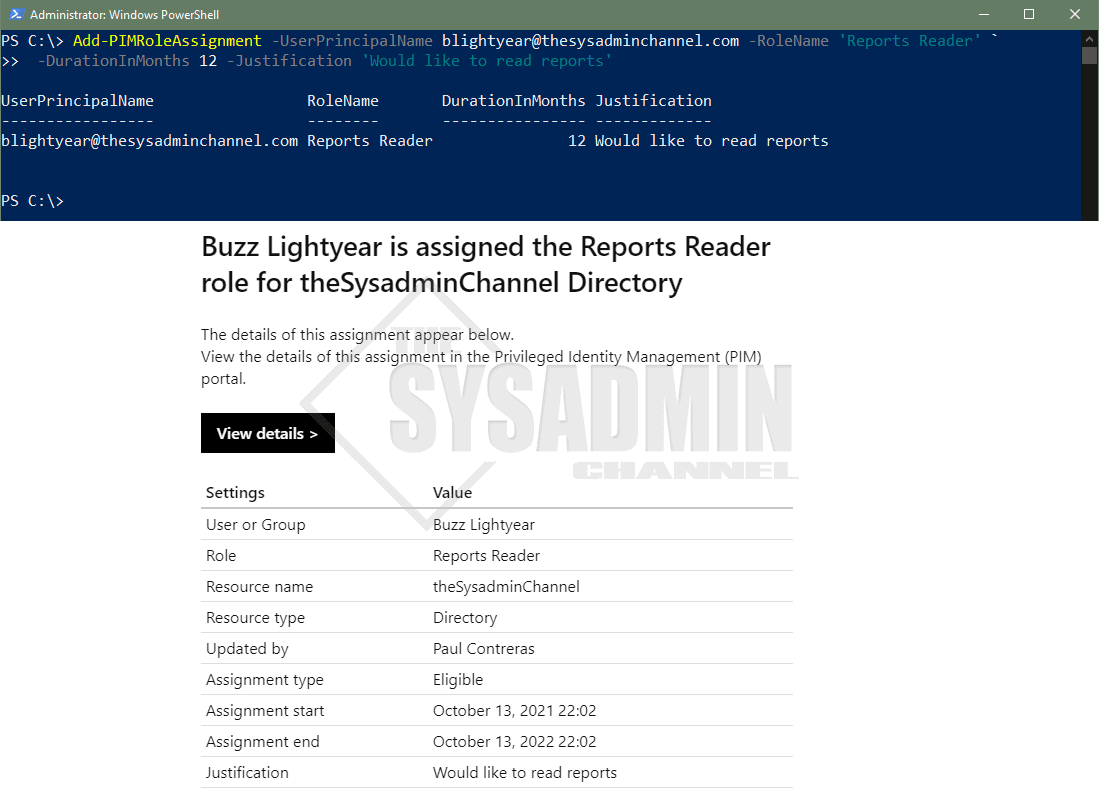
So there you have it, we’re able to add Azure AD Roles Using PowerShell to ensure Just in time access with Privilege Identity Manegment (PIM). Hopefully this was informative and you’re able to use it in your environment.
If you’re interested in more Powershell scripts, be sure to check out our personal Powershell Gallery full of real world, useful scripts just like this one.
Paul Contreras
Hi, my name is Paul and I am a Sysadmin who enjoys working on various technologies from Microsoft, VMWare, Cisco and many others. Join me as I document my trials and tribulations of the daily grind of System Administration.
To permanently assign a role, leave off the duration when calling the Function: Add-PIMRoleAssignment -UserPrincipalName ‘ [email protected] ’ -RoleName ‘SharePoint Administrator’ -Justification ‘TicketNumber’
and amend the end date to be: $Schedule.EndDateTime = $null
This worked for me.
This script is very useful for me, many thanks for sharing.
I’ve tried to adapt for my usage but wasn’t quite successfully. how we can set the duration to be permanently eligible ?
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *

List Eligible Entra ID PIM Assignments

- Kaido Järvemets
- June 26, 2024
As organizations grow and adopt cloud services, managing role assignments in Entra ID becomes critical. Role assignments are necessary to grant access to resources and to delegate administrative privileges. However, it’s important to ensure that only the right users have access to the right resources and that the access is properly monitored and audited. In this blog post, we’ll show you how to audit eligible Entra ID role assignments using PowerShell.
Entra ID offers a feature called Privileged Identity Management (PIM) , which provides time-based and approval-based role activation, auditing, and reporting. PIM allows you to assign eligible roles to users and groups for a limited duration of time and review audit logs of role activations and deactivations. In this post, we’ll focus on auditing eligible roles , which are roles that users or groups are eligible to activate but haven’t yet.
It’s important to periodically audit role assignments in Entra ID to ensure that only the necessary permissions are granted to the right users, groups, or applications. In this blog post, we will show you how to use PowerShell and Microsoft Graph API to audit only the eligible Entra ID role assignments.
You can read my previous post Audit Entra ID Privileged Identity Management Role Settings – Kaido Järvemets (kaidojarvemets.com)
Prerequisites:
- Entra ID Global Administrator
- Latest Microsoft Graph PowerShell module
- PowerShell 7.x
- Visual Studio Code
Step 1: Install Microsoft.Graph PowerShell Module
First we need to install the Microsoft Graph PowerShell module:
Step 2: Define the desired permission scopes
We need to define the permission scopes required to access role management information in Entra ID. The following scopes are required to retrieve information about eligible role assignments:
If you are unsure how to define the permissions scope for a particular command, you can try using the Find-MgGraphCommand cmdlet. While this command may no t provide all the information you need, it can still give you some helpful hints.
Step 3: Connect to Microsoft Graph API
To connect to the Microsoft Graph API run the following command:
Step 4: Get eligible role assignments
We can use the Get-MgRoleManagementDirectoryRoleEligibilityScheduleInstance cmdlet to retrieve eligible role assignments. Eligible role assignments are those that meet the following conditions:
- The role is a privileged role
- The role is assigned to a user or group with an active role assignment
- The user or group has a P2 license assigned
Here’s the PowerShell script to retrieve eligible role assignments:
Auditing Entra ID PIM roles is a critical task to ensure proper access controls and maintain a secure environment. By using PowerShell and the Microsoft Graph API, you can quickly and easily retrieve information about role assignments.
If you haven’t yet performed an assessment of your Entra ID environment, now is the time to do so. Regular assessments can help you identify potential security risks and implement appropriate controls to mitigate them. So, take action today and conduct an Entra ID assessment to ensure the security of your organization’s digital assets.
Leave a Reply Cancel reply
You must be logged in to post a comment.
Table of Contents
- September 4, 2024

WARNING: Don’t Manage Another Server Without This Azure Arc Training!
- October 31, 2024
One-Day Training on Azure Administrative Model: Secure Your Entra Tenant
- December 10, 2024

One-Day Training on Mastering Azure Update Manager
You might also like....

Windows LAPS PowerShell Commands

Maximizing Your Security with Azure Update Management

New Video Tutorial: Mastering Restricted Management Administrative Units in Entra ID
Ready to get started.

FOLLOW ME ON
AAD Support Notes
Random thoughts from an aad support engineer, automating azure privileged identity management (pim) with powershell.
On a recent support case we had a customer who was trying to automate Privileged Identity Management (PIM) role assignments for Azure Resources with PowerShell. We could not find any public end to end documentation on the syntax to make this work. After some trial and error we found the following syntax works.
NOTE: PIM can assign both Azure AD roles and Azure resource roles so both scenarios are shown below. Additionally, make sure you have the latest version of AzureADPreview module installed .
Assigning Azure AD roles
For this scenario there is a public doc explaining the syntax which can be found at PowerShell for Azure AD roles in Privileged Identity Management . For roleDefinitionID you can also look these IDs up on Azure AD built-in roles doc
PowerShell code example:
Assigning Azure Resource Roles
For Azure Resource roles I could not find any end to end public doc examples but after trial and error the below steps were confirmed to work.
NOTE: The additional cmds compared to Azure AD role scenario are to convert ARM subscription IDs and ARM role IDs into their PIM resource IDs. For roleDefinitionID you can also look up built-in role IDs on Azure built-in roles doc if you are using custom roles, you can look these up in Azure Portal -> Subscription blade -> Access Control -> Roles
Leave a Reply Cancel reply
You must be logged in to post a comment.

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell

Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...

How to Export All Entra PIM Roles with Microsoft Graph PowerShell
- Post author: Daniel Bradley
- Post category: Microsoft Graph / PowerShell
- Post last modified: April 26, 2024
- Reading time: 5 mins read
Microsoft Entra Privileged Identity Management (PIM) is a fantastic tool for managing and monitoring access to resources in your environment. However, naturally, over time, active and eligible PIM assignments can build up, and you may need to programmatically export a top-level view of all assignments to validate if they are still necessary or to at least report on them.
In this tutorial I am going to show you how to programmatically use Microsoft Graph PowerShell to Export a report of all PIM assignments, I will also show you how to export a similar report from the portal.
Page Contents
Pre-requisites
- How to export all PIM roles using the Azure AD portal
How to export all PIM roles using Microsoft Graph PowerShell
To export the PIM roles in this tutorial you must ensure you have the Microsoft Graph modules installed. Check out my tutorial here: How To Install the Microsoft Graph PowerShell Module which details how to install and upgrade the Microsoft Graph PowerShell modules.
As well as this, to grant consent to Microsoft Graph in Microsoft Entra you will need to log in interactively in the script as a global admin account, however, the session will only be active for the permissions defined in this scope of this script (RoleManagement.Read.Directory and Directory.Read.All).
How to export all PIM roles using the Microsoft Entra portal
If you like the simplicity of using the Web GUI to complete this task, you can use the Identity Governance portal in Microsoft Entra to export the same report. Follow the below steps to export the PIM roles through the Microsoft Entra portal:
2. From the menu, select Identity Governance > Priviledged Identity Management
3. Under the Manage heading, select Assignments
4. Select Export the when the option appears, Select Download
5. Your report will look like the following:
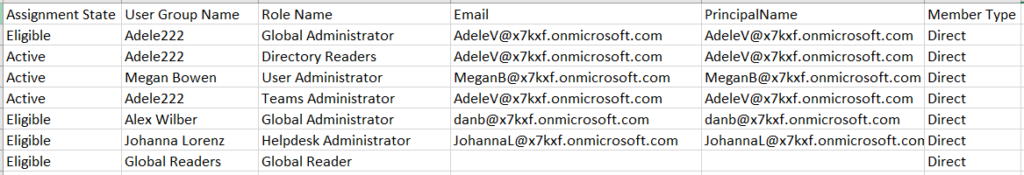
I have written the script below for this tutorial to gather all eligible and active PIM role assignments and bring the relevant information into a similar report. Start by opening Notepad or PowerShell ISE and copying the code below. Paste it into your editor, make any necessary modifications, such as the export path and run the script in PowerShell to create the PIM role report.
Daniel Bradley
Leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
Use code: MGP15 for 15% off the Microsoft Graph PowerShell for Administrators book!
Enable PIM role with PowerShell
At my customer we are using Privileged Identity Management (PIM) for all admin related tasks, no employee has standing access within the company.
What is PIM
Let’s first start by explaining Privileged Identity Management. It is a service that is available in Azure AD and is part of Azure AD Plan 2. For a user to use it, they need this plan enabled. PIM makes it possible to give a user the privilege to elevate his or her access rights for a preset amount of time to a higher role such as User Administrator or SharePoint Administrator. PIM gives access to about 35 different roles in Office 365 and Azure resources where the user is by default a reader and can elevate it to be an owner of a resource (group).
Enabling a PIM role is done by going to the Azure Portal and select the role you want to elevate. You need to do this for every role separately. In our team, we have members that need to elevate their account daily to be a SharePoint and User administrator, so they need to do this daily. After enabling they need to sign out and sign in again to make sure the roles are activated. A colleague made a script to enable these two roles, but you were not able to set different durations and reasons for the role, so in the audit logs it was the same every day.
That was for me a reason to create a complete script to enable any role with any duration with a reason you provide.
Prerequisites
To get started with PowerShell and PIM you need to install the module “Microsoft.Azure.ActiveDirectory.PIM.PSModule” and can be found in the PowerShell Gallery.
Enabling PIM role with PowerShell
Enabling is very straightforward and a two-step process. First you need to connect to PIM, and second, you need to enable the role
Connect to PIM is done with the command: “Connect-PimService”
Enabling the role is done with the command “Enable-PrivilegedRoleAssignment”, and you need to give the ID of the role or the PrivilegedRoleAssignment object.
A complete script is on my GitHub repository: https://github.com/worktogether-tech/PowerShellScripts/blob/master/Enable-PIMrole.ps1
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Tutorial: Assign Microsoft Entra roles in Privileged Identity Management using Microsoft Graph PowerShell
- 4 contributors
The Microsoft Entra Privileged Identity Management (PIM) service allows role administrators to make time-bound admin role assignments. Additionally, privileged role administrators can make users eligible for Microsoft Entra admin roles. An eligible administrator can activate the role when they need the role, and the permissions expire once the eligible administrator is done.
In this tutorial, you'll create, extend, activate, deactivate, and remove eligible role assignments.
Prerequisites
To successfully complete this tutorial, make sure you have the required prerequisites:
Microsoft Graph PowerShell SDK is installed. Follow the Install the Microsoft Graph PowerShell SDK guide to install the SDK.
To use the Microsoft Entra Privileged Identity Management, you must have one of the following licenses:
- Microsoft Entra ID P2
- Enterprise Mobility + Security (EMS) E5 license
Microsoft Graph PowerShell using a Privileged Role Administrator role and the appropriate permissions. For this tutorial, the RoleManagement.ReadWrite.Directory delegated permission is required. To set the permissions in Microsoft Graph PowerShell, run;
Select Consent on behalf of your organization before accepting in the sign-in dialog box.
Step 1: Create a user account
In this step, you'll create a user who will be the target of the admin assignments. When you make these calls, change contoso.onmicrosoft.com to the domain name of your tenant. You can find tenant information on the Microsoft Entra overview page.
Step 2: Create an eligible role assignment for the user for 10 hours
In PIM, there are two types of role assignments:
- Eligible role assignments - The user doesn't have access to permissions defined for that role. They can potentially activate it to get access to all the permissions.
- Active role assignments - When a role is active, the user has access to all permissions defined for that role, for the defined duration.
To create an eligible role assignment, you need the following values:
| Value | Description |
|---|---|
| Identifier of the principal to which the assignment is being granted, for example, a user or a group. For groups, they must be assignable to roles. That is, the property of the group is set to . | |
| Identifier of the the assignment is for. It's read only | |
| Identifier of the directory object representing the scope of the assignment. Use for tenant-wide scope. Use to limit the scope to an application only. | |
| The type of operation on the role assignment. The possible values are: • : for administrators to assign roles to users or groups. • : for administrators to remove users or groups from roles. • : for administrators to change existing role assignments. • : for administrators to extend expiring assignments. • : for administrators to renew expired assignments. • : for users to activate their assignments. • : for users to deactivate their active assignments. • : for users to request to extend their expiring assignments. • : for users to request to renew their expired assignments. | |
| A message provided by users and administrators when creating the request about why it's needed. | |
| The schedule object of the role assignment request. This property isn't required when the action is or . |
To get all the all eligible role assignments for this user, run:
Step 3: Extend eligible role assignment for the user to one day
As the admin, you can extend the eligible role assignment created in step 2. To extend the eligible role assignment, run:
Step 4: User activates eligible assignment for 1 hour
An active role assignment allows the user to gain access to all permissions defined for that role for the defined duration.
There are two ways to create active role assignments:
- An admin can directly create an active role assignment for a user without first creating an eligible role assignment.
- A user can activate an existing eligible role assignment.
In this step, you'll activate the eligible role assignment created in step 2. To complete this step, sign in to the terminal as the user we created in step 1.
To get the existing active role assignments for this user, run:
Step 5: User deactivates an active role assignment
To deactivate an active role assignment, you need the following values:
| Value | Description |
|---|---|
| Identifier of the principal to which the assignment is being granted, for example, a user or a group. For groups, they must be assignable to roles. That is, the property of the group is set to . | |
| Identifier of the UnifiedRoleDefinition the assignment is for. It's read only. is a collection of permissions listing the operations, such as read, write, and delete that can be performed by an RBAC provider, as part of Microsoft 365 RBAC role management. | |
| Identifier of the directory object representing the scope of the assignment. Use for tenant-wide scope. Use to limit the scope to an application only. | |
| Set it to . | |
| A message provided by users and administrators when creating the request about why it's needed. |
The ScheduleInfo value isn't required.
Step 6: Admin removes an eligible assignment
To remove an eligible role assignment, you need the following values:
| Value | Description |
|---|---|
| Identifier of the principal to which the assignment is being granted. For example, a user or a group. For groups, they must be assignable to roles. That is, the property of the group is set to . | |
| Identifier of the UnifiedRoleDefinition the assignment is for. It's read only. | |
| Identifier of the directory object representing the scope of the assignment. Use for tenant-wide scope. Use to limit the scope to an application only. | |
| Set to . | |
| A message provided by users and administrators when creating the request about why it's needed. |
- Manage PIM policies using Microsoft Graph PowerShell
Was this page helpful?
Additional resources
Get the Reddit app
A companion sub to /r/sysadmin where redditors can share their blog articles, news links and information useful or interesting to fellow technology professionals.
Get PIM Role Assignment Status For Azure AD Using Powershell
By continuing, you agree to our User Agreement and acknowledge that you understand the Privacy Policy .
Enter the 6-digit code from your authenticator app
You’ve set up two-factor authentication for this account.
Enter a 6-digit backup code
Create your username and password.
Reddit is anonymous, so your username is what you’ll go by here. Choose wisely—because once you get a name, you can’t change it.
Reset your password
Enter your email address or username and we’ll send you a link to reset your password
Check your inbox
An email with a link to reset your password was sent to the email address associated with your account
Choose a Reddit account to continue
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
Entra ID PIM - Powershell + Graph Rest API - create role assignments
I need to create powershell code for adding PIM role assignments on azure subscription scope. I have prepared below presented code:
I am using $auth_token , my registered application is added to Global Administrator group in EntraID. I am trying to use Microsoft Graph Rest API (MS documentation - Graph rest API documentation ). I have code prepared:
Once I run the script I am still facing error code
- azure-active-directory
- azure-powershell
- azure-rest-api
- Can you decode the access token and check if PrivilegedAccess.ReadWrite.AzureADGroup API permissions is present? – Rukmini Commented Oct 31, 2023 at 5:04
- Application permissions are not supported to perform the action. Hence user interaction is needed to create the role assignments. Use Connect-MgGraph -Scopes "PrivilegedAccess.ReadWrite.AzureADGroup" and run this script learn.microsoft.com/en-us/graph/api/… – Rukmini Commented Oct 31, 2023 at 7:30
- OK, what should I pass under this variable --> $privilegedAccessId ? – tester81 Commented Oct 31, 2023 at 9:40
- Refer this script in this QnA learn.microsoft.com/en-us/answers/questions/257384/… by ravishekharreddy yanamala – Rukmini Commented Oct 31, 2023 at 9:45
- Pass azureResources as $privilegedAccessId and try – Rukmini Commented Oct 31, 2023 at 9:48
Note that: To create governance role assignment request for the group, the application or the user must have PrivilegedAccess.ReadWrite.AzureADGroup delegated API permission.
- Application permissions are not supported to perform the action as per the MsDoc . Hence user interaction is needed to create the role assignments.
- Hence, if you want to use the Azure AD Application to create roles then use of access on behalf of a user flow to generate access token.
- Make sure the access token contains the required scopes.
I assigned the user Privileged role Administrator like below:

And directly use the below script to create role assignments:

If still the issue persists, change azureResources with aadroles as suggested by SaurabhSharma in this SO Thread
I tried to create the governance role assignment request via Rest API with above permissions using access token and roles and the request is successful:

Graph api call to make AAD role assignment request not working - Microsoft Q&A by Siva-kumar-selvaraj
- Thanks for these hints, but still got the same error, i did all you suggested, tried via poweshell and rest api and still 403 error message. – tester81 Commented Nov 1, 2023 at 7:04
- What are you passing for resourceId? Try passing tenantid instead of subscriptionid? – Rukmini Commented Nov 1, 2023 at 7:07
- Tried, and the same error. I am passing $roleDefinitionId = "RBAC built in role like Contributor ID", $resourceId = "tenant or subscription ID", $subjectId = "My test Entra ID group Object ID" – tester81 Commented Nov 2, 2023 at 9:24
- Did you assign Privileged role Administrator role to the user? – Rukmini Commented Nov 2, 2023 at 9:25
- My user is added to Global Administrator and Privileged role Administrator Entra ID roles. – tester81 Commented Nov 2, 2023 at 9:26
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged azure-active-directory azure-powershell azure-rest-api or ask your own question .
- The Overflow Blog
- Where does Postgres fit in a world of GenAI and vector databases?
- Featured on Meta
- We've made changes to our Terms of Service & Privacy Policy - July 2024
- Bringing clarity to status tag usage on meta sites
- What does a new user need in a homepage experience on Stack Overflow?
- Feedback requested: How do you use tag hover descriptions for curating and do...
- Staging Ground Reviewer Motivation
Hot Network Questions
- Running fully sheathed romex through a media box
- Flyback Controller IC identification
- Trying to find an old book (fantasy or scifi?) in which the protagonist and their romantic partner live in opposite directions in time
- How would increasing atomic bond strength affect nuclear physics?
- Using "no" at the end of a statement instead of "isn't it"?
- Philosophies about how childhood beliefs influence / shape adult thoughts
- Optimal Bath Fan Location
- Does the Greek used in 1 Peter 3:7 properly translate as “weaker” and in what way might that be applied?
- Parse Minecraft's VarInt
- I don’t know what to buy! Again!
- Is having negative voltages on a MOSFET gate a good idea?
- How to establish this generalization rule in sequent calculus for First Order Logic?
- Simple casino game
- Passport Carry in Taiwan
- Dress code for examiner in UK PhD viva
- What is the significance of bringing the door to Nippur in the Epic of Gilgamesh?
- Story where character has "boomerdisc"
- Who was the "Dutch author", "Bumstone Bumstone"?
- My colleagues and I are travelling to UK as delegates in an event and the company is paying for all our travel expenses. what documents are required
- How to attach a 4x8 plywood to a air hockey table
- What was I thinking when I made this grid?
- What to call a test that consists of running a program with only logging?
- What does it say in the inscriptions on Benjamin's doorway; A Canticle for Leibowitz
- Why does Russia strike electric power in Ukraine?

IMAGES
COMMENTS
Get PIM Role Assignment Status For Azure AD Using Powershell. By using this script you'll be able to see all the people who have standing access as well as PIM eligible roles. This will check if a user is added to PIM or standing access. For updated help and examples refer to -Online version.
To get all AAD roles including their eligible users using PowerShell: Thanks to @thesysadminchannel, By referring to this article, we can get all AAD roles including their eligible users and PIM Assignment Status. I have made a few changes in the portion of the param code block and execute the Begin & Process procedure calls in the same manner as mentioned in that article.
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To determine what resources users, groups, service principals, or managed identities have access to, you list their role assignments. This article describes how to list role assignments using Azure PowerShell.
Step 1: List policies. Step 2: Get policy assignments. Step 3: Get policy rules. Show 2 more. The Microsoft Entra Privileged Identity Management (PIM) service allows role administrators to make time-bound admin role assignments. Each role has a group of settings that manage it. For example, activation and assignment settings.
Recently my role assignments in Azure AD were switched from permanent to eligible ones. This is part of PIM - Privileged Identity Management, you can read more about it on MS Docs: To activate your eligible assignment you can use Azure Portal, Graph API, and PowerShell. The activation in the portal and Graph API is described on MS Docs:
Generate a report of Azure AD role assignments via the Graph API or PowerShell. A while back, I published a short article and script to illustrate the process of obtaining a list of all Azure AD role assignments. The examples therein use the old MSOnline and Azure AD PowerShell modules, which are now on a deprecation path.
Add Azure AD Roles Using PowerShell With PIM Eligible Assignment. Now that we know what's needed, let's move on to the actual script. This add a user to a PIM Role in Azure AD. For updated help and examples refer to -Online version. Now when I look at the Azure AD Roles for the role name I just granted, we can see that Buzz now has an ...
Conclusion. Auditing Entra ID PIM roles is a critical task to ensure proper access controls and maintain a secure environment. By using PowerShell and the Microsoft Graph API, you can quickly and easily retrieve information about role assignments. If you haven't yet performed an assessment of your Entra ID environment, now is the time to do so.Regular assessments can help you identify ...
You could just simply run the command as is to interactively select a role and input activation time and reason. # Enable one of your Azure AD PIM roles. Enable-DCAzureADPIMRole. Or you could do the same but with multiple selected roles via the -RolesToActivate parameter. This is great for times when you need multiple roles to complete your job.
On a recent support case we had a customer who was trying to automate Privileged Identity Management (PIM) role assignments for Azure Resources with PowerShell. We could not find any public end to end documentation on the syntax to make this work. ... For this scenario there is a public doc explaining the syntax which can be found at PowerShell ...
To assign a role, you might need to specify the unique ID of the object. The ID has the format: 11111111-1111-1111-1111-111111111111. You can get the ID using the Azure portal or Azure PowerShell. User. For a Microsoft Entra user, get the user principal name, such as [email protected] or the user object ID.
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function. Written by Vukasin Terzic.
To export the PIM roles in this tutorial you must ensure you have the Microsoft Graph modules installed. Check out my tutorial here: How To Install the Microsoft Graph PowerShell Module which details how to install and upgrade the Microsoft Graph PowerShell modules. As well as this, to grant consent to Microsoft Graph in Microsoft Entra you will need to log in interactively in the script as a ...
PowerShell is a cross-platform (Windows, Linux, and macOS) automation tool and configuration framework optimized for dealing with structured data (e.g. JSON, CSV, XML, etc.), REST APIs, and object models.
At my customer we are using Privileged Identity Management (PIM) for all admin related tasks, no employee has standing access within the company. What is PIM Let's first start by explaining Privileged Identity Management. It is a service that is available in Azure AD and is part of Azure AD Plan 2. For a user to use it, they need this plan enabled. PIM makes it possible to give a user the ...
In PIM, there are two types of role assignments: Eligible role assignments - The user doesn't have access to permissions defined for that role. They can potentially activate it to get access to all the permissions. Active role assignments - When a role is active, the user has access to all permissions defined for that role, for the defined ...
Get PIM Role Assignment Status For Azure AD Using Powershell. thesysadminchannel. comments sorted by Best Top New Controversial Q&A Add a Comment More posts you may like. r/activedirectory • FSMO transfer issues with Schema Operations Master ... Powershell Script for Admin on all machines via RMM application.
I'm having a hard time pulling PIM assignments for every child resource within a subscription in Azure. I'm currently using Get-AzureADMSPrivilegedRoleAssignment from ...
I'm trying to automate the activation of my PIM role for Azure resources via Powershell or REST API and I can't seem to figure this out. ... If the status of the returned request object's status field is PendingApprovalProvisioning and the you pim configuration isn't requiring approval, you can trigger a self-approved approval by including ...
Hence user interaction is needed to create the role assignments. Hence, if you want to use the Azure AD Application to create roles then use of access on behalf of a user flow to generate access token. Make sure the access token contains the required scopes. I assigned the user Privileged role Administrator like below: