- Essay Topic Generator
- Essay Grader
- Reference Finder
- AI Outline Generator
- Paragraph Expander
- Essay Expander
- Literature Review Generator
- Thesis Generator
- Text Editing Tools
- AI Rewording Tool
- AI Sentence Rewriter
- AI Article Spinner
- AI Grammar Checker
- Spell Checker
- PDF Spell Check
- Paragraph Checker
- Free AI Essay Writer
- Paraphraser
- Grammar Checker
- Citation Generator
- Plagiarism Checker
- AI Detector
- AI Essay Checker
- Proofreading Service
- Editing Service
- AI Writing Guides
- AI Detection Guides
- Citation Guides
- Grammar Guides
- Paraphrasing Guides
- Plagiarism Guides
- Summary Writing Guides
- STEM Guides
- Humanities Guides
- Language Learning Guides
- Coding Guides
- Top Lists and Recommendations
- AI Detectors
- AI Writing Services
- Coding Homework Help
- Citation Generators
- Editing Websites
- Essay Writing Websites
- Language Learning Websites
- Math Solvers
- Paraphrasers
- Plagiarism Checkers
- Reference Finders
- Spell Checkers
- Summarizers
- Tutoring Websites
- Essay Checkers
- Essay Topic Finders

Most Popular
13 days ago
JustDone AI Review
Education department wants to police online education more control over remote learning is coming, how redditors spend time between classes, kamala harris picks tim walz as running mate but can he really bring the financial interest back to education.
12 days ago
The Summer I Turned Pretty Summary
Digital privacy & cybersecurity thesis statement examples.
freepik.com

In an age of increasing digital reliance, digital privacy and cybersecurity are paramount topics that require meticulous academic exploration. Thesis statements in this realm should articulate clear and specific research objectives. Below are examples of good and bad thesis statements, alongside analyses delineating their respective merits and flaws.
Good Thesis Statement Examples
Specific and Clear
- Good: “This thesis will scrutinize the efficacy of end-to-end encryption in safeguarding users’ privacy on social media platforms.”
- Bad: “Encryption is crucial for privacy on social media.”
The good example is specific, pinpointing the type of encryption and the context (social media privacy). In contrast, the bad example is general, lacking clarity on encryption type and application.
Arguable and Debatable
- Good: “The adoption of GDPR has significantly enhanced digital privacy protection for EU citizens, albeit at the expense of restricting certain online services.”
- Bad: “GDPR has changed digital privacy.”
The good statement provides a debatable argument, acknowledging GDPR’s impact on privacy and online services. The bad example is factual but lacks a defined stance or specific areas of impact.
Researchable and Measurable
- Good: “The thesis explores the correlation between the increase in remote work and the rise in phishing attacks during the COVID-19 pandemic.”
- Bad: “Cybersecurity threats have increased with remote work.”
The good example is researchable, measurable, and time-bound, providing clear variables and context. The bad statement, while true, lacks specificity and measurable variables.
Bad Thesis Statement Examples
Overly Broad: “Cybersecurity is important for protecting privacy.”
While true, this statement is excessively broad and doesn’t pinpoint specific cybersecurity aspects or privacy areas for exploration.
Lack of Clear Argument: “Digital privacy matters to everyone.”
This statement, though factual, doesn’t present a clear argument or specific area for research, serving poorly as a research guide.
Unmeasurable and Unresearchable: “Without privacy, there’s no freedom on the internet.”
While philosophically valid, this statement isn’t easily measurable or researchable, lacking specificity for empirical investigation.
Developing a strong thesis statement for digital privacy and cybersecurity research is imperative, serving as the foundation for your scholarly endeavor. Effective thesis statements are precise, arguable, and conducive to research, guiding both the researcher and readers through a focused academic inquiry. Conversely, ineffective ones are often vague, lacking clear arguments, and not easily researchable. By considering these examples and analyses, students can craft thesis statements that are not only academically sound but also pivotal for exploring the critical issues of digital privacy and cybersecurity.
Follow us on Reddit for more insights and updates.
Comments (0)
Welcome to A*Help comments!
We’re all about debate and discussion at A*Help.
We value the diverse opinions of users, so you may find points of view that you don’t agree with. And that’s cool. However, there are certain things we’re not OK with: attempts to manipulate our data in any way, for example, or the posting of discriminative, offensive, hateful, or disparaging material.
Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
More from Essay About Privacy: Best Samples and Examples

The Ethical Implications and Societal Impact of Biometric Surveillance Technology

Ethical Implications of Genetic Testing and Personal Data Sharing
Balancing personal health details with privacy considerations. essay sample and references.
Remember Me
Is English your native language ? Yes No
What is your profession ? Student Teacher Writer Other
Forgotten Password?
Username or Email
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
- How to Write a Thesis Statement | 4 Steps & Examples
How to Write a Thesis Statement | 4 Steps & Examples
Published on January 11, 2019 by Shona McCombes . Revised on August 15, 2023 by Eoghan Ryan.
A thesis statement is a sentence that sums up the central point of your paper or essay . It usually comes near the end of your introduction .
Your thesis will look a bit different depending on the type of essay you’re writing. But the thesis statement should always clearly state the main idea you want to get across. Everything else in your essay should relate back to this idea.
You can write your thesis statement by following four simple steps:
- Start with a question
- Write your initial answer
- Develop your answer
- Refine your thesis statement
Instantly correct all language mistakes in your text
Upload your document to correct all your mistakes in minutes
Table of contents
What is a thesis statement, placement of the thesis statement, step 1: start with a question, step 2: write your initial answer, step 3: develop your answer, step 4: refine your thesis statement, types of thesis statements, other interesting articles, frequently asked questions about thesis statements.
A thesis statement summarizes the central points of your essay. It is a signpost telling the reader what the essay will argue and why.
The best thesis statements are:
- Concise: A good thesis statement is short and sweet—don’t use more words than necessary. State your point clearly and directly in one or two sentences.
- Contentious: Your thesis shouldn’t be a simple statement of fact that everyone already knows. A good thesis statement is a claim that requires further evidence or analysis to back it up.
- Coherent: Everything mentioned in your thesis statement must be supported and explained in the rest of your paper.
Receive feedback on language, structure, and formatting
Professional editors proofread and edit your paper by focusing on:
- Academic style
- Vague sentences
- Style consistency
See an example
The thesis statement generally appears at the end of your essay introduction or research paper introduction .
The spread of the internet has had a world-changing effect, not least on the world of education. The use of the internet in academic contexts and among young people more generally is hotly debated. For many who did not grow up with this technology, its effects seem alarming and potentially harmful. This concern, while understandable, is misguided. The negatives of internet use are outweighed by its many benefits for education: the internet facilitates easier access to information, exposure to different perspectives, and a flexible learning environment for both students and teachers.
You should come up with an initial thesis, sometimes called a working thesis , early in the writing process . As soon as you’ve decided on your essay topic , you need to work out what you want to say about it—a clear thesis will give your essay direction and structure.
You might already have a question in your assignment, but if not, try to come up with your own. What would you like to find out or decide about your topic?
For example, you might ask:
After some initial research, you can formulate a tentative answer to this question. At this stage it can be simple, and it should guide the research process and writing process .
Here's why students love Scribbr's proofreading services
Discover proofreading & editing
Now you need to consider why this is your answer and how you will convince your reader to agree with you. As you read more about your topic and begin writing, your answer should get more detailed.
In your essay about the internet and education, the thesis states your position and sketches out the key arguments you’ll use to support it.
The negatives of internet use are outweighed by its many benefits for education because it facilitates easier access to information.
In your essay about braille, the thesis statement summarizes the key historical development that you’ll explain.
The invention of braille in the 19th century transformed the lives of blind people, allowing them to participate more actively in public life.
A strong thesis statement should tell the reader:
- Why you hold this position
- What they’ll learn from your essay
- The key points of your argument or narrative
The final thesis statement doesn’t just state your position, but summarizes your overall argument or the entire topic you’re going to explain. To strengthen a weak thesis statement, it can help to consider the broader context of your topic.
These examples are more specific and show that you’ll explore your topic in depth.
Your thesis statement should match the goals of your essay, which vary depending on the type of essay you’re writing:
- In an argumentative essay , your thesis statement should take a strong position. Your aim in the essay is to convince your reader of this thesis based on evidence and logical reasoning.
- In an expository essay , you’ll aim to explain the facts of a topic or process. Your thesis statement doesn’t have to include a strong opinion in this case, but it should clearly state the central point you want to make, and mention the key elements you’ll explain.
If you want to know more about AI tools , college essays , or fallacies make sure to check out some of our other articles with explanations and examples or go directly to our tools!
- Ad hominem fallacy
- Post hoc fallacy
- Appeal to authority fallacy
- False cause fallacy
- Sunk cost fallacy
College essays
- Choosing Essay Topic
- Write a College Essay
- Write a Diversity Essay
- College Essay Format & Structure
- Comparing and Contrasting in an Essay
(AI) Tools
- Grammar Checker
- Paraphrasing Tool
- Text Summarizer
- AI Detector
- Plagiarism Checker
- Citation Generator
A thesis statement is a sentence that sums up the central point of your paper or essay . Everything else you write should relate to this key idea.
The thesis statement is essential in any academic essay or research paper for two main reasons:
- It gives your writing direction and focus.
- It gives the reader a concise summary of your main point.
Without a clear thesis statement, an essay can end up rambling and unfocused, leaving your reader unsure of exactly what you want to say.
Follow these four steps to come up with a thesis statement :
- Ask a question about your topic .
- Write your initial answer.
- Develop your answer by including reasons.
- Refine your answer, adding more detail and nuance.
The thesis statement should be placed at the end of your essay introduction .
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
McCombes, S. (2023, August 15). How to Write a Thesis Statement | 4 Steps & Examples. Scribbr. Retrieved August 13, 2024, from https://www.scribbr.com/academic-essay/thesis-statement/
Is this article helpful?
Shona McCombes
Other students also liked, how to write an essay introduction | 4 steps & examples, how to write topic sentences | 4 steps, examples & purpose, academic paragraph structure | step-by-step guide & examples, "i thought ai proofreading was useless but..".
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”
- Research article
- Open access
- Published: 05 June 2013
Internet safety education for youth: stakeholder perspectives
- Megan A Moreno 1 , 4 ,
- Katie G Egan 2 ,
- Kaitlyn Bare 1 ,
- Henry N Young 3 &
- Elizabeth D Cox 1
BMC Public Health volume 13 , Article number: 543 ( 2013 ) Cite this article
32k Accesses
28 Citations
1 Altmetric
Metrics details
Internet use is nearly ubiquitous among US youth; risks to internet use include cyberbullying, privacy violations and unwanted solicitation. Internet safety education may prevent these negative consequences; however, it is unclear at what age this education should begin and what group is responsible for teaching this topic.
Surveys were distributed to key stakeholders in youth safety education including public school teachers, clinicians, parents and adolescents. Surveys assessed age at which internet safety education should begin, as well as experiences teaching and learning internet safety. Surveys of adults assessed willingness to teach internet safety. Finally, participants were asked to identify a group whose primary responsibility it should be to teach internet safety.
A total of 356 participants completed the survey (93.4% response rate), including 77 teachers, 111 clinicians, 72 parents and 96 adolescents. Stakeholders felt the optimal mean age to begin teaching internet safety was 7.2 years (SD = 2.5), range 2-15. Internet safety was regularly taught by some teachers (20.8%), few clinicians (2.6%) and many parents (40.3%). The majority of teachers, clinicians and parents were willing to teach internet safety, but all groups surveyed identified parents as having primary responsibility for teaching this topic.
Conclusions
Findings suggest agreement among key stakeholders for teaching internet safety at a young age, and for identifying parents as primary teachers of this topic. Clinicians have a unique opportunity to support parents by providing resources, guidance and support.
Peer Review reports
While the internet has provided adolescents with numerous benefits, including increased social support, academic enrichment and worldwide cross-cultural interactions, there are concomitant risks to internet use [ 1 – 8 ]. The American Academy of Pediatrics’ (AAP) recent report on children’s social media use describes specific risks such as privacy violations and cyberbullying [ 9 ]. A previous study found that one-third of adolescents had given their internet password to friends and one-fourth were unaware that content uploaded online cannot be permanently deleted [ 1 ]. Cyberbullying, or internet harassment, impacts up to a third of youth and has been linked to a variety of health concerns, some as serious as suicidal ideation [ 10 – 15 ]. In addition, adolescents frequently display personal and identifiable information about themselves on the internet. These details may include their home location, revealing photographs, or descriptions of sexual behavior and substance use [ 16 – 18 ].
Internet safety is highly salient for today’s youth as they spend up to 10 hours a day using various forms of media [ 8 , 19 , 20 ]. The ever-increasing popularity of social media, including websites such as Facebook and Twitter, have contributed to youth’s time investment in the internet [ 7 ]. The vast majority of adolescents have internet access and most report daily use [ 21 , 22 ]. Several organizations, including the AAP, have offered expert advice regarding internet safety, but an evidence-based approach to educate youth about the dangers of being online does not currently exist [ 23 ]. Further, data to guide decisions about the age at which such education should begin, and who would have primary responsibility for teaching this topic are incomplete.
An ideal approach for teaching internet safety would likely involve a person or group who could reach most children in order to provide widespread dissemination of this knowledge. An ideal candidate would also have experience teaching about the internet or related safety issues, and be willing to invest in teaching this topic. Given that most US youth and adolescents attend public school, a first possibility is public school teachers. However, it is unclear at what grades and in which school subjects this material could be integrated into existing curricula. A second possibility is child health providers such as pediatricians or family medicine physicians. The AAP social media report argues that “pediatricians are in a unique position” to provide internet safety education [ 9 ]. Several resources exist to guide pediatricians in these discussions, but it is unclear whether pediatricians are comfortable in these discussions. Previous work has suggested that pediatrician’s performance of adolescent health behavior screening and prevention counseling regarding health risk behaviors is quite low [ 24 , 25 ]. A third potential candidate is the parent of the adolescent. While adults’ use of online media such as social networking sites continues to rise, data regarding parents’ comfort or experience with teaching internet safety remains elusive [ 26 ]. While all three groups undoubtedly should play a role in online safety education, it remains unclear which group is seen as holding primary responsibility among these stakeholders.
The purpose of this study was to investigate views of key stakeholders on internet safety education, including school teachers, clinicians who see children and adolescents, parents of adolescents, and adolescents themselves. Our goals were to investigate at what age internet safety education should begin, and to identify a primary candidate to teach this topic.
This study was conducted between July 1, 2009 and August 15, 2011 and received IRB approval from the University of Wisconsin Human Subjects Committee.
Setting and subjects
Participants in this study included public school teachers, health care providers who see children and adolescents, parents of adolescents, and adolescents themselves. School teachers were recruited from a summer continuing education conference within a public school district. This district includes 4 elementary schools, one middle and one high school. Inclusion criteria limited participants to teachers who taught kindergarten through 12 th grade within that public school district. Clinicians were recruited at a yearly regional continuing medical education conference; inclusion criteria limited participants to physicians (MDs and DOs), nurse practitioners (NPs), physician assistants (PAs), and nurses, all of whose practice included pediatric patients. Parents of adolescents were identified within a large general pediatric practice that includes 8 pediatric providers. Inclusion criteria for parents were that they had a child between the ages of 11 and 18 years. Adolescents (ages 11-18 years) were identified and recruited within this same large general pediatric practice. Most parents and teens were recruited as dyads. We did not exclude parents or teens who elected to participate in the study separately because we did not compare data between parents and teens.
Data collection and recruitment
In each recruitment setting, potentially eligible participants were approached by a research assistant. After explaining the study and obtaining consent, participants completed a paper survey. Survey respondents were provided a $5 gift card as compensation.
Survey design
The goals of the survey were to understand at what age internet safety education should begin, explore the experiences of adult participants in teaching online safety or the adolescents learning about this topic, and to identify a group who has primary responsibility for teaching this topic. Thus, we included all potential survey participants in the survey design process. Surveys were designed after a review of the literature and conversations with a panel of physicians, parents and researchers. Questions were pilot-tested first with a panel and then among teachers and adolescents. In the final survey items some words were modified to make the survey clear to all groups of participants. For example, among health care provider groups the question: “For how many years have you been in practice?” was changed for teacher groups to read: “For how many years have you been teaching?” All four surveys are included as Additional files 1 , 2 , 3 and 4 .
Data sources and variables
Participants provided demographic data including gender and age. Teachers were asked to disclose the grade levels they taught, subjects taught and years of teaching experience. Clinicians were asked to provide their training background (i.e. MD, NP), field of practice (Pediatrics, Family Practice) and years in practice. Parents provided their age, gender and the ages of their children. Adolescents were asked for their age, gender and grade in school.
Age to begin teaching internet safety
Teachers, clinicians, parents and adolescents were asked to provide at what age internet safety education should begin. An “other” option was presented for write-in answers.
Candidates to teach internet safety
In order to identify potential candidates to teach internet safety, participants were asked about previous experiences teaching or learning about internet safety. Then participants were asked for their own willingness to teach this subject and to identify an ideal primary candidate to teach this topic.
Experiences teaching internet safety
To describe experiences in providing internet safety education, teachers were asked how frequently they had ever taught internet safety education. Clinicians were asked how frequently they had ever counseled patients on this topic. Answer options included regularly, sometimes, never and never but plan to do so soon. Parents were asked about how frequently they talked with their child about internet safety: regularly, sometimes, never and never but plan to do so soon (Table 1 ).
Adolescents’ experiences learning about internet safety
Adolescents were asked ways in which they had learned about internet safety. A list of answer options was developed through review of the literature and the web and then piloted with several adolescents to ensure completeness. Answer options included learning from friends, siblings, parents, teachers and clinicians as well as learning by self-teaching. A write-in “other” option was also provided. Adolescents were allowed to choose all applicable answers from this list.
Willingness to teach internet safety
Teachers were asked whether or not they supported teaching internet safety education in public schools. Health care providers were asked whether or not they supported teaching internet safety education in provider offices (yes or no).
All groups, including teachers, clinicians, parents and adolescents were asked to select a candidate group whom they felt had primary responsibility for teaching internet safety to children and adolescents. Based on a review of current groups engaged in teaching this subject, answer options included churches, community groups, health care providers, law enforcement, parents and teachers. An “other” option was presented for write-in answers.
All statistical data analyses were conducted using STATA version 11.0 (Statacorp, College Station, TX). Descriptive statistics were calculated for survey responses. ANOVA was used to compare mean age to begin teaching between teachers, clinicians, parents and adolescents. Logistic regression was used to assess whether experience teaching internet safety was associated with years of career experience.
Participants
A total of 356 participants completed the survey (93.4% response rate), including 77 teachers, 111 clinicians, 72 parents and 96 adolescents. Teachers had an average of 14.8 (SD = 8.4) years of teaching experience. The subjects that teachers taught included: health, social studies, language arts/English, special education, health and technology/computer skills. Clinicians included 68 (61.3%) physicians, 16 (14.4%) nurse practitioners, 15 (13.5%) physician assistants and 8 (7.2%) nurses. Their practice background was mainly pediatrics (61.3%) and family practice (27.9%). Clinicians’ years of experience averaged 14.5 (SD = 10.1). Parents were 81% female. Adolescents were 62.5% female and had an average age of 15.1 (SD = 2.3). Please see Table 2 for further descriptive information.
The overall mean age at which stakeholders indicated for starting to teach internet safety was 7.2 years (SD = 2.5), range 2-15. Teachers reported that the average age at which internet safety should be taught was 6.9 years (SD = 2.1), while clinicians felt the average age to start teaching this topic should be 7.3 years (SD = 2.4). Parents felt that internet safety education should begin at age 6.6 years (SD = 2.3). There were no statistically significant differences between these groups regarding age to begin teaching internet safety (p = .2). Adolescents reported that internet safety education should begin at age 8.7 years (SD = 2.4). Please see Figure 1 for a summary of recommended ages to begin internet safety education.

Age to begin teaching internet safety to youth.
Among teachers, 16 (20.8%) reported currently teaching internet safety, 51 (66.2%) had never taught it, and 4 (7.8%) had never taught it but planned to soon. The number of years teaching was not significantly associated with the likelihood to have taught internet safety.
Among clinicians, 3.6% regularly and 55% sometimes counseled patients on internet safety. One-third of clinicians (33.3%) had never counseled or taught patients about internet safety and a few clinicians (8.1%) had no experience with this but planned to begin soon. The number of years in practice was not associated with the likelihood to have taught internet safety (p = .6).
All parents reported discussing online safety with their children either sometimes (58.3%) or regularly (40.3%).
Experiences learning internet safety
Adolescents were asked to identify ways in which they had learned about online safety. Adolescents were permitted to select all options that applied. Adolescents selected people including teachers (87.5%), parents (75%), friends (41.7%), siblings (27.1%) and clinicians (11.5%). Some adolescents indicated that they had learned internet safety by being self-taught (27.5%).
Teachers uniformly reported supporting online safety education in public schools (100%). Clinicians almost uniformly supported providing online safety education in clinicians’ offices (99.1%).
All groups selected parents as the primary candidate to teach internet safety. Among teachers, 97% ranked parents as their first choice candidate, and 3% ranked teachers as first choice. Among clinicians 97% ranked parents as first choice candidate, and 3% ranked teachers as first choice. Among parents, 96% ranked themselves as first choice candidate, and 4% ranked teachers as first choice. Among adolescents, there was more variety in answers. Most adolescents (74.7%) ranked parents as first choice candidate, 13.8% ranked teachers as first choice, 5.7% ranked law enforcement as first choice, 1.5% ranked community as first choice, 3% ranked churches as first choice and 3% wrote in answers of making a movie related to online safety and making a powerpoint regarding online safety.
The results of this study illustrate several key points regarding promoting safe internet use among youth. Findings suggest general agreement among key stakeholders for teaching internet safety at a young age, and for identifying parents as primary teachers of this topic.
First, our findings regarding the suggested age to begin teaching online safety may seem younger than expected. The suggested age range of 6 to 8 years identified by participants suggests that internet safety education could begin in early grade school, around 1 st or 2 nd grade. However, given our current society’s focus on technology, it is likely that children are being introduced to computers at ever-younger ages. Data from 2010 suggests that almost 20% of 8 to 10 year olds spend time on social networking sites daily, in the past three years it seems likely that this percentage has grown [ 20 ]. Timing safety education with the onset of internet use may allow for the concomitant development of computer skills and safety skills. As with many health teachings such as nutrition or sexual behavior, providing education to children before dangers can arise is a key strategy to help youth integrate these lessons into their lives and prevent negative consequences.
Second, our findings include a general agreement among key stakeholders that parents should hold the primary responsibility for internet safety education. These findings are supported by a recent study in which teachers felt that parents should have the primary role in teaching this topic [ 27 ]. Interestingly, we found that while parents all reported that they regularly or sometimes teach internet safety, only 75% of adolescents reported hearing from parents on this topic. These conflicting findings may be due to social desirability on the part of parents reporting their teaching efforts, or that teens may underreport their parents counseling efforts as they may not recognize parent attempts to discuss these difficult topics. Previous work has found a similar disconnect between parent and pediatrician reporting of counseling on risk behaviors [ 28 ].
Finally, our findings suggest that parents are willing teachers in providing internet safety education, and that many report some experience in this area. However, while parents may be candidates to guide their children’s digital lives, some parents may feel underprepared for the task of instructing their children who have grown up as “digital natives.” Thus, health care providers and public health educators may have an unique opportunity to support parents by providing resources, guidance and support. Pediatricians who see adolescent patients have the opportunity to serve an important and perhaps familiar role. As with many other topics of health supervision including safety, nutrition and fitness, parents are the primary source of education for their children. However, in many of these health topics, clinicians and health educators are trusted sources for parents on how to talk with their children about these issues. Some child health providers may feel untrained or unprepared to answer questions about internet safety or cyberbullying given that these are relatively recent health concerns about which much remains unknown. Pediatricians can use American Academy of Pediatrics guidelines to recommend parental supervision of internet activities, decreasing or eliminating isolated screen time (ie, moving the computer to a public space), and having open discussions about the potential dangers of electronic media [ 23 ]. Pediatricians and educators can also partner with schools or other community groups, such as law enforcement, to provide consistent and reinforced messages about internet safety.
Limitations to this study include the regional focus of our data collection. Our study aimed to draw representation of populations of teachers, clinicians, parents and adolescents within our region, the excellent response rates and distribution of participants within each category support that our results are generalizable within our region. However, there are other groups who may engage in teaching internet safety that were not included in this study such as churches and community groups. Second, it is notable that our study did not provide data on what methods would be best to provide internet safety education, this is a logical next step for future study. Third, we did not specify in the context of this study whether online safety should include additional technologies such as cell phones or texting. Fourth, data was collected by self-report, thus recall bias or overestimation of experience or willingness could have impacted our findings. Based on the varied stakeholders included in this study, there was some variation in data collected from each group.
Technology is now an integral part of life, and thus, part of the health of our patients. Our findings illustrate consensus around several groups with experience and investment in working with children and adolescents that parents should have primary responsibility for teaching internet safety. Our study highlights an opportunity for pediatricians to play a collaborative role with parents, patients and teachers to address the critical topics towards improving internet safety. Given the importance of this topic for today’s youth, it is likely that collaborative efforts are needed to provide consistent education about safety in the digital world.
Authors’ information
MM is an adolescent medicine physician who conducts research on the intersection of technology and health. KE is a medical student interested in pediatrics. KB studied consumer science and is interested in ways to improve internet safety education for youth. HY is a pharmacist and researcher with interest in provision of education to patients and parents. EC is a pediatrician and researcher interested in improving health systems and communication.
Joiner R, et al: Gender, Internet identification, and Internet anxiety: correlates of Internet use. Cyberpsychol Behav. 2005, 8 (4): 371-378. 10.1089/cpb.2005.8.371.
Article PubMed Google Scholar
Anderson KJ: Internet use among college students: an exploratory study. J Am Coll Health. 2001, 50 (1): 21-26. 10.1080/07448480109595707.
Article CAS PubMed Google Scholar
Caplan SE: Preference for online social interaction - a theory of problematic Internet use and psychosocial well-being. Commun Res. 2003, 30 (6): 625-648. 10.1177/0093650203257842.
Article Google Scholar
Colley A, Maltby J: Impact of the Internet on our lives: male and female personal perspectives. Comput Hum Behav. 2008, 24 (5): 2005-2013. 10.1016/j.chb.2007.09.002.
Goold PC, Ward M, Carlin EM: Can the Internet be used to improve sexual health awareness in web-wise young people?. J Fam Plann Reprod Health Care. 2003, 29 (1): 28-30. 10.1783/147118903101196864.
Hunley SA, et al: Adolescent computer use and academic achievement. Adolescence. 2005, 40 (158): 307-318.
PubMed Google Scholar
Lenhart A, Madden M: Social Networking Sites and Teens: An Overview. 2007, Pew Internet and American Life Project, http://www.pewinternet.org/pdfs/PIP_SNS_Data_Memo_Jan_2007.pdf ,
Google Scholar
Lenhart A, Madden M, Hitlin P: Teens and Technology: Youth are Leading the Transition to a Fully Wired and Mobile Nation. 2005, Pew Internet and American Life Project, http://www.pewinternet.org/pdfs/PIP_Teens_Tech_July2005web.pdf ,
O’Keeffe GS, et al: The impact of social media on children, adolescents, and families. Pediatrics. 2011, 127 (4): 800-804. 10.1542/peds.2011-0054.
Patchin JW, Hinduja S: Cyberbullying and self-esteem. J Sch Health. 2010, 80 (12): 614-621. 10.1111/j.1746-1561.2010.00548.x. quiz 622-4
Lenhart A: Cyberbullying and Online Teens. 2007, Pew Internet and American Life Project, http://www.pewinternet.org/pdfs/PIP%20Cyberbullying%20Memo.pdf ,
Ybarra ML, Espelage DL, Mitchell KJ: The co-occurrence of Internet harassment and unwanted sexual solicitation victimization and perpetration: associations with psychosocial indicators. J Adolesc Health. 2007, 41 (6 Suppl 1): S31-S41.
Perren S, et al: Bullying in school and cyberspace: associations with depressive symptoms in Swiss and Australian adolescents. Child Adolesc Psychiatry Ment Health. 2010, 4: 28-10.1186/1753-2000-4-28.
Article PubMed PubMed Central Google Scholar
Agatston PW, Kowalski R, Limber S: Students’ perspectives on cyber bullying. J Adolesc Health. 2007, 41 (6 Suppl 1): S59-S60.
Hinduja S, Patchin JW: Bullying, cyberbullying, and suicide. Arch Suicide Res. 2010, 14 (3): 206-221. 10.1080/13811118.2010.494133.
Hinduja S, Patchin JW: Personal information of adolescents on the Internet: A quantitative content analysis of MySpace. J Adolesc. 2008, 31 (1): 125-146. 10.1016/j.adolescence.2007.05.004.
Moreno MA, et al: Display of health risk behaviors on MySpace by adolescents: Prevalence and Associations. Arch Pediatr Adolesc Med. 2009, 163 (1): 35-41. 10.1001/archpediatrics.2008.502.
Back MD, et al: Facebook profiles reflect actual personality, not self-idealization. Psychol Sci. 2011, 21 (3): 372-374.
Jones S, et al: US College Students’ Internet Use: Race, Gender and Digital Divides. J Comput-Mediat Commun. 2009, 14 (2): 244-264. 10.1111/j.1083-6101.2009.01439.x.
Rideout VJ, Foehr UG, Roberts D: Generation M2: Media in the lives of 8 to 18 year olds. 2010, Menlo Park: Kaiser Family Foundation
Lenhart A, Purcell K, Smith A, Zickhur K: Social media and young adults. 2010, Washington, DC: Pew Internet and American Life Project
Sun P, et al: Internet accessibility and usage among urban adolescents in Southern California: implications for web-based health research. Cyberpsychol Behav. 2005, 8 (5): 441-453. 10.1089/cpb.2005.8.441.
AAP: Media and Children. 2013, Available from: http://www.aap.org/en-us/advocacy-and-policy/aap-health-initiatives/Pages/Media-and-Children.aspx
Halpern-Felsher BL, et al: Preventive services in a health maintenance organization: how well do pediatricians screen and educate adolescent patients?. Arch Pediatr Adolesc Med. 2000, 154 (2): 173-179. 10.1001/archpedi.154.2.173.
Mangione-Smith R, et al: The quality of ambulatory care delivered to children in the United States. N Engl J Med. 2007, 357 (15): 1515-1523. 10.1056/NEJMsa064637.
Lenhart A: Adults on Social Network Sites. 2009, Pew Internet and American Life Project, http://www.pewinternet.org/Infographics/Growth-in-Adult-SNS-Use-20052009.aspx ,
Zogby: The State of K-12 Cyberethics, Cybersafety and Cybersecurity Curriculum in the United States. 2011, The National Cyber Security Alliance, http://www.staysafeonline.org/download/…/2011_national_k12_study.pdf ,
Cheng TL, et al: Determinants of counseling in primary care pediatric practice: physician attitudes about time, money, and health issues. Arch Pediatr Adolesc Med. 1999, 153 (6): 629-635.
Pre-publication history
The pre-publication history for this paper can be accessed here: http://www.biomedcentral.com/1471-2458/13/543/prepub
Download references
Acknowledgments
This project was supported by Award Number K12HD055894 from the Eunice Kennedy Shriver National Institute of Child Health and Human Development. The funding organization had no role in the design, collection of data, analysis or interpretation on the data in this manuscript. The authors would like to acknowledge the contributions of Michael Swanson and Jay Farnsworth to this project.
Author information
Authors and affiliations.
School of Medicine and Public Health, University of Wisconsin, Madison, WI, USA
Megan A Moreno, Kaitlyn Bare & Elizabeth D Cox
School of Nursing, University of Wisconsin, Madison, WI, USA
Katie G Egan
School of Pharmacy, University of Wisconsin, Madison, WI, USA
Henry N Young
Seattle Childrens Research Institute, University of Washington, M/S CW8-6, PO Box 5371, Seattle, WA, 98145-5005, USA
Megan A Moreno
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Megan A Moreno .
Additional information
Competing interest.
The authors declare that they have no competing interest.
Authors’ contributions
MM conceived of the study, participated in its design and coordination, participated in analysis and wrote the manuscript. KE and KB participated in data collection and helped to draft the manuscript. HY and EC participated in analysis and helped to draft the manuscript. All authors read and approved the final manuscript.
Electronic supplementary material
Additional file 1: survey given to teachers.(doc 28 kb), additional file 2: survey given to clinicians.(doc 29 kb), additional file 3: survey given to parents.(doc 31 kb), additional file 4: survey given to adolescents.(doc 28 kb), authors’ original submitted files for images.
Below are the links to the authors’ original submitted files for images.
Authors’ original file for figure 1
Rights and permissions.
This article is published under license to BioMed Central Ltd. This is an Open Access article distributed under the terms of the Creative Commons Attribution License ( http://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Reprints and permissions
About this article
Cite this article.
Moreno, M.A., Egan, K.G., Bare, K. et al. Internet safety education for youth: stakeholder perspectives. BMC Public Health 13 , 543 (2013). https://doi.org/10.1186/1471-2458-13-543
Download citation
Received : 16 April 2012
Accepted : 17 May 2013
Published : 05 June 2013
DOI : https://doi.org/10.1186/1471-2458-13-543

Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Internet safety
- Online safety
- Parent education
- Patient education
- Survey research
BMC Public Health
ISSN: 1471-2458
- General enquiries: [email protected]
Privacy and Safety on the Internet Research Paper
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
This paper deals with the issue of safeguarding privacy on the internet. It outlines safety policies to follow when disseminating or allowing personal private data to be used. Further, the paper the paper considers ethical principles or conduct individuals should develop in order to promote their personal security and their information on the internet. In conclusion, this essay reiterates the importance of adhering to safe practices when using the internet.
Privacy protection on the internet is pegged on surveillance and individuals anticipating control of how personal information is disseminated and used. This has become a major concern because of modern information technology advancement that makes it easy to compromise information safety on the internet (Weber 200).
Privacy of personal information on the internet encompasses three major aspects. The first one is individual space. Individuals feel comfortable when performing in a protected environment; guarded against undesirable objects and signals which they haven’t anticipated (Weber 203).
The second aspect is freedom to make personal decisions in relation to the information flow and dissemination. Freedom to share information is what users demand in the cyberspace. Individuals do not want to be interfered with and they feel they should be in control of their personal data and how it is processed at their own discretion (Weber, 205). Modern information technology innovations pose serious security concerns for users of the internet.
Quick stream, cookies and electronic data warehousing have caused digital discomfort because it leads to exposure of personal information. There has been no thorough surveillance technology developed to comprehensively monitor how malicious applications steal or make away with personal data (Khosrow-Pour 68). Privacy should therefore encompass safety in three major ways i.e. confidentiality of personal information, anonymity and attention paid to an individual (Khosrow-Pour 73).
To enhance privacy and security on the internet, data should be accessed in a confidential way so that it cannot be divulged to third parties. A policy to govern internet usage is vital. Data controllers, which are parties empowered by the law to guarantee safety on the internet should be competent enough as to handle the contents of personal data with utmost care.
The data controllers should enforce security measures to ensure collection, storage, processing and dissemination is performed in secure environment to protect the recipients (Imparato 99).
A privacy guideline plays an important role with regard to personal information collected on the internet. Sound policies enable users to feel comfortable because it enables the user in identifying safe sites on the internet. Secondly, privacy guidelines foster trust between users and the developers as they read from the same script when it comes to security on the internet. When users feel comfortable and confident about a given website, they can interact more or use the website more, which is the aim of developers (Imparato 119).
Policy should strive towards transparency in internet transactions. The user should have knowledge of how his or her information is being collected, the purpose of collection and how the party is going to use the information. This knowledge builds the trust of the user because incase the information is taken into wrong hands; the user can hold the liable party basing on policies they have outlined.
To ensure effective internet policy and promote accountability in the use internet technology, the following policy guideline should be considered. The first important aspect of a guideline is responsibility (Schell 112). The party collecting data should be responsible for the data collected i.e. he or she should account for personal information in his or her possession.
The second guideline is that the purpose of personal information collected and processed should be clear at the onset of collection and its limit specified; this will ensure that an individual feels safe with his data on the internet (Schell 114). The third guideline is that the information collected should be limited to the task of accomplishing a set purpose.
The final guideline is that a person whom the information is collected from should have access to the information collected and should have the freedom to correct and make it accurate as possible. An individual should be notified within a reasonable time and in a form which he can clearly understand. If the data collected is not about him, he can challenge to have data discarded, to be completed or amended to safeguard his safety (McBride, 56).
Finally, the principle regarding personal data and protection or full disclosure in relation to all security concerns is critical. There should be a policy which outlines development and practices. A policy to solely screen and enhance integrity should exist within established framework to ensure openness prevails (Schell 124).
Security protection policy is essential towards ensuring that individuals are protected while using the internet. The internet has evolved with set of complex challenges and realizing security for individuals and data has been a major concern. However, several methods can be used to safeguard an individual and resources while interacting with the internet. The first security measure that can be considered is encryption (McBride, 112).
Encryption involves using an algorithm to transform txt messages to human unreadable format. It is performed using a special key which is needed to decrypt it back to human readable form. To securely disseminate information on the net, this security method is useful because it prevents potential hackers who intercept the data from understanding (McBride, 124).
The second measure for enhancing safe internet computing is instituting firewall. Firewalls play a significant role in the network by barring unwarranted users. It screens inbound and outbound information hence no threat is allowed to enter into and individual network thereby improving internet security (Imparato 134).
The final security measure to ensure safety and protection is achieved on the internet is use of password. Password provide efficient protection on stored data, however, the password should often be changed to enhance its effectiveness because they have been prone to hacking (Imparato, 135). Password practices when practiced promotes users protection while on the internet
In conclusion, effective policy guidelines facilitate individual protection while on the internet. Proper guidelines and practice prevent situations where identity theft and other security breaches happen; impacting negatively on individuals and organizations. Precaution is necessary when divulging personal information to guarantee safety and confidentiality.
When inputting some personal information on some website, individuals have to be extremely conscious about how safe the website is; some sites have been technically advanced in that they use cookies and other methods to tap into personal information that can later be used against the user.
Some sites can tap into credit card information which is later use to transact businesses without the owners’ consent. For effective safety, guidelines or policy regarding personal data and how it is used can be very helpful for individuals. Safeguarding safety on internet leads to user confidence and trust thus enabling realization of maximum benefits from internet usage.
Works Cited
Imparato, Nicholas. Public Policy and the Internet: Privacy, Taxes, and Contract . California: Hoover Press, 2000.
Khosrow-Pour, Mehdi. Web Technologies for Commerce and Services Online . Pennsylvania: Idea Group Inc (IGI), 2008.
McBride, Patrick. Secure Internet Practices: Best Practices For Securing Systems In The Internet And E-Business Ag e. Boca Raton: CRC Press, 2002.
Schell, Bernadette, Hlubik. The Internet and Society: a Reference Handbook . California: ABC-CLIO, 2007.
Weber, Rolf, H. Shaping Internet Governance: Regulatory Challenges . Michigan: Springer, 2010.
- Improper Internet Use at Work
- Ethical Issues in Network Regulation
- End-to-End Encryption: Hash, Passwords, and Security
- Privacy on the Internet: A Critical Analysis
- Authentication and Securing Personal Information in Untrusted Internet
- Multitasking: BlackBerry v. Radio
- Aspects of Internet Censorship by the Government
- Code switching and millennial generation
- The information Divide (NBN)
- What is the negative and positive side for the national broadband network?
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2019, February 7). Privacy and Safety on the Internet. https://ivypanda.com/essays/privacy-and-safety-on-the-internet/
"Privacy and Safety on the Internet." IvyPanda , 7 Feb. 2019, ivypanda.com/essays/privacy-and-safety-on-the-internet/.
IvyPanda . (2019) 'Privacy and Safety on the Internet'. 7 February.
IvyPanda . 2019. "Privacy and Safety on the Internet." February 7, 2019. https://ivypanda.com/essays/privacy-and-safety-on-the-internet/.
1. IvyPanda . "Privacy and Safety on the Internet." February 7, 2019. https://ivypanda.com/essays/privacy-and-safety-on-the-internet/.
Bibliography
IvyPanda . "Privacy and Safety on the Internet." February 7, 2019. https://ivypanda.com/essays/privacy-and-safety-on-the-internet/.
Reference management. Clean and simple.
How to write a thesis statement + examples

What is a thesis statement?
Is a thesis statement a question, how do you write a good thesis statement, how do i know if my thesis statement is good, examples of thesis statements, helpful resources on how to write a thesis statement, frequently asked questions about writing a thesis statement, related articles.
A thesis statement is the main argument of your paper or thesis.
The thesis statement is one of the most important elements of any piece of academic writing . It is a brief statement of your paper’s main argument. Essentially, you are stating what you will be writing about.
You can see your thesis statement as an answer to a question. While it also contains the question, it should really give an answer to the question with new information and not just restate or reiterate it.
Your thesis statement is part of your introduction. Learn more about how to write a good thesis introduction in our introduction guide .
A thesis statement is not a question. A statement must be arguable and provable through evidence and analysis. While your thesis might stem from a research question, it should be in the form of a statement.
Tip: A thesis statement is typically 1-2 sentences. For a longer project like a thesis, the statement may be several sentences or a paragraph.
A good thesis statement needs to do the following:
- Condense the main idea of your thesis into one or two sentences.
- Answer your project’s main research question.
- Clearly state your position in relation to the topic .
- Make an argument that requires support or evidence.
Once you have written down a thesis statement, check if it fulfills the following criteria:
- Your statement needs to be provable by evidence. As an argument, a thesis statement needs to be debatable.
- Your statement needs to be precise. Do not give away too much information in the thesis statement and do not load it with unnecessary information.
- Your statement cannot say that one solution is simply right or simply wrong as a matter of fact. You should draw upon verified facts to persuade the reader of your solution, but you cannot just declare something as right or wrong.
As previously mentioned, your thesis statement should answer a question.
If the question is:
What do you think the City of New York should do to reduce traffic congestion?
A good thesis statement restates the question and answers it:
In this paper, I will argue that the City of New York should focus on providing exclusive lanes for public transport and adaptive traffic signals to reduce traffic congestion by the year 2035.
Here is another example. If the question is:
How can we end poverty?
A good thesis statement should give more than one solution to the problem in question:
In this paper, I will argue that introducing universal basic income can help reduce poverty and positively impact the way we work.
- The Writing Center of the University of North Carolina has a list of questions to ask to see if your thesis is strong .
A thesis statement is part of the introduction of your paper. It is usually found in the first or second paragraph to let the reader know your research purpose from the beginning.
In general, a thesis statement should have one or two sentences. But the length really depends on the overall length of your project. Take a look at our guide about the length of thesis statements for more insight on this topic.
Here is a list of Thesis Statement Examples that will help you understand better how to write them.
Every good essay should include a thesis statement as part of its introduction, no matter the academic level. Of course, if you are a high school student you are not expected to have the same type of thesis as a PhD student.
Here is a great YouTube tutorial showing How To Write An Essay: Thesis Statements .


An Examination of Parenting Strategies for Children's Online Safety
Degree type.
- Dissertation
- Institute for Software Research
Degree Name
- Doctor of Philosophy (PhD)
Usage metrics
- Computer Software
Staying Safe Online: 6 Threats, 9 Tips, & 1 Infographic
Before the current pandemic, we used the Internet to do a lot of things. Now, however, with everyone confined to their homes, we have been doing almost everything online. We’re not only talking about shopping. People from all around the world can connect via video calls. They can even work or study online. The Internet has become an essential tool to participate in modern life. However, it’s important to remember that online connection comes with a price.

“Stay home, stay safe” is the current motto. But the more time you spend online, the greater the risk of cyber threats. During the pandemic, the frequency of online crimes has risen exponentially. According to an FBI report of 2020, the number of instances has doubled compared to previous years. Since we can’t stop using the Internet entirely, how can we protect ourselves?
This article:
- examines the six main threats you face online
- provides a list of nine effective tips on how to stay safe
- contains an infographic that is easy to print out
- Top 6 Cybersecurity Threats
9 Internet Safety Tips
- Internet Safety Infographic
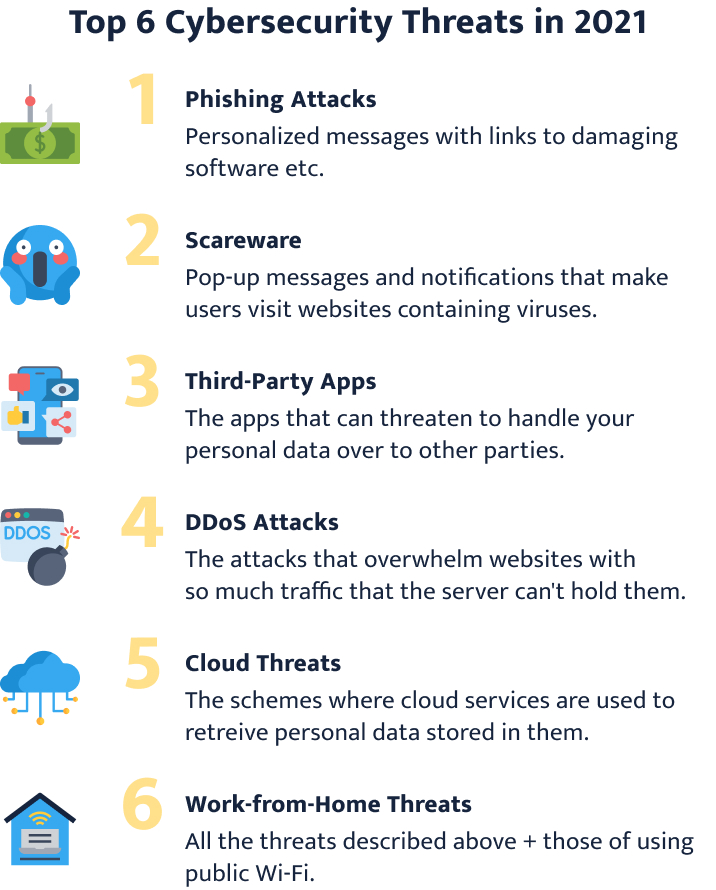
Top 6 Cybersecurity Threats in 2024
The FBI released a report created by the Internet Crime Complaint Center. It revealed that in 2020 the number of registered cybercrimes almost doubled compared to the previous year. Victims have lost large quantities of money due to different types of online scams. What caused such a drastic rise in online crimes?
One theory is that those who have been left unemployed have begun to make money as cybercriminals. These job seekers are so desperate that they agree to work for organized groups of criminals who scam Internet users. Unfortunately, this is the new reality that the high unemployment rates from the pandemic have created.
Online frauds are becoming more and more sophisticated. Now, successful hackers also use tactics from human psychology and social engineering . Cybercriminals find weaknesses by applying psychological tricks. They blackmail people through social media or their phones. To keep yourself and your money safe, you need to be aware of all the online threats described below.
- Phishing Attacks Phishing is one of the most popular types of cyber-attacks. The method works by sending out personalized messages to people and inviting them to click a link. These links damage the victim’s operating system by installing harmful software or even compromising the victim’s safety through the exposure of private information. Since most people are aware of such attacks, cybercriminals have had to develop new methods to trick users. Now, they use machine learning to create even more convincing messages. The main goal is to fool employees into disclosing sensitive information , such as passwords to the organization’s systems or credit card data.
- Scareware Like phishing, this type of cybercrime is based on social engineering. Scareware describes all software that tricks users into visiting websites that contain viruses. These can be especially dangerous because they can mimic notifications from antivirus software . They show up in the form of pop-up messages that claim to have detected a virus on your computer. Such notifications look authentic. Users don’t think twice before paying for the installation of the software that can fix the supposed problem. However, what they receive instead is malware that intends to steal private data. Often, scareware saves your credit card information so that cybercriminals can use it for identity theft.
- Third-Party Apps Even though third-party apps may have some benefits, they still carry potential risks to your privacy. Such apps ask for your permission to access your accounts. For example, some post on your social media accounts via other apps. This saves time and seems handy, right? Not so fast! There have been many cases where third-party apps have spammed and posted messages on people’s accounts. However, that’s not the worst thing they can do. Those apps can potentially hand your personal data over to other parties . Your security and privacy are undermined with third-party apps.
- DDoS Attacks Distributed denial-of-service (DDoS) attacks are usually aimed at websites or online services. These attacks try to overwhelm a website with so much traffic that the server can’t withstand the assault. This can be in the form of an enormous number of requests or incoming messages. As a result, the website crashes and fails to operate normally. Sometimes, these attacks are mild or demand that you transfer money. However, with attacks powerful enough, hackers can take control of huge international services, such as Amazon, Netflix, or even Visa. Another way cybercriminals use DDoS attacks is to initiate them as a distraction. While the company or organization is trying to get things under control, the criminal steals data or installs malicious software.
- Cloud Threats The idea behind cloud threats is simple – hackers use cloud services to retrieve personal data stored there. Sometimes accessing cloud data is just a first step in their plan to perform a DDoS attack or blackmail the users. Many companies and organizations have been the victims of these attacks. In 2020, the situation worsened. Individual users and big organizations have been reporting more and more cases of data loss through cloud attacks. Sometimes, cybercriminals remain unnoticed in the cloud system until much later. The time they spend preparing the attacks helps them evade security measures.
- Work-from-Home Threats Since the start of the pandemic, many people have started working from home, which means that they receive less protection from their employers in regards to cybersecurity. The risks have increased for employees, which has IT specialists pretty worried. In addition to all the threats described above, users are exposed to the risks of using public Wi-Fi . Those who work from home are suffering from more phishing attacks as well. In part, this is due to the more active use of email and messaging apps.
All of these threats seem quite dangerous to your privacy, don’t they? What can you do to protect yourself from cyber-attacks? You don’t have to become an IT expert. Just following a few simple rules is enough.
Here are our main tips on how to keep cybercriminals away:
- Capital letters
- Unique signs
There are tools that can make this process easier. For example, password generators provide you with solid and secure passwords in just a few seconds.
- Don’t share personal data on your social media accounts. Sharing pictures of major life events or everyday moments on social media may seem fairly innocent. However, you should probably be more careful. Everyone has access to that information. Skilled cybercriminals have no trouble tracking down your relationships and other details about your life. They may use what they find to trick your friends into giving up sensitive information. It’s not hard to find out dates of birth, email addresses, interests, and details about family members, which makes it even easier for hackers to break into your account (see the first tip to avoid this!).
- Visit only secure websites. Sometimes, website content may seem too appealing not to visit. You might even go ahead and create a profile, sharing your personal information. You should be careful, though, because not all websites are safe places. Who knows what malicious programs and scams are hidden there? Before doing anything, make sure you check the website address. URLs beginning with “https” are safer than ones with “http” because the letter “s” stands for security. Another thing to look out for is a small lock sign near the URL . Nowadays, web browsers are able to recognize safe websites and mark them as secure with this sign.
- Use legitimate software. Yes, we understand that it carries a high price tag, but do you really want to take risks? Going to unsafe websites and using third parties to get free software is not the best idea nor the most ethical practice. Whenever you want to get an app or a program, you should do it through an official provider’s website, whether or not you pay. This ensures the authenticity of the software. Otherwise, you risk downloading a virus or malicious program instead. Don’t forget to keep everything updated!
- Be careful when using credit cards. It is estimated that for every $100 spent by credit card users, about $10 is lost due to fraud . There are many dangers in using your cards for online shopping, but these tips will help you avoid those traps. First of all, try not to use debit cards that are directly linked to your bank account, and use only one card to purchase things online. Another thing to consider is adding a second layer of protection, which is usually offered by your bank. For example, not only will you be asked to put in a password, but a code sent to your email or phone will be required. Lastly, don’t forget to check if the website is safe.
- Use two-step verification. It’s easy for hackers to guess your password and steal your personal data unless they have to verify that they are the rightful owners. How is this done? The most common solution is a process called two-step verification. For example, Google offers this option to all of its users. Instead of simply typing in your password, you also need to enter a code that is sent to your phone in order to log in to your account. Many websites and services offer these security measures (such as banks, which we highlighted in the previous tip).
- Steer clear of phishing scams. Chances are that at least once in your life, you have received a message with questionable content. Keep an eye out for similar ones and never respond or click on any links! Typically, the message contains some irresistible offer or could allegedly be sent from a website you trust. Sometimes, they can appear as notifications about an issue, calling for you to take some action. It is essential to recognize whether the sender of these messages is someone you actually know. Always remember to follow the tips described above, such as using two-step verification and legitimate software.
- After getting a router from your provider, make sure you change its name and password . It is not hard to do by yourself, and such a measure can provide additional security.
- It is also a good idea to see whether your new router has the most recent security protocols since these make it harder for cybercriminals to hack into it.
- Don’t forget to log out. The convenience of staying logged in to your favorite websites is high, but it is dangerous for the security of your personal information. Not only can online services keep you logged in at all times, but they can also save all of your data. Sometimes, websites don’t even ask if you want them to remember passwords. We know that it is more difficult to enter long passwords every time you enter a website, especially from your phone, but this provides additional security. Think about these issues carefully and determine your priorities. We are only here to help you.
Internet Safety Tips: Infographic
In this infographic, we have put together all the best tips to help you stay safe online. These nine tips are easy to incorporate into your daily life. Read over this list of small things you can do every day to protect your private information (it’s easy to print out, too!).

To sum up, in today’s world, you need to stay alert even when you are at home using your laptop. Being aware of the ways hackers steal your sensitive data is essential. Besides, we highly recommend making good use of the tips we provided in this article. You can start making your online life safer right now!
- Share to Facebook
- Share to LinkedIn
- Share to email
![thesis statement about internet safety UniPapers Review—Trustworthy Academic Service [10+ Years of Experience]](https://custom-writing.org/blog/wp-content/uploads/2021/04/close-up-woman-working-laptop-284x153.jpg)
The issue of students struggling with home assignments and seeking additional help always causes active discussions. Especially when academic assistance services are involved in the talks. We can’t deny that homework help websites have been surrounded by controversies for quite a while (more than a decade, actually). Some people see...

Have you ever felt like you could use some additional help with assignments? If the answer is yes, then you’re not alone. The number of students who struggle with their academic tasks is a lot bigger than you might expect. The main problem here is that curriculums in high schools,...

Every student has their own good reasons to be looking for help with assignments. Overload with too much homework, other tasks and responsibilities to take care of, part-time job, lack of information or resources, insufficient language skills in ESL students… The list can go on and on. The fact that...

How do you deal with criticism? The first reaction many of us have is to defend ourselves, or worse, fight back. We can feel offended, seeing negative feedback as a dismissal of our work. Yet, while criticism can feel hurtful and demoralizing, it can also be viewed in a positive...

This infographic contains all the basic information on the benefits of mindfulness for students. It also describes 6 simple mindfulness techniques you can use in your daily life. In order to find the best ways of applying those thecniques, you can take a learning style quiz for students to find...

This infographic contains nine tips on organizing your study space so that you could work without any distractions. Wondering how to choose the furniture, organize and decorate your place, and what colors to use? Here you’ll find the answers!

The winter holidays are a much-anticipated break for everyone, particularly for school and college students. It’s an opportunity to get some much-needed rest and refresh their minds. Afterward, students can get back to class, full of strength and inspiration. While relaxation is essential during this period, it is also possible...

When you participate in face-to-face communication, your appearance, tone of voice, and word choice determine the impression you make. In the era of globalization, the internet allows us to contact people we have never seen and might never meet. This online interaction can impact our lives even more than our...

You’ve graduated high school and got admitted to college or university. Or maybe you’ve already been on that continued path to getting a degree for some time. Whatever the case is, let’s face it—studies can get unbearably tough.

Are you wondering what the most effective study methods are? Do you want to know how to study fast in less time? Do you require more time for extracurricular activities but have to reserve to get prepared for exams? With our scientifically proven study tips and tricks for college students,...

Learning English as a second language and want to make progress but don’t know how? Spend a lot of money on ESL textbooks and classes? You can find many free or affordable resources for ESL students online! Our team listed ESL websites for listening, reading, speaking, and writing to develop...

According to recent statistics, approximately 72% of adults are passive job-seekers. That means that hundreds of candidates are aiming for your potential job. And they might be more experienced and skilled than you. We’re sure there are many advantages to hiring you. But to beat all those competitors, you, yesterday’s...
Not only would I give the tips you gave but for eachvone as a teacher I would try to find concrete examples of how people accomplish the cyber acts. I use to find many in my junk mail. Illustrate to the students how they are worded and take advantage of the innocent.
25 Thesis Statement Examples

Chris Drew (PhD)
Dr. Chris Drew is the founder of the Helpful Professor. He holds a PhD in education and has published over 20 articles in scholarly journals. He is the former editor of the Journal of Learning Development in Higher Education. [Image Descriptor: Photo of Chris]
Learn about our Editorial Process
A thesis statement is needed in an essay or dissertation . There are multiple types of thesis statements – but generally we can divide them into expository and argumentative. An expository statement is a statement of fact (common in expository essays and process essays) while an argumentative statement is a statement of opinion (common in argumentative essays and dissertations). Below are examples of each.
Strong Thesis Statement Examples

1. School Uniforms
“Mandatory school uniforms should be implemented in educational institutions as they promote a sense of equality, reduce distractions, and foster a focused and professional learning environment.”
Best For: Argumentative Essay or Debate
Read More: School Uniforms Pros and Cons

2. Nature vs Nurture
“This essay will explore how both genetic inheritance and environmental factors equally contribute to shaping human behavior and personality.”
Best For: Compare and Contrast Essay
Read More: Nature vs Nurture Debate

3. American Dream
“The American Dream, a symbol of opportunity and success, is increasingly elusive in today’s socio-economic landscape, revealing deeper inequalities in society.”
Best For: Persuasive Essay
Read More: What is the American Dream?

4. Social Media
“Social media has revolutionized communication and societal interactions, but it also presents significant challenges related to privacy, mental health, and misinformation.”
Best For: Expository Essay
Read More: The Pros and Cons of Social Media

5. Globalization
“Globalization has created a world more interconnected than ever before, yet it also amplifies economic disparities and cultural homogenization.”
Read More: Globalization Pros and Cons

6. Urbanization
“Urbanization drives economic growth and social development, but it also poses unique challenges in sustainability and quality of life.”
Read More: Learn about Urbanization

7. Immigration
“Immigration enriches receiving countries culturally and economically, outweighing any perceived social or economic burdens.”
Read More: Immigration Pros and Cons

8. Cultural Identity
“In a globalized world, maintaining distinct cultural identities is crucial for preserving cultural diversity and fostering global understanding, despite the challenges of assimilation and homogenization.”
Best For: Argumentative Essay
Read More: Learn about Cultural Identity

9. Technology
“Medical technologies in care institutions in Toronto has increased subjcetive outcomes for patients with chronic pain.”
Best For: Research Paper

10. Capitalism vs Socialism
“The debate between capitalism and socialism centers on balancing economic freedom and inequality, each presenting distinct approaches to resource distribution and social welfare.”

11. Cultural Heritage
“The preservation of cultural heritage is essential, not only for cultural identity but also for educating future generations, outweighing the arguments for modernization and commercialization.”
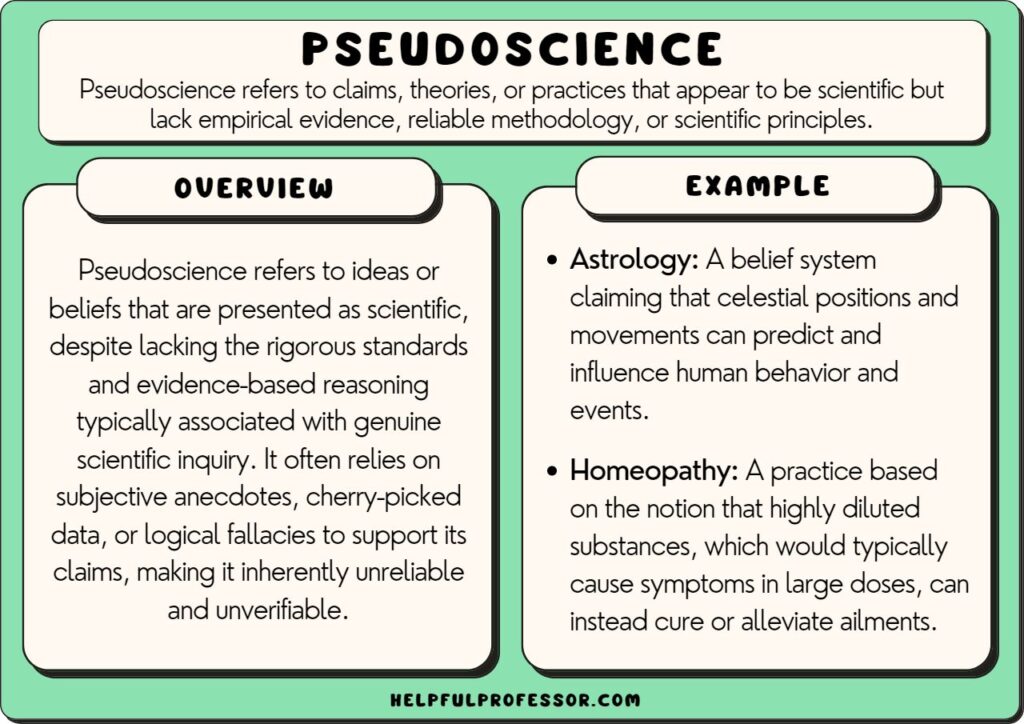
12. Pseudoscience
“Pseudoscience, characterized by a lack of empirical support, continues to influence public perception and decision-making, often at the expense of scientific credibility.”
Read More: Examples of Pseudoscience

13. Free Will
“The concept of free will is largely an illusion, with human behavior and decisions predominantly determined by biological and environmental factors.”
Read More: Do we have Free Will?

14. Gender Roles
“Traditional gender roles are outdated and harmful, restricting individual freedoms and perpetuating gender inequalities in modern society.”
Read More: What are Traditional Gender Roles?

15. Work-Life Ballance
“The trend to online and distance work in the 2020s led to improved subjective feelings of work-life balance but simultaneously increased self-reported loneliness.”
Read More: Work-Life Balance Examples
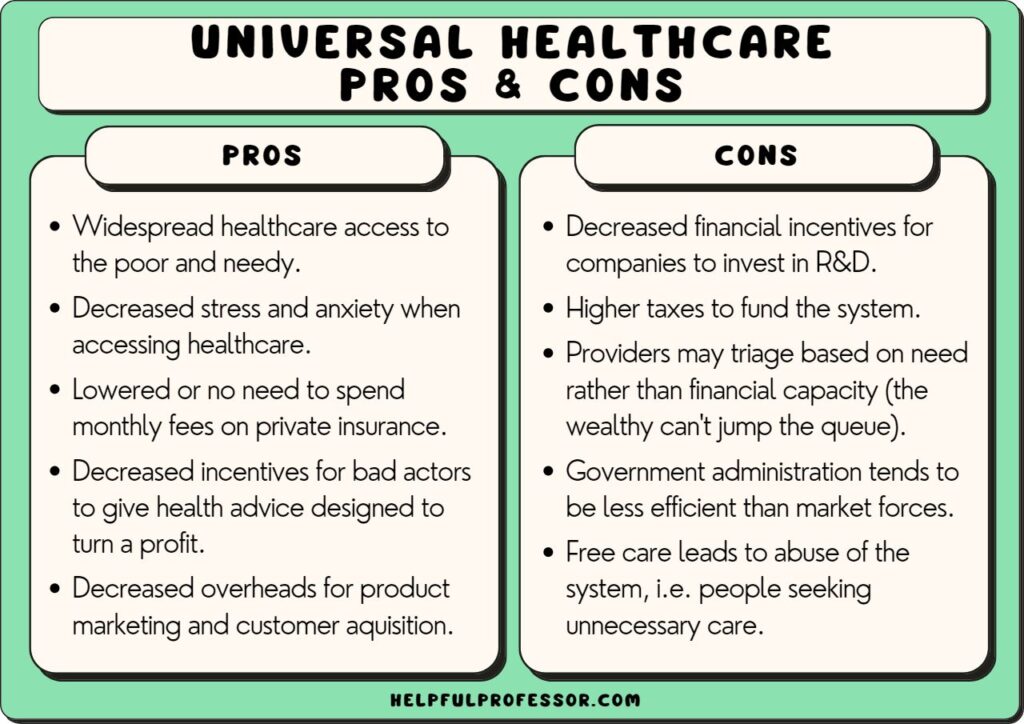
16. Universal Healthcare
“Universal healthcare is a fundamental human right and the most effective system for ensuring health equity and societal well-being, outweighing concerns about government involvement and costs.”
Read More: The Pros and Cons of Universal Healthcare

17. Minimum Wage
“The implementation of a fair minimum wage is vital for reducing economic inequality, yet it is often contentious due to its potential impact on businesses and employment rates.”
Read More: The Pros and Cons of Raising the Minimum Wage

18. Homework
“The homework provided throughout this semester has enabled me to achieve greater self-reflection, identify gaps in my knowledge, and reinforce those gaps through spaced repetition.”
Best For: Reflective Essay
Read More: Reasons Homework Should be Banned

19. Charter Schools
“Charter schools offer alternatives to traditional public education, promising innovation and choice but also raising questions about accountability and educational equity.”
Read More: The Pros and Cons of Charter Schools

20. Effects of the Internet
“The Internet has drastically reshaped human communication, access to information, and societal dynamics, generally with a net positive effect on society.”
Read More: The Pros and Cons of the Internet

21. Affirmative Action
“Affirmative action is essential for rectifying historical injustices and achieving true meritocracy in education and employment, contrary to claims of reverse discrimination.”
Best For: Essay
Read More: Affirmative Action Pros and Cons

22. Soft Skills
“Soft skills, such as communication and empathy, are increasingly recognized as essential for success in the modern workforce, and therefore should be a strong focus at school and university level.”
Read More: Soft Skills Examples

23. Moral Panic
“Moral panic, often fueled by media and cultural anxieties, can lead to exaggerated societal responses that sometimes overlook rational analysis and evidence.”
Read More: Moral Panic Examples

24. Freedom of the Press
“Freedom of the press is critical for democracy and informed citizenship, yet it faces challenges from censorship, media bias, and the proliferation of misinformation.”
Read More: Freedom of the Press Examples

25. Mass Media
“Mass media shapes public opinion and cultural norms, but its concentration of ownership and commercial interests raise concerns about bias and the quality of information.”
Best For: Critical Analysis
Read More: Mass Media Examples
Checklist: How to use your Thesis Statement
✅ Position: If your statement is for an argumentative or persuasive essay, or a dissertation, ensure it takes a clear stance on the topic. ✅ Specificity: It addresses a specific aspect of the topic, providing focus for the essay. ✅ Conciseness: Typically, a thesis statement is one to two sentences long. It should be concise, clear, and easily identifiable. ✅ Direction: The thesis statement guides the direction of the essay, providing a roadmap for the argument, narrative, or explanation. ✅ Evidence-based: While the thesis statement itself doesn’t include evidence, it sets up an argument that can be supported with evidence in the body of the essay. ✅ Placement: Generally, the thesis statement is placed at the end of the introduction of an essay.
Try These AI Prompts – Thesis Statement Generator!
One way to brainstorm thesis statements is to get AI to brainstorm some for you! Try this AI prompt:
💡 AI PROMPT FOR EXPOSITORY THESIS STATEMENT I am writing an essay on [TOPIC] and these are the instructions my teacher gave me: [INSTUCTIONS]. I want you to create an expository thesis statement that doesn’t argue a position, but demonstrates depth of knowledge about the topic.
💡 AI PROMPT FOR ARGUMENTATIVE THESIS STATEMENT I am writing an essay on [TOPIC] and these are the instructions my teacher gave me: [INSTRUCTIONS]. I want you to create an argumentative thesis statement that clearly takes a position on this issue.
💡 AI PROMPT FOR COMPARE AND CONTRAST THESIS STATEMENT I am writing a compare and contrast essay that compares [Concept 1] and [Concept2]. Give me 5 potential single-sentence thesis statements that remain objective.

- Chris Drew (PhD) https://helpfulprofessor.com/author/chris-drew-phd-2/ 25 Number Games for Kids (Free and Easy)
- Chris Drew (PhD) https://helpfulprofessor.com/author/chris-drew-phd-2/ 25 Word Games for Kids (Free and Easy)
- Chris Drew (PhD) https://helpfulprofessor.com/author/chris-drew-phd-2/ 25 Outdoor Games for Kids
- Chris Drew (PhD) https://helpfulprofessor.com/author/chris-drew-phd-2/ 50 Incentives to Give to Students
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
- Essay Database
- world trade center
- Greek Food and Culture
- The Future Portrayed I…
- Intercultural Communications
- In Heart of Darkness, …
- Things Fall Apart by C…
- In J.M. Coetzee's Wait…
- The Criminals Of Profe…
- Socialization of Children
- The Poet of Nature, Wi…
- Leonhard Euler
- Articles of Confederat…
- About all Sharks
- Vietnam Poetry
Internet Safety
What is paper-research.
- Custom Writing Service
- Terms of Service
- Privacy Policy
- Biographies

IMAGES
COMMENTS
1 Youth Internet Safety: Risks, Responses, and Research Recommendations Adina Farrukh, Rebecca Sadwick, and John Villasenor I. IntroductIon A s Internet use by children and teenagers increases, so ...
This thesis will lay out the importance of connectivity in our society - from the individual user to national security and the military. I will examine the vulnerabilities, cite case studies, and look at the consequences the cyberattacks have or could have on society. To best frame my research, I will include recent cyber events and examine the
referred to as " online safety ," " digital safety," o r "e-saf ety," this concept i s associated. both with the risks in dividuals face onl ine and with the wa ys they can protect th ...
Get Free Tools. Good Thesis Statement Examples. Specific and Clear. Good:"This thesis will scrutinize the efficacy of end-to-end encryption in safeguarding users' privacy on social media platforms.". Bad:"Encryption is crucial for privacy on social media.". The good example is specific, pinpointing the type of encryption and the ...
With the growth of Internet use, also new risks and dangers came along. Currently, Internet safety is politically and socially an important issue. One of the ways by which governments try to stimulate Internet safety, is to develop user awareness campaigns. However, the effectiveness of these campaigns is questioned (Siponen 2001, Görling 2006).
Cybercrime is one of the recurrent crimes perpetrated online. The social, economic, and security impacts of the phenomenon are enormous. Organizations are increasingly becoming victims of cybercrime and looking for effective means of preventing and managing cyber threats and cybercrimes (Enigbokan & Ajayi, 2017).
The objectives of this thesis were to understand habitual Digital Safety behaviour of students aged 10−14, the expectations of their parents, teachers and experts as well as awareness strategies ...
ascheroni, Ólafsson, 2014).Children use the Internet for various purposes: education, fun, entertainment, socializing, expressing thems. lves in many different ways. Variety of activities they tend to be engaged in online has an extremely wide range and all these activities can be beneficial to children.
Safety and Heath in it Environments Applied Business esearch: The need for Safety and Health Standards in Hazardous Working Environments in the Information Technology Businesses including IT firms are flooded with IT tools like microcomputers, photocopiers, digital surveillance tools, internet, among others. There is mounting evidence from a review of literature that in the IT work environment ...
In a recent study, Finnish children age 10-12, their use of the Internet and their online safety have been addressed (Hartikainen, 2017). In that study criticism of parental control software was presented, however they were not put under experimentation or testing. This thesis will therefore explore, discuss and make suggestions for making children
Step 1: Start with a question. You should come up with an initial thesis, sometimes called a working thesis, early in the writing process. As soon as you've decided on your essay topic, you need to work out what you want to say about it—a clear thesis will give your essay direction and structure.
Internet use is nearly ubiquitous among US youth; risks to internet use include cyberbullying, privacy violations and unwanted solicitation. Internet safety education may prevent these negative consequences; however, it is unclear at what age this education should begin and what group is responsible for teaching this topic. Surveys were distributed to key stakeholders in youth safety education ...
surveillance in the form of data-mining and data-trafficking. The former concern is an issue of safety, here defined as protection against danger, risk, threat, or injury. The latter, however, is an issue of privacy, here understood as the. state of being free from oversight or intrusion by others.
Data controllers, which are parties empowered by the law to guarantee safety on the internet should be competent enough as to handle the contents of personal data with utmost care. The data controllers should enforce security measures to ensure collection, storage, processing and dissemination is performed in secure environment to protect the ...
It is a brief statement of your paper's main argument. Essentially, you are stating what you will be writing about. Organize your papers in one place. Try Paperpile. No credit card needed. Get 30 days free. You can see your thesis statement as an answer to a question. While it also contains the question, it should really give an answer to the ...
Teenagers are using the internet for a variety of social and identity-based activities, but in doing so, they are exposed to risky situations. The work of ensuring teens' online safety largely falls to parents, many of whom are unprepared to understand the realities and norms of teens' online activity. In this thesis, we investigate how parents and teens perceive online risks, the eff ...
These factors combine to create problems for security teams to keep up with the pace, and smarter solutions are required. This thesis gives an overview of how artificial intelligence (AI) approaches, and sub-domains such as machine learning and deep learning, can be applied to cybersecurity issues.
time to sit with me, discuss and contribute to my thesis, especially under Covid-19 restrictions and SOPs we had to follow. My sincere thanks to my supervisor, Prof. David Randall for his very friendly behavior, constant support, and timely guidance throughout the thesis process. He encouraged me to limit the boundaries of my thesis
Top 6 Cybersecurity Threats in 2024. The FBI released a report created by the Internet Crime Complaint Center. It revealed that in 2020 the number of registered cybercrimes almost doubled compared to the previous year. Victims have lost large quantities of money due to different types of online scams.
Strong Thesis Statement Examples. 1. School Uniforms. "Mandatory school uniforms should be implemented in educational institutions as they promote a sense of equality, reduce distractions, and foster a focused and professional learning environment.". Best For: Argumentative Essay or Debate. Read More: School Uniforms Pros and Cons.
Thesis Statement On Internet Usage. Thesis Statement: Internet usage is negatively affecting families, knowledge, and improperly used. It has changed over the past few years and increasingly being used. Akinoglu, Orhan. "Internet and internet use: teacher trainees' perspective.". Journal of Instructional Psychology, vol. 36, no. 2, 2009 ...
Thesis Statement: The internet has become an important aspect of modern life - it improves our way of communication not just with friends and family but with different people across the globe, it provides better access to health information at the comfort of our home, it strengthens connections or social ties, it improves education and learning opportunities, it enhances business ...
Download thesis statement on Internet Safety in our database or order an original thesis paper that will be written by one of our staff writers and delivered according to the deadline. ... Parenting Report Internet Safety The internet today is a great source of information. It is also known as the super information highway because it is the ...