We use cookies to give you the best experience possible. By continuing we’ll assume you’re on board with our cookie policy

- A Research Guide
- Research Paper Topics

40 Terrorism Research Paper Topics
Read also: How to start off a research paper ?
- How does the development of technologies affect the tactics of terrorists?
- The tragedy of 9/11
- The Incels movement: a growing danger?
- Terrorism and religion
- Using minors and vulnerable social groups in terrorist acts
- The role of terrorism in the creation and development of Israel
- The most powerful international terrorism groups: Boko Haram, Al Qaeda and others
- Partisan movements and terrorism
- The history of terrorism
- What methods are justified when fighting terrorism?
- Hiroshima bombing: can it be considered terrorism?
- Terrorism in media and films
- The process of radicalization. The creation of terrorist groups
- Motivations of terrorist groups
- Terrorism and Mafia: similarities, differences and cooperation
- Terrorism as a tool for politics. Can it be used to benefit some particular political forces?
- Guantanamo Bay Detention Camp: was it justified?
- Suicide bombing and psychological conditioning of suicide bombers
- Bioterrorism
- Terrorism and human trafficking
- Terrorism threat and the international travel safety
- Is non-violent response to terrorism possible?
- The ways to work with society to prevent terroristic acts
- The first psychological aid to the victims or witnesses of terrorist act
- Why terrorists use hostages? What shall the potential hostages do to survive?
- The main differences between political and non-political terrorism
- The recruiting strategies of terrorists
- Counterterrorism all over the world
- The most prominent terrorist leaders
- The most famous counterterrorist operations
- What can society do to prevent terrorism?
- The future of terrorism. May it evolve?
- The process of taking responsibility for terrorist act: why and how the terrorists do this?
- The model of Israel society. Is it good for fighting terrorism?
- Terrorism as international crime
- Nuclear terrorism
- Terrorism and blackmailing
- Is it possible to exit a terrorist cell?
- Ideological terrorism
- The different definitions of terrorism and the cause of their creation
By clicking "Log In", you agree to our terms of service and privacy policy . We'll occasionally send you account related and promo emails.
Sign Up for your FREE account
528 Terrorism Essay Topic Ideas & Examples
⁉️ how to write a terrorism essay: do’s and don’ts, 🏆 best terrorism topic ideas & essay examples, 🥇 most interesting terrorism topics to write about, ⚡ shocking terrorism essay topics, 📌 simple & easy terrorism essay titles, 👍 good essay topics on terrorism, 💡 interesting topics to write about terrorism, ❓ terrorism essay questions.
Current-day problems, from global warming to human rights, continue to be a topical subject, urging students to address acute issues.
However, this relatability means that you, as an essay writer, may find yourself faced with conflicting facts and circumstances, which your inherent bias may affect.
Thus, a terrorism essay becomes not merely an academic endeavor, but an attempt to immerse yourself in contemporary issues with a multitude of opinions.
- Research and outline your subject beforehand. This process will not only save your time but also help you structure your thoughts and arguments coherently.
- Use tools, such as topic sentences and brainstorming techniques, in the prewriting phase of your paper. Doing so will help you understand how you would like to develop your central theme.
- Start compiling a bibliography early on. When many different viewpoints exist, creating a structured argument in favor of a particular approach may require a wide array of supporting book and journal titles.
- Give a historical overview of your issue. For example, if you are writing about global terrorism, then it is apparent that a worldwide network of violent radicals did not come into existence overnight. Acknowledge and explain the origins of your assigned issue.
- Read other’s sample essays. This action will help you gain a better understanding of what works and what does not in terrorism essay topics.
- Use terrorism essay quotations. Since this is a contemporary issue, then there are bound to be many people involved in activities to counter terrorism, survivors of attacks, and general onlookers. Utilize their perspectives and memories to give your essay a unique touch.
- Remain respectful throughout your paper. Recognize the gravity of your essay and understand the privilege you have when writing about ideas that you may not have experienced.
- Write your essay with no references. Despite watching TV coverages, listening to critics, and reading tabloids, none of us are experts on war or terrorism. Always cite the sources of your information to uphold the integrity of your work.
- Plagiarize from the work of others. While you may read essays written by your peers or those that are available online, directly copying from them is an academic offense.
- Go off point. If you are writing about the history of Al Qaeda, do not disintegrate your work into a how to stop terrorism essay. However, you may give some points in your conclusion on how the overall situation may be amended.
- Write controversial terrorism essay titles. While your title should be catchy and grab your readers’ attention, you should not resort to cheap tactics to make your headings memorable by shock value. Remember that your audience may perceive this tactic as making light of your subject, thus destroying your hard-earned credibility.
- Try to advocate for a pro-terrorist approach. While it is a sound idea to subvert some essay topics, this is not the case in such papers and your work should always be against terrorism.
- Integrate examples from unreliable sources. While readers are often less informed than the essay’s writer is, the opposite may also occur. Therefore, always check the facts, which you include in your work, to avoid embarrassment.
- Draw out your essay to stress the seriousness of the subject. Use your instructor’s specified word count as a measure for how much you should write. Your readers will not appreciate a long-winded paper, as they are hoping instead to get a quick and concise introduction to an important problem.
Want to get more inspiration on terrorism essay topics? Head over to IvyPanda!
- “To Any Would-Be Terrorists” by Naomi Shihab Nye While trying to address the extremist audience, the writer resorted to the strong methods of personification to be able to talk straight to each reading the letter. Despite the character of the text, the writer […]
- Terror in “The Dumb Waiter” Play by Harold Pinter Pinter exemplifies the existential view of the absurd and the non-existence in The Dumb Waiter in the same manner as that employed in Waiting for Godot by Beckett.
- Role of Media in Terrorism and Its Force Multipliers The following passages describe the role of the media in terrorism, how terrorists use laws to their advantage, the concept of asymmetrical warfare, and force multiplier as they apply to terrorism.
- Biowarfare and Bioterrorism: History and Origin According to Edmond and William, the dawn of bioterrorism dates back to the nineteenth century, when Louis Pasteur and Robert Koech studied and understood the basics of microbiology. Moreover, another application of biological weapons is […]
- Investigation Methods: Terrorism and Cyber Crime The question on whether the investigations in these areas of cyber crime and terrorism to remain incident driven or to adopt strategic approach are still is of great concern to the security agencies and the […]
- Islamic Terrorism in Ridley Scott’s “Body of Lies” As it was implied earlier, in order for us to be able to gain a better understanding of the phenomenon of Islamic terrorism, we need to make an inquiry into the very tenets of Islam, […]
- Leila Khaled: Freedom Fighter or Terrorist? This essay elaborates her intentions with the support of academic sources and her movie in order to demonstrate her cause of action as a freedom fighter for her country and not a terrorist as perceived.
- “Monsters, Inc.” and the War on Terror The problem of fear in the American society can be discussed as the multidimensional concept which is directly associated with the developed idea of the War on Terror because fear is the main force to […]
- Analysis of a Domestic Terrorist Group and Homeland Security Policies The Boogaloo Movement is a severe menace, and the government must take all necessary measures to put a stop to it, it is concluded.
- Suspected Terrorist Interrogation and Use of Torture Regardless, torture is still popular across the globe, and it has elicited a new debate questioning whether it is immoral and unacceptable to use torture in the case of efforts to fight terror in the […]
- Terrorism, Corruption, and Climate Change as Threats Therefore, threats affecting countries around the globe include terrorism, corruption, and climate change that can be mitigated through integrated counter-terror mechanisms, severe punishment for dishonest practices, and creating awareness of safe practices.
- Problems the US Faced in the Prosecution of the International Terrorists Differentiating a potential extremist from the rest of the population has been challenging because most international criminals interact with civilians and become part of them.
- Terrorist Impact on Maritime Transportation Security Notably, the United States established the Transportation Security Administration under the Department of Transportation, which was soon transferred to the newly formed Homeland Security Department.
- International Terrorism: Waves and Countermeasures The concept of modern terrorism emerged in Russia, and after a decade, it spread to Western Europe, the Balkans, and Asia.
- The Nexus of Homeland Security and Terrorism The Department of Homeland Security is one of the several bureaucracies formed to tackle the issues of rising insecurity due to external powers and potential facilitators within the US.
- The Future and Change of Terrorism As a result, even if terrorists get their hands on these weapons, they might hesitate to use them on individuals because of the associated implications.
- The Terrorist Attack Recovery Process Terrorism response strategies and the recovery process vary according to the scope of damages and the implications of the methods used in the terror attacks.
- Preparing for a Potential Terrorist Attack The ultimate aim of preparedness is to limit exposure to adversities during and after a terrorist attack. Thus, a recommended approach to limiting the potential security hazard of terrorist attacks is assessing its attributes and […]
- Role of Terrorism in Russo-Ukrainian War Due to this factor, one of the most influential and widespread typologies of terrorism is the New Terrorism that emerged after the tragedy of 2001 in the USA.
- Anti-Terrorism Clarification Act of 2018 Therefore, the current policies are a response to existing problems, and as the problem inside the country has become smaller, the reaction has also decreased.
- Anti-Terrorism Security Complex for Civil Aviation It is expected that the increase in the number of flights in the absence of a strengthened anti-terrorist culture should also lead to an increase in the number of unintended consequences of such flights – […]
- Terrorism: Goals and Strategies Their main purpose can range from changing the direction of the politics in the state to overthrowing the exciting government and establishing control over the population.
- Religious Terrorism: Ideologies and Methods of Al Qaeda and ISIS Strict adherence to the recorded practices and sayings of the Prophet in the letter of the Koran is emphasized. It endorses the rationalization of terrorism and violence in the efforts to fight against infidels.
- Principles of Leadership and Future of Terrorism At the present time, leadership is presented in various forms; however, the primary objectives of the model generally include the improvement of organizational performance and the enhancement of the relationships between the members.
- The 2012 Tel Aviv Bus Bombing and Crisis Management Musa was the manufacturer and detonator of the bomb, which he used Mafarji to deliver inside the Tel Aviv-based commuter bus.
- The Role of the Military in Domestic Terrorism Acts The video focuses on the issue of domestic terrorism in the U.S.in light of the January 6th attack on the Capitol.
- Addressing Challenges of Religious Terrorism The various methods used in religious terrorism are spiritual scriptures to justify the violent acts and the use of apocalyptic images of destruction to justify the actions.
- Terrorism and Changes in Police Management Firstly, the police and organizations related to the population’s safety prioritized the prevention of terrorism to minimize the damage. Organizing in the police station involves the creation of organizational structure, points of authority, and responsibilities.
- Terrorists’ Minds and Radicalization Processes Moreover, the models agree that radicalization is a stepwise process in which one stage or step leads to another and eventually reaches the act of terrorism.
- The Terrorism and Oil Industry Relationship Since terrorism is a source of political instability in the world, there is expected to be a positive correlation between oil prices and terrorist attacks. The purpose of this research was to examine the relationship […]
- Understanding the Definition of WMDs and the Constraints on Terrorist Acquisition The most known WMD a nuclear weapon is limited in numbers and difficult to create. The most probable WMD for terrorists to acquire are chemical weapons.
- Online Interventions Addressing Terrorism and Radicalization The study will also identify that the Sakinah campaign can be considered a suitable example of how it is possible to address Internet terrorism and radicalization.
- A Terrorism Attack in the Middle East Countries in the Middle East are prone to terrorist attacks rendering it one of the unsafest regions in the world. The importance of this study is to understand the purpose of terrorist attacks in the […]
- Behavioral Factors of Individual Terrorists The behavior of individual terrorists is dictated by the group dynamics, their mental health, and well-being, as well as the underlying incentives for joining a terrorist organization.
- The Ways Terrorists Raise and Move Money Moreover, the government has put into action the freezing orders and blocking of united states individuals who are presumed to have a hand in terrorist activities.
- Terrorism and Transnational Organized Crime as Threats to Homeland Security The US is among the nations that have suffered some of the worst terrorist attacks worldwide and it is also a hub of international criminal activities due to its wealth of resources and powerful economic […]
- Planning for Terrorist Events: Case Study To review the response of France’s forces and evaluate its efficiency To provide several recommendations for the prevention of attacks during the FIFA World Cup 2022 in Qatar Terrorist attacks that took place across Paris […]
- Global Impact of 9-11 Events on Terrorism Prevention Many people resorted to religion and faith, and the majority reported that they were praying more frequently. Moreover, it stimulated the intervention in Iraq and Afghanistan to fight terrorist groups.
- September 11, 2001 Attacks: What We Have Learned About Terrorism Since 9,11 The world has remembered one of the most tragic attacks in the USA in 2001, and the consequences of this event stay one of the most discussed.
- The Case of Saudi Arabia’s Soft Counter-Terrorism Strategy Therefore, this assessment is essential for government agencies, consulting organizations, and society in general, since innocent people suffer from the consequences of terrorism.
- Terrorism Prevention: Operation Geronimo Intelligence briefings had been vital in this operation, and there was sufficient evidence to show that the wanted terrorist was in the compound. In conclusion, the operation was a necessary undertaking in ensuring international peace […]
- Trump Tells Story About Killing Terrorists With Bullets Dipped in Pigs’ Blood The text reflects on Donald Trump’s recollection of the myth that terrorists were killed before the bullets used were dipped in pig blood.
- US Strategy From the Cold War to the Post-Global War on Terrorism Before the collapse of the United Soviet Socialist Republic in 1991, the United State’s strategy during the Cold War era had been one of deterrence to the potential threats of the USSR and its allies […]
- Analysis of the Terrorist Organizations: “Red Brigades” and “Boko Haram” The most famous action in the organization’s history is the abduction and murder of the former Prime Minister of Italy Aldo Moro in the spring of 1978.
- Tools Required to Intercept and Obstruct Terrorism in the US The very first section of this act is devoted to strengthening the internal security of the population of the States in the framework of countering terrorism.
- Countering Terrorism Through Innovative Approaches The vital issue of this meeting became the issue of the technological development of international terrorism, its rapid growth in the online world, and acquaintance with the most recent technologies.
- Iran’s Involvement in Sponsoring Global Terrorism Due to the particular features of the theocratic regimes, in the case of Iran, the inclination towards terrorism can be explained by two pillars of the Islamic doctrine underlining the constitution.
- Criminalistics: Forensic Science, Crime, and Terrorism These writings can be on the second, third, and so on pages, depending on the pressure on the writing subject, that is, a pen or pencil.
- Terrorism: the Victim of Terrorism and of Mechanisms to Combat It The Concept of Terrorism: Unlawful act Broad interpretations Threatening lives Generic term of terror Caused by forces opposed to the state Sociopolitical
- Countering Terrorism and Preventive Measures Considering the events of the past century, including the first and 9/11 bombing of the World Trade Center in 1993 and 2001, United States Embassy in Beirut and Kuwait bombing, and many other attacks, the […]
- Why Terrorism Is Not a Serious Threat to International and National Security We accept the existence of this threat, but we are still sure terrorism narrative as an existential threat is doing more damage to a larger amount of people than local terroristic attacks.
- An Analysis of Terrorist Activities The main terrorist attack of al Qaeda was the 9/11 Bombing of the World Trade Centers, claiming the lives of thousands of people and leading to the beginning of the War on Terror.
- Response to a Hypothetical Terrorist Event Prior to explicit action, the first thing to do in such a situation is to assess the environment depending on the location of terrorists and the type of attack and to outline the civilians that […]
- Biological Warfare and Agro-Terrorism However, the most important thing from which those infected with botulism die is paralysis of the respiratory muscles and the respiratory failure that follows. The bacteria Bacillus Anthracis, which causes anthrax, is one of the […]
- Terrorism Impacts on Policing in Belgium Nevertheless, when studying the world experience of countries facing the threat of high extremist activity and falling victim to attacks by militant fanatics at the beginning of the 21st century, the Belgian government has strengthened […]
- Researching of Morals of Terrorists Terrorism attacks are a form of violence, and the moral implication is death in the form of revenge. Realism is a form of acceptance that everyone on the battlefield is a civilian with their families.
- The Structures, Motivations, and Qualities of Terrorist Groups This implies that the structures of terrorist groups are determined by the capacity and character of the government and society where they operate.
- The Functionalism Theory Assumptions of Terrorism The functionalism theory echoes the candid assumptions of terrorism and further resonates with the evolving terrorism threat. As Barkan outlines, the functionalism perspective postulates that terrorism creates social bonding and solidarity within societies at war.
- Terrorism: Cargo and Passenger Screening To avoid such events, security systems need to be improved by the management both in the field of technological equipment and in the training of professionals.
- Motivations of Lone-Wolf Terrorists The phenomenon of lone-wolf terrorism is an interesting one because it challenges one to attempt to understand the motivation of a person to commit a violent criminal act knowing of the severe consequences.
- Public Policy Issue: Domestic Terrorism At the same time, proponents of the policy argue that the rise of domestic terrorism is due to the failure of holding accountable and confronting the perpetrators by the responsible authorities and not a case […]
- Radicalization and Terrorism in the United States The individuals or self-proclaimed bombers are one of the major threats that the USA will have to be on the lookout for most of the time.
- America: Racism, Terrorism, and Ethno-Culturalism The myth of the frontier is one of the strongest and long-lived myths of America that animates the imagination of the Americans even to this day.
- Terrorism: Domestic, Transnational, and Maritime Forms All types of terrorism are based on the forcible imposition of a worldview, ideology, morality, politics using violence, threats of murder or other forms as the primary means of achieving goals.
- “Terrorism” Is a Biased Term According to Bin Ladin, the bombing of the World Trade Center was an intimidation technique targeting the Americans due to the violence against the Islamic community.
- Terrorism and Data Mining Algorithms However, this is a necessary evil as the nation’s security has to be prioritized since these attacks lead to harm to a larger population compared to the infringements.
- Cyber-Terrorism and International Interventions Most of the cyber-attacks that have occurred involve the direction of the malware and attacks to specific critical systems and Information Technology infrastructures.
- Terrorism and Media Coverage In that regard, the issue of media coverage is specifically important to consider in situations involving hostages, as the media either covering a news report or responding to the terrorists’ demands is in a position […]
- Airfreight Security Breaches and Terrorism The majority of terrorist attacks happened after the 1990s, thereby indicating the deterioration of the security system and breaches in it.
- Terror and Religion One of the common religious terror activities has been on martyrdom, the practice of causing death to oneself on the basis of being a witness to ideological and theological perspectives and beliefs.
- Encryption, Stenography & Cyber Criminal Terrorist The internet and the ICT system as a whole are vulnerable to cyber attacks. This is the method of using to trademark to protect our images and copyright on our intellectual properties.
- Radicalization and Terrorism Phenomena A precursor to radicalization and terrorism is the lack of proper socio-political integration of certain communities in countries. Radicalization lies at the heart of terrorism and plays a central role in the propagation of ideas.
- Boko Haram Terrorist Organization: History and Facts Since the inception of the organization in 2002, the primary goal of Boko Haram has been to impose Islamic rule in Nigeria by promoting a version of the religion that forbids participation in any social […]
- Local Efforts to Counter the Terror Threat in New York City The program encompasses a series of both current and future policy efforts that are associated with the private sector security as well as counterterrorism in the state.
- Cyber-Terrorism and Healthcare Information Systems – Past, Present, and Future The cyber appliances in the health sector then again sustain correspondence amongst shareholders and service providers and as well support resources management.
- Bioterrorism Response by Healthcare Organizations Bioterrorism is a frequently used term that proves human responsibility on the development of its outcomes and effects on people and other living beings on Earth.
- Response to Terrorist Attacks: The Role of Military and Public Sector Entities Nevertheless, to understand the basis of such partnership, one has to understand the actions that the public sector takes and has taken to respond to terrorism in the United States and globally.
- Emergency Operations in Case of Radiological Terrorism An excellent example of an explosion that profoundly affected the Americans is the 9/11 attack that led to the destruction of the Twin Towers and the Pentagon.
- Command Structure of Sharing the Information About Possible Acts of Terror Following the infamous events of 9/11, the government of the United States introduced new strategies and roles that have continued to reshape the roles and involvement of law enforcers in cases of terrorism.
- Bio-Terrorism: When Microbes Become a Threat to Human Existence In general, due to the cooperation of scientists, policymakers, and public agencies across the globe, the international community has recognized the potential of biological weapons and is prepared for the majority of threats.
- How Terrorism Impacts the Human Experience From the point of view of modern definitions or attempts to define these phenomena, the difference is most often established in the globality of the character, duration of the act, and the number of actors […]
- Annotated Bibliography About Terrorism This is a book review article written by Khanna on the book “Terrorism as a war” written by Walter Laqueur and published by Continuum Books.
- Cyberterrorism, Competing Factions, and Possible Course of Action Various aspects can be analyzed concerning cyberterrorism, competing factors, and possible course of actions in corporations to show that cyberterrorism is a legitimate option for the expression of grievances by terrorists.
- Importance of Emergency Response to Terrorist Attack According to the scenario presented, it makes sense to involve the DoD since the terrorists, supposedly AWOLs, pose an extreme threat to the lives of civilians and the military.
- National Response to Terrorism & Natural Disaster The National Response Framework governs the national security and crisis response to dynamic emergencies and natural disasters that occur in the community.
- Terrorism: Definitions, Features Shared by Terrorists However, since there is no agreed-upon definition of a terrorist attack, it is possible to state that some incidents were omitted from the statistics. Terrorism is difficult to combat and requires the input of international […]
- Alienation and Solidarity: The Logic of Suicide Terrorism Pape’s “The Strategic Logic of Suicide Terrorism” discusses the growing prevalence of suicide attacks in the arsenal of terrorist movements from 1980 onward.
- Terrorists and Their Rights Under US Laws The key problems of the research are the ways in which Islamists are protected by the US legislation and society, where the threat comes from, and what the consequences might be.
- Anti-Terrorism Protocol and Counter-Terrorism Units The 1995 Tokyo sarin attack is a case in point because it proved the real possibility of such a scenario and was used as the reference for the L.A. First of all, as shown in […]
- Oklahoma City Bombing as Domestic Terrorist Act The federal building housed the offices of various government agencies, including the Bureau of Alcohol, Tobacco, and Firearms, which was directly involved in the Waco debacle. The attack allowed McVeigh to send a message to […]
- Foreign Fighters and Contemporary Terrorism Finally, recruiters have received access to the vulnerable groups directly, which is demonstrated in the book In the Skin of a Jihadist written by an investigative journalist Anne Erelle.
- Terrorist Attacks: Paul Hanson vs. Patrick Crusius He made some preparations in the form of stockpiling weapons and researching the locations in which they reside. Crusius was more discrete in his information gathering, though it was still the failure of the FBI […]
- Terrorism Liaison Officer’s Responsibilities The analyst was involved in the assessment of the case and contributed to false-positive reporting regarding the journalist and other civilians being terrorists.
- Cyberterrorism: A 21st Century Threat and the Global Response Thus, it can be concluded that terrorism and cyberterrorism have become one of the many global challenges, and for this reason, they should be the object of close attention to the world community.
- Terrorism in the United States of America The group might disintegrate in the future because of its dwindling number of followers, leadership wrangles, and a lack of finances to fund its activities.
- Identifying Terrorism-Related Situations In the selected setting of Philadelphia, the general environment appears to be in control, yet further measures may need to be undertaken to prevent the instances of protests from reaching a state of havoc.
- Task Force and the Fusion Center: Terrorism Prevention Thus, it can be argued that the main task of JTTF in targeted violence prevention is crime investigation and intelligence generation.
- Fusion Centers: The Role in Terrorism Prevention Boston Globe reports that the information-sharing system currently in use is not efficient in preventing terrorism, highlighting the fact that the FBI and the CIA probes of Tamerlan Tsarnaev were unbeknown to Massachusetts counterterrorist units.
- DHS and Intelligence: Terrorism The organization of the fight against terrorism requires a comprehensive approach to the analysis of the sources and subjects of terrorist activity, a clear definition of the functions and areas of responsibility of each item […]
- The Molly Maguires as a Domestic Terrorism Group It is these origins of the Molly Maguires terrorist group that gave them their thirst for blood and led to the killing of a myriad of Irishmen until the group was exterminated in the proximities […]
- Australian Anti-Terrorism Laws In the quest to protect citizens, some governments have gone to the extend of inflicting torture on terror suspects in need to obtain some information from the suspect, which raises concern about the suspect’s civil […]
- Bioterrorism Preparedness and Public Health Response Therefore, the current state of the preparedness cannot be estimated as high or sufficient, and the approach needs to be elaborated.
- Aggressive Behavior Among the Al-Shabaab Terrorists The former are the underlying sources that propel susceptible individuals to radicalization, while the latter are the incentives that the terrorist groups offer to attract and retain recruits.
- War on Terrorism: Budget and Policy Discussion The discussion of the specific Acts and Policies directed at USA security is going to be considered with the purpose to follow the changes which occurred in the USA after 9/11 attacks.
- Criminology: Terrorism–Security Policy for Large Events This attack proved to the government the vulnerability of the state concerning external threats, especially because, prior to the attack, the customary means of attack had been the use of military force as evidenced in […]
- Causes of Terrorism Terrorism is defined as violent actions that are aimed at instilling fear to people as a means of coercing them to submit to ideologies of a certain group.
- Violent Resistance and Terrorism The following study is an attempt to establish the root causes of violent resistance, the challenges facing the world due to violent resistance, and possible remedies to the problem citing specific cases that are helpful […]
- Terror Groups – Abu Nidal Organization Abu Nidal is the Arabic meaning of ‘father of the struggle.’ The terror group was named after its leader and founder Sabri al-Banna who was born in Palestine to a land owning family. Among the […]
- Impacts of Terrorism on Police Mission in the U.S. The incidence of September 11 2001 has remarkably transformed the police force in the U.S. There is an increase in the level of monitoring of international travels and boundaries by the police force.
- Homeland Security: Digital Crime and Terrorism Activities However, the US law enforcement system is characterized by the activities of different agencies, including the Federal Bureau of Investigations, Department of Homeland Security, Secret Service, Immigration and Customs Enforcement.
- Understanding the Basics of Terrorism On the other side of the rail is another man lying flat on the ground with a sniper rifle in his hands ready to wreak havoc.
- “Policing Terrorism” by Waddington He is of the argument that case-specific policing is focused on the outcome of court verdicts. He points out an incident in which the palace security was breached, and the commissioner of police reacted to […]
- Definite Paths to Terrorism: Main Dimensions This assimilation is enforced by the use of violence to instil discipline and loyalty in the participants. In conclusion, there are other dimensions of the Islamic terrorism namely Al-Qaeda and Hezbollah.
- War on Terror: Propaganda and Freedom of the Press in the US There was the launching of the “Center for Media and Democracy”, CMD, in the year 1993 in order to create what was the only public interest at that period. There was expansive use of propaganda […]
- Terrorism and U.S. National Security Thomas Jefferson was the author of the Statute of Virginia for religious freedom in the year 1777 as well as the author of the famous United States Declaration of independence in the year 1776.
- Domestic Terrorism: Trends, Challenges, and Future Predictions Under the provisions of the US PATRIOT act, acts of domestic terrorism entail dangerous acts that pose a threat to human life and amount to a violation of various criminal laws of the US and/or […]
- Organizations Convincing to Become a Suicide Terrorist One of the underlying tenets taught to candidate suicide bombers is: “Islam is the answer and jihad is the way”. Pathological altruism refers to any behavior or personal tendency in which ‘the goal or motivation […]
- Bioterrorism: Term Review According to Meinhardt, “water supplies and water distribution systems represent potential target for terrorist activity in the United States because of the critical need for water in every sector of our industrialized society”.
- US & UK Human Rights While Countering Terrorism The threat of terror and the further legal reactions of the nations to the problem were considered as challenging, and it is necessary to examine differences and similarities associated with the promotion of human rights […]
- Organizational Change: Models Influencing American Terrorism This paper seeks to discuss the three models of terrorism, the effects of international terrorism locally, and the impacts of international terrorism on local cell groups.
- The Goal of a Terrorist Attack This objective is being accomplished by the mean of exposing people to the graphic accounts of terrorist acts-in-making, as was the case with the attacks of 9/11.
- Local Response to Terrorism Local response to terrorism involves using the resources and the law enforcement officers at the state and county level to detect and prevent acts of terror.
- Adjusting to Terrorism: The Issue of Detention Without Trial The country also needs to train more prosecutors and legal experts so that justice is disseminated to suspected terrorists who continue to be held at Guantanamo Bay without trial.
- Biological Terrorism: Dealing With the Threat It is therefore the responsibility of the recipient of this information to take action to secure his/her life against the potential lethality of the agent in question.
- The Maritime Terrorism Risk and Liability The research describes in detail aspects of maritime terrorism but does not clearly state the research question to be explored. However, in the summary part of the research paper there is several questions implied as […]
- Bioterrorism Preparedness in Healthcare Organizations It is also necessary to carry out a test on the public health emergencies for this would help the department to be aware of the strengths and weaknesses which are in the system.
- Adjusting to Terrorism In the US, the Department of Homeland Security is the primary body that deals with all matters of homeland security, including the prevention of terrorism. As such, the department needs to address it as a […]
- Impact of Terrorism on the Economy The premise of the essay is to evaluate the nature and the nature and the severity of the risks posed by terrorism on IFAD a United Nations specialized agency.
- A Criminal Justice Approach to Suppressing Terrorism The threat of terrorism substituted communism as the rationale which was used for justifying the state of emergency in America prior to 1990s.
- Comparison Between Organized Crime And Terrorism Organized crime refers to unlawful activities conducted by members of highly organized gangs and associations. Its defined by members and activities of a group.
- Boilover: Fire Aspects of the World Trade Center Terrorist Attacks Analysis These includes the intensity of the incident heat on the burning object, the composition of the burning fire, the ability of air that supports combustion to reach the burning fire, the mass of the burning […]
- Secure Transportation System Against Global Terror The good news is that cooperation, coordination, and new technology can be used to secure the global transportation system and halt the activities of terror groups.
- Sharing Terror Data: Criminal Analysis The FBI continuing investigation of the attacks to identify the hijackers and their sponsors, codenamed “PENTTBOM,” represents the largest investigation ever in the history of the agency.
- Torture and War Towards Terrorism An example of mental torture can be explained by the following; Y is a friend to X, they have been caught in the same crime act, Y is then taken to a separate room adjacent […]
- Women and Terrorism Relations The role of women in secular terrorist organizations has been more pronounced in history due to the conservative nature of religious terrorist movements, which often exclude women from their ranks.
- Terrorism: Assessing the Past to Forecast the Future The terrorists groups all over the world, having the knowledge of lethargic weapons held by their enemies, are engaged in the discoveries of how the rapidly growing technology may improve the lethargy of their current […]
- Terrorism Response Strategy The preliminary assessment is performed on the basis that before implementing any rescue operations, the hazards that are contained in the area must be positively identified and the resources available or necessary to deal with […]
- Homeland Security and Terrorism The important root causes of terrorism are mainly two: a perceived sense of social & political injustice such that the group seeks to right the wrong and, the view that violence is the only way […]
- Terrorism Preparedness and Response The third and most important step to take is to switch off the available electrical gadgets to prevent the spread of fire. Of importance to prevent such catastrophes is cooperation from citizens, media, and the […]
- Terrorism Mitigation and Risk In order to avert the danger of possible portable nuclear attacks, it is important to assess the possibility and impact of attacks in the first place.
- Terrorism Risk Assessment: Threat of Al Shabaab and Hezbollah to the USA Attacks such as those that happened outside the US and more are likely to occur due to what Hezbollah perceives as the US posing a threat to its ties with Iran.
- Four Priorities of Action for Combating Terrorism on Our Shores There is therefore the need to employ new pragmatic foreign policy steps that promote the national interest within the broader values of international peace and security if any gains are to be realized in the […]
- The Cyber Terrorism Plan and Counter Strategy The news of hacking the website of the Pentagon will immediately get the attention of the media and this message will spread everywhere at the speed of light.
- The Potential for State Sponsored Terrorism Also, he mainly tries to bring all the enemies of the United States together and he believes that the United States is a devilish country.
- Bioterrorism and Biosecurity The epidemiology of the infection is spread in the world evenly though in some of the parts there is only one form of Anthrax, for instance in the United States of America and therefore our […]
- Bioterrorism and Biosecurity – Aum Shinrikyo The Aum Shinrikyo began their attacks in 1994 in Matsumoto where they used the refrigerator truck to release sarin near the homes of three judges who were overseeing a lawsuit that was predicted to go […]
- Terrorism: A Definition and Analysis The Federal Bureau of Investigation defines terrorism as the perpetration of violence and force unlawfully against people or property with a sole aim of intimidating or coercing the government or the targeted population or any […]
- International Political Economy, Democratization, and Terrorism IPE describes the global power dynamics that control international trade and finance, fuel globalization, and wealth distribution across the globe. Sachs argues that globalization and the emergence of political economics have led to the increased […]
- Terrorism Definition at the National Level The development of a unified definition of terrorism at the global level is challenging because the domestic laws of several countries differ significantly.
- War and Terrorism in the Modern World They are used to frighten the public and pursue political goals, for example, to change the government in the country. For instance, acts of terrorism are meant to inflict fear and intimidation to put pressure […]
- Sociology. Terror and Violence Impacts A comparison between theory and the actual case is made in order to promote the claim that terror leads to mental health issues that will pursue the victims for the whole life, but such consequences […]
- US and Terrorism Relations Overview The US and its allies intensified attacks on ISIS bases and areas of control, assassinated ISIS leaders, reclaimed regions captured by the group, cut off their supply of funds, and imposed restrictions on travel to […]
- Agro-Terrorism: Definition and Impacts The ultimate objective for agro-terrorism is to cause economic damage and lead to loss of confidence among the population in the government. It is the responsibility of the FDA and DHS Agro division to monitor, […]
- Terrorism and Trauma in American Literature Key points that are brought up for discussion in both books are the crisis of communication, the crisis of meaning, the crisis of self-identification, and possible ways out. The letters are a part of the […]
- War on Terror: The Battle Continues The levels of political tension have skyrocketed over the past several decades, causing the instances of confrontations and the number of acts of terror to rise, hence the launch of the War on Terror in […]
- Terrorism Nowadays: Islamic State of Iraq and Syria The cases of terrorism and the transformation of the international situation over the past 20 years make people realize the global nature of the current events.
- How Terrorism Affects Airline Security Additionally, agencies that oversee aviation changed their course and became much more stringent in their enforcement of security to avoid a repeat of the incident.
- What Makes Terrorism Different From Other Forms of Violence The purpose of this paper is to define terrorism and identify the crucial features that distinguish terrorism from different types of abuse.
- Terrorist Networks as a Threat to the United States Today One of the most notorious acts committed by the representatives of the eco-terrorist movement is the 2001 arson of the University of Washington.
- Consequence Management and Terrorist Attacks Analysis It is suggested that the focus of the effort once an incident occurs should be on minimization of the consequences to the society and infrastructure, evoked by the emergency.
- Terrorist Groups’ Establishment: The Theory of Four-Wave Terroristic Groups
- Domestic & Global Terrorism and Its legal Aspects
- Crime Myths and Domestic Terrorism
- Terrorist Attacks in Paris, 13th November 2015
- Hue Newton: A Terrorist and a Thinker
- Impact on Terrorist Activities of Regional Governments
- Regional Terrorism: The Bali Bombing, Australian and Indonesian Responses
- How to End Terrorism: Diplomacy or Military Action?
- Terrorism: Methods and Weapons
- Terrorism: Analysis of Definitions
- Screening for Terrorist for Aviation Security
- The Role of Hashemite Kingdom of Jordan in the Fight Against Terrorism
- Terrorist Event Countering: First Responders Risk
- Financing Terrorism: Challenges and Solutions
- Hashemite Kingdom of Jordan and Terrorism
- Domestic Terrorism: A Comparative Analysis with Hate Crimes
- Al Shabaab: An Intriguing Example of Islamist Terror
- Causes and Motivations of Terrorism
- Ali Al-Timimi’s Case of Terrorism
- “The Lessons of Terror: A History of Warfare Against Civilians” by C. Carr
- Biological and Chemical Terrorism: Preparedness and Response
- Legislation Related to Bioterrorism
- Israel’s Response to Munich Terror Attack
- Bioterrorism and Its Harmful Consequences
- Domestic Terrorism in the US: Causes, Impacts, and Countermeasures
- The Evolution of Terrorism on the World Stage
- Terrorism and Liberal Democracy: What We Should Know
- Michael Collins and His Terrorist Method
- Biological Weapon and Bioterrorism
- Is Terrorism Still the Most Important Security Issue for Australia?
- War on Terror and Its Effect on Individual Right
- Crimes Against the State: Terrorist Attacks and Death Penalty
- “Nuclear Terrorism: Risks, Consequences, and Response” by Jim Walsh: Stimulating Ideas, Logical Organization, Engaging Voice
- Middle-East and Africa Terrorist Movements
- The History of Ku Klux Klan: A Terrorist Organization Founded in the Southern States After the American Civil War
- The Use of Counter-Terrorism Attacks During the Algerian War of Independence From F.L.N.
- Comparison Between Secular and Religious Terror
- Political Violence and Terrorism. Crowd Behavior
- Types of Terrorism: Centers Establishment
- Sociology of Terror: Contemporary Sense
- Understanding the War on Terror in the United States
- Foreign Policy Challenges Created by the War on Terror
- Middle-Eastern and African Terrorist Movements
- Bioterrorism: Impact of Science and Technology
- Community Policing and War on Terror
- Biosecurity and Bioterrorism
- Palestinian Islamic Jihad: Radical Terrorism
- Money Laundering and Terrorist Finance
- Pakistan’s Double Game in the War on Terror
- Eradicated Terrorism in the World
- The Interrelation Between Terrorism and Technology
- War on Terror & Violation of Constitutional Rights
- Media and the War on Global Terrorism
- Is the Geneva Convention Applicable to War on Terror?
- Adjusting to Terrorism in Modern World
- Death Sentence to Muslim Terrorists: Should We Murder People Who Had Done the Same Before?
- Terrorism and Security Issues Review
- How Terrorist Have Financial and Recruitment Growth Since 1980
- Recent Developments in the History of Terrorism
- War on Terror. 42-Day Detention: An Equitable Solution?
- Early Response to Weapons of Mass Destruction Terrorism
- Counter Terrorism Measures in the UK
- The War on Terrorism in the United States
- United States & EU Efforts to Fight Terrorism
- Global Terrorism and State Security Measures
- American Governmnet Against the Threat of Terrorism
- “Terrorism and Economic Security” by Robert L. Hutchings
- Bioterrorism and Health Care Delivery
- Terrorism: Countering and Responding to the Treat
- Crimean Crisis and Russian State Terrorism
- A Terrorist Attack on Atlanta, Georgia
- How Counselors Assist Survivors of Terrorism
- Comprehensive Terrorist-Related Screening Procedures
- Terrorism and National Security
- The Functioning of Terrorist Groups
- Terrorist Organization: Euskadi Ta Askatasuna (ETA)
- “Terror and Democracy at the Age of Stalin” by Goldman
- Terror in the Mind of God by Mark Juergensmeyer
- Counter Terrorism and Public Awareness Plan
- Organized Terrorism Against Government Leaders
- War on Terror and Its Victory Meaning
- Terrorism Definitions by the Global Community
- Terrorist Attack: Contemporary Social or Cultural Issues
- Poverty as a Factor of Terrorist Recruitment
- War on Drugs and Terror and American Promise
- Hazard Vulnerability Analysis and Terrorism
- Terrorist Participation and Its Motives
- The UAE Against Money Laundering and Terrorism Financing
- Cyberterrorism as the Greatest Risk for the US
- Cultural Miscommunication and Hostility Against Muslims
- Domestic Terrorism and Homegrown Extremism in the US Criminal Justice System
- The Rise of Terrorist Organisations in Post-Invasion Iraq
- Factors That Motivate to Terrorism
- State-Sponsored and Non-State Terrorism
- Terrorism, Human Trafficking, and International Response
- Internet Crimes and Digital Terrorism Prevention
- Vietnam War vs. War on Terror in the Middle East
- Ideology and Terrorism: Rights from Wrongs?
- Islamic and Christian Religion and Terrorism
- American War on Terror and Operational Strategies
- Death Penalty for Murder by Terrorism
- Local Operational Planning for Potential Terrorist Threats
- Terrorism Preventive Measures in the United States
- Aum Shinrikyo Terrorist Group’s Activity
- Bioterrorism Attacks and Nursing Countermeasures
- Terrorism Prevention on the International Level
- Violent Extremism and Suicide Terrorist Attacks
- Al-Qaeda Emergence, Ideology, and New Terrorism
- Terror Attacks and Intelligence Community in the US
- Distressed Terrorism: Politics, Religion and Ideology
- War on Terror: Critical Terrorism Studies’ Views
- Egyptian Tourism Industry and Terrorism Effects
- Islamic State Global Terror Threat Countermeasures
- War on Terror in Saudi Arabia and Arab Gulf States
- Terrorist Groups: Critical Discourse Analysis
- US Intelligence to Prevent Terrorist Attacks
- Terrorism: Power of the Islamic State of Iraq and Syria Power
- Female Terrorism: Causes and Features
- Terrorism: the Evolution of ISIS
- Cyber Security’s and Counter Terrorism’ Intersection
- Digital Media Usage to Recruit and Promote Terrorism
- Modern Terrorism and Globalization
- Stereotyping Terrorists and Mental Sanity
- Homeland Security Changes: Adjusting to Terrorism
- China in 1950-53: “Paternalist Terror” by J. Strauss
- Human Trafficking as a Terrorist Activity
- Coping with Terrorism in the USA
- Terrorism in the Middle East
- Contemporary Terrorism: The American Army Special Forces
- Countering Terrorism: The US Intelligence Community
- Terrorism and Its Organisations: Al Qaeda and ISIL
- First Responders to Terrorist Attack
- The Westgate Terror Attack in Kenya
- Current Hurdles in Combating Terrorism
- Ethnic, Racial and Religious Profiling in Terrorism
- Halal Food and Terrorist Organizations in Australia
- Osama Bin Laden’s Role in Terror
- Hospitals Security Upgrade: Terrorist or Criminal Actions
- International Counter Terrorism’ Elements
- Bioterrorism: Biological Agents as Weapons
- Terrorism: The Islamic State of Iraq and the Levant
- Terrorism: Post-9/11 Maritime Security Initiatives in the USA
- Bio-Terrorism Preparedness and Response
- Jonathan Moreno: Bioethics After the Terror
- What is the Best Way for Fighting Terrorism According to Mortenson?
- The Advanced Community Planning in Response to the Potential Threat of Terrorism
- The Impacts of the Intelligence Reform and Terrorism Prevention Act of 2004 on the National Intelligence Community
- War on Terrorism: How to Cope With the Global Threat?
- The Primary Causes of Terrorist Political Violence
- Rumsfeld’s Memo & The War on Global Terrorism
- Terrorism Handling in Our Life
- Defense Imperatives: “Thwarting Terrorism & Bringing Terrorists to Justice”
- Understanding the Failure of the Global War on Terrorism and Suggestions for Future Strategies
- Counter-Terrorism and the Patriot Act
- Al-Qaeda as a Terrorist Organization
- Human and Technical Intelligence in Countering Terrorism
- Financial Markets After Terrorist Assault and The Enron Financial Outrage
- Terrorism, Counter-Terrorism, and Intelligence
- Lessons From the Mumbai Terrorist Attacks
- Proliferation of Nuclear Weapons to Rogue States and International Terrorists
- Does Poverty Lead to Terrorism?
- Terrorism and Jihadist Movement
- US Exceptionalism in Constructing and Conceptualizing a Terrorist
- American Exceptionalism in Constructing and Conceptualizing a Terrorist
- History of Cyber Terrorism
- Economic Concerns in the Aftermath of Terrorism
- Terrorism in International Relations
- Terrorism in Israel and Palestine
- Local, State, and Federal Partnerships: Terrorism
- Hezbollah: A Terrorist Organisation?
- United States Domestic Terrorism
- International Terrorism: The Challenge to Global Security
- Salafist Takfiri Terrorism
- Anti Money Laundering and Combating the Financing of Terrorism
- Weapons of Mass Destruction: The Terrorist Threat
- Terrorists’ Usage of Chemical or Biological Agents
- Cyber Security Threat Posed by a Terrorist Group
- The Effect of Terrorism on Human Rights: The Clash Between the Human Rights Advocates and Victims of Terrorism
- Eliminating Terrorism at the Domestic Level
- Terrorism, Poverty and Financial Instability
- United States War on Terror Policy
- The Real Cause of Terrorism in Palestine
- Terrorism: Searching for a Definition
- Industrial Terrorism in Modern World
- Terrorist Cells and Groups Within the Northern Region of Africa
- Terrorism as a Communication Strategy
- How the U.S. Can Combat the Terrorist Threat in Africa?
- Hypothetical Scenario of a Terrorist Attack
- Terrorism Before and After the September 11 Attacks
- U.S. War in Afghanistan: Pros and Cons
- Orientalist Constructions of Muslim Bodies and the Rhetoric of the «War on Terror»
- The U.S. Government Strategies Against the Terrorist Threats
- How Readily Terrorists Can Acquire Nuclear Weapons
- Post September 11, 2001 Terrorist Attacks
- Civil Liberties, Habeas Corpus and War on Terror
- Concept of Terrorism Phenomenon in Modern World
- The Spectacle of Terror
- Foreign Policy: United States and Fight with Terrorism
- Law Enforcement and Terrorism
- What New Demands on Policing Have Resulted From the International ‘War on Terror’?
- Religious and Secular Terrorism: Analyzing Differences and Points of Intersection
- Terrorist Acts Prevention and Aftermaths Minimization
- Torture During the Algerian War and Its Relevance on the War on Terror
- The Definition of Terrorism
- International Terrorism: The Operations of the Hezbollah
- The Psychological Explanation of Terrorism
- The Kurdish Conflict in the Middle East
- The US Anti-Terrorism Efforts Are Failing
- The Media and Terrorism
- Terrorist Groups in Turkey
- Terrorism: The United States’ Involvement
- Terrorism: Can Terrorism Ever Be Justified?
- America’s War on Terrorism
- Terrorism in Political Protest
- Cause and Effect of Terrorism
- Impact of Terrorism on Italian Economy
- “What Is the Definition of Terrorism? And Why Is the White House Afraid of Using the Term?” by Timothy Kelly
- Habeas Corpus and the War on Terror
- Civil Liberties, Habeas Corpus and the War on Terror
- Benefits of Preparing for Emergencies and Terrorism
- Preparing for Incidents of Terrorism at the Local Level
- Domestic Terrorism in the Post 9/11 Era
- Eco-Defense and Kinds of Ecological Terrorism
- Bush Doctrine, Explanation of the Administration and War on Terror
- Moral Convictions of Terrorists
- Why Terrorism is a Contested Concept
- Presidential Powers and the War on Terror
- Agro-Terrorism: The Lessons to Learn
- Terrorism: The War on Iraq
- Stereotyping Comparison: All Italians Are in a Mob, All Jamaicans Smoke Weed, All Muslims Are Terrorists
- The Al-Qaida Terrorist Group’s Recent Happenings
- The Fight Against Terrorism by Christian and Islam Leaders
- Is Terrorism Ever Justified?
- The War on Terrorism
- The Terrorist Attacks in the United States
- Analyzing the Concept of Terrorism
- The Problems of Terrorism in Modern World
- Counter-Terrorism Plans Development
- Consequence Management After the 9/11 Terrorist Attacks
- Intelligence Reform and Terrorist Prevention Act
- Terror and Terrorism
- September 11: Terror Attack and Huge Casualties
- The Concept of Terrorism
- Homeland Security: Collecting Information about Terrorism
- Terrorists and the Left and Right: Definitions & Examples
- Should the USA Use Drones to Combat Terrorism?
- How Are Terrorists Financing Their Acts of Terrorism?
- What Can History Teach Us About Terrorism?
- Why Do Americans Feel More Sympathy for Western Terrorism?
- How Can the United States of America Better Defend Itself Against Terrorism?
- Can the U.S. Prevent Future Acts of Domestic Terrorism?
- What Has Been the Effect of Globalization on Terrorism?
- How Can Businesses Cope With Terrorism?
- Can Democracy Stop Terrorism?
- Should the U.S. Government Be Scared of Cyber Terrorism?
- Why Does Western Europe Experience More Terrorism Than America?
- Are Terrorism and Globalization Linked to Politics?
- What Are the Causes of Terrorism, and How Can It Be Stopped?
- Are Muslim Communities Affected by Counter-Terrorism Legislation?
- Does American Foreign Policy Cause Terrorism?
- Does the Media Encourage Terrorism?
- Does the Terrorism Act Infringe Upon Our Human Rights?
- What Challenges Are Posed by International Terrorism to Democracy?
- How Can the Digital World Lead to a New Type of Terrorism?
- Whose Support Matters for the Occurrence of Terrorism?
- How America Prevents Terrorism?
- Does Higher Education Decrease Support for Terrorism?
- Can Foreign Aid Dampen the Threat of Terrorism to International Trade?
- Should Americans Fear Urban Terrorism?
- Can Illegal Immigration Lead to Terrorism?
- Does Distinguishing Domestic Terrorism From International Terrorism Help?
- Will the American Economy Benefit From the War Against Terrorism?
- Are Some Rights Negotiable When It Comes to Fighting Terrorism?
- Why Has Terrorism Become Such an Important Issue Over the Last 40 Years?
- Will Terrorism Lose Its Significance?
- Islam Topics
- Organized Crime Titles
- Islamophobia Paper Topics
- Nuclear Weapon Essay Topics
- Sunni Islam Paper Topics
- Torture Essay Ideas
- North Korea Titles
- Racial Profiling Essay Topics
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, March 3). 528 Terrorism Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/terrorism-essay-examples/
"528 Terrorism Essay Topic Ideas & Examples." IvyPanda , 3 Mar. 2024, ivypanda.com/essays/topic/terrorism-essay-examples/.
IvyPanda . (2024) '528 Terrorism Essay Topic Ideas & Examples'. 3 March.
IvyPanda . 2024. "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
1. IvyPanda . "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.
Bibliography
IvyPanda . "528 Terrorism Essay Topic Ideas & Examples." March 3, 2024. https://ivypanda.com/essays/topic/terrorism-essay-examples/.

Presentations made painless
- Get Premium
116 Terrorism Essay Topic Ideas & Examples
Inside This Article
Terrorism has become a major global issue in recent years, with attacks happening all around the world. It is a complex and multifaceted problem that requires a deep understanding of its causes, consequences, and potential solutions. If you are tasked with writing an essay on terrorism, it can be challenging to come up with a topic that is both interesting and relevant. To help you get started, we have compiled a list of 116 terrorism essay topic ideas and examples that you can use as inspiration for your own writing.
- The rise of terrorism in the 21st century
- The impact of terrorism on global security
- The role of technology in modern terrorism
- The psychology of terrorism: understanding the motives of terrorists
- Terrorism and religion: exploring the link between faith and violence
- The effectiveness of counterterrorism strategies
- The role of social media in promoting terrorism
- The impact of terrorism on tourism and the economy
- The ethics of using drone strikes to combat terrorism
- The role of the media in shaping public perceptions of terrorism
- The relationship between terrorism and organized crime
- The impact of terrorism on human rights and civil liberties
- The role of intelligence agencies in preventing terrorist attacks
- The history of terrorism: from the French Revolution to the present day
- The impact of terrorism on mental health and well-being
- The role of propaganda in promoting terrorist ideologies
- The impact of terrorism on children and families
- The role of education in preventing radicalization and extremism
- The impact of terrorism on refugee populations
- The role of women in terrorist organizations
- The impact of terrorism on religious minorities
- The role of NGOs in providing support to victims of terrorism
- The impact of terrorism on the environment
- The role of cybersecurity in preventing cyberterrorism
- The impact of terrorism on healthcare systems
- The role of international organizations in combating terrorism
- The impact of terrorism on social cohesion and community relations
- The role of law enforcement agencies in preventing terrorist attacks
- The impact of terrorism on freedom of speech and expression
- The role of diplomacy in addressing the root causes of terrorism
- The impact of terrorism on the education system
- The role of the United Nations in promoting peace and security
- The impact of terrorism on the rights of indigenous peoples
- The role of technology in detecting and preventing terrorist attacks
- The impact of terrorism on the rights of LGBTQ+ individuals
- The role of the private sector in preventing terrorism
- The impact of terrorism on urban planning and infrastructure
- The role of the judiciary in prosecuting terrorists
- The impact of terrorism on cultural heritage and monuments
- The role of community policing in preventing radicalization
- The impact of terrorism on the rights of migrants and refugees
- The role of the European Union in combating terrorism
- The impact of terrorism on the rights of prisoners and detainees
- The role of social movements in countering extremist ideologies
- The impact of terrorism on the rights of persons with disabilities
- The role of interfaith dialogue in promoting peace and understanding
- The impact of terrorism on the rights of women and girls
- The role of emergency response agencies in responding to terrorist attacks
- The impact of terrorism on the rights of older persons
- The role of non-state actors in promoting violent extremism
- The impact of terrorism on the rights of children and youth
- The role of cultural diplomacy in countering terrorist narratives
- The impact of terrorism on the rights of indigenous women
- The role of intelligence sharing in preventing terrorist attacks
- The impact of terrorism on the rights of journalists and media workers
- The role of religious leaders in promoting peace and tolerance
- The impact of terrorism on the rights of refugees and asylum seekers
- The role of civil society organizations in countering violent extremism
- The impact of terrorism on the rights of persons with HIV/AIDS
- The role of peacebuilding initiatives in preventing conflict and violence
- The impact of terrorism on the rights of persons with mental health conditions
- The role of youth engagement in promoting social cohesion and resilience
- The impact of terrorism on the rights of persons with albinism
- The role of gender equality in countering extremist ideologies
These essay topic ideas and examples cover a wide range of issues related to terrorism, and can serve as a starting point for your research and writing. Whether you are interested in exploring the causes of terrorism, analyzing the impact of terrorist attacks on different populations, or evaluating the effectiveness of counterterrorism strategies, there is a topic on this list that will pique your interest. Remember to approach your essay with an open mind, and to consider multiple perspectives and sources of information as you delve into this complex and challenging subject.
Want to research companies faster?
Instantly access industry insights
Let PitchGrade do this for me
Leverage powerful AI research capabilities
We will create your text and designs for you. Sit back and relax while we do the work.
Explore More Content
- Privacy Policy
- Terms of Service
© 2024 Pitchgrade
- How it works

Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Terrorism Dissertation Topic Ideas
Published by Owen Ingram at January 5th, 2023 , Revised On May 21, 2024
Terrorism is a major global threat to public safety and security. It is an unlawful use of violence and intimidation to achieve political, ideological or religious goals. Terrorist attacks are always extremely devastating and have the potential to cause significant destruction, fear, injury and even death.
Terrorists employ many tactics, including bombings, hijackings, hostage takings, assassinations, cyber-attacks and more. The impact of terrorism on society is widespread, as it can cause economic damage by disrupting financial markets, creating social unrest through fear-mongering and creating long-term psychological trauma for affected individuals or communities.
Governments worldwide have implemented various initiatives designed to tackle this type of crime, but terrorist groups continue to operate across international borders with impunity.
Conducting research on terrorism is an essential aspect of a student’s dissertation and understanding of terrorism-related topics. In order to develop a comprehensive understanding of this complex field, students should dedicate time to researching the phenomenon of terrorism and its implications for national security.
In today’s world, terrorism has become one of the most pressing issues faced by countries all over the globe. Thus, it is important for students to be knowledgeable about current events and how they relate to global security.
Developing a solid analytical outlook on terrorist groups, their goals, and objectives can open up new opportunities in national security policy-making and counter-terrorism initiatives. Moreover, it can help develop comprehensive solutions aimed at curbing terrorist activity in areas around the world that are prone to violence.
How Should Students Choose Terrorism-Related Dissertation Topics?
When it comes to topics related to terrorism, this task becomes even more difficult as many complex and diverse topics can be investigated. Students should consider certain factors while choosing their dissertation topic to ensure they have chosen an appropriate and practical research area.
First, students should identify what area or field they wish to focus on for their dissertation. For example, suppose a student is interested in researching international terrorism. In that case, they should look for potential research topics related to this field, such as analysing terrorist networks or understanding state responses towards transnational terrorist organisations.
Students can also look on more specific areas, such as examining the role of social media in recruiting individuals into terror networks or looking at counter-terrorism strategies employed by different countries around the world.
Trending Terrorism Dissertation Topics List
- Are counter-terrorism strategies effective? The results of the Campbell systematic review on counter-terrorism evaluation research
- Combating terrorism: strategies of ten countries
- Rethinking Nigeria’s counter-terrorism strategy
- Common threat and common response? The European Union’s counter-terrorism strategy and its problems
- Credibility in the global war on terrorism: Strategic principles and research agenda
- A strategic framework for terrorism prevention and mitigation in tourism destinations
- From convergence to deep integration: Evaluating the impact of EU counter-terrorism strategies on domestic arenas
- Counter-terrorism strategies in Indonesia, Algeria and Saudi Arabia
- Hard versus soft measures to security: Explaining the failure of counter-terrorism strategy in Nigeria
- Putting terrorism in context: Lessons from the Global Terrorism Database
- What is domestic terrorism? A method for classifying events from the global terrorism database
- Characterising chemical terrorism incidents collected by the global terrorism database, 1970-2015
- Machine learning techniques to visualise and predict terrorist attacks worldwide using the global terrorism database
- The impact of terrorism on financial markets: An empirical study
- The impact of terrorism and conflicts on growth in Asia
- The economic impact of terrorism from 2000 to 2018
- The impact of terrorism on European tourism
- The impact of terrorism on Italian employment and business activity
- Impact of terrorism on economic development in Pakistan.
- Psychological impact of terrorism on children and families in the United States
- The impact of terrorism on the brain and behaviour: what we know and what we need to know
- Terrorism, the future, and US foreign policy
- Jewish terrorism in Israel
- Israel–Palestine: One State or Two: Why a Two-State Solution is Desirable, Necessary, and Feasible
- The Terrorism Acts In 2011: Report of the Independent Reviewer on the Operation of the Terrorism Act 2000 and of Part 1 of the Terrorism Act 2006
- The Rise of Lone Wolf Terrorism in the Age of Social Media
- Far-Right Extremism and Domestic Terrorism
- The Role of Online Propaganda in Radicalisation and Recruitment by Terrorist Groups
- The Intersection of Cyberterrorism and Critical Infrastructure
- The Impact of Drone Warfare on Counterterrorism Strategies and Civilian Casualties
- The Psychological Impact of Terrorism on Victims and First Responders
- The Legal Challenges of Prosecuting Terrorists
- The Impact of Foreign Intervention on State Formation and the Rise of Terrorism
- The Integration of Refugees and the Prevention of Radicalisation in Host Countries
- The Use of Narrative Analysis in Understanding the Motivations of Terrorists
- The Effectiveness of Soft Power Strategies in Countering Terrorism and Promoting Peace
Also read: Dissertation Topics on Ukraine, Russia and NATO Conflict , Dissertation Topics on USA’s Withdrawal From Afghanistan , International Relations and Geopolitics Dissertation Topics , International Development Dissertation Topics , Criminal Psychology Dissertation Ideas .These subject topics will help you in getting dissertation research ideas, if you are studying in any mentioned subject.
How Can ResearchProspect Help?
ResearchProspect writers can send several custom topic ideas to your email address. Once you have chosen a topic that suits your needs and interests, you can order for our dissertation outline service which will include a brief introduction to the topic, research questions , literature review , methodology , expected results , and conclusion . The dissertation outline will enable you to review the quality of our work before placing the order for our full dissertation writing service!
What are the Benefits of Choosing a Good Terrorism Dissertation Topic?
Choosing the right topic for a dissertation on terrorism can be difficult. However, considering the various factors associated with it can help make the decision more accessible and beneficial to students.
A good terrorism dissertation topic should be relevant, engaging and unique enough to stand out from other written works in the field. It is also essential to address an issue or question that has yet to be looked at in depth.
In addition to helping students build their research skills, choosing an effective dissertation topic on terrorism will allow them to explore an area of interest in depth and develop a better understanding of complex issues related to this subject matter.
Students should also remember that selecting a current issue or one with potential implications for national security is likely to attract greater interest from potential employers or universities when applying for jobs or further study opportunities.
What are some terrorism dissertation topics for students?
In the article above, there are multiple dissertation topics related to terrorism. You can choose any of them. A few areas explored include:
- Counterterrorism,
- Global governance,
- Conflict resolution
Are these dissertation topics unique?
Yes, all these dissertation topics are unique. But other students might have used them. You can take help from our dissertation topic services to get a unique topic for your terrorism dissertation.
What are the benefits of using the dissertation topic service?
The most beneficial part of dissertation topic services is that they offer help from experienced professionals with extensive knowledge in the field of research. This includes an initial consultation to discuss ideas, direct access to resources and databases, advice on turning those ideas into concrete topics, and suggestions on organising a literature review or methodology.
You May Also Like
Disasters can potentially be quite dangerous to the continued existence of humans on Earth. Therefore, it is crucial to develop fresh, cutting-edge approaches to managing the damage caused by natural disasters.
Portfolio management examines the projects and programs of an organization. There are three aspects involved here: selection, prioritization, and control. This is done by taking into account the strategic goals of the organization.
Need interesting and manageable HRM dissertation topics or thesis? Here are the trending HRM dissertation titles so you can choose the most suitable one.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
- Abuse Topics Topics: 434
- Veterans Essay Topics Topics: 151
- Terrorist Attack Topics Topics: 76
- September 11 Topics Topics: 96
- World War 1 Paper Topics Topics: 179
- World War 2 Research Topics Topics: 161
- Afghanistan War Research Topics Topics: 66
- Nazism Essay Topics Topics: 75
- Operation Geronimo Topics Topics: 93
- War Essay Topics Topics: 628
- Holocaust Topics Topics: 126
- Afghanistan Paper Topics Topics: 81
- Nationalism Research Topics Topics: 139
- Homeland Security Research Topics Topics: 100
- Arab Spring Topics Topics: 60
299 Essay Titles & Research Topics on Terrorism
🏆 best topics for essays about terrorism, 📖 terrorism essay topics for college, 📚 terrorism topics for research paper & essay examples, ✍️ good research topics on terrorism, 💡 simple ideas for terrorism research paper topics, 📌 easy terrorism essay topics, 👍 good terrorism essay topics to write about, ❓ research questions about terrorism, ✒️ great terrorism dissertation topics.
- Iranian Revolution and Terrorism: the Rex Cinema Massacre
- Pirate Terrorists as an International Threat
- Efforts to Prevent Terrorist Attacks
- What Is Terrorism: Main Aspects of Term
- Homeland Security and Terrorist Attack Prevention
- Preparing for Terrorism and Disasters in the New Age of Health Care
- Causes and Consequences of Terrorism in South America: Colombia and Peru
- Discussion: Terrorism in South America Individual nations struggle with domestic terrorism, and international terrorist groups pose an additional danger by using the region to advance their causes.
- Continuity Plan for Houston City in the Event of a Terrorist Attack A terrorist attack in Houston City would cause societal upheaval. A continuity plan can alleviate the upheaval as well as ensure the protection of the city.
- The Patriot Act as an Anti-Terrorism Policy Anti-terrorism policies such as the Patriot Act have been successful in preventing and discouraging terrorist attacks, and lowering and mitigating the impact of attacks.
- How International Terrorism Threats Transformed American Political Landscape International terrorism consists of violent or harmful activities to human life that violate the criminal laws of the United States or any state.
- Domestic Terrorism in the United States Such terroristic elements as mass shootings and social radicalization induced by conspiracy theories appear to be the most dangerous terrorist elements in the United States.
- Community Policing Combating Terrorism Community policing has proven to be effective in addressing terrorism since members play a significant role in helping police officers identify high-risk individuals.
- Terrorism and War Crimes in the Battle of Algiers This essay will discuss how the film depicted the atrocities during the 1950s in Algeria when it fought for independence.
- Ku Klux Klan (KKK) as a Terrorist Group One of the two American white supremacists that used terrorism to further their racial objectives was the Ku Klux Klan (KKK).
- Connection Between Criminal and Terrorism Organization The paper gives a broad understanding of the nature of terrorism-organized crime collaboration and their operations supporting criminal activities.
- The Case of the 2015 Terrorist Attack in Paris: Bombing Investigation In the case of the Paris attacks in 2015, the targeted autopsy allowed forensic teams to identify victims and terrorists and define the nature of the explosive device.
- British Anti-Terrorist Structures In this paper, all possible mechanisms of anti-terrorist structures are presented in the example of countering Al-Qaeda at the beginning of the 21st century.
- Terrorism Prevention With Community Policing One of the measures that has proven to be effective in addressing terrorism is community policing which requires the engagement of officers and members of the public.
- The Ansar Al-Din Terrorist Organization’s Activities By conducting a simulation, it was found that acts of terrorism are capable of causing enormous damage to the country’s infrastructure and its people.
- The Geneva Convention and Terrorism Prevention The Geneva Conventions and their Additional Protocols form the center of international humanitarian law that regulates the conduct of armed conflicts.
- The Ansar Al-Din Terrorist Group Analysis This paper evaluates the measures implemented by the intelligence agencies to analyze information about Ansar al-Din that is currently available to grasp their terrorist tactics.
- Extremism and Terrorism in Nigeria Considering Nigeria’s high rates of terrorism and extremism, it is vital to illuminate the government’s strategies to eliminate the terrorist cells and extremist groups.
- Terrorism and Associated Media’s Response The media’s response to terrorism is often different from other crimes and specialized in targeting an audience that is susceptible to the current ‘war on terror’ model.
- Impact of Terrorism on the Economy Terrorism’s wider consequences are also dependent on the economy’s ability to reallocate and distribute capital from the affected sectors smoothly.
- Internationally Focused Terrorist Organization: Al Qaeda This paper addresses the inspiration of Al Qaeda, how this inspiration acts as a catalytic means of recruitment, and the means of communication used by Al Qaeda.
- Terrorism: Sources of Inspiration Perceived injustice, attention for a sense of belonging, and the need to find one’s identity are typical inspirations by potential terrorists.
- Importance of Outsourcing the War on Terror The paper discusses the benefits, disadvantages, and the necessity of the usage of private security and military companies in the War on Terror.
- The Terrorism Definition in International Law Terrorism is an anxiety-inspiring method of repeated violent action, employed by (semi-) clandestine individual, group, or state actors.
- War vs. Terrorism: What Are the Main Differences? War is an armed confrontation between the parties to protect their interests. Terrorism, in turn, is a manifestation of violence aimed at inspiring fear.
- Counterterrorism Approaches: Terrorism Prevention There are five categories of counterterrorism approaches, proactive, defensive, coercive, long-term, and persuasive.
- Communication Technology’s Impact on Global Terrorism The main question of this work is the role of communication technology in modern international terrorism, and to what extent may vigilance and science mitigate adverse outcomes.
- Counter-Terrorism and Unemployment Approaches A more novel approach to unemployment that considers the needs of a disenchanted youth is vital to reducing the draw towards terrorist activities.
- The True Story of Che Guevara: Conflict & Terrorism The name of Ernesto “Che” Guevara is among the most well-known names in the world. The Argentinian freedom fighter played a crucial role in the Cuban revolution.
- Terrorism as a Pressing Social Issue Terrorism is a crime, the aim of which is a violation of public safety, which is expressed in encroachment on the life and health of citizens and infrastructure facilities.
- Modern Terrorism Regarding the Role of Media Modern terrorism uses the media to report its threats and activities. However, governments should not use their power to restrict the media from covering terror-related events.
- The Ku Klux Klan and Modern Terrorism This work will be about the terrorist part of the Ku Klux Klan and its similarities and diversities to other types of domestic terrorism that exist in our contemporary time.
- Terrorist Cells Issues in America The paper focuses on identifying the means used by terrorists to enhance their success and measures that military officers and law enforcement can embrace to help curb terrorism.
- Operation Anaconda: Terrorism Prevention Operation Anaconda has become one of the most significant an example of an operation in which commanders applied six basic principles of mission command.
- Technologies to Reduce Crime and Acts of Terrorism Terrorism can be met with a nonviolent, credible, and justifiable reaction if counterterrorism actions are anchored in an accountable and productive criminal justice system.
- Homeland Security Efforts to Counter Terrorism The counter-terrorism efforts of the Department of Homeland Security have multiple positive outcomes and generally ensure safety for citizens.
- Aaronson’s and McCue’s Speeches on Terrorism Aaronson and McCue have had their chance to deliver their speeches at TED regarding the problem of terrorism. The speakers shed light on the issue from quite a unique perspective.
- The Study of the Future of Terrorism: Review of Literature Politicians, international researchers, world-known philosophers, and engineers devote their lives to creating the best and safest conditions for people.
- US Terrorism and Criminal Justice Decision Making Model Terrorism is a significant security and safety threat. The United States has experienced both domestic and international terrorist attacks.
- Terrorism in Mumbai 2008: Before and After the Attack Before the attack, the terrorists carefully planned this operation, as it was supposed to be large-scale, ambitious, and have a powerful destructive character.
- Future of Terrorism and Emergency Management Today terrorism has become a serious threat to the security of the entire world and regional communities. It is expressed in the commission of explosions.
- Terrorism: The Faith-Based Discourses Although there are many discourses regarding the role of God and religion in terrorism, there are some similarities in what Falwell, the Jewish extremists, and Sayyid Qutb believe.
- The Phenomenon of Terrorism and Its Relation to Globalization This paper states that the phenomenon of terrorism is tightly connected to the concept of inequality of globalization.
- Terrorist Attack in San Bernardino The San Bernardino shootings in 2015 killed 14 innocent people and injured 24 more. It was also the bloodiest mass shooting in the US since 2012.
- Homeland Security Efforts: Counter-Terrorism and Threats The homeland security mission is to protect the country from various types of threats, including terrorism and national disasters.
- Terrorism and Violent Extremist Organizations in Somali and Their Elimination This project aimed to understand how the current Federal Government of Somalia plans for current and future threats against terrorism and violent extremist organizations.
- The Future of Domestic Terrorism in the United States The research issue of this paper is the future development of domestic terrorism in the United States and the possibility of mitigating it.
- Domestic Terrorism and Hate Groups The paper states that domestic terrorism and hate groups are interdependent terms that imply violence towards a state. Both target innocent people.
- Migration, Diasporas, and Terrorism This topic examines the relationship between different concepts (migration, diaspora communities, and terrorism) in the context of globalization.
- Crisis Management During Terrorism Threat In the essay, the crisis management strategies of preparation for change are viewed on the example of the terrorism threat.
- America and Terrorism in the 21st Century There are many threats that people face every day without even realizing it. For example, terrorism is a major global problem addressed by authorities and different organizations.
- Threat of Terrorism in the Middle East If tomorrow the US withdraws its troops from the Middle East, it is highly likely that terrorist activity in the region will subside but will not disappear.
- Terrorism: Radicalization and the Internet The current paper examines the main causes and types of radicalism, as well as what role the Internet plays in the hands of terrorists.
- The Four Waves of Modern Terrorism – In Comparison with Freedom Fighting Terrorism is an act of political violence aimed to incite terror and panic into the target population and further a specific political goal.
- Forensics Analysis of Terrorism Crime Scene Terrorism uses calculated violence to generate public fear and panic to establish a specific political agenda within the general population.
- Analysis of Terrorism in Spain The paper looks at the history of terrorism in Spain and how the European Union has countered terrorism and helped Spain fight against it.
- Is Terrorism Ever a Justifiable Form of “Political Violence” Young people are an essential source of support to various terrorist groups as they are used as fighters and even cooks.
- Financing Terrorist Organizations The financing of terrorist organizations is a significant problem for the national security agencies that monitor and suppress extremists’ activities and the entire world community.
- Terrorism of Liberation Tigers of Tamil Eelam This paper makes a prognosis of the Liberation Tigers of Tamil Eelam’s future operations and the possibility of stopping its functions in Sri Lanka.
- Operational Principles in the US War Against Terror The US war against terror has intensified aftermath of the 9/11 attacks, and to that day, remains one of the most contested and protracted US military operations abroad.
- What Is Water-Related Terrorism and How to Cope With It? Water-related terrorism includes damaging government facilities, and since water resources are vital for human existence, it is profitable for terrorists to attack them.
- Strategies to Prevent Radicalization and Lone-Wolf Terrorism This paper discusses approaches toward building trust and relationships with the Community to prevent radicalization and formulating counter-terrorism strategies.
- Cyberterrorism Threat to the United States National Security The United States remains vulnerable and largely unprepared for cyber terrorism threats that threaten its national security due to the increased growth of adversary capabilities.
- How Do Terrorists Conduct Cyber Warfare? Terrorism activities are a global concern since they can occur in any part of the world depending on the perpetrators’ target.
- The Threat of Nuclear Terrorism The issue of nuclear terrorism has been discussed by many researchers and policy-makers. Some believe that the threat is unrealistic.
- Terrorism Prevention: Operation Geronimo Operation Geronimo was carried out by the US military in the Pakistani city of Abbottabad. As a result, the head of al-Qaeda was killed.
- An Overview of Investigative Techniques as They Apply to Terrorism The paper focuses on the psychological and behavioral features of terrorists and offers several recommendations on the use of investigative techniques in their case.
- The 26/11 Terrorist Attack on Mumbai The instance of a terrorist act is always a tragic occurrence since, especially when it results in a tremendous number of casualties and the deaths of innocent civilians.
- Terrorist Drag in “Stop Being Poor” Video “Stop Being Poor” invokes stereotypes of racialized and gendered deviance in terms that show that only White, rich women deserve to stay alive.
- Terrorism Current Events Terrorist attacks have for a long time culminated in the loss of lives, property destruction, destabilized governments, and resulted in economic paralysis.
- Money Laundering, Corruption and Terrorism Issues Money laundering, corruption and terrorism are rife in East and Southern Africa is largely attributed to the abject poverty that at times seems to be endemic.
- War on Terrorism on USA After 9/11/2001 The discussion of the acts and policies directed at the USA security are going to be considered with the purpose to follow the changes that occurred after the 9/11 attacks.
- Extremism and Terrorism in the Society Extremism includes the activities that are not violent but grossly violate citizens’ rights and freedoms, having an ideological motive behind them.
- Terrorism: Palestine Liberation Organization (PLO) Terrorists are the individuals who practice terrorism; they can also be referred to as the agents of terrorism since they attack nations they are opposed to.
- The Fourth Wave of Terrorism and Religion The diverse religious ethnicities have primeval ancestry evidence in a terror campaign. The fourth or the current wave of terrorism derived its incentives from religious activities
- Terrorism Theories and Media Discourse This paper discusses theoretical comprehension of the terrorism phenomenon, mass media discourse concerning terrorism, and implications for the future.
- Terrorism in Northern Ireland and in Middle East There is no universal instrument to end the terrorism, but profound analysis of this phenomenon is one of the primary measures for the solution of this issue.
- Robust Security System vs Terrorists in Airport America has stepped up its security system by appointing TSA – a government organization to protect the nation’s transport system.
- Drug Trafficking and Terrorism in the Middle East Terrorism and drug trafficking are the major wars that the world has been trying to fight for several centuries.
- Handling of the Terrorist Suspects According to the English Legislations The main aim of this study is to explore how terrorism suspects are handled in relation to English laws. The study examines some of the powers accorded to the police.
- Terror and Religious Belief System Contemporary fourth wave terrorists justify their use of violence through the theological and moral teachings taken from their chosen religious belief system.
- On the Reasons for the Terrorist Attack on September 11 The purpose of this article is to investigate allegedly American offenses that may have led to the 9/11 terrorist attack.
- International Terrorism in the United States Analysis There is a review of the Congressional Research Service report on International Terrorism, the focus being on threat, policy, and response issues.
- Possible Terrorist Attack Local law enforcement agencies with the help of the federal government created a network of databases called fusion centers, after 9/11.
- Terrorism and the Media This paper reveals how several media reporting incidents have embraced an ideology that Islam is inherently violent.
- Targeted Killing: Counter-Terrorism The current paper discusses that targeted killing represents a part of consequentialist philosophy in counter-terrorism.
- Counter Terrorism Methods and Their Effectiveness In many cases, terrorists are destroyed with the help of military people, although to a greater extent, this is the work of special services and the police.
- The Mind of a Terrorist Terrorism seems to bring a certain consolation within the terrorists yet does not offer them the solution to their problem.
- Terrorism: Understanding the Key Issues Terrorism remains a major challenge in many societies today. Terrorism is a necessary practice among many extremist groups in the Middle East.
- Terrorist Response Organizations Members of specialized terrorist response organizations undergo special training which allows them to respond to emergency situations more quickly.
- The US Response to the Terrorism Threats This report outlines the central directions of terrorist activities targeted at the US seaports and the ways American security counteracts them.
- Religion and Middle Eastern Terrorism The Middle Eastern region is occupied by Muslims, Christians and Jews. Their constant conflicts have been attributed to the rise in modern terrorism across the region.
- About the Motives of the Terrorists This article attempts to determine what is more important in influencing the intentions of terrorists: human psychology or the social impact of a group.
- The Long Term Effects of Terrorism Terrorism attacks have become very common in today’s world especially with the increasing conflicts of power and the increase in financial difficulties around the globe.
- The Emerging Terrorist Threat in Africa Most terrorism acts are usually portrayed as political, emotional, or religious undertones. Terrorist threats in Africa started way back in the 1980s and 1990s.
- Historical Responding to Terrorism Terrorism is not the only resort to injustices. Processes like peace talks, negotiations and compromise of some standards solves any stalemate amicably.
- Bioterrorism: History, Types, and Detection This paper explains what is bioterrorism, gives a background of bioterrorism, and discusses the types of bioterrorism, and the difficulties to detect bioterrorism.
- Terrorism a Critical Issue of the Modern World Terrorism is, undoubtedly, a criminal act aimed at civilians. Terrorists tend to invent new, unusual ways to commit crimes, making them more dangerous and powerful.
- The Past and Present Effects of Terrorism on Society Terrorism is one of the main challenges that the world has encountered for several decades. It can be defined as the use of violence against civilians.
- Global Terrorism and Ways of Its Impact In the 21st century, global terrorism has become a complex problem that all nations need to address from an informed perspective.
- UK Anti-Terrorism Strategy and the Human Rights Implications on its Implementation The prevention of terrorism has been given a higher priority, and the new legislation has drawn on new instruments equivalent to the European levels.
- Hacktivism & Cyberterrorism vs Government Response Hacktivism is the use of technology or computer system for social or political motivations. Cyberterrorism can be defined as intentional violent acts conducted in cyberspace.
- Terrorists’ Motives: The Psychology of the Individual The psychology of the individual may be useful to the activities of terrorists but this is realized well if the individual undergoes indoctrination amidst the group.
- Terrorism. Hezbollah: Ideology and Financing The problems of combating terrorist crimes in the framework of the modern world are becoming increasingly important.
- Three Cases of Terrorism: Ideological, Nationalist and Religious The main aim of terrorism is to draw the attention of the local population, state, and the entire world to the cause of terrorists.
- The Terrorism Threat in the Modern World This work describes the essence of terrorism, its essence, origins, forms of manifestation, tells about modern single and international approaches to combating terrorism.
- Lone Wolf Terrorism: Theoretical Analysis and Implications for Public Policy Countering lone-wolf terrorism is much more difficult than fighting organized terrorist activity, as it leaves a much smaller informational footprint.
- White Supremacy and the Terrorism Threats White supremacists are uniting in a comparable way with jihadist terror groups, such as Al Qaeda; they are uniting in a comparable way with jihadist terror groups, such as Al Qaeda.
- The Problem of Terrorism Prevention Each government should develop innovative strategies for the struggle against terrorism while special attention should be paid to the financial front in the global war on terrorism.
- Policy Memorandum: Terrorist Organizations Nowadays, terrorist organizations are more geographically dispersed than it was before, and their tactics became more sophisticated and untypical.
- Emerging Terrorist Threat in Africa If judging terrorism only by the media, its face is always changing. In that regard, it can be stated that its most recent face seems to be in Africa.
- Sociological Failure of the War on Terrorism This article explains why the War on Terror has failed sociologically by focusing on three pillars: an international reputation, cost, and lack of results.
- The Earth Liberation Front as the Domestic Terrorist Organization The purpose of this essay is to analyze the ELF’s history, structure, and actions, to fully understand the rationale behind their decisions.
- Domestic and International Terrorism There is an evident dismissal of domestic terrorism, which is also reflected in the fact that there is a more aggressive monitoring approach for the international one.
- Terrorism: Threat and Ways of Combating Terrorism has an aggressive and violent nature and, most importantly, a public character that threatens nation safety and requires law enforcement agencies’ intervention.
- The Phenomenon of Terrorism in the Modern World This essay aims to discuss the phenomenon of terrorism through the prism of two opposing sources, including a speech by the U.S. President and a letter from Osama bin Laden.
- Unconventional Warfare on the Global War on Terror The implications of the findings for US foreign policy can be seen through targeting regional security, rather than focusing on a single country a source of terrorism.
- United States Foreign Policy and Terrorism The foreign policy in the USA aimed at fighting terrorism demonstrates the integrity of the two concepts, human and national security.
- Terrorism and Genocide: Impact on Populations Victims of terror actions usually recover within a short time, given that terrorist actions are considered moderate stress reactions.
- A Duty of Care in Cyberspace and How It Relates to Cyber Terrorism Confronting the threat posed by cyber attackers and to the internet security of critical infrastructure still remains a challenge.
- Terrorism Attack in United States America has invested a lot of money towards improving its ability to detect any act of terrorism, prevent the acts and if they occur, respond to them.
- Terrorism as a Transnational Organized Crime Terrorism and organized crime have always been considered to stand among the primary security threats in any society.
- Terrorism and Genocide: Traumatic Impacts The defense centers of excellence for psychological health and traumatic brain injury were launched to help those veterans who feel their lives are at risk psychologically.
- The Role of the Media in the Propaganda of Terrorism An article on how the terrorists managed to attract everyone’s attention, as well as a brief overview of the reasons and consequences of the change of government in Tunisia.
- Psychology of Terrorism: Leaders and Development The war on terror has been a losing battle because the leaders in today’s democracies fail to understand the reasons for the terrorism activities.
- A Biological Terror Attack in Agriculture The United States is highly vulnerable to terror attacks of biological nature in agriculture yet such an occurrence can cripple the economy.
- The Three Categories of Dissident Terrorism This paper seeks to contrast the three categories of dissident terrorism as documented by Assistant Vice President Gus Martin in his bestselling book.
- Torture Debate in America’s War on Terror Torture has mainly been used as a way to extract information from crime suspects for example who are intent on withholding it.
- International Consensus for Terrorism Mitigation It is imperative for various countries to come together and cooperate on diplomatic, law enforcement, military and intelligence capabilities.
- Community Policing Practice and Terrorism Activities Community policing is the best development ever in the police force. This is because it is still the best way to effectively combat crime and bring it to control.
- Ways to Defend Against Cyber Terrorism With the development of technology, new ways of terrorism on the web are reaching a new level. People need to know how to confront them and protect their privacy.
- Power of Terror as a Political Weapon The use of power of terror by the French monarchy was the main reason that made the people to think about democracy.
- The Power of Cyberterrorism The paper will look at what cyberterrorism could do to opponents and the actual possibility of such an attack.
- History And Threats Of Global Terrorism The paper shall argue that historical events after the cold war demonstrate how vulnerable the US is to global terrorism.
- Parsing and Analysis of the Phenomenon of Terrorism The common objective for most terrorist groups that engage in violent activities has been achieve their political goals.
- Definition of Terrorism Mitigation Terrorism mitigation is the assignment that should be solved on all governmental levels, and, in comparison with risk mitigation the terrorism mitigation entails several additional steps.
- Impact of Bioterrorism on the U.S Agriculture System The paper describes that the term bioterrorism has several definitions depending upon the origin of the attack but in general terms, it refers to any form of terrorist attack.
- Terrorist Attack Prevention Policy on the Example of the US Patriot Act The US Patriot Act is a multi-tiered government policy to prevent terrorist attacks that arose in response to the upheavals of the 2000s.
- The Roots of Islamic Terrorism The history of the Islamic religion has influenced the cause of terrorism since most terrorist groups are linked to the Islamic religion.
- Terrorism Prevention and Scenario Development The paper shall focus on the Aum Shinrikyo cult of Japan and its utilization of WMD as a case study. The Aum Shinrikyo cult staged six attacks against Japanese citizens.
- War on Terror Impact on Muslims & Their Responses The war on terror has been transformed into a war on Muslims. The Muslims living in the US have lived in constant fear and panic.
- How U.S. Political Parties View Terrorism The purpose of this paper is to examine the differences in position between the Democratic Party and the Republican Party on the issue of Terrorism as a national and global threat.
- US Preemptive Attacks: Counter-Terrorism Campaign After the 9/11 attacks, the United States Government and President Bush Administration started their comprehensive counter-terrorism campaign but the world community perceived the practice.
- Media’s Role on Terrorism Terrorism in respect to the media can be said to be a form of propaganda. It is a kind of persuasive communication and it can be seen to be the propaganda of actions.
- Brainwashed Terrorists: Are Terrorists Crazy? The main reason why terrorist attacks are so frightful is that they are organized by people who are not afraid to die, people who die for their faith, or what they think to be their faith.
- Public Health Problems: Bioterrorism The issues of bioterrorism are not paid much attention in various media in comparison with other factors of everyday life in the global scales.
- Emergency Response and Management in a Terrorist Attack This report depicts the scenario that will ensue if a terrorist attack were launched against an urban population center in the US today.
- Non-Conventional Terrorism and Protection Among the types of terrorism the most inevitable and unpredictable one is non-conventional which terrifies by its unexplored nature and effects.
- War Against Terrorism and Social Injustices Terrorism by itself is the outcome of serious social injustices faced by several communities. Doing more injustice will only worsen the condition.
- Human Rights Conservation and the War on Terror Public Safety is the concept of governmental organizations concerned with protecting their citizens from all kinds of threats.
- Singapore Armed Forces in Counter-Terrorism Efforts The tragedy of Lo Hwei Yen can only serve as a reminder to all Singaporeans that terrorism transcends all borders and that the need to remain vigilant is more urgent than ever.
- The American Skinhead, and Greenpeace: Humanitarians or Terrorists The Greenpeace and American Skinhead movements have come to attract a lot of controversies in regard to their intentions and legality of action.
- Terrorist Groups’ Social and Psychological Origins Terrorism is a complex social issue which requires multiple levels of analysis from interdisciplinary fields of psychology, political science, and cultural and historical studies.
- How Media Helps Promote Terrorists’ Agenda The media serves as the platform that helps to popularize the ideas of various terrorist organizations by familiarizing people with them.
- Non-Conventional Terrorism from Theoretical Viewpoints Non-conventional terrorism mainly uses and executes non-traditional forms of weapons. They might include chemical, biological, and nuclear types of threats.
- Terrorist Campaigns of Extremist Organizations The paper considers extremist actions of such prohibited groups as Vanguard America (VA), the Balochistan Liberation Army (BLA), and Boko Haram (BH).
- Terrorism and Other Crimes Against the State This paper overviews crimes against the state and discusses terrorism as an offense, its types, and the legislator allowing for combating it.
- Russian Cyber Terrorism and the United States: A Research Proposal This paper presents the key information on a proposal for a case study of the cyberattacks used as a part of the interference of Russia in the US elections of 2016.
- Russian Cyberterrorism and the United States Cyberspace With the development of the cyberspace, some new uses of the related technologies have appeared, including beneficial and malevolent ones.
- Russian Cyberterrorism and the United States Election 2016 The present paper attempts to contribute data to the discussion of the topic of the Russian electoral interference of 2016 by conducting a case study of that accident.
- The Terrorist Aspects of Narcoterrorism This project intends to respond to the question of what are the terrorist features of narcoterrorism attacks in Mexico, and what are their implications for security efforts.
- Vital Issues of Terrorism and Ways to Counter Terrorism The evolution of weapons and the development of technology have led to a significant inflow of resources to extremists who use the latest achievements of armament.
- Terrorism History in the United States
- War on Terrorism: The Modern Perspective
- Generation Kill: Anti-Terrorism Fight After 9/11
- Generation Kill: War on Terrorism After 9/11
- Human Factors in Aviation: 2016 Brussels Terrorist Attacks
- Military Commissions and Terrorism Prevention
- Terrorist Profiling from Various Perspectives
- Terrorist Weapons Sources and Extremist Attacks
- How Terrorists Prepare for Attacks
- The Arab Spring and Terrorism
- Terrorist Surveillance Techniques for Predicting and Identifying Terrorist Activities
- Terrorism Today: the Past, the Players, the Future
- Local Police Response to Terrorism
- Emergency Management in Past Acts of Terrorism
- Terrorism as a Threat to American Airport Security
- Understanding Terrorism: Course of Action
- Liberation Tigers of Tamil Eelam and Hezbollah Terrorist Groups
- United States and Negotiation With Terrorists
- The Impact of Terrorism on Walmart Global Logistics
- “Unemployment and Terrorism” TED Talk by Mohamed Ali
- Terrorism and The Peshawar School Bus Bombing
- Human Rights Advocates vs. Terrorism Victims
- America’s Fight Against Terrorism
- Terrorists: Criminals or Crusaders?
- American Domestic Terrorism and Its Historical Roots
- Terrorism as Global Issue and Preventive Laws
- Terrorism: A Philosophical Investigation
- Khobar Towers Bombing and Terrorism in the US
- Terrorism and Its Damage to Modern Society
- Holy Terrors: Religion and Terrorism in the US
- Terrorist Organizations: Key Concepts
- Homegrown Terrorism in the United States
- Terrorist Activities in Media Broadcasting
- Intelligence Requests for Terrorist Attacks Prevention
- Government Preparedness to Chemical and Bio Terrorism
- Policy on National Security and Terrorism in the USA
- John Brown: Terrorist or Freedom Fighter
- Ethical Terrorist Elimination in the United States
- Terrorism in the USA
- Arab Spring, Terrorism and Libyan Political Changes
- Problem of Terrorism in Modern World
- Terrorism’s Serious Problems: Can It Be Justified?
- The Role of Homeland Security in Terrorism and Disaster Management
- Extremist Groups and Domestic Terrorism in the US
- Terrorist Hazards and Education Role in Security
- Disaster Management: Terrorism and Emergency Situations
- Extreme Islamic Terrorist Groups in Comparison
- World Trade Center Disaster and Anti-Terrorism
- Terrorism Financing and Combating Methods
- Terrorist Activity in the United States
- The USA Patriot Act in Fight with Terrorism
- Religion as a Root of Terrorism
- Legislation After the 9/11 Terrorist Attack in New York
- Global War on Terrorism: Main Challenges
- Terrorist Attacks: Death and Horrifying Effects on Innocent People
- Terrorism Evolution from 1972 to 2016
- Terrorism Definition and Motivation
- State Terrorism vs. Critical Terrorism
- Terrorism Definitions in the US Legislation System
- Guantanamo Bay as a Terrorists’ Location
- The Concept of Terrorism
- Events of 9/11 and an Era of New Terrorism
- The US Intelligence Community Role in Countering Terror Threats
- Terrorism: Irish Republican Army History and Ideologies
- Terrorist Bomb Attacks in France
- Anti-Terrorist Attitudes and Measures in the US
- Tokyo Terrorist Attack in 1995: Stakeholders and Effects
- Terrorism, Its History and Constituents
- Homeland Security: Fast Response to Disasters and Terrorism
- Crimes in America: The 9/11/01 Terrorist Attacks
- Supreme Court’s and Habeas Corpus War on Terror
- History of Cold War and War on Terror
- 9/11 Terrorist Attacks and Its Effect on Muslims
- Information Warfare and Cyberterrorism
- War on Terrorism: Reasons, Essence, and Social Outcomes
- Counter-Terrorism: Constitutional and Legislative Issues
- Psycho-Political Terrorism and Its Main Principles
- Right and Left Wing Terrorist Groups
- Terrorism in Perspective: Characteristics, Causes, Control
- The Right of Habeas Corpus in the Context of the War on Terror
- Terrorism: Definition, History, Countermeasures
- Intelligence Implications for Self-Radicalized Terrorism
- Why Does Globalization Contribute to the Rise of International Terrorism?
- Is Democracy Promotion a Cure for Ending Terrorism?
- What Is the Effect of Globalization on Terrorism?
- Can Islamic and Global Terrorism Ever Be Defeated?
- What Are the Four Elements of the Government’s Counter Terrorism Strategy?
- Can the State Commit Acts of Terrorism?
- Does the International Community Think That Iran Is a Direct Contributor to Terrorism?
- What Are the Political Causes of Terrorism?
- How Does the Patriot Act Define Domestic Terrorism?
- Why Does Poverty Cause Terrorism?
- Does Economic Growth Cause Terrorism in Pakistan?
- How Does Social Identity Theory Explain Terrorism?
- What Are the Effects of Terrorism in India?
- Does Transnational Terrorism Reduce Foreign Direct Investment?
- How Does Terrorism Affect the Economy?
- What Strategy Aims to Reduce the Threat to the UK From Terrorism?
- Is Terrorism a Social Phenomenon?
- Why Are Developing Countries More Vulnerable to Terrorism?
- How Does Terrorism Affect International Business?
- Does Terrorism Influence Domestic Politics?
- What Is the Difference Between Cybercrime and Cyber Terrorism?
- Is Cyber Attack a Form of Terrorism?
- What Is the Link Between Transnational Organized Crime and Terrorism?
- How Can Cyber Terrorism Be Prevented?
- Does Immigration Increase the Risk of Terrorism?
- The Role of International Relations in Combating Cyberterrorism: Challenges and Strategies
- Analyzing the Psychological Profiles of Terrorists: Motivations and Mindsets
- The Role of Women in Terrorist Organizations: Perpetrators, Supporters, and Defectors
- The Influence of Religion and Ideology in Shaping Terrorism
- The Impact of Political Regimes on Terrorism: A Comparative Analysis of Authoritarian and Democratic States
- The Use of Technology in Modern Terrorism: Drones, Cyber Attacks, and Artificial Intelligence
- Cybersecurity and Critical Infrastructure Protection: Assessing Vulnerabilities to Cyberterrorism
- Homeland Security and Border Control: Addressing the Challenges of Terrorism through Immigration Policies
- The Impact of Terrorism on Tourism and the Global Economy
- The Evolution of Terrorism: A Historical Analysis of Ideologies and Tactics
- Criminology and Terrorism: Analyzing the Social and Psychological Factors Influencing Terrorist Behavior
- Comparative Study of Counterterrorism Strategies in Different Political Systems
Cite this post
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2021, September 9). 299 Essay Titles & Research Topics on Terrorism. https://studycorgi.com/ideas/terrorism-essay-topics/
"299 Essay Titles & Research Topics on Terrorism." StudyCorgi , 9 Sept. 2021, studycorgi.com/ideas/terrorism-essay-topics/.
StudyCorgi . (2021) '299 Essay Titles & Research Topics on Terrorism'. 9 September.
1. StudyCorgi . "299 Essay Titles & Research Topics on Terrorism." September 9, 2021. https://studycorgi.com/ideas/terrorism-essay-topics/.
Bibliography
StudyCorgi . "299 Essay Titles & Research Topics on Terrorism." September 9, 2021. https://studycorgi.com/ideas/terrorism-essay-topics/.
StudyCorgi . 2021. "299 Essay Titles & Research Topics on Terrorism." September 9, 2021. https://studycorgi.com/ideas/terrorism-essay-topics/.
These essay examples and topics on Terrorism were carefully selected by the StudyCorgi editorial team. They meet our highest standards in terms of grammar, punctuation, style, and fact accuracy. Please ensure you properly reference the materials if you’re using them to write your assignment.
This essay topic collection was updated on June 24, 2024 .

International Relations
Gale provides useful and authoritative resources for terrorism studies and education.
International Relations | Human Rights | Immigration | International Business | International Trade
Find information and resources for the research and interdisciplinary study of terrorism—acts of violence committed by a group or an individual in support of a political or ideological goal. While international law doesn’t provide a single definition of terrorism, it may involve hijackings, bombings, mass shootings, kidnappings, deployment of military weapons on civilians, and the use of chemical, biological, and radioactive weapons. Terrorism may also include acts of violence or psychological tactics carried out solely to intimidate specific groups of people.
International terrorism is committed by foreign groups across borders, and domestic terrorism is committed by groups or individuals in the same country where the terrorist acts are made.
Motivations among terror groups vary. There is political and dissent-oriented terrorism as well as religious, xenophobic or ethnocentric, state-sponsored, and environmental terrorism. Radicalization is the process of developing extreme beliefs on a specific issue. It is a tool used by terror groups as they recruit new members and gain support for their ideologies.
Any religion’s beliefs can be twisted by individuals or groups who seek to commit acts of terror. For example, Islamist terrorists hold beliefs that are not in line or supported by the standard teachings of Islam and are strongly opposed by the worldwide Islamic community. Extremist views and warped forms of religious fundamentalism have also led to acts of terror among Christian and Hindu religious groups.
Political terror acts may be driven by separatist ideologies. One example of separatism involves the Spanish region of Catalonia, where some Catalan separatists have used bombings to promote their extreme political views not held by all Catalonians.
Ecoterrorism seeks to protect the environment through acts of sabotage designed to interfere with or stop activities that harm nature or animal life. To date, no human lives have been lost due to ecoterrorism.
Cyberterrorism is the use of computer systems and information technology to cause harm and panic by taking control of major systems and creating panic and even loss of life. Potential targets of cyber terrorists may range from air traffic control systems and nuclear energy stations to hospitals and health care facilities, public utilities, and stock markets. The increased use of internet systems due to the COVID-19 pandemic has provided opportunities for terror groups to commit crimes and take advantage of heightened fears and a weakened economy.
Social media has become a recruiting tool for terror groups. Facebook, Twitter, Microsoft, and YouTube have pledged to monitor individuals and groups that use their platforms to promote radical views and spread propaganda. These companies founded the Global Internet Forum to Counter Terrorism in 2017 to aid in preventing the spread of extremist content online.
Students and researchers of terrorism who want to analyze terror data may be interested in the Global Terrorism Database, maintained by the University of Maryland. Political scientists, military advisers, and other individuals researching terrorism seek to understand why terror acts occur and how to prevent them.
Terrorism Resources
Gale provides resources that support research with collections from databases, microform , and eBooks .
Gale databases include collections of published materials from books, newspapers, journals, essays, and periodical articles as well as primary source documents and multimedia, such as images, audio, and videos, that support users interested in terrorism studies.
Gale OneFile: War and Terrorism
This library resource provides authoritative periodical content addressing both historic and contemporary topics in the fields of war and terrorism. With more than 1.7 million articles, Gale OneFile: War and Terrorism gives researchers valuable insight into conflicts and their causes, impact, and perception on a global scale.
Gale OneFile: Criminal Justice
Gale OneFile: Criminal Justice informs the research process for those studying law, law enforcement, terrorism, homeland security, forensic science, and more.
Microform includes reels of published materials from documents that support users interested in terrorism studies.
Studies in Global Crises: The Global War on Terrorism
Studies in Global Crises: The Global War on Terrorism assembles research studies that analyze the goals and strategies of global terrorism. Theses studies, reports, and analyses were conducted by governmental agencies and private organizations under contract with the Federal government. They represent the most rigorous and authoritative research on the global war on international and domestic terrorism.
Gale eBooks
Gale's eBook collection offers a variety of publications online to support terrorism research. Users can add Gale eBooks to a customized collection and cross-search to pinpoint relevant content. Workflow tools help users easily share, save, and download content.
Emerging Security Challenges: American Jihad, Terrorism, Civil War, and Human Rights
Praeger | 2018 | ISBN-13: 9781440863059
When American jihadists join such international terrorist organizations as the Islamic State of Iraq and Syria and Al Qaeda, the danger to security and stability is often magnified on both global and domestic fronts. The global rise of terrorism, in turn, causes a deterioration in the quality of human rights for politically disadvantaged people or minority groups within a national territory. Meanwhile, the internal crisis created by terrorist violence and human rights violations can expedite the development of civil wars, which is likely to endanger domestic and international stability. Taking a consistent theoretical and empirical approach, this title explicates the relationships among these four closely related areas of concern for national security. Each chapter presents systematic, empirical evidence of security trends for more than 100 sample countries, determined using the most current statistical methods. Given that security studies should provide practical policy recommendations, this book also offers potentially effective policy suggestions at the end of each chapter.
Contact my sales rep >>
Essentials of Counterterrorism
Praeger | 2015 | ISBN-13: 9781440832840
This book is a comprehensive overview of counterterrorism that examines key aspects of the fight against terrorism, including intelligence, law enforcement, the military, financial and criminal activity, ethics, and social media. An interdisciplinary team of expert contributors examines a wide range of topics, such as "lone wolf" and homegrown terrorists, intelligence cooperation, social media, community policing, terrorism finance, and the shadow economy. Case studies from Europe, Latin America, South Asia, the Middle East, and the United States provide clear, practical examples of effective and sometimes not-so-effective approaches to combating terrorism. The volume will serve as a central textbook for professional development courses, workshops, and academic degree programs on terrorism, counterterrorism, and security studies.
Browse more subjects >>
Resources to boost your research.
From trending social issues to classic literature, Gale resources have you covered. Explore overviews, statistics, essay topics, and more or log in through your library to find even more content.
Access topics >>

How to Write a Terrorism Research Paper/Essay

Terrorism has become a menace and a reality that every nation around the world has to confront. As a global problem, terrorism is fought jointly to ensure that counterterrorism measures bear fruit.
Terrorists keep devising creative and ingenious ways further, from suicide bombers to things like bio-weaponry and Cyberterrorism. Today, the terrorism agenda is at the center stage in the discussions within the public, scholarly, and political domains. Religions, countries, ideologists, nations, and continents have suffered conflicts over terrorism.
New organized criminal and terrorist groups emerge almost annually. The mushrooming of terror groups make terrorism a key topic for research papers and essays. Suppose you are studying security studies, criminology, criminal justice, homeland security, and international relations. In that case, the chances are that you will write either an essay or a term paper/ research paper on terrorism.
There are many trending terrorism topics to write about. In this article, we give you examples of topics to use in your dissertation, speech, thesis, essay, term papers, or research proposals. You will also get insights on the types of terrorism and the steps to follow to write an excellent terrorism paper.
Typology of Terrorism to Feature in Your Research Paper
Have you ever wondered what types of terrorism are there or how terrorism is classified? There are various types of terrorism , each defined independently.
- Single-actor terrorism: Even though terrorism is a group phenomenon, attacks like those by Anders Behring Brevik in Norway and Mohamed Merah in France proved otherwise. Single-actor terrorism, which also goes by aliases such as lone-wolf terrorism, solo terrorism, and leaderless resistance, only involves one individual. You can find more examples of lone-wolf terrorism online.
- Criminal terrorism: Criminal terrorism entails all the terrorism activities whose perpetrators aim at achieving a criminal profit agenda. It often leads to violence, loss of property, or targets a specific group or business officials. By default, all terrorism activities fall under criminal terrorism.
- Religious terrorism: Religious terrorist groups have a twisted ideological view based on religion. An extremist religious belief always motivates all the actions.
- Dissent terrorism: Dissent terrorism targets overthrowing governments or changing the state of political affairs. It entails using terror attacks to enforce a political ideology.
- State-sponsored tourism: Yes, governments can initiate and fund terrorism covertly to ensure that they get hold of specific agendas. In most conflict-prone countries, state-sponsored terrorism is often an alternative.
- Quasi-terrorism: Quasi-terrorists present themselves as real terrorists. They use the same methods and motivations as conventional terrorists. Mostly, they will hold people or businesses and services hostage, sabotage processes, and make threats to attain a specific goal.
- Political terrorism: Like state-sponsored terrorism, civic organizations or candidates to exert their agenda and impose their ideology on the people often fund political terrorism. It could also be against those with a dissenting opinion or belonging to the opposite political factions.
We will continue to update the list as we come across different or emerging terrorism trends. As you can conclude from the above definition, terrorism is a complex phenomenon, and so are the countermeasures against terrorism. When writing your terrorism essays or research papers, you ought to have an open mind.
When assigned any of the classifications of terrorism, there are a few tips you need to follow to get a full-grade.
How to Male your Terrorism Research Paper Great
In our research paper writing article, we covered some of the steps taken when writing a research paper. Here is a step-by-step guide on how to write a research paper on terrorism. Even though we know that you can write a research paper on the war on terrorism, counterterrorism, or cyber terrorism, we have to remind you of some facts to make the writing process seamless.
1. Do not choose any topic; choose a narrow one!
Even though your professor might give you a list of research paper topics, rest on a topic judiciously. Your topic of choice for the terrorism essay or research paper should be narrow enough to let you delve deeply into the essentials.
2. Research deeply and keenly.
After reading the research paper prompt to get a rough picture of what to include, the next step is to research online or offline to get more insights on the topic. Instead of spending countless times in the library, you can now use the Internet to access nearly every scholarly material. From understanding the different types of terrorism to the motivation of terror groups, you can get information to shape your ideology or point of view.
3. Choose scholarly and reliable sources.
A research paper cannot be excellent if it is based on unreliable sources. Therefore, you have to adhere to the rigorous standards of scholarly sources strictly. Go for journals, white papers, government publications, trustworthy news media, books, peer-reviewed papers, and any other source you deem fit. As you choose the sources, remember not to use Wikipedia and Encyclopedia as your references. However, they are a great place to begin your research, especially when building your point of view, which requires more information.
4. Outline the paper.
Although obvious, writing an outline helps you create a blueprint for your paper. 99% of our writers create an outline on paper or Word Document before writing the research papers. They indicate that doing so helps structure the research paper, organize ideas and thoughts, and visualize how the reader will get informed.
5. Write the introduction, including the thesis.
After drafting the outline, you need to write the introduction to your paper. Your introduction should have a hook, background, rationale for choosing the topic, and thesis statement . Constructing the best thesis statement allows you to get the readers glued from the onset.
6. Develop your point of view in the body.
After reading in-depth, we expect that by now, you have developed or adopted a research-based point of view. Never be afraid of your research paper bearing your personal opinion; there is a way you can write that indirectly, but make sure you neutralize it to fit the requirements of the rubric. Writing a terrorism research paper is easy in thought and tough on paper. Be very careful what you put where in the terrorism essay or research paper.
7. Use strong arguments supported by facts
One thing that will earn you whole marks or get your research an A, whatever the topic, is having strong and backed arguments. Mainly, the arguments can be reflected in either your topic sentences or the supporting facts. When talking on the topic of terrorism, make your readers convinced by using examples, quotations from sources, and concluding sentences. Do not use any logical fallacies lest you lose your readers.
8. Cite the paper as you write
We maintain that you use in-text citations when you write the terrorism paper. It helps you do less when editing and proofreading or polishing your research paper on terrorism. If it is in Chicago, MLA, Harvard, or APA, make sure the in-text citations and the end and footnotes are in place.
9. Format your terrorism paper
A terrorism research paper is not complete if it defies the academic writing style conventions. Therefore, it is paramount to have a proper formatting style. From the cover page or title page to the references section, make sure you align with APA, MLA, Harvard, or Chicago format. Your rubric or prompt will give you information on the type of formatting style to use in your research paper.
11. Edit your terrorism research paper
Finally, after writing your terrorism paper for class, make sure you take some breaks. After the break, you can now edit and proofread your essay. Alternatively, you can use online editing services such as GradeCrest to find an editor. We have writers who can check your essay for grammatical errors, syntax errors, and mechanical errors.
Now, that is how you ace your paper on terrorism. Make sure that you choose reliable sources and use them to support the arguments in your paper. If you are wondering how to write an essay on terrorism, the same tips apply as well. Finally, we have given you tips. Now, let us delve into the list of topics for a research paper on terrorism.
Cyber Terrorism Research Paper Topics
- Role of Network Forensics in combating cyber terrorism.
- The implication of increased use of cryptocurrencies by terrorist groups.
- Why cyber terrorism is a top-tier risk at the national level globally.
- Impacts of Ransomware on Corporations.
- Cybercrime as an organized international crime.
- Response to cyber-attacks: Strategy and Approach.
- Criminological impacts of cybercrime.
- Impacts of cybercrime on the global financial system.
- Cybercrime and electronic banking systems.
- War on Terrorism research paper.
- The national consortium for the study of terrorism and responses to terrorism.
- How many terrorist attacks in 2016?
- Is antivirus alone an effective countermeasure to cyber-attacks?
- Access controls as a strategy to prevent cyber-attacks
- Cybercrime and Big Data.
- The use of blockchain to prevent cyber-attacks.
- Role of cryptography in fighting cybercrime.
- Cloud computing and Cyberterrorism.
- A multi-pronged approach to address Cyberterrorism through training and professional development
- How Fintech is becoming targets of cyber terrorists.
- The motivation behind Cyberterrorism.
- Role of cyber forensics in fighting cyber terrorism.
- Intelligence gathering and sharing as a countermeasure for cyber terrorism.
- Impact of Cyber Security Risks on Businesses Cyber Security Policies.
- Activism, activism, and Cyberterrorism.
- Implications of different laws on prosecuting cyberterrorists.
- Cyberspace as a medium that terrorists can use.
- Global law enforcement on cyber-crime.
- Agroterrorism, its consequences, and mitigation strategies.
- The link between agroterrorism and bioterrorism.
- Blue Balls Theory and Domestic Terrorism.
- The vulnerability of social engineering.
- Dark Web and Cyberterrorism.
- Impacts of Cryptocurrencies on Cyberterrorism
- Role of computer forensics in preventing Cyberterrorism
- How Cyberterrorism can impact the Internet of things
- The use of social networks to recruit cyber terrorists
- Five levels of cyber threat and vulnerability
- The role of Data Governance in preventing cyber-terrorist Attacks
- Multiagency approach to preventing Cyberterrorism
- Use of digital footprints to thwart cyberterrorists
- Cyber hypnotism and cyber vigilantism in fighting cybercrime
International Terrorism Research Paper Topics
Terrorism happens on a global scale. Given the connectedness of different parts of the globe, thanks to globalization, the impacts of terrorism in one state can spill over to others. Here are some thoughtful global terrorism topics:
- Impacts of terrorism and extremism on emerging markets
- The future of terrorism in a globalized society
- Role of governments in combating global terrorism
- The impacts of immigration in Europe on terrorism
- The sociology and psychology of terrorism
- Can strict immigration policies solve the threat of terrorism?
- Understanding the funding mechanisms of global terror cells
- Post-911 strategies to combat terrorism in America
- Role of homeland security in preventing terrorism
- The use of the vulnerable and children to do terrorist acts
- The representation of terrorism in the international media
- How terrorists recruit and radicalize the recruits
- The annex between terrorism and political instability in the Middle East
- Bioterrorism
- Treaties against bioterrorism
- Differences between Political and Non-political terrorism acts
- Role of the United States in fighting Global terror
- The role of the FBI and CIA in combating global terror
- The impacts of travel advisories on terrorism attacks
- Role of Interpol in Counterterrorism
- Deconstructing the role of blackmailing in terrorism
- Nuclear terrorism and its threat to global peace
- Understanding terrorism cells
- The purpose of social media on terrorist recruitment
- A comparison of the link between global terror groups
- Evaluating the counterterrorism strategies and policies
- National terrorism prevention strategies in the USA
- Role of international organizations in preventing terrorism
- The connection between terrorism, drug trafficking, and human trafficking
- Terrorism and arms trafficking
- Jihadism and terrorism: Demystifying the Essentials
- Methods of countering radicalization of the youths
- Human rights violations during terrorist attacks
- Can terror suspects released from prison be reintegrated into society
- Role of racism and discrimination in terrorism
- Community policing and terrorism
- Understanding domestic terrorism
- Homegrown Terrorism in the UK and USA
- Porous borders and terrorism
- Role of the UN Security Council in fighting terrorism
- The role of films and movies in promoting terrorism
- How the terrorist groups use the media
- Anthropological basis of terrorism
- How society should respond to terrorism
- Impacts of terrorism on air travel
- Impacts of terrorism on global trade
- Comparison of impacts of terrorism on France and the USA
- The entry of Russia and the USA as a creator of today's terrorism
- Why has terrorism increased in the 21 st century?
- Psychological impacts of terrorism
- Can institutions of global governance address terrorism?
- The use of chemical weapons by ISIS in Syria
- How the invasion of Libya by the USA led to the rise of terror groups
- The organizational structure of terrorist groups
- The most popular terrorist groups globally
- Strategies used by terrorists to radicalize youths
- Ethical issues in domestic terrorism
- Impacts of international terrorism on tourism
- Role of surveillance in combating terrorism
- Racial profiling in the war against terror
- The role of Osama in 9/11
- Methods used in interrogating terror suspects by the US soldiers post 9/11
- Role of ISIS and Al Qaeda on international terrorism
- How the rich Middle East nations support terrorist groups
- How terrorist groups benefit from the proceeds of Oil
- The social process of terrorism
- Models of terrorism
- The role of the Internet on the development of terror groups
- The new strategies used by terrorists
- The Antiterrorism and Effective Death Penalty Act of 1996
- The role of Middle East governments in funding terrorism
- Can nations win the global war on terrorism?
- The use of torture to fight terrorism
- History of terrorism
- Trends of terrorism in the social media age
- How terrorism created a super-powerful Israel
- Impacts of international relations on terrorism
- Motivations of terrorist groups to attack the USA
- Impacts of terrorism on children and women
- Al Shabaab and Bokoharam as new terrorist groups
- The nexus of international organized crime and terrorism
- Domestic terrorism in the USA
- Homegrown Terrorism in the US
- Historical roots of domestic terrorism
- The role of intelligence sharing in combating terrorism
- Challenges in multiagency counterterrorism approaches
- Why terrorist groups like the MENA region
- Terrorism and political violence
- Is the Hiroshima Bombing an act of terror?
Terrorism and Religion Research Paper Topics
- The link between terrorism and religion
- Religious fundamentalism and terrorism
- Perceptions of Arab-Americans being viewed as terrorists
- How Muslim Arabs and Muslim Americans are being branded as terrorists
- Role of religiosity on terrorist group affiliation
- Religious motivations of terrorist groups
- Media framing and terrorism
- How the international media frames Islam and terrorism
- The link between Terrorism, Islamophobia, and Anti-Semitism
- Deconstructing the Holly terror ideology.
- The Implications of Terrorism Motivated by a Religious Imperative
- How extremists use religion as a getaway for terrorism
Now, you can spend the whole day, a week, or a month brainstorming on a terrorism topic or war on terror topics for your research paper.
If you need help with choosing a topic, writing a draft, and writing a sample terrorism paper, our research paper writing service is always the best. You can place an order and let us assign your research paper on terrorism to a professional writer. We are the best place to hire someone to write your research paper. All those who have bought research papers from us can attest to the success that preceded their bold move. Do not hesitate to talk to us if you need help.

Gradecrest is a professional writing service that provides original model papers. We offer personalized services along with research materials for assistance purposes only. All the materials from our website should be used with proper references. See our Terms of Use Page for proper details.

Top 100 Terrorism Essay Topics for Students
Sep 13, 2021 | 0 comments

Sep 13, 2021 | Topics | 0 comments
Most people in the world know what terrorism is, but most of us don’t have a good understanding of it. To understand and combat this problem, we must first define terrorism for ourselves. Terrorism can be defined as any act that threatens life or property with the intent to intimidate civilians from exercising their basic civil rights, such as freedom of speech. Whether by threatening violence against them directly or indirectly through fear-inducing words like death threats, acts designed to influence government policy on an issue at home or abroad. It also the intimidation meant deliberately harm innocent bystanders who are not partaking in military action (such as bombings). The topic of terrorism is no stranger to difficulty, as not all students can find appropriate topics for essays . We understand how difficult it can be to find new and interesting ideas when other people have already explored the subject thoroughly in their essay papers. However, we’ve compiled a list of 10 popular research paper topics that will help you get your best grades ever. With these easy-to-follow tips from our writers at PaperMarti’s blog, there should be nothing stopping you from getting an A+ grade on your next terrorism assignment.
Table of Contents
Relevant terrorism essay topics
- Is it proper for the government to negotiate with terrorists?
- How parents can discourage their children from joining terrorist groups
- Why should the government make deals with terrorists?
- Terrorism and blackmailing
- How to combat nuclear terrorism
- Things that make an individual become a terrorist
- How the media and films portray terrorism
- Why do some politicians use terrorism as a political tool?
- The most popular and powerful international terrorism groups: Al Qaeda, Boko Haram, and others.
- Common motives behind terrorist attacks
- Is the model of Israeli society good for fighting terrorism?
- How did terrorist groups come into existence?
- How can the government discourage its citizens from becoming terrorists?
- Why do terrorists sometimes pretend to be fighting for religion?
- How has the advancement in technology affected the tactics of terrorists?
- The link between terrorism and human trafficking
- How has terrorism affected the world over the last decade?
- How can terrorism affect the government?
- Why do terrorists take responsibility for terrorist acts?
- The history of terrorism
- The biggest terrorist attack the world witnessed
- What should be the first psychological aid to witnesses of terrorist acts?
- Is it possible to escape a terrorist cell?
- Is it possible to respond to terrorism without resorting to violence?
- The proper way to handle terrorist cases
- How can society prevent terrorism?
- How is the government combating terrorism?
- What the government Is Doing to Stop Bioterrorism
- Partisan movements and terrorism
- Ideological terrorism
- What role did terrorism play in the creation of Israel?
- Terrorism is an international crime.
- How the citizens can help the government in eradicating terrorism in the country
- Can We Consider Hiroshima Bombing as Terrorism?
- How terrorists often take responsibility for terrorist acts
- Who is a terrorist?
- How terrorism serves as a barrier to international travel in some parts of the world
- What causes terrorism?
- Why do some terrorists resort to suicide bombing
- Why do terrorists use hostages? How do these hostages survive?
- Can the world be free from every form of a terrorist act?
- Can public enlightenment reduce the acts of terrorism?
- What should be the proper punishment for anyone who takes part in acts of terrorism?
- The Cooperation between Terrorism and Mafia
- Terrorism and its impact on society
- Reasons that may justify terrorist acts
- Counterterrorism Is Everywhere
- How can terrorism be used to the advantage of particular political forces?
- Terrorism can serve as a tool for politics
- Does terrorism play any useful role in society?
- What differentiates political terrorism from non-political terrorism?
- Why The Incels Movement Could be a Big Danger in the Future
- The right ways schools can enlighten students about the dangers of terrorism
- The recruiting strategies of terrorists
- Things that make people resort to terrorism
- Reasons to say no to terrorism
- How to work with society in preventing terroristic acts
- The use of minor social groups in terrorist acts
- What are the Justified methods for fighting terrorism?
- Motivations of terrorist groups
- Is the US government doing enough to combat terrorism?
- Was Guantanamo Bay Detention Camp Justified?
- The most acknowledged counterterrorist operations
- Psychological conditioning of suicide bombers
- What could be the future of terrorism?
Get Help from the Experts with your Terrorism Essay Topics Paper
We’ve covered a lot of ground in this article, so it would be wise to take some time and reflect on what you want out of your research paper. If you need help with brainstorming or structuring an argument, let us know. Our writers are here for you 24/7. Don’t forget that we also offer editing services if there is any last-minute proofreading needed before submitting your work. Place your order today and get the writing assistance you deserve. Have fun researching terrorism essay topics; make sure not to do all the hard work yourself !

With a passion for education and student empowerment, I create blog content that speaks directly to the needs and interests of students. From study hacks and productivity tips to career exploration and personal development
People Also Read
- Top 100 Biology Essay Topics for Students
- Top 100 Road Essay Topics for Students

Most Popular Articles
Racism thesis statement example, how to rephrase a thesis statement, capstone project topic suggestions, how to write an abortion essay, should students wear school uniforms essay, list causal essay topics write, respect essay, signal words, great synonyms, informative speech examples, essay writing guide, introduction paragraph for an essay, argumentative essay writing, essay outline templates, write an autobiographical essay, personal narrative essay ideas, descriptive essay writing, how to write a reflective-essay, how to write a lab report abstract, how to write a grant proposal, point of view in an essay, debate topics for youth at church, theatre research paper topics, privacy overview.
15 Useful Examples of Terrorism Research Paper Topics
Note: Only 'PhD' academic level option is available for Dissertation
23 Oct 2019
Place an Order
You can use it on one order over $
How to Come Up with Good Research Paper Topics About Terrorism?
The topic you choose has a significant influence on your entire approach to your writing a paper and eventually defines your grade in some way. So before you begin thinking over gripping introduction, arguments, analysis points and presume how to end a research paper about terrorism, you need to pick up a workable theme. Here are of the signs of a good topic to keep in mind:
- it is interesting to you;
- it's meaningful and relevant to the modern world;
- it is narrow enough to answer one specific question in the paper;
- it is broad enough to present a number of aspects under one issue.
As you can see, having not a run-of-the-mill topic is necessary for proper study when drafting an effective thesis statement and outline. You don’t want to select what would make you struggle when researching information or omitting ideas having too much of it. However, by following three simple steps presented below, you can choose a thoughtful paper topic you will be excited to write about.
- Brainstorm paper ideas. Think very broadly and make a note of topics that pop into your head. Consult the syllabus to see which aspects are the most relevant within this particular course. Here you do not need a cohesive statement, just let your brain make pleasant and unexpected connections. Write down your areas of interest and narrow the list down to two or three potential topics.
- Do the research. Go to the university library and delve deep with the encyclopedia, articles or online publications on the subject. Choose trustworthy, factual sources and adhere to the guidelines provided by your professor. After proper research, pick up one topic that you like most and that has enough reference sources to draw from.
- Refine your idea. Phrase the topic into a specific research question that you are going to answer in your paper. Then, narrow the scope with adding some details: time frame, geography, or population limitations are common ways to do this. Shortly speaking, make your question more precise by approaching it in a unique manner.
Of course, after you’ve settled down with the topic, now the fun part of writing begins. Though, if you are still deciding on the subject to cover, in the next paragraphs our skilled research paper writers have provided a list of exceptional topics you are welcome to try.
International Terrorism Research Paper Topics to Write About
Nowadays, acts of terrorism occur all over the world, spanning from the Middle East to Europe, Latin America, and literally every part of the globe. It’s a day to day issue happening to innocent citizens of their states. Terrorism is different in its forms and affects different areas of our like. Hence, there is a wide range of aspects you can cover in the research paper:
- How do extremism and terrorism affect global emerging markets?
- Role of the UN Security Council in preventing
- Which groups of people would benefit the most from putting an end to the war of terrorism?
- How has the perception of terrorism shaped by mass media evolved?
- Main differences between political and non-political acts of terrorism.
Terrorism in 21st Century - Top Research Paper Ideas
In recent years, terrorism has spread its tentacles far and wide and is one of the favorite methods of fanatics to get what they desire. Moreover, new methods of terrorist attacks appear – from biohazards to cyber-attacks. This all requires us to be always on the lookout and stay flexible in developing ways of its prevention. Here are some of the palpitating terrorism topics for research paper worth considering.
- Global terrorist threats focusing on Africa and the Middle East.
- Is the threat posed by ISIS and other modern terrorist organizations overhyped?
- What are the roots of the rise of Islamic extremism in France?
- Does exposure to cyber terrorism affect psychological well-being and political attitude?
- How has terrorism changed after the September 11, 2001 tragedy?
- Why is the Internet the potential weapon for terrorists?
- What are the new US strategies to combat terrorism?
- How has the immigration issue within the EU and Schengen agreement influenced terrorism issues?
- What future do you predict for terrorism and its forms?
- What is the current threat level to the United States and why?
We hope that our topics will give you a fresh impulse for crafting a top-notch paper. However, if it’s hard for you to write a paper or you want an expert eye to proofread it, just reach out to us, and we will gladly accompany you during your academic writing journey.
Related posts:
- Good Article Review About The Real Leadership Lessons Of Steve Jobs
- Cognition Research Papers
- Anger Essays
- Contest Essays
- Economic Geography Essays
- Chicken Essays
- Macbeth Essays
- Human Nature Essays
- Spirituality Essays
- Greenberg Essays
- Bargain Essays
- Medical School Essays
- Astrology Essays
- Glucose Essays
- Juvenile Diabetes Essays
- Kidney Essays
- Serum Essays
- Hypoglycemia Essays
- Graduation Essays
- Perfection Essays
- Graphic Essays
- Drill Essays
- Shine Essays
- Downtime Essays
- Henry Ford Essays
- Acreage Essays
- Estate Essays
- Thomas Jefferson Essays
- Sectional Essays
- Six Sigma Essays
- Elite Essays
- Imbalance Essays
- Carbon Atom Essays
- Impression Essays
- Label Essays
- Album Essays
- Emergent Essays
- Suit Essays
- Dawes Essays
- Gilded Age Essays
- Plain Essays
- Housewife Essays
- Suitcase Essays
- Pinto Essays
- Circulation Essays
- Retina Essays
- Stainless Essays
- America Essays
- Anti-Imperialism Essays
- Black Music Essays
- Coca Cola Essays
- Community Essays
- Data Analysis Essays
- Digestive Essays
- Emperor Hadrian Essays
- Good Deeds Essays
- Infinitesimal Calculus Essays
- Iskandar Essays
- Management Of Hypertension Essays
- Media Literacy Essays
- Nothing Gold Can Stay Essays
- Organized Religion Essays
- Pablo Picasso Essays
- Parol Evidence Rule Essays
- Peak Expiratory Flow Essays
- Receiver Essays
- Retinol Essays
- Risk Essays
- Street Credibility Essays
- The Alienist Essays
- Vitalism Essays

We use cookies to improve your experience with our site. Please accept before continuing or read our cookie policy here .
Wait, have you seen our prices?
Research and term paper writing guidelines
Our editorial team consists of academic writers, editors and professors who have joined their efforts to build a free online resource for students.
- Term paper sections
- Term paper outline hints
- Research proposal samples
- Writing an acknowledgement
- Drafting a conclusion
- Biology topics to explore
- History paper bibliography
- Best topics on terrorism
- Business paper templates
- Term paper writing process
- Music paper topics
- Writing on hurricane Katrina
- References page format
- Paper on renewable energy sources
- Professional assistance
- Education paper topic
- 5 ways to get academic help
- Good topics in psychology
- Tips for middle school
- Best places to seek assistance
- Writing about Roman Empire
- Exploration paper intro
- Agencies you can rely upon
- Sociology term paper topics
- Sample papers on religion
- 8 steps to success
- Buying a project for cheap
- How to avoid frauds
- APA format presentation
- 5 Psychology topics
- Hiring a professional writer
- How to pick a History topic
- High school paper topics
- How to find a writing company
- Term paper help
- Writing an MLA term paper
- Selecting exciting topics
- Argumentative paper topics
- Proposal writing tips
- 10 great research paper topics
- Term paper topic selection
- Globalization paper sample
- Crafting a thesis statement
- How to pick up a topic
- Research topics
- 6 Psychology paper topics
- Useful term paper guide
- Fast term paper writing tips
- A term paper abstract sample
- Analysis paper tutorial
- Term paper ideas
- Quick essay paper writing tools
- Web sites selling papers
- Scientific term paper guide
- Improving academic papers
- Cinderella paper sample
- Business paper topics
- Term paper topic finding advice
- Dressing up your essay
- Thesis outline composing guide
- Thesis statement tips
- Hypothesis statement hints
- Writing an exploration paper
- Research proposal
- Research paper draft writing
- Computer science paper
- Academic paper help
- Composing a term paper topic
- Best sports topics
- Research paper samples offline
- Fresh ideas for your paper
- Political research topics
- Term paper education topics
- The thesis and the draft
- High School research paper samples
- APA research project title page samples
- Sports research paper subjects
- Health care research project topics
- Composing a midterm paper outline
- APA format project cover page
- A research project about insomnia
- A project about academic success
- Creating an introduction on bullying
- A 7th grade research project
In recent years, thousands of students were expelled and punished for plagiarism issue with their papers. Learn how to protect yourself using well-known plagiarism detection software.
Consider yourself an expert in writing academic papers? Want to help fellow college students from US, UK and Canada? Join our team!
Research Paper Topics On Terrorism: 15 Interesting Writing Ideas
If you are looking for an interesting writing idea for a research paper topic on terrorism consider the following:
- you can review current ethical implications associated with torture
- You can explore personal freedoms and the use of terrorism
- You can explore the limits between religious freedom and terrorism
- You can explore the relationship that exists between politics and Law
- You can explore international law including human rights law
- You can explore preemptive counterterrorist measures and the challenges it presents to human rights
- You can explore the definition of terrorism
- You can explore prevention methods and human rights
- You can create a paper that focuses on the right to self-determination
- You can review whether a victims government should be trusted with the punishment and the trial for a terror suspect
- You should review whether international law criminalizes terrorism
- You can review whether there is a neutral international definition for terrorism
- You can review whether terrorism should be added to the crimes over which the international criminal Court has jurisdiction
- You should review whether national leaders should be tried for their counterterrorism policies if they are in excess
- You should review whether lawyers should be tried if they give advice to governments about excessive counterterrorism policies
One of the best ways to stay organized when you are conducting research is to bring with you multiple colored pens or notecards. If you designate one color for one topic or alternatively, one color for main topics and one color for supporting evidence, you can keep your information organized. By maintaining such organization you can make it significantly easier to play around with the order of your arguments until you find the best presentation of your information.
If you are researching at a library it is important that you always write down related bibliographic information. Many students who are either in a rush or excited about finding pertinent information will immediately photocopy relevant pages and bring them back for print off important quotes. But in cases like this they often tend to neglect the pertinent bibliographic information. By not writing down the bibliographic information mind that later on when you need to create your in-text citations and references page you are lacking the necessary information. Once you have written down all pertinent bibliographic information It is important to keep it all in one place. Having all of this information together will not only provide you with multiple copies of your bibliographic information but will also give you the opportunity to more easily and quickly format your citations when you find the time.
Terrorism Essay Topics & Ideas
- Terrorism Essay Topics for High School Students
- Terrorism Compare and Contrast Essay Topics
Argumentative Essay Topics About Terrorism
Good essay topics about terrorism, persuasive essay topics about terrorism.
- Interesting Essay Topics About Terrorism
✒️ Terrorism Essay Topics for High School Students
- A Criminal Justice Approach to Suppressing Terrorism
- A Research on Terrorism Before and After the September 11, 2001 Attacks Research
- A Review of Greece’s Effort to Thwart Terrorism
- A Study of The Impact of Anti Tax Evasion, Anti Terrorism and Anti Money Laundering Measures Taken on Americans Living Overseas
- Adjusting to Terrorism
- Adjusting to Terrorism in Modern World Term
- Adjusting to Terrorism in the United States
- Al-Qaeda Emergence, Ideology, and New Terrorism
- Ali Al-Timimi’s Case of Terrorism
- America’s War on Terrorism
- American Governmnet Against the Threat of Terrorism Research
- An Argument Against Corrado and Cohen’s Theory of Political Terrorism
- Analyzing the Concept of Terrorism Definition
- Anti Money Laundering and Combating the Financing of Terrorism
- Background of the Terrorism
- Benefits of Preparing for Emergencies and Terrorism Term
- Can terrorism be justified?
- Can Terrorism Only Be Defeated by Military Means?
- Cause and effect of terrorism
- Causes and Motivations of Terrorism Term
- Combating the Threat of Nuclear Terrorism
- Common Definition of Terrorism
- Comparison Between Organized Crime And Terrorism
- Concept of Terrorism Phenomenon in Modern World

✨ Best terrorism Topic Ideas & Essay Examples
- terrorism position paper Measures To Eliminate International TerrorismTerrorism has been an international nuisance for an extremely long time. Terrorism has been usedto express political and religious beliefs, in retaliation for certain wrongdoing, and in other cases for ….
- Terrorism Research Paper What are the What are the causes of terrorist act and how can it be stopped? “ Terrorism and guerilla warfare, whether justified as opposition to subjugation or condemned as interrupting the regulation of jurisprudence, are every bit old as civilisation itself. ….
- Public Resilience Against Terrorism Terrorism is a disease that has plagued the society for a long time. The main objective of most terrorist organizations and individuals is establishing an atmosphere of panic and fear among the members of the public. As a result, the public turns ….
- Terrorism And Security in the Olympics Security is a fundamental notion in sports. Nowadays athletes are viewed often through the media, therefore they are recognizable. In the Olympics security measures must be taken to protect the athletes. There are many different nationalities ….
- The Impact of Terrorism to Homeland Security Terrorism has been a worldwide concern of countries in view of the increased attacks causing destruction to lives and properties of hundreds of people. It does not discriminate on race, sex and gender nor does it respect human rights, and it seems ….
- What is the relationship between terrorism and globalization? From this essay, I will explain the relationship between terrorism and globalization. Terrorism has always been defined as a very negative ideology and philosophy for western countries, and even until today, there has not been a single agreed ….
- Combating Terrorism and USA PATRIOT Act At 8:45am, on September 11th, 2001 America’s heart was torn by a hijacked plane crashing through the north tower of the World Trade Center. Eighteen minutes later, a shocked country received a second blow as a second plane tore through the south ….
- Extraordinary Rendition And Terrorism Criminology What is terrorist act? Although it is hard to come to a cosmopolitan definition of terrorist act, it can be described as warfare affecting the usage or menace of force, typically against an influential noncombatant mark, with the thought of making ….
- Terrorism in Southeast Asia Terrorism in Southeast Asia Bruce Vaughn, Coordinator Specialist in Asian Affairs Emma Chanlett-Avery Specialist in Asian Affairs Ben Dolven Section Research Manager Mark E. Manyin Specialist in Asian Affairs Michael F. Martin Analyst in Asian Trade ….
- Media and Terrorism When the word “terrorists” is heard, most people in the west think of relatively the same thing. Long-bearded men with long dresses called “thawb” that dangle to just above the ankle, or veiled women with nothing visible to the public but their eyes ….
- Differences Between Old And New Terrorism Criminology Terrorism is non a new construct, and despite it was used really frequently over the past decennary, it remains one of the most hard issues to specify. Its ambiguity comes from the different intensions that the term has gained over history. James D. ….
- Adjusting to Terrorism Is Not New Terrorism is not new, and even though it has been used since the beginning of recorded history it can be relatively hard to define. Terrorism has been described variously as both a tactic and strategy; a crime and a holy duty; a justified reaction ….
- Terrorism Liberalism Realism Since September 11, 2001, terrorism has captured the attention of Americans to such an extent that it is the main force driving our nation’s foreign policy. The Bush doctrine, which seeks to justify pre-emptive strikes against threats to American ….
- Short Essay- Terrorism Terrorism and terrorists are defined as people who cause death and destruction through means of bombs and hostage taking who bassically cause terror for religious reasons or another cause they see just. After the end of the cold war people claimed ….
- Types of Terrorism Terrorism in the United States has taken a big step since 9/11. After 9/11 there have been more and more police officers working. There are a lot or terrorist groups around the world but there are also motivational terrorist. The word terrorism does ….
- Terrorism over the past Century Essay Over the past Century, terrorism has evolved from random killings to massive plans for terrorist groups. To understand terrorism you must first describe it. There have been many different definitions of terrorism. The one that truly describes it is; ….
- Does Islam Promote Terrorism Islam is derived from the word ‘salam’ which means peace and shows its followers how to preserve and encourage peace all over the world. Unfortunately more and more often, Islam has been associated with terrorism and violence due to the actions of a ….
- Terrorism and homeland security The region around the Persian Gulf has been the focus of world attention during the Iran-Iraq war (1980-1988) and the 1991 gulf war when Iraq invaded Kuwait but was expelled by American forces. The Persian Gulf region has huge oil and natural gas ….
- Terrorism on Tourism The economic importance of tourism is undeniable. The impact of terrorism on a countries economy may be enormous. In an information free society, tourists might travel to destinations regardless of whether a terrorism threat exists or not. However, ….
- Terrorism Short Essay The definition of terrorism according to Webster’s Dictionary is “the use of force or threats to intimidate.” The news is filled with references to terrorism worldwide. Thousands of people have been killed in many countries because of terrorism. ….
✍ Terrorism Compare and Contrast Essay Topics
- Conventions on Terrorism in the 21st Century
- Coping with Terrorism in the USA
- Counter Terrorism and Public Awareness Plan Coursework
- Counter Terrorism measures in the UK
- Counter Terrorism Policies and Organizations in Iran
- Countering Global Terrorism
- Crime Myths and Domestic Terrorism Report
- Crimean Crisis and Russian State Terrorism
- Criminology and Terrorism
- Current Hurdles in Combating Terrorism Essay (Critical Writing)
- Current Issues in Iraq and Terrorism
- Cyber Terrorism and Information Warfare
- Cyber Terrorism as a Major Security Challenge
- Death Penalty for Murder by Terrorism Research
- Defense Imperatives: “Thwarting Terrorism & Bringing Terrorists to Justice”
- Definition of Terrorism And Police Powers
- Digital Media Usage to Recruit and Promote Terrorism Report
- Domestic & Global Terrorism and Its legal Aspects Research
- Domestic Terrorism and Homegrown Extremism in America Research
- Domestic Terrorism in the Post 9/11 Era
- Domestic Terrorism in the United States of America Research
- Domestic Terrorism in USA Research
- Early Response to Weapons of Mass Destruction Terrorism Research
- Eco-Defense and Kinds of Ecological Terrorism
- Effects of Terrorism
- Effects of Terrorism in Indian Industries
- Effects of Terrorism on International Business: A Detailed Analysis
- Egyptian Tourism Industry and Terrorism Effects Proposal
- Eliminating Terrorism at the Domestic Level Term
- Eradicated Terrorism in the World Term
- Ethnic, Racial and Religious Profiling in Terrorism Research
- Factors That Motivate to Terrorism
- Facts about Counter Terrorism
- Foreign Policy: United States and Fight with Terrorism
- Four Priorities of Action for Combating Terrorism on Our Shores
- Fraud, Money Laundering, and Terrorism Financing
- Global Terrorism and State Security Measures Research
- Hashemite Kingdom of Jordan and Terrorism Research
- Have Terrorism Laws been Helpful?
- Hazard Vulnerability Analysis and Terrorism Case Study
- History and Financing of Terrorism
- History of Cyber Terrorism Research
- Homeland Security and Terrorism
- Homeland Security Changes: Adjusting to Terrorism
- Homeland Security: Collecting Information about Terrorism Research
- Homeland Security: Terrorism Issue
- How Counselors Assist Survivors of Terrorism Research
- How Does Modern Terrorism Operate?
- How Terrorism Affects Airline Security
- How The Digital World Can Lead to a New Type of Terrorism
- Human and Technical Intelligence in Countering Terrorism Analytical
- Human Rights and Terrorism
- Human Rights, Terrorism and Counter-Terrorism
- Immigration Services Against Crime and Terrorism Case Study
- Impact of Terrorism and Violence on Global Tourism
- Impact of terrorism on Italian economy Research
- Impact of Terrorism on the Economy
- Impact of War, Conflict & Terrorism on the UPS
- Industrial Terrorism in Modern World Term
- Informative Essay on Terrorism
- Intelligence, Civil Law, and Terrorism Investigations
- International Political Economy, Democratization, and Terrorism Essay (Critical Writing)
- Internet Crimes and Digital Terrorism Prevention Research
- Investigation Methods: Terrorism and Cyber Crime
- Is Terrorism a Muslim Monopoly
- Is terrorism a serious threat to international and national security
- Is terrorism a serious threat to national and international security?
- Is Terrorism an Act of War?: Different Types of Terrorism
- Is Terrorism Ever Justified? Research
- Is Terrorism Still the Most Important Security Issue for Australia?
- Is the War on Terrorism a War
- Isis: Terrorism and Richest Terrorist Group
- Islamic and Christian Religion and Terrorism Research
- Islamic Terrorism in the “Body of Lies” Film Research
- Law Enforcement and Terrorism
- Local Response to Terrorism Research
- Local, State, and Federal Partnerships: Terrorism Case Study
- Media and Terrorism Essay (Article)
- Media and the War on Global Terrorism
- Modern Terrorism and Globalization
- National Security Strategy Against Terrorism in The United States
- NATO and Terrorism
- Nigeria – Preventing Nuclear Terrorism
- Organizational Change: Models Influencing American Terrorism
- Organizations for the Definition of Terrorism and Their Assessment
- Organized Terrorism Against Government Leaders Term
- Origins of Terrorism and Solutions
- Palestinian Islamic Jihad: Radical Terrorism Report
- Port Security Operations and Maritime Cyber Terrorism in USA
- Preparing for Incidents of Terrorism at the Local Level Research
- Primoratz’ Definition of Terrorism
- Problem of Cyber Security and Terrorism
- Protecting Human Rights While Countering Terrorism
- Psychological Profiling in Terrorism Prevention Report (Assessment)
- Psychology of Terrorism and Political Violence
- Public Fear of Terrorism
⭐ Interesting Essay Topics About Terrorism
- Recent Developments in the History of Terrorism
- Reflections on the Course Counter Terrorism
- Religion and Terrorism
- Religious fundamentalism and terrorism
- Risk of Terrorism Financing in Non-profit Organizations
- Role of Youth in Combat Terrorism
- Rumsfeld’s Memo & the War on Global Terrorism Analytical
- Salifist Takfiri Terrorism Coursework
- Saudi Arabian Lone Wolf Terrorism in 2011-2016
- Similarities Between Terrorism and Organized Crime:
- State-Sponsored and Non-State Terrorism Essay (Critical Writing)
- Suicide Terrorism and Its Psychological Factors Research
- Technology-the Future of Terrorism
- Terror and Terrorism Analytical
- Terrorism and Drug Trafficking at The South American Borders
- Terrorism and Human Rights
- Terrorism and Immigration Legal Report
- Terrorism and Its Impact on Muslims
- Terrorism and Its Organisations: Al Qaeda and ISIL
- Terrorism and Jihad Report
- Terrorism and Just War Theory
- Terrorism and Liberal Democracy: What We Should Know
- Terrorism and Media
- Terrorism and Modern Society
Get a Quality Essay on Your Topic
Other Topics
- Holocaust Essay Topics & Ideas
- History Research Paper Topics
- Imperialism Essay Topics & Ideas
- Industrial Revolution Essay Topics & Ideas
- Julius Caesar Essay Topics & Ideas

Hi, my name is Amy 👋
In case you can't find a relevant example, our professional writers are ready to help you write a unique paper. Just talk to our smart assistant Amy and she'll connect you with the best match.
- Homework Help
- Essay Examples
- Citation Generator
- Writing Guides
- Essay Title Generator
- Essay Topic Generator
- Essay Outline Generator
- Flashcard Generator
- Plagiarism Checker
- Paraphrasing Tool
- Conclusion Generator
- Thesis Statement Generator
- Introduction Generator
- Literature Review Generator
- Hypothesis Generator
- Human Editing Service
- Essay Hook Generator
- Terrorism Essays
Terrorism Essays (Examples)
Filter by keywords:(add comma between each), example essays.

Terrorism Refers to Threats Violence Bombings Etc
Terrorism refers to threats, violence, bombings, etc. Terrorism is known to have a long history, but even today, the reason behind this terror by the super powers and the government remains explicit. The acts of terror are very common these days and could be found in current political and social environment. A part of terror is still confused when it is applied in the actual present world (obb, 2007). Where the word terrorism comes from and its definitions According to the department of USA that deals with terrorism, defense, violence etc., terrorism could be defined as "something that creates illegal violence, fear, chaos among the population. Common basis of terror are politics, religion or even ideology. They threat the society to achieve their goals." The main features are fear, threats and aggression that lead to terror in the victims. Another similar definition by the FBI states that terrorism involves illegal forces that…...
mla References Allen, C, (2006), God's Terrorists: The Wahhabi Cult and the Hidden Roots of Modern Jihad, Cambridge, MA, Da Capo Press. Bascio, P, (2007), Defeating Islamic Terrorism: An Alternative Strategy, Wellesley, MA, Branden Books. Nacos, B.L, (2006), Terrorism and Counterterrorism: Understanding Threats and Responses in the Post-9/11 World, New York, Pearson/Longman. Robb, J. (2007), Brave New War: The Next Stage of Terrorism and the End of Globalization, Hoboken, NJ, John Wiley & Sons.
Terrorism Define and Contrast the Many Definitions
Terrorism The term "terrorism" is profoundly political, as can be seen by the numerous definitions of terrorism and the lack of a globally-agreed description. The myriad definitions show nations struggling to define "terrorism" in self-serving ways. Efforts to clarify and unify those definitions vary from legalistic to nearly bombastic. After listing many definitions from different nations and from within the United States, itself, this paper examines a legalistic attempt to lay the groundwork for a universal definition, then a more cutting attempt to dispel the self-serving political "fog" surrounding these definitions. The common thread in both approaches is the appeal to diplomatically weigh competing national interests in order to form a workable worldwide definition of "terrorism Definitions of Terrorism a. UN General Assembly Resolution 54/109 (1999) "Criminal acts intended or calculated to provoke a state of terror in the general public, a group of persons or particular persons for political purposes are in any…...
mla Works Cited Arab Convention on Terrorism. (2009, June 18). Document: Arab Convention on Terrorism, 1998. Retrieved from Al-Bab Web site: http://www.al-bab.com/arab/docs/league/terrorism98.htm Department of Justice Canada. (2008, April 1). The Anti-Terrorism Act. Retrieved from Department of Justice Canada Web site: http://www.justice.gc.ca/antiter/sheetfiche/terrordefp1-terreurdefp1-eng.asp#tfpotdota Office of the Law Revision Counsel, U.S. House of Representatives. (2011, January 7). U.S. Code. Retrieved from U.S.Code.House.gov Web site: http://uscode.house.gov/uscode-cgi/fastweb.exe-getdoc+uscview+t17t20+1097+8++%28terrorism%29%20%20AND%20%28%2818%29%20ADJ%20USC%29%3ACITE%20%20%20%20%20%20%20%20%20 The Council of the European Union. (2002, June 13). Official Journal of the European Communities | (Acts adopted pursuant to Title VI of the Treaty on European Union) | Council Framework Decision of 13 June 2002 on Combating Terrorism | (2002/475/JHA). Retrieved from Eur-lex.europa.eu Web site: http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=OJ:L:2002:164:0003:0003:EN:PDF
Terrorism Influences
Terrorism Influences Terrorism has no specific definition and its definition largely depends upon the viewpoint of an individual for example Samuel Adams (a well-known revolutionary fireband) or Thomas Gefferson would have been terrorist from ritish perspective but they have been Great heroes from American perspective. Take the case of George Washington who was previously fighting with ritish army against French and was loyalist of ritish crown but later on he sought American independence from ritish rule and became terrorist in the eyes of ritish (Kreamer). ut there is an accepted definition of terrorism as UN has reached on no consensus but generally crimes against humanity, war crimes, cleansing of ethnicity and genocide are included in definition of terrorism. Recent trial of osnian Serb army Chief Ratko Mladic on the charges of genocide has been included in the concept of terrorism by various circles. Similarly, act of genocide by Hitler has also been…...
mla Bibliography Fine, J. (2008). contrastin secular and religious terrorism. Retrieved from Middle east forun: http://www.meforum.org/1826/contrasting-secular-and-religious-terrorism Kahn, P.F. (2004). Protection against weapons of mass destruction. Kreamer, T.A. (n.d.). Archiving early America. Retrieved from Sons of Liberty:Patriots or Terrorist: http://www.earlyamerica.com/review/fall96/sons.html Kurgel, L. (2011, August). e-International Relations. Retrieved from Terrorism and Global economy: http://www.e-ir.info/2011/08/31/what-is-the-impact-of-terrorism-on-the-ipe/
Terrorism Is a Weapon of
Global Jihad, a Myth or Reality The Jihad is often associated with a certain Muslim fight against the unfaithful, one that has been going on for decades now and which is unlikely to stop in coming years. However, despite this sustainable development of the notion and everything it entangles, it cannot be stated without a doubt that this is an obvious reality. This assumption is made based on the fact that the Jihad, as a means of war, is an artificial creation rather than one that is dictated by religion or supported by it. This perspective largely depends on the point-of-view that is applied when looking at the global jihad. Therefore, from the point-of-view of the extremist Muslims the Jihad is an inevitable took with which pressure is applied on the "unfaithful." It represents a legitimate expression of the will of the Muslim and is justified in particular by the fact that…...
mla Works cited Kaplan, Eben. Targets for Terrorists: Post-9/11 Aviation Security. Council of Foreign Relations. 2006. Available at http://www.cfr.org/publication/11397/targets_for_terrorists.html#3 Townshend, Charles. "Terrorism: in search of the definite article." Open Democracy. 2007, available at http://www.opendemocracy.net/conflicts/democracy_terror/what_is_terrorism Wilkinson, Paul. "The Strategic Implications of Terrorism." Terrorism & Political Violence. A Sourcebook. Indian Council of Social Science Research. Haranand Publications. India, 2000.
Terrorism Is at This Point One of
Terrorism is at this point one of the main threats that decision makers in the field of national security have to deal with especially in the United States. The issue has been raised mainly after the events from 9/11 2001, but have been a constant concern for the law enforcement agencies since the beginning of the 90s and even before. The United States have a particular way in which it deals with homeland security issues given the nature of its administrative and political organization. The national, regional, and local law enforcement agencies and subdivisions are the ones that provide the legal and operational framework and background for actions to be taken at all the levels that could be affected by a terrorist threat or by any time of threat posed at the homeland security. The present paper researches the role national security agencies have, with due regard for the shared responsibility…...
mla Bibliography Department of Homeland Security. (2013) "About" Official website of the Department of Homeland Security. Available at http://www.dhs.gov/about-dhs New York State Police. (2013)Specialized Services. Available at http://www.troopers.ny.gov/Specialized_Services/ New York State Police. (2013)Vision, Values and Mission. Available at http://www.troopers.ny.gov/Introduction/ Suffolk County Police Department. (2013) Specialized Units. Available at http://apps.suffolkcountyny.gov/police/specialunits.htm
Terrorism and National Policy
TEOISM & NATIONAL POLICY Terrorism and National Policy The main concern of the U.S. National Security Council relates to the existing terrorist movements that pose risks to Americans citizens and its territory. The U.S. has historically been one of the main targets of the Islamist terrorist groups alongside other countries such as Israel. The U.S. has undertaken various national policies to combat terrorism within and beyond its borders. However, the September 11 attacks on U.S. led the U.S. through Bush Administration to take up critical measures to deal with terrorism and its threats. This saw the U.S. attacking the backyard of renowned terrorists Iraq and Afghanistan being key targets. This led to the top leaders being killed and ushered in the leaderless Jihad terrorist movements existent today. These new movements demand new approaches to combat them. New ideologies and measures must be designed to ensure that the leaderless Jihad terrorist movements diminish. Sageman's…...
mla Reference List Cameron, Fraser. U.S. Foreign Policy after The Cold War. (London: Routledge, 2005), 64-98 Johnston, Douglas. Religion, Terror, and Error. (New York: ABC-CLIO, 2011), 55-94 Lebovic, James. Deterring International Terrorism And Rogue States: U.S. National Security Policy After 9/11, (New York: Taylor & Francis, 2007), 99-154
Terrorism the Efforts to Outdo Terrorists Are
Terrorism The efforts to outdo terrorists are seemingly falling off, leaving with it underprivileged notion of the prospective for a proper psychological involvement to terrorist perception only. However, the bulk research within this circumference have brought about hopeful as well as exhilarating beginning for an intangible progress in coming to terms to psychological procedure transversely to all ranks of terrorist activities. An argument has come up for much considerable detachment with a clearer task for psychological study to inform as well as improve realistic counterterrorism activities. This paper demonstrates knowledge and assimilation of terrorism perspectives, counter- and anti-terrorism, and aspects relating to prediction, prevention, mitigation, preparedness, response and post-response (recovery) activities and analyze it in terms of how it would be dealt with it in terms of a counterterrorism plan that includes orientation (diplomatic, military, law enforcement, etc.) and specific strategies and tactics you would develop relating to prediction, prevention, mitigation,…...
mla Work Cited Whittaker, D.J. (2012). The terrorism reader (4th ed.). New York: Routledge. (ISBN: 978-0-415-68732-4)
Terrorism Annotated Bibliography Gardner K L 2007 Fighting
Terrorism Annotated Bibliography Gardner, K.L. (2007). Fighting terrorism the FATF way. Global Governance: a Review of Multilateralism and nternational Organizations. (13:3). 325-45. FATF, or Financial Task Force, is considered a successful organization in terms of investigating how global terrorism is funded. Without financial backing, the complexities required that go into terrorism attacks would not be possible. Kathryn Gardner argues that other aspects of investigation into potential terrorist organization could benefit from duplicating the FATF model. The three factors Gardner identifies that are most pertinent to these investigations are: coordination, flexibility, and commitment by the government. dentification of terrorist threats and fighting global terror must be a joint effort. Only through coordinated efforts on the part of law enforcement agencies can terrorism be properly tracked and the threats evaluated. Although differing scholars have not decided upon a universal protocol for conduct, what they do all concur with is the idea that terrorist cells…...
mla In order to find ways to combat terrorism in the future, there should be increased focus on research into currently functioning organizations, how they communicate, and how they can access dangerous technologies. In this day and age, the world is changing rapidly and while we can learn about our own country's mistakes from past terrorist attacks, there is little else that can be gained in terms of combating terrorism or in predicting future attacks. By taking Ranstorp's suggestions seriously, emphasis can be placed on identification and proper research methodologies, thereby performing efficient work into prevention. Sinclair, S.J. & LoCicero, A. (2007). Fearing future terrorism: development, validation, and psychometric testing of the terrorism catastrophizing scale (TCS). Traumatology. Sage. (13: 4). 75-90. Samuel Sinclair and Alice LoCicero, in this study, have devised a scale by which potential psychological damage to terrorism can be measured. This is an important aspect of terror management theory (TMT). Terrorism, by the very definition of the word, are acts which are designed to inflict terror and therefore their psychological results are important components of their success. The scale measures these threats based upon three criteria, rumination, magnification, and helplessness. Although the test is designed to test the individual and how they respond to terrorism, it can be applied to a national scale. The more likely that a group is to psychologically break down in the threat of terrorist action, the more important it is to prevent action because the group will be more likely to be attacked. If a terrorist organization knows one country's population will be psychologically decimated, then it makes sense that they will devote their resources to harming that group instead of going after a more resilient population.
Terrorism in Northern Ireland Northern Ireland Has
Terrorism in Northern Ireland Northern Ireland has been traditionally associated with pleasant concepts standing as a reference to its beautiful landscape, its benevolent people, and the general atmosphere in the country. However, things have changed significantly in recent decades as terrorism has pervaded the nation and as terrorists there have become more determined and more powerful. hile the Irish Republican Army's choice to employ non-violent strategies in dealing with the government influenced many in thinking that Northern Ireland should no longer be considered a terrorism hotspot, the Real IRA's recent actions prove otherwise, taking into account that the group's members are resolute about having the whole world accept their thinking regardless of the fact that they have to kill innocent individuals in order to get what they want. Body Ireland has had a long history of political and social problems as a result of English intervention on the island. The fact that the…...
mla Works cited: Whittaker, David J., "TERRORISM READER," (Routledge, 12.12.2012)
Terrorism in Western Europe That Terrorism Be
Terrorism in Western Europe That terrorism, be it transnational or domestic, impacts negatively on the overall well-being of economies is a well-known fact. With that in mind, governments have overtime embraced numerous counterterrorism measures in an attempt to mitigate the adverse effects of terrorist activities. In this text, I concern myself with terrorism in Western Europe. In so doing, I will limit my discussion to two countries in Western Europe where I will explore the history of terrorism and the various counterterrorism efforts being undertaken by law enforcement. Terrorism in Western Europe: An Overview To a keen analyst, Western Europe remains one of the most developed regions in the world today in terms of democracy and freedom. Further, most of the countries in this region are relatively wealthy and provide their citizens with significant rights and privileges (Engene, 2004). However, though Western European countries have relatively responsible governments in comparison to other countries…...
mla References Antonello, P. & O'Leary, A. (2009). Imagining Terrorism: The Rhetoric and Representation of Political Violence in Italy 1969-2009. MHRA. Engene, J.O. (2004). Terrorism in Western Europe: Explaining the Trends since 1950. Edward Elgar Publishing. Kearns, T.C. & Weber, J.L. (2010). Terrorism. Infobase Publishing.
Terrorism Memo to the Department of Homeland
Terrorism Memo to the Department of Homeland Security: There are federal statutes on the books that can help address the way that terrorists finance their draconian operations. This document delves into the specifics of how financing can be cut off or at least addressed to some extent, enough to bottle up terrorist movements which of course require money. hat is terrorist financing? Jeff Breinholt coordinated the Department of Justice Terrorist Financing Task Force in 2003, and he published an article explaining what the law is in the United States vis-a-vis terrorist financing. "Terrorist financing enforcement has emerged as a powerful means of disrupting…" those terrorist supporters in the U.S., and also "…those who use our financial system and generosity against us" (Breinholt, 2003, p. 1). Breinholt explains that terrorist financing entails "…the act of knowingly providing something of value to persons and groups engaged in terrorist activity," this crime has actually been in the…...
mla Works Cited Breinholt, Jeff. (2003). Terrorist Financing. United States Attorney's Bulletin. 51(4). Retrieved November 13, 2012, from U.S. Department of Justice. Elsea, Jennifer K. And Murphy, Maureen M. (2006). Treasury's Terrorist Finance Program's Access to Information Held by the Society for Worldwide Interbank Financial
Terrorism Is an Act That Requires Will
Terrorism is an act that requires will, determination, conviction, and intelligence to number merely a few attributes. Whereas the first three regard purely motivational attitudes, the latter implies the skillfulness to act according to what drives the act. Today, technology facilitates terrorist activities and thus national security is more so endangered and with it, people's lives and the well being of societies are put at risk. Modern technological means of communication and information technology allow for prospective terrorist individuals to connect with each other at unlimited level, whereas no previous time boundaries and distances restrict them. Director of National Intelligence ames Clapper admitted to the ever-growing concern for an increase in number of advanced cyber attacks within the following years. If, in 2011, the issue was among the last addressed, cyber threats moved ahead of the list a year later when it was acknowledged that ?we currently face a cyber…...
mla James R. Clapper, op. cit., p. 6. James R. Clapper, ibid., p. 18. Idem,, "Statement for the Record on the Worldwide Threat Assessment on the U.S. Intelligence Community for the House Permanent Select Committee on Intelligence" (Assessment of threats presented to the House Permanent Select Committee, February 10, 2011), p. 32.
Terrorism 4 Different Topics 3
Rational choices are limited in this setting, and may merely consist of making the best of the worst available alternatives. The American public is becoming increasingly frustrated with national policymakers who seem to be firing global broadsides but are not able to hit anything. In fact, utler even questions whether the war on terrorism is a struggle against Osama bin Laden, his Al Qaeda network, and a few similarly minded groups, or, "is it also an effort to undermine the paradigm that anything goes in the name of a cause and the idea that even the slaughter of civilians is an acceptable political act? 3. Predict the most important trends in terrorism. Clearly, things are going to get worse before they get better. Today militant Islam is gaining power and influence around the world. The relentless increase in the destructive capacity of small groups and individuals has been fueled in large party…...
mla Bibliography Butler, Paul. (2002). Foreword: Terrorism and Utilitarianism Lessons from, and for, Criminal Law. Journal of Criminal Law and Criminology, Vol. 93, Issue 1, p. 1. Cetron, Marvin J. & Owen Davies. (March/April 2003). Trends Shaping the Future. Futurist, Vol. 37, Issue 2, p. 30. Chalk, Peter. (1998). The Response to Terrorism as a Threat to Liberal Democracy. The Australian Journal of Politics and History. Vol. 44, Issue 3, p. 373. Elnur, Ibrahim. (2003). 11 September and the Widening North-South Gap: Root Causes of Terrorism in the Global Order. Arab Studies Quarterly, Vol. 25, Issue 1-2, p. 57.
Terrorism Has Posed a Threat
As any crime, an act of terrorism can happen at any time and anywhere without anyone suspecting it. In spite of being unable to stop all terrorist acts from happening, the fight against terrorism has surely contributed to diminishing it. After the 9/11 attack in the U.S., terrorism has been taken to a whole new level, as, the whole world has been traumatized. Most people regard terrorism as one of the greatest problems that humanity has to face in the present. However, as it has been proved, terrorism, when compared to other threats that the world has to face, causes very little damage. Furthermore, the chances of one becoming involved in a terrorist act are more than insignificant. As years passed, consequent to the events from 2001, the fear of an impending terrorist act did not pass, and Americans feel just as scared as they were right after the events.…...
mla Works cited: 1. Crenshaw, Martha. (1981). The Causes of Terrorism. Comparative Politics, Vol. 13, No. 4 (Jul., 1981), pp. 379-399. 2. Mueller, John. (2007). REACTING TO TERRORISM: PROBABILITIES, CONSEQUENCES, AND THE PERSISTENCE OF FEAR. Retrieved April 29, 2009, from The Ohio State University Web site: http://polisci.osu.edu/faculty/jmueller/ISA2007T.PDF 3. Victoroff, Jeff. (2005). The Mind of the Terrorist: A Review and Critique of Psychological Approaches. The Journal of Conflict Resolution. Vol. 49, No. 1 (Feb., 2005), pp. 3-42. 4. Whittaker David J. Terrorists and Terrorism in the Contemporary World. Routledge, 2004.
Terrorism Is Not a New
Although they created considerable turmoil in Germany for over a decade, it is questionable what they actually accomplished. The Gang gradually disappeared from the scene and has not been heard from for a number of years. Their activities, however, did cause a major change in how Germany, as a nation, addressed terrorism within its borders. Because of the Gang's activities, Germany enacted some of the broadest enforcement laws available for combating terrorism. The activities of the Liberation Tigers of Tamil Eelam are much broader-based than those of the Baader-Meinhof Gang. The LTTE membership numbered in the thousands and had clearly defined mission: the establishment of homeland for the Tamils. This terrorist group has maintained itself for an extended period of time and, despite being no closer to accomplishing its goals now than it was thirty years ago still maintains its activities. The LTTE marked a new era in terrorism by…...
mla References Alex, P.S. (2010). Frameworks for Conceptualizing Terrorism. Terrorism and Political Violence, 197-221. Aust, S. (1987). The Baader-Meinhoff Group: The inside story of a phenomenon. London: Bodley Head. Combs, C. (1997). Terrorism in the Twenty-First Century. Upper Saddle River, NJ: Prentice-Hall, Inc. Manoj, J. (1996). On the Razor's Edge: The liberation tigers of Tamil Eelam. Studies in Conflict & Terrorism, 19-42.
I am looking for papers on interagency information sharing as it relates to terrorism?
What was operation anaconda.
Operation Anaconda was, at the time, the largest combat operation in Afghanistan as part of the War on Terrorism that was declared after the 9-11 attacks on the World Trade Center and the Pentagon. It was launched on March 2, 2002. Major General F.L. Hagenback, the commander of the U.S. Army 10 th Mountain Division, was responsible for leading an offensive attack on al-Qaeda and Taliban forces that were located in the Shahi-Kot Valley/ Arma Mountain region near Zormat in Afghanistan. It was the first major battle after the Battle of Tora Bora and was the first battle to feature American....
What is the affiliations of domestic and transnational terrorism?
We would start this essay by looking at the Department of State’s list of Foreign Terrorist Organizations . Looking at that list is a great way to identify transnational terrorist groups. Working from those groups, you could the identify a transnational group that is linked to a domestic terrorist group. The County Reports on Terrorism also reveal how international terrorist groups work and can provide some insight into their ties to domestic organizations. Working this way may be important for the integrity of your research because the designation of groups as domestic terrorist groups changed....
Could someone kindly recommend me a topic for my A-levels global perspective essay?
The term global perspective actually has a few different meanings, depending on the discipline. It can refer to an individual’s personal lens and how they view the globe; to various perspectives about an issue from around the globe; and to views linked to globalization and the impact of individual or nation-wide actions on the world and its inhabitants. We are going to provide a range of topic suggestions that incorporate all of these different definitions of global perspectives, with the most suggestions coming from the last topic, as it is the most commonly used across academic disciplines.
A-levels....
Sign Up for Unlimited Study Help
Our semester plans gives you unlimited, unrestricted access to our entire library of resources —writing tools, guides, example essays, tutorials, class notes, and more.

Politics and Terrorism Research Paper

View sample political science research paper on politics and terrorism. Browse other research paper examples for more inspiration. If you need a thorough research paper written according to all the academic standards, you can always turn to our experienced writers for help. This is how your paper can get an A! Feel free to contact our writing service for professional assistance. We offer high-quality assignments for reasonable rates.
I. Introduction
Academic writing, editing, proofreading, and problem solving services, get 10% off with 24start discount code, ii. defining terrorism: a distinct form of political violence, a. a historical review of the terminology, b. developing an explicit definition, iii. historical examples of terrorism, a. al qaeda and the september 11 attacks, iv. historical patterns, v. theoretical and empirical contributions to the study of terrorism, a. the causes of terrorism, 1. individual and group motivations, 2. structural causes of terrorism, b. the effects of terrorism, 1. the economic effects of terrorism, 2. the consequences of suicide attacks, vi. conclusion.
Since September 11, 2001, considerable attention has been devoted to the study of terrorism, yet scholarly analysis of the subject has actually been active for several decades. With this increased focus, confusion has arisen as to the very meaning of terrorism. In addition, there are competing theories in regard to the causes and effects of terrorism, with contributions coming from economists, sociologists, psychologists, and political scientists. The study of terrorism is truly a multidisciplinary endeavor. This research paper provides a review of the debate regarding the definition of terrorism, presents historical examples of terrorism to provide context, and introduces the primary theoretical and empirical contributions of major scholars in the field.
The term terrorism, like globalism, is difficult to define and has a diversity of meanings among different groups and individuals. As a common cliché says, “One man’s terrorist is another man’s freedom fighter.” The shifting contexts in which the term is used make it difficult, but not impossible, to study the phenomenon as a distinct form of political violence. For the purposes of empirical analysis, terrorism must be defined explicitly. This research paper offers such a definition, while acknowledging that it may differ from that of other scholars, cultures, governments, media outlets, and perhaps the reader. It is useful to examine first the evolution of the usage of the term throughout history. Although examples of terrorism stretch back several millennia, the word terrorism is relatively new to the world stage.
The first usage of “terrorism” was in reference to the actions of a nation, not a subnational group. After the French Revolution in the late 18th century, the victors conducted a brutal campaign against nobles perceived to be enemies of the newly formed state. The series of mass executions by the postrevolutionary government was referred to as the terror. This early conceptualization differs from the more modern use of terrorism, in which the perpetrators are not usually governments and are instead nonstate actors (Laqueur, 2001). The usage of terrorism to refer to the violent actions of nonstate actors arose in response to the bombings and assassinations conducted by radical members of political movements such as anarchism and revolutionary socialism in the late 1800s and early 1900s. During the 20th century, the use of the term expanded immensely, often to include any type of political violence that the observer found to be disagreeable. This is where the murkiness of terrorism’s meaning arises. Politicians and the media are quick to label any enemy violence as terrorism. When any act of violence one disagrees with constitutes terrorism, the concept loses its meaning as it has become highly contextual and subjective. This is why we see certain acts of violence covered as terrorism by certain media outlets and as legitimate resistance by others. The atmosphere of confusion is not helped by the fact that, between governments and researchers, there are more than 100 different working definitions of terrorism. In addition to these observations, Jenkins (1974) pointed out the relativistic nature of the term when he wrote that terrorism seems to mean simply whatever the “bad” guys are doing. Merari (1993) echoed this when he noted that the term had become more of a derogatory epithet than an adjective describing a unique phenomenon.
If terrorism is simply a subjective catchall term for many types of political violence, why then is it given so much attention? The answer is that, although the expression can be carelessly or intentionally misused by political figures and media outlets, there is a general consensus among scholarly researchers that terrorism is a distinct form of violence, different from riots, coups, inter- and intrastate warfare, and so forth. Tilly (2004) contended that the definition should be based on characteristics of perpetrators and victims. That is certainly a good starting point.
First, an examination of the nature of the victims is in order. By far, this is the most controversial definitional aspect of terrorism. Take, for example, the 1983 suicide bombing of a United States marine barracks in Lebanon by the militant group Hezbollah. The strike occurred after U.S. troops were sent in to mediate an increasingly violent civil war, and well over 200 soldiers were killed. The attack is almost universally referred to as terrorism, but this is problematic. The victims in this case were armed security personnel stationed in a war zone. If every surprise attack on active armed forces is considered terrorism, there is little to distinguish terrorism from unexpected attacks that occur in conventional warfare. Hence, many scholars believe that terrorism involves violence directed at civilians. That is to say, the victims of terrorism are not actively or officially involved in a violent conflict.
Second, it is important to distinguish the characteristics of the perpetrators of terrorism. History is replete with examples of nation-states targeting civilians, whether their own citizens or individuals in other countries. Traditionally, though, such actions are referred to as state terror or war crimes. More often, those designated as terrorists are members of subnational groups, meaning they do not have the characteristics of a modern state, such as holding a monopoly on the legitimate use if violence in keeping with the classic Weberian definition in an internationally recognized, geographically defined territory or fielding a conventionally equipped army and navy. Examples of such nonstate actors include transnational groups such as al Qaeda or regionally based rebel groups such as the Basque separatists Euskadi Ta Askatasuna (ETA) in Spain. It follows, then, that another criterion for a violent act to be considered terrorism is that it be committed by nonstate actors. Note that excluding state terror or war crimes from falling under the rubric of terrorism does not pass a moral judgment regarding the reprehensibility of such acts. In fact, the goal of this section of the research paper is to arrive at a definition that is as free from subjective moral, or “normative,” conditionality as possible. Discarding some of the emotional and moral baggage that accompanies the loaded term will allow us to arrive at a more analytically useful conceptualization.
Beyond the nature of the attacker and the victims, it is important to analyze motivations behind terrorist acts. If we were to stop with the definition we have now, any violent crime committed by one civilian against another would be considered terrorism. However, there appears to be something qualitatively different that distinguishes the violent crimes committed by individuals and groups motivated by the desire for economic gain from the violent crimes committed by terrorist organizations. For example, there appears to be a fundamental difference between violent groups such as Hamas in the Palestinian territories and violent groups such as the Sicilian Mafia in southern Italy. Both are nonstate actors that use violence against members of a civilian population, but the distinction lies in the goals of the organizations. Hamas desires to destroy the Israeli state and claims to fight for a Palestinian homeland—a political goal. Organized crime outfits such as the Mafia have no such political intentions. They may have political connections in the form of corruption and bribery, but their aspirations essentially revolve around making money. Groups that use terrorism have political goals that extend beyond the immediate consequences of an attack. In other words, they seek to effect political change by committing violent acts against civilians. Political change can take a variety of forms. For example, terrorism can be used with the aim of changing or gaining policy concessions from a particular government or of destabilizing that government altogether. It can also be used to gain domestic support from an aggrieved group by demonstrating a willingness to fight for a cause. Thus, a final condition for a violent act to qualify as terrorism is that it be motivated by a desire to influence a political outcome. This is not to say that those who use terrorism cannot also engage in organized crime (the Taliban in Afghanistan and the Fuerzas armadas revolucionarias de Colombia, [Revolutionary Armed Forces of Colombia; FARC] turn huge profits by trafficking in narcotics), but their goals are primarily political in nature. This last condition excludes several other types of violence. For example, hate crimes without any known motivation beyond the immediate act would not be considered terrorism. Violent crimes committed by the mentally disabled, such as the attempted assassination of President Ronald Reagan by John Hinckley, also do not have an ultimate political motive and would not fall under terrorism.
Therefore, the working definition of terrorism developed in this research paper is as follows:
Terrorism is the use of violence against civilians and is perpetrated by nonstate actors with the intent of achieving some political outcome.
This definition is by no means the authoritative final word, and there remain several gray areas. Some terrorist groups have skillfully stretched the meaning of combat ants to apply to virtually every citizen of the state that they oppose. Below are some alternate definitions illustrating the fact that, even within the U.S. government, competing definitions exist:
Terrorism is the use of force or violence against persons or property in violation of the criminal laws of the United States for purposes of intimidation, coercion, or ransom. (U.S. Federal Emergency Management Agency, 2009, para.1) [Terrorism is] premeditated, politically motivated violence perpetrated against noncombatant targets by subnational groups or clandestine agents, usually intended to influence an audience. (U.S. State Department, 2001)
Terrorism can be practiced alongside other modes of violence. For example, a rebel group can choose to use hit-and-run attacks against military targets while also conducting strikes against a civilian population. In such a case, terrorism is one component of the group’s overall strategy of warfare. It can be expanded, put on hold, or altered according to the decisions of the group’s leader or leaders. This occurred in the case of the African National Congress (ANC), which used terrorism in its fight against the South African apartheid-era government. When the apartheid government finally collapsed and the ANC took over the reins of power, it no longer conducted terrorist attacks. As a result of such examples, terrorism is treated in this research paper as a tactic that can be used strategically. Repugnant though it may be, terrorism is a method for achieving an objective, and terrorist groups may more accurately be considered to be groups that use the tactic of terrorism.
The works of Enders and Sandler (2006), Laqueur (2001), Hoffman (1998), and White (1998) together provide a fascinating account of the history of terrorism. Although the term is relatively new, there are many historical examples of nonstate actors using violence against civilians with the broader goal of influencing a political outcome. One of the famous early examples was that of the Sicarii. The group’s name derives from its preference for using sica, or long knives, when attacking its targets. During the middle of the 1st century, Palestine was occupied by the Roman Empire. A rebellious Jewish group known as Zealots chafed under Roman rule and actively agitated for the removal of the Roman regime. Within the Zealots, a more radical sect existed, the Sicarii, who felt that violent overthrow was the most appropriate course of action. The strategy of the Sicarii was what would become a classic element of terrorist violence: to provoke a government (in this case, that of Rome) into an overreaction that would, in turn, drive more supporters (in this case, fellow Jews in Palestine) toward the terrorists’ cause. The Sicarii embarked on a campaign of assassinations directed against Roman officials and fellow Jews deemed to be collaborators. Historical reports indicate that the Sicarii assassinated their victims in broad daylight and among crowds of people to maximize the dramatic effect. The group also attacked infrastructure, damaging the water supply and destroying agricultural and financial targets.
Operating from the 11th to the 13th centuries in Persia and Syria, a group known as the Assassins was a violent splinter group from the Ismaili religious sect. The Assassins were a small group motivated by a desire to protect their religious practices from repression by rival factions, and they held sacred the act of eliminating their victims with daggers. Because of the limited manpower of the Assassins, their leader realized they could not confront the government head-on and instead opted for a sustained campaign of assassinations. Among their most prominent victims were high officials of government, including the king of Jerusalem. The premium that the Assassins placed on dying for their cause, which they believed to be an act of martyrdom, would be echoed by religious extremists in far more recent times.
Religious fanaticism and radical separatism are not the only motivating ideology among groups that used terrorism in history. In the mid-19th and early-20th centuries, a political movement known as anarchism became popular in Europe and North America. The ideology advocated the dissolution of all forms of government, deeming them inherently exploitative and unjust. Some anarchists rejected the more traditional means of political expression, such as protests and the dissemination of propaganda through pamphlets. Rather, they advocated what has been called “propaganda by deed.” Using violent action to demonstrate by example is a thematic element found among practitioners of terrorism. Violent anarchists in France, Italy, Britain, and the United States were not coherently organized groups, and their targets and methods differed. In Italy and France, there were several high-profile assassinations of government officials and merchants deemed to be part of the corrupt state apparatus. The technological advances that have occurred since the Assassins now allow for a new type of terrorism that has become emblematic of the modern era: the use of bombs. Dynamite was a weapon of choice among violent French and American anarchists, and the use of explosives in terror attacks has been adopted by an ever-widening array of groups in the last two centuries.
The systematic campaign of violence and intimidation directed toward Blacks and moderate Whites in the United States by the Ku Klux Klan (KKK) is an infamous example of domestic, “homegrown” terrorism. The KKK was devoted to preserving the traditional dominance of Whites in the U.S. South, and this vision entailed violent actions designed to forcibly dissuade Blacks from participating in the political process. A ritualistic right-wing organization, the KKK was indelibly known for its practice of wearing white hoods and its pseudoreligious practice of burning crosses. KKK activities included a series of extrajudicial (outside the law) executions known as lynchings. The KKK used lynchings and other forms of violence to murder numerous individuals throughout the 19th and 20th centuries. In the 1960s, the KKK caused an international uproar when it planted a bomb in the basement of the 16th Street Baptist Church in Birmingham, Alabama. The resultant explosion killed four young girls and served to galvanize the civil rights movement that was emerging in the United States (National Public Radio, 2003).
Terrorism was a central strategy for gaining power within several political movements during the 20th century. Communist revolutionaries were among several groups using terrorism to agitate against czarist rule in Russia in the 1900s. By the time they achieved power in a 1917 coup, they had conducted three major campaigns of assassination against political enemies. The fascist Nazi party also used terrorism in its ultimately successful attempt to gain control over the German government prior to World War II. Thus, two of the most historically significant political movements of the 20th century, fascism and communism, made use of terrorism to successfully transition from being challengers of governments to becoming the governments themselves.
The post–World War II era heralded several new developments that came to characterize modern terrorism. First, the growing popularity and availability of commercial air flight presented new opportunities for groups aiming to conduct terrorist attacks. During the 1960s and 1970s, skyjacking was used effectively and often. In these hostage-taking situations, aircrafts were forcibly commandeered in flight or on the ground, and political demands were made by the hijackers. Defensive countermeasures taken, such as the installation of metal detectors at airports, helped to greatly reduce the number of terrorist hijackings in the 1980s and 1990s. Second, the 1980s saw the advent of suicide bombing, first used by the Lebanese group Hezbollah and refined by the Liberation Tigers of Tamil Elam (LTTE) separatists in their fight for an autonomous homeland separate from the Sri Lankan government.
Following the September 11, 2001, attacks, the U.S. government tasked the National Commission on Terrorist Attacks Upon the United States to create a comprehensive account. The Commission produced the Complete 9/11 Commission Report (2004), which is a massive and freely available online resource that is easy to read and highly recommended for students interested in a more thorough accounting of the attacks. The following account is primarily derived from the Complete 9/11 Commission Report.
In 1978, the Soviet Union invaded the Central Asian nation of Afghanistan. A rugged geographic region characterized by a tribal society, Afghanistan was home to several million Muslims of differing ethnic backgrounds. The possibility of an atheistic Communist regime occupying a Muslim nation proved to be an incendiary prospect for many Muslims across the world. It also presented an opportunity for governments in the Middle East, such as Saudi Arabia and Pakistan, to export young radicals to fight the Soviet occupation. In doing so, these governments gained stature as defenders of the Muslim faith while also relieving themselves of the internal security threat these radicals represented. The United States, Soviet Russia’s primary cold war enemy, also provided funding for some of the groups battling the Soviets. These groups were by no means uniform in their methods and motivations, and after their victory over the Soviets in 1989, they proceeded to battle among themselves, plunging Afghanistan into another decade of statelessness and civil war. One of the many foreigners who traveled to Afghanistan to fight against the Soviets was Osama bin Laden, the son of an immensely wealthy Saudi Arabian construction magnate. After the Soviets left Afghanistan, bin Laden was instrumental in maintaining a cadre of followers that eventually became known as al Qaeda.
Bin Laden was largely the financier of al Qaeda, and his deputy, Egyptian physician Ayman al-Zawahiri, headed up operational control of the organization. Espousing a radical version of Sunni Islam and inspired by the Muslim Brotherhood, the al Qaeda leadership was determined to battle any party it perceived to be hostile toward its austere version of Islam. Bin Laden blamed the suffering of fellow Muslims on corrupt Middle Eastern regimes, whom he perceived to have betrayed the faith, and the actions of Western governments, particularly the United States. When Iraq invaded Kuwait in 1991, the neighboring Saudi regime became concerned that it was Saddam Hussein’s next target. Bin Laden offered the protective services of his fighters, but the Saudis, wary of importing the same figures that helped topple the Soviets, instead opted for protection from the United States, allowing U.S. military forces to use Saudi territory as a launching pad for the first Gulf War. The prospect of foreign troops on Saudi soil (home to the two most holy sites in Islam: Mecca and Medina) proved to be intolerable to al Qaeda. The organization also held grievances against the United States for the country’s support of Israel and other Middle Eastern governments that al Qaeda held a deep enmity toward. Thus, the United States became a primary target of the organization.
In 1998, bin Laden and al-Zawahiri held a news conference to announce the issuance of a religious edict. In it, they claimed it was the duty of every observant Muslim to attack Americans whenever and wherever possible. Soon afterward, bin Laden clarified that the group made no distinction between American troops and civilians, reasoning that civilians in a democratic society were directly responsible for the policies of a government they voted for. Several terrorist attacks attributable to al Qaeda had already occurred by the time the 1998 edict was issued, but none at that point had been as large as the two simultaneous vehicular bombings of U.S. embassies in Sudan and Kenya that followed that summer. The bombings killed hundreds of civilians, mostly Muslim East Africans. This irony did not go unnoticed by al Qaeda, which, hoping to be the vanguard for disaffected Muslims throughout the world, had already embarked on more ambitious plans to attack Americans directly.
Some time that same year, bin Laden purportedly gave approval for the September 11, 2001, attacks. The operational planning for this task was largely delegated to a man known as Khalid Sheikh Mohammed. Born in Kuwait and college educated in the United States, Khalid Sheikh Mohammed reportedly claimed to have gotten the idea for a plane attack on the World Trade Center (WTC) after his nephew’s 1993 attempt to destroy the towers with a vehicle bomb failed. Throughout 1999, the plan progressed as candidates for the operation were recruited, trained in Afghanistan, and secured visas for entry into the United States. While in the United States in 2000 and 2001, the hijackers attempted to blend in as visiting students, and select members attended flight training school.
By 2001, the U.S. government had indications that al Qaeda was planning a massive attack on the homeland, but the government was unable to connect the bits and pieces of intelligence, spread across several governmental agencies, into a coherent enough picture to stop the plot before its execution. The nature of the attack was also unexpected because there had never been one like it before. There had been suicide bombings in other countries, but no one had ever combined suicide attacks with airline hijacking. The conventional model of hijacking and hostage negotiation was not part of the plan, and few, if any, predicted that entire commercial airliners could be taken over and commandeered with items as seemingly innocuous as box cutters. Thus, most of the world was shocked when 19 men hijacked four planes on September 11, crashing three of the planes into their intended targets—the WTC towers and the Pentagon—while the fourth was brought down in a Pennsylvania field when the passengers fought to retake control of the aircraft. The attacks resulted in the destruction of the WTC towers and part of the Pentagon, with more than 3,000 civilians murdered. The size and scope of the operation are without parallel.
A few patterns emerge in this brief, and by no means exhaustive, historical review of the occurrence of terrorism. These patterns have guided much of the research in academia. First, groups that employ terrorism come from a variety of ideological backgrounds. Some, like the Assassins, were religiously motivated. Others were devoted to a left or right wing political cause, such as the anarchists or the KKK. Groups such as the LTTE aimed to carve out a piece of territory for their ethnic kin. These motivations are not mutually exclusive. For example, the Sicarii were a religiously motivated group that also sought an element of territorial control. The primary lesson to draw is that no one extreme political or religious ideology dominates the use of terrorism. The backgrounds and motivations of these organizations are highly diverse, and attempting to uncover a single, overarching ideology among them all is a fruitless endeavor. Second, a similar amount of diversity is found across time and geographic region. Although the methods of implementation have shifted with technology, terrorism is not a new phenomenon, and it is not restricted to one region of the world. Third, all the previously mentioned groups, at least initially, lacked the size and ability to field regular armies that could mount a direct challenge to governmental authorities. This makes sense because, by definition, groups that use the tactic of terrorism are nonstate actors. However, some movements have grown large enough to challenge authorities by more conventional military means, being able to simultaneously pursue guerrilla campaigns or fight traditional battles while also conducting terrorist strikes. Last, the attacks conducted by various terrorists were intended to provoke a response, whether from the element of society they were challenging, the societal groups they claimed to be fighting for, or both.
Terrorism studies, as a subfield of political science, are a relatively new endeavor. They do not have the level of development we find in other arenas of political science, such as the study of interstate war or internal revolutions. Despite that, there have been some major developments in the field during the past three decades. This portion of the research paper analyzes some of the seminal works on terrorism and reports some of the critical empirical conclusions from this area of study.
As is often the case with the study of some unique social phenomenon, the first efforts were primarily aimed at explaining its causes. There is also much to be learned from the effects of terrorism, but understanding the origins of terror is of primary importance. Jenkins (1974) produced an analysis for the U.S. Congress that contained considerable insight into the nature of terrorism. Jenkins forcefully argued against the perception that terrorism was the work of senseless, mindless, and irrational actors. Attacks on civilian targets shock the conscience, and the seemingly random, chaotic carnage that is produced by terrorism understandably gives the impression to many that it is the work of insane individuals. This impression may even be intentionally cultivated by terrorist practitioners themselves, and the media also play a role in casting terrorists as lunatics, but the evidence belies this assumption. Jenkins’s work noted that practitioners of terrorism had concrete political goals and did not simply engage in violence for the sake of violence in the way that sociopathic criminals might. Rather, because terrorist groups often lack the resources to mount a direct challenge to government security forces, they shift their focus to “softer,” less fortified targets, such as civilians. The often indiscriminant nature of attacks on civilians garners the most attention, so while the purpose of a more conventional military operation may be to take and hold a piece of territory, the terrorist attack is designed to influence an audience beyond that of the immediate victims. Often the goal is to create a climate of panic and to expose a government’s inability to prevent such indiscriminate violence. Because of these unconventional goals, Jenkins cast terrorism as a form of political “theater” in which the harm suffered by the immediate victims of terrorism is of secondary importance to the group conducting the attack. Take, for example, the September 11, 2001, attacks. The perpetrators chose targets that were steeped in symbolism. The Pentagon and the WTC were prominent symbols of American financial and military might, readily recognizable as such by both American citizens and the worldwide audience that witnessed the attacks. The attacks sent a message that the citizens and institutions within the United States mainland were not safe, and the atmosphere of fear following the attacks was palpable. The name Osama bin Laden gained universal recognition, while al Qaeda became the object of unceasing media attention. Yet despite the disastrously large death toll, the average American citizen’s chance of being harmed in such an attack remained infinitesimally small. For the average person, the chance of being felled by a heart attack or car accident was far greater than that of being struck down by al Qaeda, yet terrorism became the central issue for several election cycles following the attack. These facts give credence to Jenkins’s argument that terrorism is theater: a spectacle designed to attract maximum attention and create massive emotional impact. It became clear that one of the reasons terrorism occurs is the massive amount of attention it can attract without being cost prohibitive for small organizations.
Crenshaw (1981) was one of the earliest political scientists to conduct research on terrorism. She concluded that terrorism was not necessarily the result of broad public dissatisfaction with the political order or evidence of a fractious society. Rather, Crenshaw contended, terrorism was often the result of the grievances of a disaffected group that had originated in the elite and claimed to fight for a larger group. This conclusion was reasonable given the makeup of left-wing terrorist groups that had dominated the news in the previous two decades. While claiming to fight for the downtrodden worker, groups such as the Red Army Faction in Germany were largely composed of students from upper- or middle-class origins. Their parents were academics, clergy, writers, and other professionals, yet the students became disaffected and alienated from the societies that spawned them. Crenshaw believed that psychological factors such as guilt, desire for vengeance, and a thirst for excitement were the primary motivations of individuals who participated in terrorism.
The idea of a rational terrorist has very real policy implications for counterterrorism officials. If an enemy is mentally deranged, irrationally lashing out at random targets, there is little use in trying to predict when, where, and how that enemy will strike. However, if an enemy is calculating, weighing the costs and benefits of conducting an attack, policymakers and analysts are more likely to be able to get an idea of what targets the enemy will select and how it will attack them. It is no surprise, then, that many researchers take the rational choice approach when modeling terrorism. In this research strategy, the choice of whether to participate in terrorism is contingent on the cost–benefit ratio for the principal actor, the terrorist. Scenarios are often presented as a game wherein an actor takes a turn, choosing whether to use terrorism, and another actor, usually representing a government or counterterrorist agency, must choose a response while considering that the terrorist opponent will be trying to predict the agency’s strategy (Lake, 2002). The key, then, is determining what particular conditions create a payoff structure for potential terrorists sufficient to entice them to commit the violence despite knowing what the counter-response will be. More simply put: What conditions cause terrorism to be worthwhile to certain groups and individuals despite the risk? The following section describes various theories regarding those conditions. Attributing thought and rationality to terrorism is controversial as many are reluctant to admit any quality but insanity to such a reprehensible form of violence, but the idea of the strategic terrorist is one of the dominant themes in academic research on the matter.
However, the rational choice approach has been criticized as unrealistic. Individual interviews of terrorists have often revealed no such cost–benefit analysis among the terrorists that were studied. Sometimes the choice to participate is based on a desire for revenge rather than a sober calculation of the possible costs and payoffs. One failed suicide bomber noted his spiritual motivations for engaging in terrorism, an inspiration that is not easily modeled by rational choice (Hassan, 2001). Perhaps the only blanket statement that can be made about the “average terrorist” is that he or she is willing to undertake extreme risk. That said, different motivating factors may drive the foot soldiers of terrorist groups and their leaders. It seems more reasonable to expect that the leaders of groups that utilize terrorism do look at the “big picture” and consider the benefits and risks of various oppositional strategies.
Rather than focus on the individual psychological calculations of the individual terrorist, some researchers have put forth causal arguments based on the institutional and structural features of a society. One such argument revolves around the supposed connection between poverty and terrorism.
In both the literature and the culture at large, there is an expectation of a causal relationship between poverty and terrorism. Following September 11, 2001, politicians such as former Vice President Al Gore and President George W. Bush argued that combating terrorism should involve efforts to eradicate poverty and increase education in the world’s troubled hot spots. Academics too have prescribed the lifting of living standards in various regions in the hope of creating a disincentive for participation in terrorist activities. There is good reason to think that certain socioeconomic factors are determinants of terrorism. The lack of economic and educational opportunities has already been empirically linked to a variety of other problems, such as property crime, the occurrence of civil war, and instability within new democracies. The general theory is that poverty and a lack of opportunity increase the level of grievances among economically marginalized members of society and that a subset of an aggrieved population may choose to express its discontent violently by way of terrorism. However, the actual evidence of a connection between poverty and terrorism is mixed at best. Counterfactual examples include of the finding that many of the perpetrators of the September 11, 2001, suicide attacks came from educated, middle-class backgrounds. A profile of failed Palestinian suicide bombers in The New Yorker returned the same results (Hassan, 2001). Most of the young men interviewed had held jobs, were educated, and did not come from extreme poverty. On the other side of the Israeli–Palestinian conflict, an analysis of the Israeli Jewish Underground, an organization that attacked Palestinian civilians during the 1970s and 1980s, also found that a strong majority of members were highly educated and held prominent occupational positions. There is the possibility that although poverty or lack of educational opportunities is not prevalent among the practitioners of terrorism, it may be that poor socioeconomic conditions experienced by their ethnic or religious kin inspire a so-called Robin Hood model of terrorist activity. If this were the case, it would be more appropriate to analyze aggregated societal or country-level indicators of economic and educational conditions than the individual socioeconomic origins of the terrorists themselves. The empirical evidence does not conform to the conventional wisdom on that level of analysis, either. For example, a survey in the Palestinian territories found that unemployment actually reduced support for terrorism against the Israelis. Another study found that, after controlling for civil liberties (on account of the fact that poorer countries are more likely to have fewer political freedoms), there is no statistically significant difference between poor and rich countries in terms of the number of terrorists that they spawn (Krueger & Maleckova, 2003).
The rational choice approach is particularly helpful in examining the strategic expectations that terrorist practitioners have for the consequences of their acts. Specifically, there is evidence that terrorism is used to goad an overreaction from the target government or societal group (Bueno de Mesquita & Dickson, 2007; Lake, 2002). This strategy appeared to be in play among jihadist elements of the Sunni insurgency in Iraq.
Following the 2003 invasion by the United States, Iraq experienced an influx of religiously motivated fighters from neighboring Muslim countries (quite similar to the influx of fighters into Afghanistan in response to the Soviet invasion), who claimed to battle on behalf of the minority Sunni population. The Sunnis had held a position of privilege over their Shi‘a counterparts during the rule of Saddam Hussein and were now facing the possibility of losing that status. These fighters, along with indigenous radical Iraqi Sunnis, formed the backbone of what would be known as al Qaeda of Mesopotamia. This regional al Qaeda franchise embarked on a series of gruesome executions and suicide bombings directed at the majority Shi‘a population, killing scores of civilians. While some Shi‘a leaders counseled restraint in the face of such attacks, the Shi’a population evinced a growing inclination toward self-protection and revenge. By the time al Qaeda of Mesopotamia blew up the Golden Mosque, one of Shi‘a Islam’s holiest shrines, reprisal killings directed at Sunni civilians were well under way by Shi‘a militants. In the following months, the country of Iraq descended into a vicious period of civil conflict, with spasms of indiscriminant killing on both sides (Frontline, 2007).
There is a coherent logic in attempting to spark a wider conflict through the use of terrorism. In provoking a disproportionate response by using terrorism, radical groups are able to pressure or shame moderate members of their community into supporting a violent approach. An extremist group without a large base of support can use as a recruitment tool the overreaction that they have intentionally caused. The Iraqi example was largely one of a disproportionate response from nonstate actors from one element of society directed at nonstate actors from another, but there are also examples of groups using terrorism to cause a government to overreact. The end result is the same: A disproportionate government response can radicalize previously fence-sitting moderates and drive them to support the extremists in their midst. Several rational choice studies have explicitly identified the causal link between overreaction and its effect of provoking further violence (Bueno de Mesquita & Dickson, 2007; Mason & Krane, 1989). Specifically, governments and subnational groups seeking to respond to a terrorist attack often suffer from an information problem. Because of the secretive nature of terrorist organizations, it is exceedingly difficult to identify the specific perpetrators and punish only them. Often, the counterattack response to terrorism is indiscriminate, harming people who had no connection with the original terrorist activity. This was certainly the case in Iraq, where simply having a Sunni-sounding last name was often enough to warrant execution by Shi‘a militia members. Imagine, then, how the calculated expectation of the risk of participating in violence changes for an individual in the face of indiscriminant violence. Beforehand, the level of risk derived from joining a violent organization exceeded the potential payoff gained by simply sitting on the sidelines and waiting the conflict out. In the face of indiscriminant violence, where one is equally likely to be harmed regardless of whether he or she had previously participated in violent activity, it becomes less risky to join a violent organization. In fact, it may appear to be in an individual’s best interest to join such a group because at least the individual is offered an element of protection by doing so. It is no surprise, then, that from the Sicarii to al Qaeda in Mesopotamia, terrorism has been strategically employed to foment higher levels of violence and gain supporters.
Assessing the economic impact of terrorism has proven to be one of the most quantitatively rigorous areas in the field of terrorism studies. Economic damage has been an implicit or explicit motive behind several terrorist movements. Osama bin Laden drew lessons from the economic toll inflicted on the Soviet Union during its invasion and occupation of Afghanistan and advised his followers to conduct strikes on Middle Eastern oil facilities in hopes of causing similar economic pain on the energy-reliant Western nations (Associated Press, 2004). Based on the logic that violence will reduce an important source of revenue for the target government, many high-profile attacks are conducted at popular tourist destinations. Indeed, an economic analysis by Enders and Sandler (1991) of terrorist attacks in Spain found that the average attack caused the number of tourists visiting the nation to decrease by approximately 140,000 people in a year. A similar investigation of terror attacks in Italy determined that a typical strike resulted in a shock to the level of tourism that took a full year to dissipate (Enders, Sandler, & Parise, 1992). Beyond affecting specific industries, terrorism appears to have macroeconomic consequences as well. It is interesting that, although terrorist attacks appear to have only a temporary, and small, negative impact on the gross domestic product of nations, a more significant and positive relationship exists between terrorism and government spending (Blomberg, Hess, & Orphanides, 2004). While the goal of an attack may be to cause economic harm by bleeding a government, an ironic consequence is that governments respond to an attack by investing in counterterrorist measures that require matériel and personnel, thus mitigating some of the economic damage caused by the strike.
Scholarly analysis has demonstrated that suicide bombing, although horrific and repugnant, can produce tangible benefits for groups seeking political change through violence. Sprinzak (2000) noted that suicide bombing is one of the most psychologically effective methods because it communicates the message that there is no deterrent that can dissuade the attacker. Before the popularization of suicide bombing by groups such as Hezbollah in Lebanon and the Tamil Tigers in Sri Lanka during the 1980s, it was largely, and erroneously, assumed that, although willing to engage in extreme risk-taking behavior, even terrorist practitioners put a certain premium on their own lives. However, as studies by Sprinzak and a highly influential piece by Pape (2003) observed, what may seem irrational on an individual level may be quite logical at the group level. That is, terrorist groups may benefit from the use of individual members to conduct suicide attacks, whereas the individual conducting the attack may not.
In addition to the psychological impact suicide terrorism causes, the tactic offers several advantages for groups willing to engage in extreme violence. First, in terms of material cost, suicide terrorism is cheap. The amount of explosive needed to rig a human bomb is small, and the monetary costs for acquiring the components are minimal to the group. Second, the operational complexity of planning a suicide attack is greatly reduced when there is no need for an exit strategy for the attacker. Third, the suicide attack is, on average, more deadly than any other form of terrorism. Pape’s most controversial argument concerned the effect of suicide attacks. He argued that the reason suicide attacks increased in popularity is that terrorist groups observed that they were successful in gaining territorial concessions from democratic states. For example, Hezbollah successfully drove the U.S. Marines and French paratroopers out of Lebanon following two massive suicide bombings. The use of suicide terrorism by the LTTE coerced the Sri Lankan government into establishing an autonomous region for the ethnic Tamils in the early 1990s. Israel abandoned the Gaza Strip and West Bank in the mid- 1990s as a consequence of being targeted by suicide bombers. Pape believed that democracies are susceptible to the effects of suicide bombing because, unlike autocracies, they are accountable to a public that recoils at such attacks. The free and open media that are characteristic of a democracy are also better able to publicize attacks than are their state-controlled counterparts in autocracies.
There are some shortcomings with Pape’s work. Some of the targeted nations characterized as democracies in his analysis did not possess convincing democratic credentials. There are also cases of suicide attacks directed at decidedly authoritarian regimes, such as the Saudi monarchy. Furthermore, because of the closed nature of the media in authoritarian states, many examples of suicide bombings may have gone unreported. Ultimately, though, Pape’s argument can be extended to terrorism in general: It is popular because it sometimes works in achieving the goals of the groups that use it.
This research paper has illuminated several aspects of the form of political violence known as terrorism. The phenomenon differs from other forms of political violence. It has occurred within many different periods, regions, and cultures and has been executed under a variety of ideological auspices. The theoretical and empirical contributions of various social scientists have advanced the study of terrorism into an academic subfield with significant explanatory power.
Bibliography:
- Associated Press. (2004). Analysis: Only U.S. can damage self majorly despite Bin Laden. USA Today. http://usatoday30.usatoday.com/news/world/2004-12-18-bin-laden_x.htm
- Blomberg, S. B., Hess, G. D., & Orphanides, A. (2004). The macroeconomic consequences of terrorism. Journal of Monetary Economics, 51, 1007-1032.
- Bueno de Mesquita, E., & Dickson, E. S. (2007). The propa ganda of the deed: Terrorism, counterterrorism, and mobi lization. American Journal of Political Science, 51(2), 364-381.
- Crenshaw, M. (1981). The causes of terrorism. Comparative Politics, 13(4), 379-399.
- Enders, W., & Sandler, T. (1991). Causality between transnational terrorism and tourism: The case of Spain. Studies in Conflict & Terrorism, 14(1), 49-58.
- Enders, W., & Sandler, T. (2006). The political economy of terrorism. New York: Cambridge University Press.
- Enders, W., Sandler, T., & Parise, G. F. (1992). An econometric analysis of the impact of terrorism and tourism. Kyklo, 45, 531-554.
- Frontline. (2007). Timeline: Struggling to find a strategy for success in Iraq. https://www.pbs.org/wgbh/pages/frontline/endgame/cron/
- Hassan, N. (2001). An arsenal of believers. The New Yorker, 77(36), 36.
- Hoffman, B. (1998). Inside terrorism. New York: Columbia University Press.
- Jenkins, B. (1974). International terrorism: A new kind of war fare. The RAND Corporation. https://www.rand.org/content/dam/rand/pubs/papers/2008/P5261.pdf
- Krueger, A. B., & Maleckova, J. (2003). Education, poverty and terrorism: Is there a causal connection? Journal of Economic Perspectives, 17(4), 119-144.
- Lake, D. (2002). Rational extremism: Understanding terrorism in the 21st century. Dialog IO, 1, 263-296.
- Laqueur, W. (2001). A history of terrorism. New Brunswick, NJ: Transaction.
- Mason, T. D., & Krane, D. A. (1989). The political economy of death squads: Towards a theory of the impact of state sanctioned terror. International Studies Quarterly, 33, 175-198.
- Merari, A. (1993). Terrorism as a strategy of insurgency. Terrorism & Political Violence, 5(4), 213-251.
- National Commission on Terrorist Attacks Upon the United States. (2004). Complete 9/11 Commission Report. https://govinfo.library.unt.edu/911/report/index.htm
- National Public Radio. (2003). 16th Street Baptist Church bombing: 40 years later, Birmingham still struggles with a violent past. https://www.npr.org/templates/story/story.php?storyId=1431932?storyId=1431932
- Pape, R. A. (2003). The strategic logic of suicide terrorism. American Political Science Review, 97(3), 343-361.
- Sprinzak, E. (2000, September/October). Rational fanatics. Foreign Policy, 120, 66-73.
- Tilly, C. (2004). Terror, terrorism, terrorists. Sociological Theory, 22(1), 5-13.
- U.S. Federal Emergency Management Agency. (2009). General information about terrorism. https://www.fema.gov/pdf/areyouready/terrorism.pdf
- U.S. State Department. (2001). Glossary. https://2001-2009.state.gov/s/ct/info/c16718.htm
- White, J. R. (1998). Terrorism: An introduction. Belmont, CA: Wadsworth.
ORDER HIGH QUALITY CUSTOM PAPER

.webp)
Research Paper Topics for 2024: Explore Ideas Across Various Fields

When you start writing a research paper, it’s like diving into a big pool of exploration and analysis. A good research paper goes beyond just gathering facts. It’s more about exploring a topic, asking the right questions, and coming up with thoughtful answers. Whether you're looking at historical events, scientific discoveries, or cultural trends, the trick is to find interesting research topics that catch your interest and keep you motivated throughout the process.
This article is here to help with that sometimes tricky job of picking a topic. We’ll cover a variety of interesting research topics from different areas, making it easier for you to find one that not only fits your assignment but also grabs your attention.
But let’s be honest, picking the right topic isn’t always easy. If you’re still unsure after reading this article, EssayService is a great place to turn for help, whether you need assistance choosing a topic or writing the entire paper.
How to Pick a Topic for a Research Paper
Choosing the right topic can make or break your research paper. Here's how to make it easier:
- Start with your interests: Pick a few areas or subjects that genuinely interest you. Narrow it down to the one that excites you the most. If you’re interested, it’ll show in your writing.
- Check for resources: Before committing, do a quick search to ensure there are enough references available. You’ll want a topic that’s well-discussed so you have plenty of material to work with.
- Stick to guidelines: Make sure your topic fits within any guidelines your teacher has set. Whether it's avoiding certain subjects or meeting specific requirements, this step is crucial for getting your paper off to a good start.
If you’re looking for easy research paper topics, keep these tips in mind to ensure you choose one that’s both manageable and engaging.

What Are Good Research Topics?
Choosing a successful research topic isn’t just about what sounds interesting — it’s about finding a topic that will help you produce a strong, insightful paper. Good research topic ideas should tick a few key boxes to ensure they’re both impactful and manageable.
| Feature | Description |
|---|---|
| 🔍 Specific and Focused | Narrow down broad areas like “climate change” to something more specific, like “the impact of urban development on local microclimates.” This gives your research a clear direction. |
| ✨ Unique Angle | Instead of rehashing well-covered topics like “social media and mental health,” explore a niche, such as “the effects of social media detox on productivity in college students.” |
| 🌍 Significant Impact | Choose topics that matter, like “renewable energy adoption in developing countries,” which could contribute to important discussions in your field or society. |
| 📚 Accessible Sources | Make sure there’s enough material available by checking databases for studies on topics like “the history of vaccine development” to ensure you have the resources you need. |
| 🔥 Current and Relevant | Focus on emerging issues, such as “the role of AI in cybersecurity,” which are timely and likely to interest both readers and reviewers. |
Best Research Paper Topics for 2024
In 2024, new challenges and innovations are shaping the world around us, making it an exciting time to dive into research. Here are 15 detailed and highly relevant topics that will keep your paper ahead of the curve:
- The impact of remote work on urban development in major U.S. cities.
- Ethical implications of AI-driven decision-making in healthcare.
- The role of social media algorithms in shaping public opinion during elections.
- Effects of climate change on global food security and crop yields.
- The influence of blockchain technology on supply chain transparency.
- Mental health outcomes related to long-term social media use among teenagers.
- Renewable energy adoption in emerging economies and its impact on local communities.
- The rise of electric vehicles and its effect on traditional automotive industries.
- Privacy concerns surrounding the use of biometric data in consumer devices.
- The evolution of cybersecurity threats in the age of quantum computing.
- Gender disparities in STEM education and their long-term effects on the workforce.
- The economic impact of climate migration on coastal regions.
- Implications of CRISPR technology in human genetic modification.
- The effectiveness of universal basic income trials in reducing poverty.
- The role of telemedicine in improving access to healthcare in rural areas.
College Research Paper Topics
These topics explore some of the most relevant and intriguing issues facing college students today, offering plenty of angles to explore in your research:
- How student loan debt shapes career paths and financial stability after graduation.
- Comparing online learning to traditional classrooms: What works best for today’s college students?
- Social media’s influence on mental health and academic success among college students.
- Diversity and inclusion: How initiatives are changing campus life and student experiences.
- University sustainability efforts: How climate change is driving new campus policies.
- The rise of esports: Transforming college athletics and student engagement.
- Campus housing: How living arrangements affect academic success and student retention.
- Balancing part-time jobs with academics: The impact on college students’ grades and well-being.
- Navigating controversial topics: The importance of academic freedom in college debates.
- Digital vs. traditional libraries: How technology is reshaping student research habits.
- Study abroad programs: Enhancing global awareness and boosting future career opportunities.
- Evaluating campus mental health services: Are they meeting students’ needs?
- Fraternities and sororities: Examining their influence on college culture and student life.
- Free college tuition: Exploring the economic and social outcomes in different countries.
- Standardized testing: How it’s affecting college admissions and the diversity of student bodies.

Research Paper Topics By Subject
Choosing a good research topic that aligns with your academic focus can make your work more relevant and engaging. Below, you’ll find topics organized by subject to help you get started.
Research Paper Topics on Health
Health is a dynamic field with ongoing developments and challenges, making it a rich area for research. These topics cover a range of health-related issues, from public health policies to advancements in medical technology:
- How COVID-19 has changed the approach to mental health care.
- Adoption rates of telemedicine among different age groups.
- Antibiotic-resistant bacteria: Exploring new treatment options.
- Barriers to healthcare access in low-income neighborhoods.
- Ethical dilemmas in using genetic testing for personalized treatments.
- Success rates of mental health programs in high schools.
- Comparing dietary patterns in managing type 2 diabetes across cultures.
- Teen vaping trends and their connection to lung health issues.
- Strategies for supporting healthcare needs in rapidly aging populations.
- Tracking climate-related health issues in coastal communities.
- Innovations in vaccine development for emerging diseases.
- Social isolation during pandemics and its link to anxiety disorders.
- Recent changes in U.S. healthcare laws and their influence on patient choices.
- Exploring how traditional beliefs shape approaches to medical treatment.
- Evaluating progress in global vaccination campaigns against childhood diseases.
Research Paper Topics on Medicine
Medicine is a vast field with plenty of areas to explore. Here are some specific topics that focus on medical advancements, practices, and challenges:
- New techniques in minimally invasive surgery for heart conditions.
- Developments in gene therapy for treating inherited diseases.
- Challenges in diagnosing and treating rare diseases.
- The role of AI in improving diagnostic accuracy in radiology.
- Progress in personalized cancer treatments based on genetic profiling.
- The rise of antibiotic alternatives in treating infections.
- Stem cell research advancements for spinal cord injuries.
- Managing chronic pain: Exploring non-opioid treatment options.
- Trends in telemedicine for rural healthcare delivery.
- Breakthroughs in vaccine technology for emerging viruses.
- Long-term outcomes of organ transplants in pediatric patients.
- Advances in robotic surgery and their impact on patient recovery.
- New approaches to treating drug-resistant tuberculosis.
- Innovations in prenatal care and fetal surgery techniques.
- The future of regenerative medicine and tissue engineering.
Research Paper Topics on Media
Explore the ever-changing world of media with these fresh and relevant topics. Each one dives into the trends and challenges shaping how we consume and create content today.
- Analyze the impact of TikTok on modern marketing strategies.
- Investigate the role of influencers in shaping public opinion during elections.
- Explore the effects of streaming services on traditional cable TV viewership.
- Examine how social media platforms handle misinformation and its consequences.
- Study the rise of podcasts and their influence on news consumption.
- Compare the portrayal of mental health in TV shows across different cultures.
- Track the evolution of digital journalism and its impact on print media.
- Look into the ethics of deepfake technology in video production.
- Research the effects of binge-watching on viewer behavior and mental health.
- Explore the relationship between video game streaming and the gaming industry.
- Analyze the shift from traditional news outlets to social media for breaking news.
- Investigate how algorithms curate personalized content and influence user behavior.
- Study the changing landscape of advertising in the age of ad-blockers.
- Examine the role of memes in political discourse and cultural commentary.
- Explore the use of virtual reality in media and entertainment.
Research Paper Topics on Politics
Politics is a field that’s constantly evolving, with new issues and debates emerging all the time. Whether you're interested in global dynamics, domestic policies, or the role of technology in politics, there’s no shortage of interesting topics to explore:
- How social media is influencing voter behavior in recent elections.
- The rise and impact of grassroots movements on political change.
- Fake news and its role in shaping public perception of political events.
- The effects of immigration policies on relationships between countries.
- Populism’s growth in global politics and what it means for the future.
- How economic inequality contributes to political instability.
- The power of political lobbying in creating and shaping laws.
- Challenges faced by democracies under authoritarian regimes.
- Youth activism and its growing influence in modern politics.
- How climate change policies are impacting national security.
- The role of technology in improving election security and voter turnout.
- Government approval ratings and their connection to pandemic responses.
- Influence of international organizations on a country’s domestic policies.
- Shifts in global trade agreements and their effects on international relations.
- The impact of gerrymandering on election results and fairness.
Research Paper Ideas on Technology
Technology is rapidly transforming our world, offering endless opportunities for research. Here are some intriguing ideas to explore:
- The ethics of artificial intelligence in decision-making processes.
- How blockchain technology is revolutionizing financial transactions.
- The role of 5G networks in shaping the future of communication.
- Cybersecurity challenges in the era of smart homes and IoT devices.
- The environmental impact of cryptocurrency mining.
- Virtual reality’s influence on education and training programs.
- How autonomous vehicles are changing urban planning and infrastructure.
- The potential of quantum computing in solving complex global problems.
- Social media algorithms and their impact on public discourse.
- The digital divide: Access to technology in rural versus urban areas.
- How wearable tech is transforming personal health management.
- The implications of deepfake technology in media and politics.
- The future of remote work and its long-term effects on productivity.
- Advancements in drone technology for disaster management and rescue operations.
- The role of big data in personalizing online shopping experiences.
Research Topic Ideas on Culture
Whether you’re interested in examining specific cultural practices or looking at how modern trends reshape traditional customs, these research topics will provide you with a focused and detailed starting point:
- Adoption of traditional Japanese tea ceremonies in contemporary urban settings.
- Practices of food preservation among Inuit communities in the Arctic.
- The revival of Celtic languages in Wales and Ireland through education programs.
- Depiction of queer relationships in Netflix original series from 2015 to 2024.
- Evolution of traditional African hairstyles in Black communities across the U.S.
- Transformation of street art in Berlin post-German reunification.
- Cultural significance of Día de los Muertos celebrations in Mexican-American neighborhoods.
- Popularity of Korean skincare routines among Western beauty bloggers.
- Modern interpretations of Norse mythology in Scandinavian literature.
- Changes in wedding rituals among Indian diaspora in the UK.
- Resurgence of indigenous Australian painting techniques in contemporary art.
- Representation of disability in children’s books published in the last decade.
- Use of traditional Māori patterns in New Zealand’s fashion industry.
- Changes in burial customs in urbanized areas of Southeast Asia.
- Incorporation of First Nations symbols in Canadian public architecture.
Research Paper Topics on Math
If you're looking to explore the depth and applications of math, these research topics are both specific and engaging:
- Applications of fractal geometry in modeling natural phenomena.
- Mathematical approaches to solving complex optimization problems in logistics.
- Development of new algorithms for large-scale data encryption.
- Mathematical modeling of population dynamics in ecology.
- The use of game theory in economic decision-making processes.
- Exploring the mathematics behind machine learning algorithms.
- Advancements in numerical methods for solving partial differential equations.
- Topological data analysis and its applications in computational biology.
- Mathematical analysis of voting systems and fairness.
- The role of number theory in modern cryptography.
- Predictive models for financial markets using stochastic calculus.
- Mathematical foundations of quantum computing and quantum algorithms.
- Applications of chaos theory in weather prediction.
- Geometry of space-time in the context of general relativity.
- Mathematical techniques for analyzing big data in social networks.
Research Paper Topics on Art
Art is full of fascinating details and stories waiting to be explored. If you’re into art research, here are some research topics that might catch your interest:
- How Caravaggio used light and shadow in his religious paintings.
- The way Cubism shaped Picasso’s "Les Demoiselles d’Avignon."
- Gustav Klimt’s "The Kiss" and its ties to Viennese culture.
- Hokusai’s woodblock techniques in "The Great Wave off Kanagawa."
- Bauhaus principles that still influence graphic design today.
- Emotions and color in Mark Rothko’s abstract paintings.
- Leonora Carrington’s role in the Surrealist movement.
- Gaudí’s architectural genius in designing La Sagrada Familia.
- Industrial scenes captured in Charles Sheeler’s Precisionist art.
- Jean-Michel Basquiat’s take on graffiti and cultural identity.
- Frida Kahlo’s evolving self-portraits through her life.
- Claude Monet’s unique use of light in his Impressionist works.
- Diego Rivera’s murals as powerful political statements.
- The simplicity and impact of Donald Judd’s minimalist sculptures.
- How African art influenced Henri Matisse during his Fauvist period.
Research Topics on Sports
Sports offer a wide range of topics that are both intriguing and highly relevant. Here are some specific research ideas to consider if you're looking to explore the world of sports:
- The biomechanics behind sprinting techniques in elite athletes.
- The psychological effects of team sports on adolescent development.
- Injury prevention strategies in professional football (soccer).
- The impact of altitude training on endurance performance in marathon runners.
- Gender equity in sports: The evolution of women’s participation in the Olympics.
- The role of nutrition in recovery and performance for endurance athletes.
- How advanced analytics are changing strategies in basketball.
- The effects of early specialization in youth sports on long-term athletic development.
- The influence of sports media coverage on public perceptions of athletes.
- Technology in sports: The use of wearable devices to monitor athlete performance.
- Doping scandals and their long-term impact on athletes' careers.
- Mental health challenges faced by retired professional athletes.
- The economics of hosting major sporting events like the World Cup or Olympics.
- How climate change is affecting outdoor sports events and training schedules.
- The evolution of sports science in enhancing athlete training programs.
In 2024, some of the most popular research topics include the impact of technology on sports, the psychological aspects of team dynamics, and the evolution of gender equity in athletics.
If you’re still unsure about which topic to choose or need help with your essay, EssayService is a great option. Our research paper writing service can assist with everything from selecting the perfect topic to crafting a well-written paper, making the whole process a lot easier.
Frequently asked questions
She was flawless! first time using a website like this, I've ordered article review and i totally adored it! grammar punctuation, content - everything was on point
This writer is my go to, because whenever I need someone who I can trust my task to - I hire Joy. She wrote almost every paper for me for the last 2 years
Term paper done up to a highest standard, no revisions, perfect communication. 10s across the board!!!!!!!
I send him instructions and that's it. my paper was done 10 hours later, no stupid questions, he nailed it.
Sometimes I wonder if Michael is secretly a professor because he literally knows everything. HE DID SO WELL THAT MY PROF SHOWED MY PAPER AS AN EXAMPLE. unbelievable, many thanks
.webp)
New posts to your inbox!
Stay in touch
- IPR Intranet
INSTITUTE FOR POLICY RESEARCH
New ipr research: august 2024, get all our news.
Subscribe to newsletter

This month’s new research from our faculty experts investigates how a family-centered education program in Tulsa supports student parents, visibility and wellbeing in the bi+ community, perceptions of a living wage, and how parent-child discussions can help address subtle racism.
Education and Human Development
A Family-Centered Approach to Helping Student Parents Succeed in Higher Education
Approximately four million people juggle parenthood and college in the United States. How can a family-centered education program in Tulsa support these student parents? IPR faculty researchers Lauren Tighe , Teresa Eckrich Sommer , Terri Sabol , and Lindsay Chase-Lansdale investigate the effects of the program in Annals of the New York Academy of Sciences . The Community Action Project of Tulsa’s Career Advance program provides education and career training in healthcare to low-income parents with children. Its original model was centered in Head Start and helped parents achieve postsecondary education while their young children received early education programming. The program also provided numerous supportive services such as free tuition and childcare. The second model, which was based in an adult education and workforce agency and designed to serve the broader Tulsa population, began offering parents similar family-centered support and assistance The IPR team conducted a randomized control trial to evaluate the impacts of the adult model. They surveyed 277 racially and ethnically diverse parents, mostly mothers, 191 of whom received access to the program and 86 who did not. After a year in the program, parent participants were more likely to have obtained a vocational certificate or an associate degree compared to those who did not participate. The study is one of the first to show experimentally that a two-generation program might be effective in promoting student parents’ educational success.
Health Inequalities
Visibility, Relationship Dynamics, and Wellbeing the Bi+ Community
Bi+ people—those who are attracted to more than one gender—are the largest group within the LGBTQ+ community, but they often feel invisible. They also experience greater mental health challenges than people who identify as heterosexual, gay, or lesbian. A study by Emma McGorray, IPR social psychologist Eli Finkel , and Brian Feinstein in Psychology of Sexual Orientation and Gender Diversity explores associations between bi+ individuals’ feelings of invisibility and their quality of life, particularly in the context of romantic relationships. The researchers focus on two main questions: whether feeling visible as a bi+ person is linked to greater wellbeing, and which features of romantic relationships are associated with greater feelings of visibility. The team surveyed 450 bi+ individuals who were single, in same-gender relationships, or in mixed-gender relationships. They found that feeling recognized as a bi+ person was linked to higher levels of wellbeing, especially for those who consider their sexual orientation central to their sense of self. Participants in mixed-gender relationships with heterosexual partners reported a lower sense of visibility compared to those in same-gender relationships and those with bi+ partners. The study also revealed that a bi+ individual may feel invisible even when their partner affirms and recognizes their identity. The researchers encourage clinicians working with bi+ individuals to pay attention to their romantic relationships and partner characteristics and to assess how visible and central these individuals consider their bi+ identity. Finkel is a Morton O. Schapiro IPR Faculty Fellow.
Race, Poverty, and Inequality
Perceptions of a Living Wage
How much money is enough to live on is fundamental to many basic life decisions. In a working paper, IPR adjunct professor Michael Kraus and his colleagues examine how people estimate a living wage, how income shapes their estimates, and how it influences their support for government policies. The researchers asked 1,000 adults across the United States several questions, including what they think is a living wage, the average wage of working adults, and the average wage of workers earning the minimum wage. The participants also reported what they consider to be a basic need, their monthly spending, and their support for redistributive policies. The researchers find that people’s estimates of a living wage are higher than the federal poverty line, the state and federal minimum wage, a popular cost of living calculator called the MIT living wage calculator, and the proposed minimum wage standard of $15 per hour. Participants who reported higher estimates of a living wage were more likely to support redistributive policies, such as expanding programs that improve the living standards of disadvantaged groups or creating a federal job guarantee program. The results show that people generally report a living wage as higher than the federal standard and their beliefs about economic conditions are shaped by their own socioeconomic experiences. Future research should continue to explore income’s influence on perceptions of a living wage and how people calculate leisure as part of a living wage, given its importance for wellbeing.
Parent-Child Discussions Can Help Address Subtle Racism
Experts recommend that White parents discuss racism with their children to reduce racial bias. However, many parents fail to do so. In a study published in Developmental Psychology, IPR psychologist Sylvia Perry and her colleagues investigate what sort of language White parents used in guided discussions of race with their 8–12-year-old children and whether the conversations effectively decreased bias. The researchers recruited 84 White parent and child pairs who participated in a guided discussion task. Parents and their children watched interactions between a White and Black child that showcased overt prejudice, subtle prejudice, or neutral interactions. Following this, parents used suggested discussion prompts meant to facilitate color-conscious conversations, where prejudice was acknowledged, and discourage colorblind conversations, where prejudice was downplayed. Parents and children separately completed implicit association tests to measure their anti-Black bias before and after the task. The results indicated that parents and children who had discussed race showed a significant decrease in anti-Black bias, with parents’ implicit bias score decreasing from 0.53 to 0.34 and children's implicit bias score decreasing from 0.41 to 0.16. Moreover, over 90% of parents and children used color-conscious language during their discussion, and this was associated with decreased bias in both parents and children. Although some parents also used colorblind language during the guided task, this language weakened but did not erase the positive effects of the color-conscious language on bias reduction. Researchers suggest that it is critical for parents to have honest conversations with their children about racism, even from a young age.
Neighborhoods and Community Safety
Officer-Involved Killings of Unarmed Black People and Racial Disparities in Sleep
Research shows that Black Americans are more likely to report that they sleep less than White Americans, putting them at risk for worse physical and mental health outcomes. In a study published in JAMA Internal Medicine, IPR sociologist Andrew Papachristos and his colleagues investigate whether exposure to police officer-involved killings of unarmed Black people is linked to sleep duration in Black communities. The researchers use data on sleep duration from two nationally representative surveys: the US Behavioral Risk Factor Surveillance Survey (BRFSS) and the American Time Use Surveys (ATUS). They examined responses from 181,865 Black and 1,799,757 White adults in the BRFSS and 9,858 Black and 46,532 White adults in the ATUS between 2013 and 2019. They also reviewed data from Mapping Police Violence (MPV), an online database tracking officer-involved killings since 2013. They then used data from both surveys to examine changes in sleep duration for Black adults before and after exposure to officer-involved killings of unarmed Black Americans in their area of residence and nationally. The evidence reveals that Black Americans are more likely to report that they got short sleep—less than seven hours of sleep—or very short sleep—less than six hours of sleep—compared to White Americans after police killed an unarmed Black person. Black Americans reported less sleep when the killing was in the state where they lived. These findings highlight the role police violence can play in shaping racial disparities in sleep duration.
Photo credit: Unsplash
Published: August 28, 2024.
Related Research Stories

Faculty Spotlight: Eli Finkel

The Mental Health Effects of School Shootings

How Do Voters Think About Electability?
- Publications
- News and Events
- Education and Outreach
Software Engineering Institute
Sei digital library, latest publications, embracing ai: unlocking scalability and transformation through generative text, imagery, and synthetic audio, august 28, 2024 • webcast, by tyler brooks , shannon gallagher , dominic a. ross.
In this webcast, Tyler Brooks, Shannon Gallagher, and Dominic Ross aim to demystify AI and illustrate its transformative power in achieving scalability, adapting to changing landscapes, and driving digital innovation.
Counter AI: What Is It and What Can You Do About It?
August 27, 2024 • white paper, by nathan m. vanhoudnos , carol j. smith , matt churilla , shing-hon lau , lauren mcilvenny , greg touhill.
This paper describes counter artificial intelligence (AI) and provides recommendations on what can be done about it.
Using Quality Attribute Scenarios for ML Model Test Case Generation
August 27, 2024 • conference paper, by rachel brower-sinning , grace lewis , sebastián echeverría , ipek ozkaya.
This paper presents an approach based on quality attribute (QA) scenarios to elicit and define system- and model-relevant test cases for ML models.
3 API Security Risks (and How to Protect Against Them)
August 27, 2024 • podcast, by mckinley sconiers-hasan.
McKinley Sconiers-Hasan discusses three API risks and how to address them through the lens of zero trust.
Lessons Learned in Coordinated Disclosure for Artificial Intelligence and Machine Learning Systems
August 20, 2024 • white paper, by allen d. householder , vijay s. sarvepalli , jeff havrilla , matt churilla , lena pons , shing-hon lau , nathan m. vanhoudnos , andrew kompanek , lauren mcilvenny.
In this paper, the authors describe lessons learned from coordinating AI and ML vulnerabilities at the SEI's CERT/CC.
On the Design, Development, and Testing of Modern APIs
July 30, 2024 • white paper, by alejandro gomez , alex vesey.
This white paper discusses the design, desired qualities, development, testing, support, and security of modern application programming interfaces (APIs).
Evaluating Large Language Models for Cybersecurity Tasks: Challenges and Best Practices
July 26, 2024 • podcast, by jeff gennari , samuel j. perl.
Jeff Gennari and Sam Perl discuss applications for LLMs in cybersecurity, potential challenges, and recommendations for evaluating LLMs.
Capability-based Planning for Early-Stage Software Development
July 24, 2024 • podcast, by anandi hira , bill nichols.
This SEI podcast introduces capability-based planning (CBP) and its use and application in software acquisition.
A Model Problem for Assurance Research: An Autonomous Humanitarian Mission Scenario
July 23, 2024 • technical note, by gabriel moreno , anton hristozov , john e. robert , mark h. klein.
This report describes a model problem to support research in large-scale assurance.
Safeguarding Against Recent Vulnerabilities Related to Rust
June 28, 2024 • podcast, by david svoboda.
David Svoboda discusses two vulnerabilities related to Rust, their sources, and how to mitigate them.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 31 August 2024
Knowledge mapping and evolution of research on older adults’ technology acceptance: a bibliometric study from 2013 to 2023
- Xianru Shang ORCID: orcid.org/0009-0000-8906-3216 1 ,
- Zijian Liu 1 ,
- Chen Gong 1 ,
- Zhigang Hu 1 ,
- Yuexuan Wu 1 &
- Chengliang Wang ORCID: orcid.org/0000-0003-2208-3508 2
Humanities and Social Sciences Communications volume 11 , Article number: 1115 ( 2024 ) Cite this article
Metrics details
- Science, technology and society
The rapid expansion of information technology and the intensification of population aging are two prominent features of contemporary societal development. Investigating older adults’ acceptance and use of technology is key to facilitating their integration into an information-driven society. Given this context, the technology acceptance of older adults has emerged as a prioritized research topic, attracting widespread attention in the academic community. However, existing research remains fragmented and lacks a systematic framework. To address this gap, we employed bibliometric methods, utilizing the Web of Science Core Collection to conduct a comprehensive review of literature on older adults’ technology acceptance from 2013 to 2023. Utilizing VOSviewer and CiteSpace for data assessment and visualization, we created knowledge mappings of research on older adults’ technology acceptance. Our study employed multidimensional methods such as co-occurrence analysis, clustering, and burst analysis to: (1) reveal research dynamics, key journals, and domains in this field; (2) identify leading countries, their collaborative networks, and core research institutions and authors; (3) recognize the foundational knowledge system centered on theoretical model deepening, emerging technology applications, and research methods and evaluation, uncovering seminal literature and observing a shift from early theoretical and influential factor analyses to empirical studies focusing on individual factors and emerging technologies; (4) moreover, current research hotspots are primarily in the areas of factors influencing technology adoption, human-robot interaction experiences, mobile health management, and aging-in-place technology, highlighting the evolutionary context and quality distribution of research themes. Finally, we recommend that future research should deeply explore improvements in theoretical models, long-term usage, and user experience evaluation. Overall, this study presents a clear framework of existing research in the field of older adults’ technology acceptance, providing an important reference for future theoretical exploration and innovative applications.
Similar content being viewed by others
Research progress and intellectual structure of design for digital equity (DDE): A bibliometric analysis based on citespace
Exploring the role of interaction in older-adult service innovation: insights from the testing stage

Smart device interest, perceived usefulness, and preferences in rural Alabama seniors
Introduction.
In contemporary society, the rapid development of information technology has been intricately intertwined with the intensifying trend of population aging. According to the latest United Nations forecast, by 2050, the global population aged 65 and above is expected to reach 1.6 billion, representing about 16% of the total global population (UN 2023 ). Given the significant challenges of global aging, there is increasing evidence that emerging technologies have significant potential to maintain health and independence for older adults in their home and healthcare environments (Barnard et al. 2013 ; Soar 2010 ; Vancea and Solé-Casals 2016 ). This includes, but is not limited to, enhancing residential safety with smart home technologies (Touqeer et al. 2021 ; Wang et al. 2022 ), improving living independence through wearable technologies (Perez et al. 2023 ), and increasing medical accessibility via telehealth services (Kruse et al. 2020 ). Technological innovations are redefining the lifestyles of older adults, encouraging a shift from passive to active participation (González et al. 2012 ; Mostaghel 2016 ). Nevertheless, the effective application and dissemination of technology still depends on user acceptance and usage intentions (Naseri et al. 2023 ; Wang et al. 2023a ; Xia et al. 2024 ; Yu et al. 2023 ). Particularly, older adults face numerous challenges in accepting and using new technologies. These challenges include not only physical and cognitive limitations but also a lack of technological experience, along with the influences of social and economic factors (Valk et al. 2018 ; Wilson et al. 2021 ).
User acceptance of technology is a significant focus within information systems (IS) research (Dai et al. 2024 ), with several models developed to explain and predict user behavior towards technology usage, including the Technology Acceptance Model (TAM) (Davis 1989 ), TAM2, TAM3, and the Unified Theory of Acceptance and Use of Technology (UTAUT) (Venkatesh et al. 2003 ). Older adults, as a group with unique needs, exhibit different behavioral patterns during technology acceptance than other user groups, and these uniquenesses include changes in cognitive abilities, as well as motivations, attitudes, and perceptions of the use of new technologies (Chen and Chan 2011 ). The continual expansion of technology introduces considerable challenges for older adults, rendering the understanding of their technology acceptance a research priority. Thus, conducting in-depth research into older adults’ acceptance of technology is critically important for enhancing their integration into the information society and improving their quality of life through technological advancements.
Reviewing relevant literature to identify research gaps helps further solidify the theoretical foundation of the research topic. However, many existing literature reviews primarily focus on the factors influencing older adults’ acceptance or intentions to use technology. For instance, Ma et al. ( 2021 ) conducted a comprehensive analysis of the determinants of older adults’ behavioral intentions to use technology; Liu et al. ( 2022 ) categorized key variables in studies of older adults’ technology acceptance, noting a shift in focus towards social and emotional factors; Yap et al. ( 2022 ) identified seven categories of antecedents affecting older adults’ use of technology from an analysis of 26 articles, including technological, psychological, social, personal, cost, behavioral, and environmental factors; Schroeder et al. ( 2023 ) extracted 119 influencing factors from 59 articles and further categorized these into six themes covering demographics, health status, and emotional awareness. Additionally, some studies focus on the application of specific technologies, such as Ferguson et al. ( 2021 ), who explored barriers and facilitators to older adults using wearable devices for heart monitoring, and He et al. ( 2022 ) and Baer et al. ( 2022 ), who each conducted in-depth investigations into the acceptance of social assistive robots and mobile nutrition and fitness apps, respectively. In summary, current literature reviews on older adults’ technology acceptance exhibit certain limitations. Due to the interdisciplinary nature and complex knowledge structure of this field, traditional literature reviews often rely on qualitative analysis, based on literature analysis and periodic summaries, which lack sufficient objectivity and comprehensiveness. Additionally, systematic research is relatively limited, lacking a macroscopic description of the research trajectory from a holistic perspective. Over the past decade, research on older adults’ technology acceptance has experienced rapid growth, with a significant increase in literature, necessitating the adoption of new methods to review and examine the developmental trends in this field (Chen 2006 ; Van Eck and Waltman 2010 ). Bibliometric analysis, as an effective quantitative research method, analyzes published literature through visualization, offering a viable approach to extracting patterns and insights from a large volume of papers, and has been widely applied in numerous scientific research fields (Achuthan et al. 2023 ; Liu and Duffy 2023 ). Therefore, this study will employ bibliometric methods to systematically analyze research articles related to older adults’ technology acceptance published in the Web of Science Core Collection from 2013 to 2023, aiming to understand the core issues and evolutionary trends in the field, and to provide valuable references for future related research. Specifically, this study aims to explore and answer the following questions:
RQ1: What are the research dynamics in the field of older adults’ technology acceptance over the past decade? What are the main academic journals and fields that publish studies related to older adults’ technology acceptance?
RQ2: How is the productivity in older adults’ technology acceptance research distributed among countries, institutions, and authors?
RQ3: What are the knowledge base and seminal literature in older adults’ technology acceptance research? How has the research theme progressed?
RQ4: What are the current hot topics and their evolutionary trajectories in older adults’ technology acceptance research? How is the quality of research distributed?
Methodology and materials
Research method.
In recent years, bibliometrics has become one of the crucial methods for analyzing literature reviews and is widely used in disciplinary and industrial intelligence analysis (Jing et al. 2023 ; Lin and Yu 2024a ; Wang et al. 2024a ; Xu et al. 2021 ). Bibliometric software facilitates the visualization analysis of extensive literature data, intuitively displaying the network relationships and evolutionary processes between knowledge units, and revealing the underlying knowledge structure and potential information (Chen et al. 2024 ; López-Robles et al. 2018 ; Wang et al. 2024c ). This method provides new insights into the current status and trends of specific research areas, along with quantitative evidence, thereby enhancing the objectivity and scientific validity of the research conclusions (Chen et al. 2023 ; Geng et al. 2024 ). VOSviewer and CiteSpace are two widely used bibliometric software tools in academia (Pan et al. 2018 ), recognized for their robust functionalities based on the JAVA platform. Although each has its unique features, combining these two software tools effectively constructs mapping relationships between literature knowledge units and clearly displays the macrostructure of the knowledge domains. Particularly, VOSviewer, with its excellent graphical representation capabilities, serves as an ideal tool for handling large datasets and precisely identifying the focal points and hotspots of research topics. Therefore, this study utilizes VOSviewer (version 1.6.19) and CiteSpace (version 6.1.R6), combined with in-depth literature analysis, to comprehensively examine and interpret the research theme of older adults’ technology acceptance through an integrated application of quantitative and qualitative methods.
Data source
Web of Science is a comprehensively recognized database in academia, featuring literature that has undergone rigorous peer review and editorial scrutiny (Lin and Yu 2024b ; Mongeon and Paul-Hus 2016 ; Pranckutė 2021 ). This study utilizes the Web of Science Core Collection as its data source, specifically including three major citation indices: Science Citation Index Expanded (SCIE), Social Sciences Citation Index (SSCI), and Arts & Humanities Citation Index (A&HCI). These indices encompass high-quality research literature in the fields of science, social sciences, and arts and humanities, ensuring the comprehensiveness and reliability of the data. We combined “older adults” with “technology acceptance” through thematic search, with the specific search strategy being: TS = (elder OR elderly OR aging OR ageing OR senile OR senior OR old people OR “older adult*”) AND TS = (“technology acceptance” OR “user acceptance” OR “consumer acceptance”). The time span of literature search is from 2013 to 2023, with the types limited to “Article” and “Review” and the language to “English”. Additionally, the search was completed by October 27, 2023, to avoid data discrepancies caused by database updates. The initial search yielded 764 journal articles. Given that searches often retrieve articles that are superficially relevant but actually non-compliant, manual screening post-search was essential to ensure the relevance of the literature (Chen et al. 2024 ). Through manual screening, articles significantly deviating from the research theme were eliminated and rigorously reviewed. Ultimately, this study obtained 500 valid sample articles from the Web of Science Core Collection. The complete PRISMA screening process is illustrated in Fig. 1 .
Presentation of the data culling process in detail.
Data standardization
Raw data exported from databases often contain multiple expressions of the same terminology (Nguyen and Hallinger 2020 ). To ensure the accuracy and consistency of data, it is necessary to standardize the raw data (Strotmann and Zhao 2012 ). This study follows the data standardization process proposed by Taskin and Al ( 2019 ), mainly executing the following operations:
(1) Standardization of author and institution names is conducted to address different name expressions for the same author. For instance, “Chan, Alan Hoi Shou” and “Chan, Alan H. S.” are considered the same author, and distinct authors with the same name are differentiated by adding identifiers. Diverse forms of institutional names are unified to address variations caused by name changes or abbreviations, such as standardizing “FRANKFURT UNIV APPL SCI” and “Frankfurt University of Applied Sciences,” as well as “Chinese University of Hong Kong” and “University of Hong Kong” to consistent names.
(2) Different expressions of journal names are unified. For example, “International Journal of Human-Computer Interaction” and “Int J Hum Comput Interact” are standardized to a single name. This ensures consistency in journal names and prevents misclassification of literature due to differing journal names. Additionally, it involves checking if the journals have undergone name changes in the past decade to prevent any impact on the analysis due to such changes.
(3) Keywords data are cleansed by removing words that do not directly pertain to specific research content (e.g., people, review), merging synonyms (e.g., “UX” and “User Experience,” “aging-in-place” and “aging in place”), and standardizing plural forms of keywords (e.g., “assistive technologies” and “assistive technology,” “social robots” and “social robot”). This reduces redundant information in knowledge mapping.
Bibliometric results and analysis
Distribution power (rq1), literature descriptive statistical analysis.
Table 1 presents a detailed descriptive statistical overview of the literature in the field of older adults’ technology acceptance. After deduplication using the CiteSpace software, this study confirmed a valid sample size of 500 articles. Authored by 1839 researchers, the documents encompass 792 research institutions across 54 countries and are published in 217 different academic journals. As of the search cutoff date, these articles have accumulated 13,829 citations, with an annual average of 1156 citations, and an average of 27.66 citations per article. The h-index, a composite metric of quantity and quality of scientific output (Kamrani et al. 2021 ), reached 60 in this study.
Trends in publications and disciplinary distribution
The number of publications and citations are significant indicators of the research field’s development, reflecting its continuity, attention, and impact (Ale Ebrahim et al. 2014 ). The ranking of annual publications and citations in the field of older adults’ technology acceptance studies is presented chronologically in Fig. 2A . The figure shows a clear upward trend in the amount of literature in this field. Between 2013 and 2017, the number of publications increased slowly and decreased in 2018. However, in 2019, the number of publications increased rapidly to 52 and reached a peak of 108 in 2022, which is 6.75 times higher than in 2013. In 2022, the frequency of document citations reached its highest point with 3466 citations, reflecting the widespread recognition and citation of research in this field. Moreover, the curve of the annual number of publications fits a quadratic function, with a goodness-of-fit R 2 of 0.9661, indicating that the number of future publications is expected to increase even more rapidly.
A Trends in trends in annual publications and citations (2013–2023). B Overlay analysis of the distribution of discipline fields.
Figure 2B shows that research on older adults’ technology acceptance involves the integration of multidisciplinary knowledge. According to Web of Science Categories, these 500 articles are distributed across 85 different disciplines. We have tabulated the top ten disciplines by publication volume (Table 2 ), which include Medical Informatics (75 articles, 15.00%), Health Care Sciences & Services (71 articles, 14.20%), Gerontology (61 articles, 12.20%), Public Environmental & Occupational Health (57 articles, 11.40%), and Geriatrics & Gerontology (52 articles, 10.40%), among others. The high output in these disciplines reflects the concentrated global academic interest in this comprehensive research topic. Additionally, interdisciplinary research approaches provide diverse perspectives and a solid theoretical foundation for studies on older adults’ technology acceptance, also paving the way for new research directions.
Knowledge flow analysis
A dual-map overlay is a CiteSpace map superimposed on top of a base map, which shows the interrelationships between journals in different domains, representing the publication and citation activities in each domain (Chen and Leydesdorff 2014 ). The overlay map reveals the link between the citing domain (on the left side) and the cited domain (on the right side), reflecting the knowledge flow of the discipline at the journal level (Leydesdorff and Rafols 2012 ). We utilize the in-built Z-score algorithm of the software to cluster the graph, as shown in Fig. 3 .
The left side shows the citing journal, and the right side shows the cited journal.
Figure 3 shows the distribution of citing journals clusters for older adults’ technology acceptance on the left side, while the right side refers to the main cited journals clusters. Two knowledge flow citation trajectories were obtained; they are presented by the color of the cited regions, and the thickness of these trajectories is proportional to the Z-score scaled frequency of citations (Chen et al. 2014 ). Within the cited regions, the most popular fields with the most records covered are “HEALTH, NURSING, MEDICINE” and “PSYCHOLOGY, EDUCATION, SOCIAL”, and the elliptical aspect ratio of these two fields stands out. Fields have prominent elliptical aspect ratios, highlighting their significant influence on older adults’ technology acceptance research. Additionally, the major citation trajectories originate in these two areas and progress to the frontier research area of “PSYCHOLOGY, EDUCATION, HEALTH”. It is worth noting that the citation trajectory from “PSYCHOLOGY, EDUCATION, SOCIAL” has a significant Z-value (z = 6.81), emphasizing the significance and impact of this development path. In the future, “MATHEMATICS, SYSTEMS, MATHEMATICAL”, “MOLECULAR, BIOLOGY, IMMUNOLOGY”, and “NEUROLOGY, SPORTS, OPHTHALMOLOGY” may become emerging fields. The fields of “MEDICINE, MEDICAL, CLINICAL” may be emerging areas of cutting-edge research.
Main research journals analysis
Table 3 provides statistics for the top ten journals by publication volume in the field of older adults’ technology acceptance. Together, these journals have published 137 articles, accounting for 27.40% of the total publications, indicating that there is no highly concentrated core group of journals in this field, with publications being relatively dispersed. Notably, Computers in Human Behavior , Journal of Medical Internet Research , and International Journal of Human-Computer Interaction each lead with 15 publications. In terms of citation metrics, International Journal of Medical Informatics and Computers in Human Behavior stand out significantly, with the former accumulating a total of 1,904 citations, averaging 211.56 citations per article, and the latter totaling 1,449 citations, with an average of 96.60 citations per article. These figures emphasize the academic authority and widespread impact of these journals within the research field.
Research power (RQ2)
Countries and collaborations analysis.
The analysis revealed the global research pattern for country distribution and collaboration (Chen et al. 2019 ). Figure 4A shows the network of national collaborations on older adults’ technology acceptance research. The size of the bubbles represents the amount of publications in each country, while the thickness of the connecting lines expresses the closeness of the collaboration among countries. Generally, this research subject has received extensive international attention, with China and the USA publishing far more than any other countries. China has established notable research collaborations with the USA, UK and Malaysia in this field, while other countries have collaborations, but the closeness is relatively low and scattered. Figure 4B shows the annual publication volume dynamics of the top ten countries in terms of total publications. Since 2017, China has consistently increased its annual publications, while the USA has remained relatively stable. In 2019, the volume of publications in each country increased significantly, this was largely due to the global outbreak of the COVID-19 pandemic, which has led to increased reliance on information technology among the elderly for medical consultations, online socialization, and health management (Sinha et al. 2021 ). This phenomenon has led to research advances in technology acceptance among older adults in various countries. Table 4 shows that the top ten countries account for 93.20% of the total cumulative number of publications, with each country having published more than 20 papers. Among these ten countries, all of them except China are developed countries, indicating that the research field of older adults’ technology acceptance has received general attention from developed countries. Currently, China and the USA were the leading countries in terms of publications with 111 and 104 respectively, accounting for 22.20% and 20.80%. The UK, Germany, Italy, and the Netherlands also made significant contributions. The USA and China ranked first and second in terms of the number of citations, while the Netherlands had the highest average citations, indicating the high impact and quality of its research. The UK has shown outstanding performance in international cooperation, while the USA highlights its significant academic influence in this field with the highest h-index value.
A National collaboration network. B Annual volume of publications in the top 10 countries.
Institutions and authors analysis
Analyzing the number of publications and citations can reveal an institution’s or author’s research strength and influence in a particular research area (Kwiek 2021 ). Tables 5 and 6 show the statistics of the institutions and authors whose publication counts are in the top ten, respectively. As shown in Table 5 , higher education institutions hold the main position in this research field. Among the top ten institutions, City University of Hong Kong and The University of Hong Kong from China lead with 14 and 9 publications, respectively. City University of Hong Kong has the highest h-index, highlighting its significant influence in the field. It is worth noting that Tilburg University in the Netherlands is not among the top five in terms of publications, but the high average citation count (130.14) of its literature demonstrates the high quality of its research.
After analyzing the authors’ output using Price’s Law (Redner 1998 ), the highest number of publications among the authors counted ( n = 10) defines a publication threshold of 3 for core authors in this research area. As a result of quantitative screening, a total of 63 core authors were identified. Table 6 shows that Chen from Zhejiang University, China, Ziefle from RWTH Aachen University, Germany, and Rogers from Macquarie University, Australia, were the top three authors in terms of the number of publications, with 10, 9, and 8 articles, respectively. In terms of average citation rate, Peek and Wouters, both scholars from the Netherlands, have significantly higher rates than other scholars, with 183.2 and 152.67 respectively. This suggests that their research is of high quality and widely recognized. Additionally, Chen and Rogers have high h-indices in this field.
Knowledge base and theme progress (RQ3)
Research knowledge base.
Co-citation relationships occur when two documents are cited together (Zhang and Zhu 2022 ). Co-citation mapping uses references as nodes to represent the knowledge base of a subject area (Min et al. 2021). Figure 5A illustrates co-occurrence mapping in older adults’ technology acceptance research, where larger nodes signify higher co-citation frequencies. Co-citation cluster analysis can be used to explore knowledge structure and research boundaries (Hota et al. 2020 ; Shiau et al. 2023 ). The co-citation clustering mapping of older adults’ technology acceptance research literature (Fig. 5B ) shows that the Q value of the clustering result is 0.8129 (>0.3), and the average value of the weight S is 0.9391 (>0.7), indicating that the clusters are uniformly distributed with a significant and credible structure. This further proves that the boundaries of the research field are clear and there is significant differentiation in the field. The figure features 18 cluster labels, each associated with thematic color blocks corresponding to different time slices. Highlighted emerging research themes include #2 Smart Home Technology, #7 Social Live, and #10 Customer Service. Furthermore, the clustering labels extracted are primarily classified into three categories: theoretical model deepening, emerging technology applications, research methods and evaluation, as detailed in Table 7 .
A Co-citation analysis of references. B Clustering network analysis of references.
Seminal literature analysis
The top ten nodes in terms of co-citation frequency were selected for further analysis. Table 8 displays the corresponding node information. Studies were categorized into four main groups based on content analysis. (1) Research focusing on specific technology usage by older adults includes studies by Peek et al. ( 2014 ), Ma et al. ( 2016 ), Hoque and Sorwar ( 2017 ), and Li et al. ( 2019 ), who investigated the factors influencing the use of e-technology, smartphones, mHealth, and smart wearables, respectively. (2) Concerning the development of theoretical models of technology acceptance, Chen and Chan ( 2014 ) introduced the Senior Technology Acceptance Model (STAM), and Macedo ( 2017 ) analyzed the predictive power of UTAUT2 in explaining older adults’ intentional behaviors and information technology usage. (3) In exploring older adults’ information technology adoption and behavior, Lee and Coughlin ( 2015 ) emphasized that the adoption of technology by older adults is a multifactorial process that includes performance, price, value, usability, affordability, accessibility, technical support, social support, emotion, independence, experience, and confidence. Yusif et al. ( 2016 ) conducted a literature review examining the key barriers affecting older adults’ adoption of assistive technology, including factors such as privacy, trust, functionality/added value, cost, and stigma. (4) From the perspective of research into older adults’ technology acceptance, Mitzner et al. ( 2019 ) assessed the long-term usage of computer systems designed for the elderly, whereas Guner and Acarturk ( 2020 ) compared information technology usage and acceptance between older and younger adults. The breadth and prevalence of this literature make it a vital reference for researchers in the field, also providing new perspectives and inspiration for future research directions.
Research thematic progress
Burst citation is a node of literature that guides the sudden change in dosage, which usually represents a prominent development or major change in a particular field, with innovative and forward-looking qualities. By analyzing the emergent literature, it is often easy to understand the dynamics of the subject area, mapping the emerging thematic change (Chen et al. 2022 ). Figure 6 shows the burst citation mapping in the field of older adults’ technology acceptance research, with burst citations represented by red nodes (Fig. 6A ). For the ten papers with the highest burst intensity (Fig. 6B ), this study will conduct further analysis in conjunction with literature review.
A Burst detection of co-citation. B The top 10 references with the strongest citation bursts.
As shown in Fig. 6 , Mitzner et al. ( 2010 ) broke the stereotype that older adults are fearful of technology, found that they actually have positive attitudes toward technology, and emphasized the centrality of ease of use and usefulness in the process of technology acceptance. This finding provides an important foundation for subsequent research. During the same period, Wagner et al. ( 2010 ) conducted theory-deepening and applied research on technology acceptance among older adults. The research focused on older adults’ interactions with computers from the perspective of Social Cognitive Theory (SCT). This expanded the understanding of technology acceptance, particularly regarding the relationship between behavior, environment, and other SCT elements. In addition, Pan and Jordan-Marsh ( 2010 ) extended the TAM to examine the interactions among predictors of perceived usefulness, perceived ease of use, subjective norm, and convenience conditions when older adults use the Internet, taking into account the moderating roles of gender and age. Heerink et al. ( 2010 ) adapted and extended the UTAUT, constructed a technology acceptance model specifically designed for older users’ acceptance of assistive social agents, and validated it using controlled experiments and longitudinal data, explaining intention to use by combining functional assessment and social interaction variables.
Then the research theme shifted to an in-depth analysis of the factors influencing technology acceptance among older adults. Two papers with high burst strengths emerged during this period: Peek et al. ( 2014 ) (Strength = 12.04), Chen and Chan ( 2014 ) (Strength = 9.81). Through a systematic literature review and empirical study, Peek STM and Chen K, among others, identified multidimensional factors that influence older adults’ technology acceptance. Peek et al. ( 2014 ) analyzed literature on the acceptance of in-home care technology among older adults and identified six factors that influence their acceptance: concerns about technology, expected benefits, technology needs, technology alternatives, social influences, and older adult characteristics, with a focus on differences between pre- and post-implementation factors. Chen and Chan ( 2014 ) constructed the STAM by administering a questionnaire to 1012 older adults and adding eight important factors, including technology anxiety, self-efficacy, cognitive ability, and physical function, based on the TAM. This enriches the theoretical foundation of the field. In addition, Braun ( 2013 ) highlighted the role of perceived usefulness, trust in social networks, and frequency of Internet use in older adults’ use of social networks, while ease of use and social pressure were not significant influences. These findings contribute to the study of older adults’ technology acceptance within specific technology application domains.
Recent research has focused on empirical studies of personal factors and emerging technologies. Ma et al. ( 2016 ) identified key personal factors affecting smartphone acceptance among older adults through structured questionnaires and face-to-face interviews with 120 participants. The study found that cost, self-satisfaction, and convenience were important factors influencing perceived usefulness and ease of use. This study offers empirical evidence to comprehend the main factors that drive smartphone acceptance among Chinese older adults. Additionally, Yusif et al. ( 2016 ) presented an overview of the obstacles that hinder older adults’ acceptance of assistive technologies, focusing on privacy, trust, and functionality.
In summary, research on older adults’ technology acceptance has shifted from early theoretical deepening and analysis of influencing factors to empirical studies in the areas of personal factors and emerging technologies, which have greatly enriched the theoretical basis of older adults’ technology acceptance and provided practical guidance for the design of emerging technology products.
Research hotspots, evolutionary trends, and quality distribution (RQ4)
Core keywords analysis.
Keywords concise the main idea and core of the literature, and are a refined summary of the research content (Huang et al. 2021 ). In CiteSpace, nodes with a centrality value greater than 0.1 are considered to be critical nodes. Analyzing keywords with high frequency and centrality helps to visualize the hot topics in the research field (Park et al. 2018 ). The merged keywords were imported into CiteSpace, and the top 10 keywords were counted and sorted by frequency and centrality respectively, as shown in Table 9 . The results show that the keyword “TAM” has the highest frequency (92), followed by “UTAUT” (24), which reflects that the in-depth study of the existing technology acceptance model and its theoretical expansion occupy a central position in research related to older adults’ technology acceptance. Furthermore, the terms ‘assistive technology’ and ‘virtual reality’ are both high-frequency and high-centrality terms (frequency = 17, centrality = 0.10), indicating that the research on assistive technology and virtual reality for older adults is the focus of current academic attention.
Research hotspots analysis
Using VOSviewer for keyword co-occurrence analysis organizes keywords into groups or clusters based on their intrinsic connections and frequencies, clearly highlighting the research field’s hot topics. The connectivity among keywords reveals correlations between different topics. To ensure accuracy, the analysis only considered the authors’ keywords. Subsequently, the keywords were filtered by setting the keyword frequency to 5 to obtain the keyword clustering map of the research on older adults’ technology acceptance research keyword clustering mapping (Fig. 7 ), combined with the keyword co-occurrence clustering network (Fig. 7A ) and the corresponding density situation (Fig. 7B ) to make a detailed analysis of the following four groups of clustered themes.
A Co-occurrence clustering network. B Keyword density.
Cluster #1—Research on the factors influencing technology adoption among older adults is a prominent topic, covering age, gender, self-efficacy, attitude, and and intention to use (Berkowsky et al. 2017 ; Wang et al. 2017 ). It also examined older adults’ attitudes towards and acceptance of digital health technologies (Ahmad and Mozelius, 2022 ). Moreover, the COVID-19 pandemic, significantly impacting older adults’ technology attitudes and usage, has underscored the study’s importance and urgency. Therefore, it is crucial to conduct in-depth studies on how older adults accept, adopt, and effectively use new technologies, to address their needs and help them overcome the digital divide within digital inclusion. This will improve their quality of life and healthcare experiences.
Cluster #2—Research focuses on how older adults interact with assistive technologies, especially assistive robots and health monitoring devices, emphasizing trust, usability, and user experience as crucial factors (Halim et al. 2022 ). Moreover, health monitoring technologies effectively track and manage health issues common in older adults, like dementia and mild cognitive impairment (Lussier et al. 2018 ; Piau et al. 2019 ). Interactive exercise games and virtual reality have been deployed to encourage more physical and cognitive engagement among older adults (Campo-Prieto et al. 2021 ). Personalized and innovative technology significantly enhances older adults’ participation, improving their health and well-being.
Cluster #3—Optimizing health management for older adults using mobile technology. With the development of mobile health (mHealth) and health information technology, mobile applications, smartphones, and smart wearable devices have become effective tools to help older users better manage chronic conditions, conduct real-time health monitoring, and even receive telehealth services (Dupuis and Tsotsos 2018 ; Olmedo-Aguirre et al. 2022 ; Kim et al. 2014 ). Additionally, these technologies can mitigate the problem of healthcare resource inequality, especially in developing countries. Older adults’ acceptance and use of these technologies are significantly influenced by their behavioral intentions, motivational factors, and self-management skills. These internal motivational factors, along with external factors, jointly affect older adults’ performance in health management and quality of life.
Cluster #4—Research on technology-assisted home care for older adults is gaining popularity. Environmentally assisted living enhances older adults’ independence and comfort at home, offering essential support and security. This has a crucial impact on promoting healthy aging (Friesen et al. 2016 ; Wahlroos et al. 2023 ). The smart home is a core application in this field, providing a range of solutions that facilitate independent living for the elderly in a highly integrated and user-friendly manner. This fulfills different dimensions of living and health needs (Majumder et al. 2017 ). Moreover, eHealth offers accurate and personalized health management and healthcare services for older adults (Delmastro et al. 2018 ), ensuring their needs are met at home. Research in this field often employs qualitative methods and structural equation modeling to fully understand older adults’ needs and experiences at home and analyze factors influencing technology adoption.
Evolutionary trends analysis
To gain a deeper understanding of the evolutionary trends in research hotspots within the field of older adults’ technology acceptance, we conducted a statistical analysis of the average appearance times of keywords, using CiteSpace to generate the time-zone evolution mapping (Fig. 8 ) and burst keywords. The time-zone mapping visually displays the evolution of keywords over time, intuitively reflecting the frequency and initial appearance of keywords in research, commonly used to identify trends in research topics (Jing et al. 2024a ; Kumar et al. 2021 ). Table 10 lists the top 15 keywords by burst strength, with the red sections indicating high-frequency citations and their burst strength in specific years. These burst keywords reveal the focus and trends of research themes over different periods (Kleinberg 2002 ). Combining insights from the time-zone mapping and burst keywords provides more objective and accurate research insights (Wang et al. 2023b ).
Reflecting the frequency and time of first appearance of keywords in the study.
An integrated analysis of Fig. 8 and Table 10 shows that early research on older adults’ technology acceptance primarily focused on factors such as perceived usefulness, ease of use, and attitudes towards information technology, including their use of computers and the internet (Pan and Jordan-Marsh 2010 ), as well as differences in technology use between older adults and other age groups (Guner and Acarturk 2020 ). Subsequently, the research focus expanded to improving the quality of life for older adults, exploring how technology can optimize health management and enhance the possibility of independent living, emphasizing the significant role of technology in improving the quality of life for the elderly. With ongoing technological advancements, recent research has shifted towards areas such as “virtual reality,” “telehealth,” and “human-robot interaction,” with a focus on the user experience of older adults (Halim et al. 2022 ). The appearance of keywords such as “physical activity” and “exercise” highlights the value of technology in promoting physical activity and health among older adults. This phase of research tends to make cutting-edge technology genuinely serve the practical needs of older adults, achieving its widespread application in daily life. Additionally, research has focused on expanding and quantifying theoretical models of older adults’ technology acceptance, involving keywords such as “perceived risk”, “validation” and “UTAUT”.
In summary, from 2013 to 2023, the field of older adults’ technology acceptance has evolved from initial explorations of influencing factors, to comprehensive enhancements in quality of life and health management, and further to the application and deepening of theoretical models and cutting-edge technologies. This research not only reflects the diversity and complexity of the field but also demonstrates a comprehensive and in-depth understanding of older adults’ interactions with technology across various life scenarios and needs.
Research quality distribution
To reveal the distribution of research quality in the field of older adults’ technology acceptance, a strategic diagram analysis is employed to calculate and illustrate the internal development and interrelationships among various research themes (Xie et al. 2020 ). The strategic diagram uses Centrality as the X-axis and Density as the Y-axis to divide into four quadrants, where the X-axis represents the strength of the connection between thematic clusters and other themes, with higher values indicating a central position in the research field; the Y-axis indicates the level of development within the thematic clusters, with higher values denoting a more mature and widely recognized field (Li and Zhou 2020 ).
Through cluster analysis and manual verification, this study categorized 61 core keywords (Frequency ≥5) into 11 thematic clusters. Subsequently, based on the keywords covered by each thematic cluster, the research themes and their directions for each cluster were summarized (Table 11 ), and the centrality and density coordinates for each cluster were precisely calculated (Table 12 ). Finally, a strategic diagram of the older adults’ technology acceptance research field was constructed (Fig. 9 ). Based on the distribution of thematic clusters across the quadrants in the strategic diagram, the structure and developmental trends of the field were interpreted.
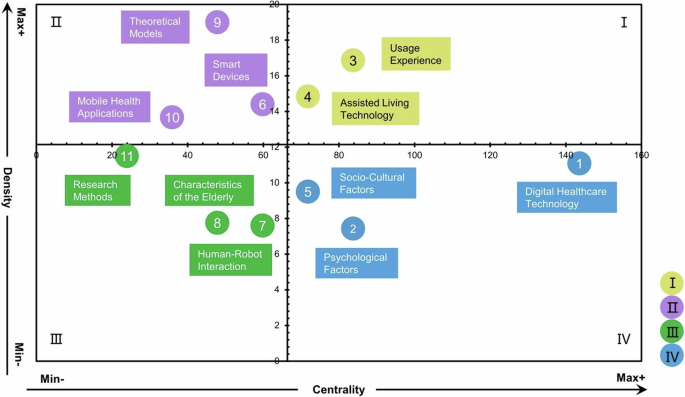
Classification and visualization of theme clusters based on density and centrality.
As illustrated in Fig. 9 , (1) the theme clusters of #3 Usage Experience and #4 Assisted Living Technology are in the first quadrant, characterized by high centrality and density. Their internal cohesion and close links with other themes indicate their mature development, systematic research content or directions have been formed, and they have a significant influence on other themes. These themes play a central role in the field of older adults’ technology acceptance and have promising prospects. (2) The theme clusters of #6 Smart Devices, #9 Theoretical Models, and #10 Mobile Health Applications are in the second quadrant, with higher density but lower centrality. These themes have strong internal connections but weaker external links, indicating that these three themes have received widespread attention from researchers and have been the subject of related research, but more as self-contained systems and exhibit independence. Therefore, future research should further explore in-depth cooperation and cross-application with other themes. (3) The theme clusters of #7 Human-Robot Interaction, #8 Characteristics of the Elderly, and #11 Research Methods are in the third quadrant, with lower centrality and density. These themes are loosely connected internally and have weak links with others, indicating their developmental immaturity. Compared to other topics, they belong to the lower attention edge and niche themes, and there is a need for further investigation. (4) The theme clusters of #1 Digital Healthcare Technology, #2 Psychological Factors, and #5 Socio-Cultural Factors are located in the fourth quadrant, with high centrality but low density. Although closely associated with other research themes, the internal cohesion within these clusters is relatively weak. This suggests that while these themes are closely linked to other research areas, their own development remains underdeveloped, indicating a core immaturity. Nevertheless, these themes are crucial within the research domain of elderly technology acceptance and possess significant potential for future exploration.
Discussion on distribution power (RQ1)
Over the past decade, academic interest and influence in the area of older adults’ technology acceptance have significantly increased. This trend is evidenced by a quantitative analysis of publication and citation volumes, particularly noticeable in 2019 and 2022, where there was a substantial rise in both metrics. The rise is closely linked to the widespread adoption of emerging technologies such as smart homes, wearable devices, and telemedicine among older adults. While these technologies have enhanced their quality of life, they also pose numerous challenges, sparking extensive research into their acceptance, usage behaviors, and influencing factors among the older adults (Pirzada et al. 2022 ; Garcia Reyes et al. 2023 ). Furthermore, the COVID-19 pandemic led to a surge in technology demand among older adults, especially in areas like medical consultation, online socialization, and health management, further highlighting the importance and challenges of technology. Health risks and social isolation have compelled older adults to rely on technology for daily activities, accelerating its adoption and application within this demographic. This phenomenon has made technology acceptance a critical issue, driving societal and academic focus on the study of technology acceptance among older adults.
The flow of knowledge at the level of high-output disciplines and journals, along with the primary publishing outlets, indicates the highly interdisciplinary nature of research into older adults’ technology acceptance. This reflects the complexity and breadth of issues related to older adults’ technology acceptance, necessitating the integration of multidisciplinary knowledge and approaches. Currently, research is primarily focused on medical health and human-computer interaction, demonstrating academic interest in improving health and quality of life for older adults and addressing the urgent needs related to their interactions with technology. In the field of medical health, research aims to provide advanced and innovative healthcare technologies and services to meet the challenges of an aging population while improving the quality of life for older adults (Abdi et al. 2020 ; Wilson et al. 2021 ). In the field of human-computer interaction, research is focused on developing smarter and more user-friendly interaction models to meet the needs of older adults in the digital age, enabling them to actively participate in social activities and enjoy a higher quality of life (Sayago, 2019 ). These studies are crucial for addressing the challenges faced by aging societies, providing increased support and opportunities for the health, welfare, and social participation of older adults.
Discussion on research power (RQ2)
This study analyzes leading countries and collaboration networks, core institutions and authors, revealing the global research landscape and distribution of research strength in the field of older adults’ technology acceptance, and presents quantitative data on global research trends. From the analysis of country distribution and collaborations, China and the USA hold dominant positions in this field, with developed countries like the UK, Germany, Italy, and the Netherlands also excelling in international cooperation and research influence. The significant investment in technological research and the focus on the technological needs of older adults by many developed countries reflect their rapidly aging societies, policy support, and resource allocation.
China is the only developing country that has become a major contributor in this field, indicating its growing research capabilities and high priority given to aging societies and technological innovation. Additionally, China has close collaborations with countries such as USA, the UK, and Malaysia, driven not only by technological research needs but also by shared challenges and complementarities in aging issues among these nations. For instance, the UK has extensive experience in social welfare and aging research, providing valuable theoretical guidance and practical experience. International collaborations, aimed at addressing the challenges of aging, integrate the strengths of various countries, advancing in-depth and widespread development in the research of technology acceptance among older adults.
At the institutional and author level, City University of Hong Kong leads in publication volume, with research teams led by Chan and Chen demonstrating significant academic activity and contributions. Their research primarily focuses on older adults’ acceptance and usage behaviors of various technologies, including smartphones, smart wearables, and social robots (Chen et al. 2015 ; Li et al. 2019 ; Ma et al. 2016 ). These studies, targeting specific needs and product characteristics of older adults, have developed new models of technology acceptance based on existing frameworks, enhancing the integration of these technologies into their daily lives and laying a foundation for further advancements in the field. Although Tilburg University has a smaller publication output, it holds significant influence in the field of older adults’ technology acceptance. Particularly, the high citation rate of Peek’s studies highlights their excellence in research. Peek extensively explored older adults’ acceptance and usage of home care technologies, revealing the complexity and dynamics of their technology use behaviors. His research spans from identifying systemic influencing factors (Peek et al. 2014 ; Peek et al. 2016 ), emphasizing familial impacts (Luijkx et al. 2015 ), to constructing comprehensive models (Peek et al. 2017 ), and examining the dynamics of long-term usage (Peek et al. 2019 ), fully reflecting the evolving technology landscape and the changing needs of older adults. Additionally, the ongoing contributions of researchers like Ziefle, Rogers, and Wouters in the field of older adults’ technology acceptance demonstrate their research influence and leadership. These researchers have significantly enriched the knowledge base in this area with their diverse perspectives. For instance, Ziefle has uncovered the complex attitudes of older adults towards technology usage, especially the trade-offs between privacy and security, and how different types of activities affect their privacy needs (Maidhof et al. 2023 ; Mujirishvili et al. 2023 ; Schomakers and Ziefle 2023 ; Wilkowska et al. 2022 ), reflecting a deep exploration and ongoing innovation in the field of older adults’ technology acceptance.
Discussion on knowledge base and thematic progress (RQ3)
Through co-citation analysis and systematic review of seminal literature, this study reveals the knowledge foundation and thematic progress in the field of older adults’ technology acceptance. Co-citation networks and cluster analyses illustrate the structural themes of the research, delineating the differentiation and boundaries within this field. Additionally, burst detection analysis offers a valuable perspective for understanding the thematic evolution in the field of technology acceptance among older adults. The development and innovation of theoretical models are foundational to this research. Researchers enhance the explanatory power of constructed models by deepening and expanding existing technology acceptance theories to address theoretical limitations. For instance, Heerink et al. ( 2010 ) modified and expanded the UTAUT model by integrating functional assessment and social interaction variables to create the almere model. This model significantly enhances the ability to explain the intentions of older users in utilizing assistive social agents and improves the explanation of actual usage behaviors. Additionally, Chen and Chan ( 2014 ) extended the TAM to include age-related health and capability features of older adults, creating the STAM, which substantially improves predictions of older adults’ technology usage behaviors. Personal attributes, health and capability features, and facilitating conditions have a direct impact on technology acceptance. These factors more effectively predict older adults’ technology usage behaviors than traditional attitudinal factors.
With the advancement of technology and the application of emerging technologies, new research topics have emerged, increasingly focusing on older adults’ acceptance and use of these technologies. Prior to this, the study by Mitzner et al. ( 2010 ) challenged the stereotype of older adults’ conservative attitudes towards technology, highlighting the central roles of usability and usefulness in the technology acceptance process. This discovery laid an important foundation for subsequent research. Research fields such as “smart home technology,” “social life,” and “customer service” are emerging, indicating a shift in focus towards the practical and social applications of technology in older adults’ lives. Research not only focuses on the technology itself but also on how these technologies integrate into older adults’ daily lives and how they can improve the quality of life through technology. For instance, studies such as those by Ma et al. ( 2016 ), Hoque and Sorwar ( 2017 ), and Li et al. ( 2019 ) have explored factors influencing older adults’ use of smartphones, mHealth, and smart wearable devices.
Furthermore, the diversification of research methodologies and innovation in evaluation techniques, such as the use of mixed methods, structural equation modeling (SEM), and neural network (NN) approaches, have enhanced the rigor and reliability of the findings, enabling more precise identification of the factors and mechanisms influencing technology acceptance. Talukder et al. ( 2020 ) employed an effective multimethodological strategy by integrating SEM and NN to leverage the complementary strengths of both approaches, thus overcoming their individual limitations and more accurately analyzing and predicting older adults’ acceptance of wearable health technologies (WHT). SEM is utilized to assess the determinants’ impact on the adoption of WHT, while neural network models validate SEM outcomes and predict the significance of key determinants. This combined approach not only boosts the models’ reliability and explanatory power but also provides a nuanced understanding of the motivations and barriers behind older adults’ acceptance of WHT, offering deep research insights.
Overall, co-citation analysis of the literature in the field of older adults’ technology acceptance has uncovered deeper theoretical modeling and empirical studies on emerging technologies, while emphasizing the importance of research methodological and evaluation innovations in understanding complex social science issues. These findings are crucial for guiding the design and marketing strategies of future technology products, especially in the rapidly growing market of older adults.
Discussion on research hotspots and evolutionary trends (RQ4)
By analyzing core keywords, we can gain deep insights into the hot topics, evolutionary trends, and quality distribution of research in the field of older adults’ technology acceptance. The frequent occurrence of the keywords “TAM” and “UTAUT” indicates that the applicability and theoretical extension of existing technology acceptance models among older adults remain a focal point in academia. This phenomenon underscores the enduring influence of the studies by Davis ( 1989 ) and Venkatesh et al. ( 2003 ), whose models provide a robust theoretical framework for explaining and predicting older adults’ acceptance and usage of emerging technologies. With the widespread application of artificial intelligence (AI) and big data technologies, these theoretical models have incorporated new variables such as perceived risk, trust, and privacy issues (Amin et al. 2024 ; Chen et al. 2024 ; Jing et al. 2024b ; Seibert et al. 2021 ; Wang et al. 2024b ), advancing the theoretical depth and empirical research in this field.
Keyword co-occurrence cluster analysis has revealed multiple research hotspots in the field, including factors influencing technology adoption, interactive experiences between older adults and assistive technologies, the application of mobile health technology in health management, and technology-assisted home care. These studies primarily focus on enhancing the quality of life and health management of older adults through emerging technologies, particularly in the areas of ambient assisted living, smart health monitoring, and intelligent medical care. In these domains, the role of AI technology is increasingly significant (Qian et al. 2021 ; Ho 2020 ). With the evolution of next-generation information technologies, AI is increasingly integrated into elder care systems, offering intelligent, efficient, and personalized service solutions by analyzing the lifestyles and health conditions of older adults. This integration aims to enhance older adults’ quality of life in aspects such as health monitoring and alerts, rehabilitation assistance, daily health management, and emotional support (Lee et al. 2023 ). A survey indicates that 83% of older adults prefer AI-driven solutions when selecting smart products, demonstrating the increasing acceptance of AI in elder care (Zhao and Li 2024 ). Integrating AI into elder care presents both opportunities and challenges, particularly in terms of user acceptance, trust, and long-term usage effects, which warrant further exploration (Mhlanga 2023 ). These studies will help better understand the profound impact of AI technology on the lifestyles of older adults and provide critical references for optimizing AI-driven elder care services.
The Time-zone evolution mapping and burst keyword analysis further reveal the evolutionary trends of research hotspots. Early studies focused on basic technology acceptance models and user perceptions, later expanding to include quality of life and health management. In recent years, research has increasingly focused on cutting-edge technologies such as virtual reality, telehealth, and human-robot interaction, with a concurrent emphasis on the user experience of older adults. This evolutionary process demonstrates a deepening shift from theoretical models to practical applications, underscoring the significant role of technology in enhancing the quality of life for older adults. Furthermore, the strategic coordinate mapping analysis clearly demonstrates the development and mutual influence of different research themes. High centrality and density in the themes of Usage Experience and Assisted Living Technology indicate their mature research status and significant impact on other themes. The themes of Smart Devices, Theoretical Models, and Mobile Health Applications demonstrate self-contained research trends. The themes of Human-Robot Interaction, Characteristics of the Elderly, and Research Methods are not yet mature, but they hold potential for development. Themes of Digital Healthcare Technology, Psychological Factors, and Socio-Cultural Factors are closely related to other themes, displaying core immaturity but significant potential.
In summary, the research hotspots in the field of older adults’ technology acceptance are diverse and dynamic, demonstrating the academic community’s profound understanding of how older adults interact with technology across various life contexts and needs. Under the influence of AI and big data, research should continue to focus on the application of emerging technologies among older adults, exploring in depth how they adapt to and effectively use these technologies. This not only enhances the quality of life and healthcare experiences for older adults but also drives ongoing innovation and development in this field.
Research agenda
Based on the above research findings, to further understand and promote technology acceptance and usage among older adults, we recommend future studies focus on refining theoretical models, exploring long-term usage, and assessing user experience in the following detailed aspects:
Refinement and validation of specific technology acceptance models for older adults: Future research should focus on developing and validating technology acceptance models based on individual characteristics, particularly considering variations in technology acceptance among older adults across different educational levels and cultural backgrounds. This includes factors such as age, gender, educational background, and cultural differences. Additionally, research should examine how well specific technologies, such as wearable devices and mobile health applications, meet the needs of older adults. Building on existing theoretical models, this research should integrate insights from multiple disciplines such as psychology, sociology, design, and engineering through interdisciplinary collaboration to create more accurate and comprehensive models, which should then be validated in relevant contexts.
Deepening the exploration of the relationship between long-term technology use and quality of life among older adults: The acceptance and use of technology by users is a complex and dynamic process (Seuwou et al. 2016 ). Existing research predominantly focuses on older adults’ initial acceptance or short-term use of new technologies; however, the impact of long-term use on their quality of life and health is more significant. Future research should focus on the evolution of older adults’ experiences and needs during long-term technology usage, and the enduring effects of technology on their social interactions, mental health, and life satisfaction. Through longitudinal studies and qualitative analysis, this research reveals the specific needs and challenges of older adults in long-term technology use, providing a basis for developing technologies and strategies that better meet their requirements. This understanding aids in comprehensively assessing the impact of technology on older adults’ quality of life and guiding the optimization and improvement of technological products.
Evaluating the Importance of User Experience in Research on Older Adults’ Technology Acceptance: Understanding the mechanisms of information technology acceptance and use is central to human-computer interaction research. Although technology acceptance models and user experience models differ in objectives, they share many potential intersections. Technology acceptance research focuses on structured prediction and assessment, while user experience research concentrates on interpreting design impacts and new frameworks. Integrating user experience to assess older adults’ acceptance of technology products and systems is crucial (Codfrey et al. 2022 ; Wang et al. 2019 ), particularly for older users, where specific product designs should emphasize practicality and usability (Fisk et al. 2020 ). Researchers need to explore innovative age-appropriate design methods to enhance older adults’ usage experience. This includes studying older users’ actual usage preferences and behaviors, optimizing user interfaces, and interaction designs. Integrating feedback from older adults to tailor products to their needs can further promote their acceptance and continued use of technology products.
Conclusions
This study conducted a systematic review of the literature on older adults’ technology acceptance over the past decade through bibliometric analysis, focusing on the distribution power, research power, knowledge base and theme progress, research hotspots, evolutionary trends, and quality distribution. Using a combination of quantitative and qualitative methods, this study has reached the following conclusions:
Technology acceptance among older adults has become a hot topic in the international academic community, involving the integration of knowledge across multiple disciplines, including Medical Informatics, Health Care Sciences Services, and Ergonomics. In terms of journals, “PSYCHOLOGY, EDUCATION, HEALTH” represents a leading field, with key publications including Computers in Human Behavior , Journal of Medical Internet Research , and International Journal of Human-Computer Interaction . These journals possess significant academic authority and extensive influence in the field.
Research on technology acceptance among older adults is particularly active in developed countries, with China and USA publishing significantly more than other nations. The Netherlands leads in high average citation rates, indicating the depth and impact of its research. Meanwhile, the UK stands out in terms of international collaboration. At the institutional level, City University of Hong Kong and The University of Hong Kong in China are in leading positions. Tilburg University in the Netherlands demonstrates exceptional research quality through its high average citation count. At the author level, Chen from China has the highest number of publications, while Peek from the Netherlands has the highest average citation count.
Co-citation analysis of references indicates that the knowledge base in this field is divided into three main categories: theoretical model deepening, emerging technology applications, and research methods and evaluation. Seminal literature focuses on four areas: specific technology use by older adults, expansion of theoretical models of technology acceptance, information technology adoption behavior, and research perspectives. Research themes have evolved from initial theoretical deepening and analysis of influencing factors to empirical studies on individual factors and emerging technologies.
Keyword analysis indicates that TAM and UTAUT are the most frequently occurring terms, while “assistive technology” and “virtual reality” are focal points with high frequency and centrality. Keyword clustering analysis reveals that research hotspots are concentrated on the influencing factors of technology adoption, human-robot interaction experiences, mobile health management, and technology for aging in place. Time-zone evolution mapping and burst keyword analysis have revealed the research evolution from preliminary exploration of influencing factors, to enhancements in quality of life and health management, and onto advanced technology applications and deepening of theoretical models. Furthermore, analysis of research quality distribution indicates that Usage Experience and Assisted Living Technology have become core topics, while Smart Devices, Theoretical Models, and Mobile Health Applications point towards future research directions.
Through this study, we have systematically reviewed the dynamics, core issues, and evolutionary trends in the field of older adults’ technology acceptance, constructing a comprehensive Knowledge Mapping of the domain and presenting a clear framework of existing research. This not only lays the foundation for subsequent theoretical discussions and innovative applications in the field but also provides an important reference for relevant scholars.
Limitations
To our knowledge, this is the first bibliometric analysis concerning technology acceptance among older adults, and we adhered strictly to bibliometric standards throughout our research. However, this study relies on the Web of Science Core Collection, and while its authority and breadth are widely recognized, this choice may have missed relevant literature published in other significant databases such as PubMed, Scopus, and Google Scholar, potentially overlooking some critical academic contributions. Moreover, given that our analysis was confined to literature in English, it may not reflect studies published in other languages, somewhat limiting the global representativeness of our data sample.
It is noteworthy that with the rapid development of AI technology, its increasingly widespread application in elderly care services is significantly transforming traditional care models. AI is profoundly altering the lifestyles of the elderly, from health monitoring and smart diagnostics to intelligent home systems and personalized care, significantly enhancing their quality of life and health care standards. The potential for AI technology within the elderly population is immense, and research in this area is rapidly expanding. However, due to the restrictive nature of the search terms used in this study, it did not fully cover research in this critical area, particularly in addressing key issues such as trust, privacy, and ethics.
Consequently, future research should not only expand data sources, incorporating multilingual and multidatabase literature, but also particularly focus on exploring older adults’ acceptance of AI technology and its applications, in order to construct a more comprehensive academic landscape of older adults’ technology acceptance, thereby enriching and extending the knowledge system and academic trends in this field.
Data availability
The datasets analyzed during the current study are available in the Dataverse repository: https://doi.org/10.7910/DVN/6K0GJH .
Abdi S, de Witte L, Hawley M (2020) Emerging technologies with potential care and support applications for older people: review of gray literature. JMIR Aging 3(2):e17286. https://doi.org/10.2196/17286
Article PubMed PubMed Central Google Scholar
Achuthan K, Nair VK, Kowalski R, Ramanathan S, Raman R (2023) Cyberbullying research—Alignment to sustainable development and impact of COVID-19: Bibliometrics and science mapping analysis. Comput Human Behav 140:107566. https://doi.org/10.1016/j.chb.2022.107566
Article Google Scholar
Ahmad A, Mozelius P (2022) Human-Computer Interaction for Older Adults: a Literature Review on Technology Acceptance of eHealth Systems. J Eng Res Sci 1(4):119–126. https://doi.org/10.55708/js0104014
Ale Ebrahim N, Salehi H, Embi MA, Habibi F, Gholizadeh H, Motahar SM (2014) Visibility and citation impact. Int Educ Stud 7(4):120–125. https://doi.org/10.5539/ies.v7n4p120
Amin MS, Johnson VL, Prybutok V, Koh CE (2024) An investigation into factors affecting the willingness to disclose personal health information when using AI-enabled caregiver robots. Ind Manag Data Syst 124(4):1677–1699. https://doi.org/10.1108/IMDS-09-2023-0608
Baer NR, Vietzke J, Schenk L (2022) Middle-aged and older adults’ acceptance of mobile nutrition and fitness apps: a systematic mixed studies review. PLoS One 17(12):e0278879. https://doi.org/10.1371/journal.pone.0278879
Barnard Y, Bradley MD, Hodgson F, Lloyd AD (2013) Learning to use new technologies by older adults: Perceived difficulties, experimentation behaviour and usability. Comput Human Behav 29(4):1715–1724. https://doi.org/10.1016/j.chb.2013.02.006
Berkowsky RW, Sharit J, Czaja SJ (2017) Factors predicting decisions about technology adoption among older adults. Innov Aging 3(1):igy002. https://doi.org/10.1093/geroni/igy002
Braun MT (2013) Obstacles to social networking website use among older adults. Comput Human Behav 29(3):673–680. https://doi.org/10.1016/j.chb.2012.12.004
Article MathSciNet Google Scholar
Campo-Prieto P, Rodríguez-Fuentes G, Cancela-Carral JM (2021) Immersive virtual reality exergame promotes the practice of physical activity in older people: An opportunity during COVID-19. Multimodal Technol Interact 5(9):52. https://doi.org/10.3390/mti5090052
Chen C (2006) CiteSpace II: Detecting and visualizing emerging trends and transient patterns in scientific literature. J Am Soc Inf Sci Technol 57(3):359–377. https://doi.org/10.1002/asi.20317
Chen C, Dubin R, Kim MC (2014) Emerging trends and new developments in regenerative medicine: a scientometric update (2000–2014). Expert Opin Biol Ther 14(9):1295–1317. https://doi.org/10.1517/14712598.2014.920813
Article PubMed Google Scholar
Chen C, Leydesdorff L (2014) Patterns of connections and movements in dual‐map overlays: A new method of publication portfolio analysis. J Assoc Inf Sci Technol 65(2):334–351. https://doi.org/10.1002/asi.22968
Chen J, Wang C, Tang Y (2022) Knowledge mapping of volunteer motivation: A bibliometric analysis and cross-cultural comparative study. Front Psychol 13:883150. https://doi.org/10.3389/fpsyg.2022.883150
Chen JY, Liu YD, Dai J, Wang CL (2023) Development and status of moral education research: Visual analysis based on knowledge graph. Front Psychol 13:1079955. https://doi.org/10.3389/fpsyg.2022.1079955
Chen K, Chan AH (2011) A review of technology acceptance by older adults. Gerontechnology 10(1):1–12. https://doi.org/10.4017/gt.2011.10.01.006.00
Chen K, Chan AH (2014) Gerontechnology acceptance by elderly Hong Kong Chinese: a senior technology acceptance model (STAM). Ergonomics 57(5):635–652. https://doi.org/10.1080/00140139.2014.895855
Chen K, Zhang Y, Fu X (2019) International research collaboration: An emerging domain of innovation studies? Res Policy 48(1):149–168. https://doi.org/10.1016/j.respol.2018.08.005
Chen X, Hu Z, Wang C (2024) Empowering education development through AIGC: A systematic literature review. Educ Inf Technol 1–53. https://doi.org/10.1007/s10639-024-12549-7
Chen Y, Chen CM, Liu ZY, Hu ZG, Wang XW (2015) The methodology function of CiteSpace mapping knowledge domains. Stud Sci Sci 33(2):242–253. https://doi.org/10.16192/j.cnki.1003-2053.2015.02.009
Codfrey GS, Baharum A, Zain NHM, Omar M, Deris FD (2022) User Experience in Product Design and Development: Perspectives and Strategies. Math Stat Eng Appl 71(2):257–262. https://doi.org/10.17762/msea.v71i2.83
Dai J, Zhang X, Wang CL (2024) A meta-analysis of learners’ continuance intention toward online education platforms. Educ Inf Technol 1–36. https://doi.org/10.1007/s10639-024-12654-7
Davis FD (1989) Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q 13(3):319–340. https://doi.org/10.2307/249008
Delmastro F, Dolciotti C, Palumbo F, Magrini M, Di Martino F, La Rosa D, Barcaro U (2018) Long-term care: how to improve the quality of life with mobile and e-health services. In 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), pp. 12–19. IEEE. https://doi.org/10.1109/WiMOB.2018.8589157
Dupuis K, Tsotsos LE (2018) Technology for remote health monitoring in an older population: a role for mobile devices. Multimodal Technol Interact 2(3):43. https://doi.org/10.3390/mti2030043
Ferguson C, Hickman LD, Turkmani S, Breen P, Gargiulo G, Inglis SC (2021) Wearables only work on patients that wear them”: Barriers and facilitators to the adoption of wearable cardiac monitoring technologies. Cardiovasc Digit Health J 2(2):137–147. https://doi.org/10.1016/j.cvdhj.2021.02.001
Fisk AD, Czaja SJ, Rogers WA, Charness N, Sharit J (2020) Designing for older adults: Principles and creative human factors approaches. CRC Press. https://doi.org/10.1201/9781420080681
Friesen S, Brémault-Phillips S, Rudrum L, Rogers LG (2016) Environmental design that supports healthy aging: Evaluating a new supportive living facility. J Hous Elderly 30(1):18–34. https://doi.org/10.1080/02763893.2015.1129380
Garcia Reyes EP, Kelly R, Buchanan G, Waycott J (2023) Understanding Older Adults’ Experiences With Technologies for Health Self-management: Interview Study. JMIR Aging 6:e43197. https://doi.org/10.2196/43197
Geng Z, Wang J, Liu J, Miao J (2024) Bibliometric analysis of the development, current status, and trends in adult degenerative scoliosis research: A systematic review from 1998 to 2023. J Pain Res 17:153–169. https://doi.org/10.2147/JPR.S437575
González A, Ramírez MP, Viadel V (2012) Attitudes of the elderly toward information and communications technologies. Educ Gerontol 38(9):585–594. https://doi.org/10.1080/03601277.2011.595314
Guner H, Acarturk C (2020) The use and acceptance of ICT by senior citizens: a comparison of technology acceptance model (TAM) for elderly and young adults. Univ Access Inf Soc 19(2):311–330. https://doi.org/10.1007/s10209-018-0642-4
Halim I, Saptari A, Perumal PA, Abdullah Z, Abdullah S, Muhammad MN (2022) A Review on Usability and User Experience of Assistive Social Robots for Older Persons. Int J Integr Eng 14(6):102–124. https://penerbit.uthm.edu.my/ojs/index.php/ijie/article/view/8566
He Y, He Q, Liu Q (2022) Technology acceptance in socially assistive robots: Scoping review of models, measurement, and influencing factors. J Healthc Eng 2022(1):6334732. https://doi.org/10.1155/2022/6334732
Heerink M, Kröse B, Evers V, Wielinga B (2010) Assessing acceptance of assistive social agent technology by older adults: the almere model. Int J Soc Robot 2:361–375. https://doi.org/10.1007/s12369-010-0068-5
Ho A (2020) Are we ready for artificial intelligence health monitoring in elder care? BMC Geriatr 20(1):358. https://doi.org/10.1186/s12877-020-01764-9
Hoque R, Sorwar G (2017) Understanding factors influencing the adoption of mHealth by the elderly: An extension of the UTAUT model. Int J Med Inform 101:75–84. https://doi.org/10.1016/j.ijmedinf.2017.02.002
Hota PK, Subramanian B, Narayanamurthy G (2020) Mapping the intellectual structure of social entrepreneurship research: A citation/co-citation analysis. J Bus Ethics 166(1):89–114. https://doi.org/10.1007/s10551-019-04129-4
Huang R, Yan P, Yang X (2021) Knowledge map visualization of technology hotspots and development trends in China’s textile manufacturing industry. IET Collab Intell Manuf 3(3):243–251. https://doi.org/10.1049/cim2.12024
Article ADS Google Scholar
Jing Y, Wang C, Chen Y, Wang H, Yu T, Shadiev R (2023) Bibliometric mapping techniques in educational technology research: A systematic literature review. Educ Inf Technol 1–29. https://doi.org/10.1007/s10639-023-12178-6
Jing YH, Wang CL, Chen ZY, Shen SS, Shadiev R (2024a) A Bibliometric Analysis of Studies on Technology-Supported Learning Environments: Hotopics and Frontier Evolution. J Comput Assist Learn 1–16. https://doi.org/10.1111/jcal.12934
Jing YH, Wang HM, Chen XJ, Wang CL (2024b) What factors will affect the effectiveness of using ChatGPT to solve programming problems? A quasi-experimental study. Humanit Soc Sci Commun 11:319. https://doi.org/10.1057/s41599-024-02751-w
Kamrani P, Dorsch I, Stock WG (2021) Do researchers know what the h-index is? And how do they estimate its importance? Scientometrics 126(7):5489–5508. https://doi.org/10.1007/s11192-021-03968-1
Kim HS, Lee KH, Kim H, Kim JH (2014) Using mobile phones in healthcare management for the elderly. Maturitas 79(4):381–388. https://doi.org/10.1016/j.maturitas.2014.08.013
Article MathSciNet PubMed Google Scholar
Kleinberg J (2002) Bursty and hierarchical structure in streams. In Proceedings of the eighth ACM SIGKDD international conference on Knowledge discovery and data mining, pp. 91–101. https://doi.org/10.1145/775047.775061
Kruse C, Fohn J, Wilson N, Patlan EN, Zipp S, Mileski M (2020) Utilization barriers and medical outcomes commensurate with the use of telehealth among older adults: systematic review. JMIR Med Inform 8(8):e20359. https://doi.org/10.2196/20359
Kumar S, Lim WM, Pandey N, Christopher Westland J (2021) 20 years of electronic commerce research. Electron Commer Res 21:1–40. https://doi.org/10.1007/s10660-021-09464-1
Kwiek M (2021) What large-scale publication and citation data tell us about international research collaboration in Europe: Changing national patterns in global contexts. Stud High Educ 46(12):2629–2649. https://doi.org/10.1080/03075079.2020.1749254
Lee C, Coughlin JF (2015) PERSPECTIVE: Older adults’ adoption of technology: an integrated approach to identifying determinants and barriers. J Prod Innov Manag 32(5):747–759. https://doi.org/10.1111/jpim.12176
Lee CH, Wang C, Fan X, Li F, Chen CH (2023) Artificial intelligence-enabled digital transformation in elderly healthcare field: scoping review. Adv Eng Inform 55:101874. https://doi.org/10.1016/j.aei.2023.101874
Leydesdorff L, Rafols I (2012) Interactive overlays: A new method for generating global journal maps from Web-of-Science data. J Informetr 6(2):318–332. https://doi.org/10.1016/j.joi.2011.11.003
Li J, Ma Q, Chan AH, Man S (2019) Health monitoring through wearable technologies for older adults: Smart wearables acceptance model. Appl Ergon 75:162–169. https://doi.org/10.1016/j.apergo.2018.10.006
Article ADS PubMed Google Scholar
Li X, Zhou D (2020) Product design requirement information visualization approach for intelligent manufacturing services. China Mech Eng 31(07):871, http://www.cmemo.org.cn/EN/Y2020/V31/I07/871
Google Scholar
Lin Y, Yu Z (2024a) An integrated bibliometric analysis and systematic review modelling students’ technostress in higher education. Behav Inf Technol 1–25. https://doi.org/10.1080/0144929X.2024.2332458
Lin Y, Yu Z (2024b) A bibliometric analysis of artificial intelligence chatbots in educational contexts. Interact Technol Smart Educ 21(2):189–213. https://doi.org/10.1108/ITSE-12-2022-0165
Liu L, Duffy VG (2023) Exploring the future development of Artificial Intelligence (AI) applications in chatbots: a bibliometric analysis. Int J Soc Robot 15(5):703–716. https://doi.org/10.1007/s12369-022-00956-0
Liu R, Li X, Chu J (2022) Evolution of applied variables in the research on technology acceptance of the elderly. In: International Conference on Human-Computer Interaction, Cham: Springer International Publishing, pp 500–520. https://doi.org/10.1007/978-3-031-05581-23_5
Luijkx K, Peek S, Wouters E (2015) “Grandma, you should do it—It’s cool” Older Adults and the Role of Family Members in Their Acceptance of Technology. Int J Environ Res Public Health 12(12):15470–15485. https://doi.org/10.3390/ijerph121214999
Lussier M, Lavoie M, Giroux S, Consel C, Guay M, Macoir J, Bier N (2018) Early detection of mild cognitive impairment with in-home monitoring sensor technologies using functional measures: a systematic review. IEEE J Biomed Health Inform 23(2):838–847. https://doi.org/10.1109/JBHI.2018.2834317
López-Robles JR, Otegi-Olaso JR, Porto Gomez I, Gamboa-Rosales NK, Gamboa-Rosales H, Robles-Berumen H (2018) Bibliometric network analysis to identify the intellectual structure and evolution of the big data research field. In: International Conference on Intelligent Data Engineering and Automated Learning, Cham: Springer International Publishing, pp 113–120. https://doi.org/10.1007/978-3-030-03496-2_13
Ma Q, Chan AH, Chen K (2016) Personal and other factors affecting acceptance of smartphone technology by older Chinese adults. Appl Ergon 54:62–71. https://doi.org/10.1016/j.apergo.2015.11.015
Ma Q, Chan AHS, Teh PL (2021) Insights into Older Adults’ Technology Acceptance through Meta-Analysis. Int J Hum-Comput Interact 37(11):1049–1062. https://doi.org/10.1080/10447318.2020.1865005
Macedo IM (2017) Predicting the acceptance and use of information and communication technology by older adults: An empirical examination of the revised UTAUT2. Comput Human Behav 75:935–948. https://doi.org/10.1016/j.chb.2017.06.013
Maidhof C, Offermann J, Ziefle M (2023) Eyes on privacy: acceptance of video-based AAL impacted by activities being filmed. Front Public Health 11:1186944. https://doi.org/10.3389/fpubh.2023.1186944
Majumder S, Aghayi E, Noferesti M, Memarzadeh-Tehran H, Mondal T, Pang Z, Deen MJ (2017) Smart homes for elderly healthcare—Recent advances and research challenges. Sensors 17(11):2496. https://doi.org/10.3390/s17112496
Article ADS PubMed PubMed Central Google Scholar
Mhlanga D (2023) Artificial Intelligence in elderly care: Navigating ethical and responsible AI adoption for seniors. Available at SSRN 4675564. 4675564 min) Identifying citation patterns of scientific breakthroughs: A perspective of dynamic citation process. Inf Process Manag 58(1):102428. https://doi.org/10.1016/j.ipm.2020.102428
Mitzner TL, Boron JB, Fausset CB, Adams AE, Charness N, Czaja SJ, Sharit J (2010) Older adults talk technology: Technology usage and attitudes. Comput Human Behav 26(6):1710–1721. https://doi.org/10.1016/j.chb.2010.06.020
Mitzner TL, Savla J, Boot WR, Sharit J, Charness N, Czaja SJ, Rogers WA (2019) Technology adoption by older adults: Findings from the PRISM trial. Gerontologist 59(1):34–44. https://doi.org/10.1093/geront/gny113
Mongeon P, Paul-Hus A (2016) The journal coverage of Web of Science and Scopus: a comparative analysis. Scientometrics 106:213–228. https://doi.org/10.1007/s11192-015-1765-5
Mostaghel R (2016) Innovation and technology for the elderly: Systematic literature review. J Bus Res 69(11):4896–4900. https://doi.org/10.1016/j.jbusres.2016.04.049
Mujirishvili T, Maidhof C, Florez-Revuelta F, Ziefle M, Richart-Martinez M, Cabrero-García J (2023) Acceptance and privacy perceptions toward video-based active and assisted living technologies: Scoping review. J Med Internet Res 25:e45297. https://doi.org/10.2196/45297
Naseri RNN, Azis SN, Abas N (2023) A Review of Technology Acceptance and Adoption Models in Consumer Study. FIRM J Manage Stud 8(2):188–199. https://doi.org/10.33021/firm.v8i2.4536
Nguyen UP, Hallinger P (2020) Assessing the distinctive contributions of Simulation & Gaming to the literature, 1970–2019: A bibliometric review. Simul Gaming 51(6):744–769. https://doi.org/10.1177/1046878120941569
Olmedo-Aguirre JO, Reyes-Campos J, Alor-Hernández G, Machorro-Cano I, Rodríguez-Mazahua L, Sánchez-Cervantes JL (2022) Remote healthcare for elderly people using wearables: A review. Biosensors 12(2):73. https://doi.org/10.3390/bios12020073
Pan S, Jordan-Marsh M (2010) Internet use intention and adoption among Chinese older adults: From the expanded technology acceptance model perspective. Comput Human Behav 26(5):1111–1119. https://doi.org/10.1016/j.chb.2010.03.015
Pan X, Yan E, Cui M, Hua W (2018) Examining the usage, citation, and diffusion patterns of bibliometric map software: A comparative study of three tools. J Informetr 12(2):481–493. https://doi.org/10.1016/j.joi.2018.03.005
Park JS, Kim NR, Han EJ (2018) Analysis of trends in science and technology using keyword network analysis. J Korea Ind Inf Syst Res 23(2):63–73. https://doi.org/10.9723/jksiis.2018.23.2.063
Peek ST, Luijkx KG, Rijnaard MD, Nieboer ME, Van Der Voort CS, Aarts S, Wouters EJ (2016) Older adults’ reasons for using technology while aging in place. Gerontology 62(2):226–237. https://doi.org/10.1159/000430949
Peek ST, Luijkx KG, Vrijhoef HJ, Nieboer ME, Aarts S, van der Voort CS, Wouters EJ (2017) Origins and consequences of technology acquirement by independent-living seniors: Towards an integrative model. BMC Geriatr 17:1–18. https://doi.org/10.1186/s12877-017-0582-5
Peek ST, Wouters EJ, Van Hoof J, Luijkx KG, Boeije HR, Vrijhoef HJ (2014) Factors influencing acceptance of technology for aging in place: a systematic review. Int J Med Inform 83(4):235–248. https://doi.org/10.1016/j.ijmedinf.2014.01.004
Peek STM, Luijkx KG, Vrijhoef HJM, Nieboer ME, Aarts S, Van Der Voort CS, Wouters EJM (2019) Understanding changes and stability in the long-term use of technologies by seniors who are aging in place: a dynamical framework. BMC Geriatr 19:1–13. https://doi.org/10.1186/s12877-019-1241-9
Perez AJ, Siddiqui F, Zeadally S, Lane D (2023) A review of IoT systems to enable independence for the elderly and disabled individuals. Internet Things 21:100653. https://doi.org/10.1016/j.iot.2022.100653
Piau A, Wild K, Mattek N, Kaye J (2019) Current state of digital biomarker technologies for real-life, home-based monitoring of cognitive function for mild cognitive impairment to mild Alzheimer disease and implications for clinical care: systematic review. J Med Internet Res 21(8):e12785. https://doi.org/10.2196/12785
Pirzada P, Wilde A, Doherty GH, Harris-Birtill D (2022) Ethics and acceptance of smart homes for older adults. Inform Health Soc Care 47(1):10–37. https://doi.org/10.1080/17538157.2021.1923500
Pranckutė R (2021) Web of Science (WoS) and Scopus: The titans of bibliographic information in today’s academic world. Publications 9(1):12. https://doi.org/10.3390/publications9010012
Qian K, Zhang Z, Yamamoto Y, Schuller BW (2021) Artificial intelligence internet of things for the elderly: From assisted living to health-care monitoring. IEEE Signal Process Mag 38(4):78–88. https://doi.org/10.1109/MSP.2021.3057298
Redner S (1998) How popular is your paper? An empirical study of the citation distribution. Eur Phys J B-Condens Matter Complex Syst 4(2):131–134. https://doi.org/10.1007/s100510050359
Sayago S (ed.) (2019) Perspectives on human-computer interaction research with older people. Switzerland: Springer International Publishing. https://doi.org/10.1007/978-3-030-06076-3
Schomakers EM, Ziefle M (2023) Privacy vs. security: trade-offs in the acceptance of smart technologies for aging-in-place. Int J Hum Comput Interact 39(5):1043–1058. https://doi.org/10.1080/10447318.2022.2078463
Schroeder T, Dodds L, Georgiou A, Gewald H, Siette J (2023) Older adults and new technology: Mapping review of the factors associated with older adults’ intention to adopt digital technologies. JMIR Aging 6(1):e44564. https://doi.org/10.2196/44564
Seibert K, Domhoff D, Bruch D, Schulte-Althoff M, Fürstenau D, Biessmann F, Wolf-Ostermann K (2021) Application scenarios for artificial intelligence in nursing care: rapid review. J Med Internet Res 23(11):e26522. https://doi.org/10.2196/26522
Seuwou P, Banissi E, Ubakanma G (2016) User acceptance of information technology: A critical review of technology acceptance models and the decision to invest in Information Security. In: Global Security, Safety and Sustainability-The Security Challenges of the Connected World: 11th International Conference, ICGS3 2017, London, UK, January 18-20, 2017, Proceedings 11:230-251. Springer International Publishing. https://doi.org/10.1007/978-3-319-51064-4_19
Shiau WL, Wang X, Zheng F (2023) What are the trend and core knowledge of information security? A citation and co-citation analysis. Inf Manag 60(3):103774. https://doi.org/10.1016/j.im.2023.103774
Sinha S, Verma A, Tiwari P (2021) Technology: Saving and enriching life during COVID-19. Front Psychol 12:647681. https://doi.org/10.3389/fpsyg.2021.647681
Soar J (2010) The potential of information and communication technologies to support ageing and independent living. Ann Telecommun 65:479–483. https://doi.org/10.1007/s12243-010-0167-1
Strotmann A, Zhao D (2012) Author name disambiguation: What difference does it make in author‐based citation analysis? J Am Soc Inf Sci Technol 63(9):1820–1833. https://doi.org/10.1002/asi.22695
Talukder MS, Sorwar G, Bao Y, Ahmed JU, Palash MAS (2020) Predicting antecedents of wearable healthcare technology acceptance by elderly: A combined SEM-Neural Network approach. Technol Forecast Soc Change 150:119793. https://doi.org/10.1016/j.techfore.2019.119793
Taskin Z, Al U (2019) Natural language processing applications in library and information science. Online Inf Rev 43(4):676–690. https://doi.org/10.1108/oir-07-2018-0217
Touqeer H, Zaman S, Amin R, Hussain M, Al-Turjman F, Bilal M (2021) Smart home security: challenges, issues and solutions at different IoT layers. J Supercomput 77(12):14053–14089. https://doi.org/10.1007/s11227-021-03825-1
United Nations Department of Economic and Social Affairs (2023) World population ageing 2023: Highlights. https://www.un.org/zh/193220
Valk CAL, Lu Y, Randriambelonoro M, Jessen J (2018) Designing for technology acceptance of wearable and mobile technologies for senior citizen users. In: 21st DMI: Academic Design Management Conference (ADMC 2018), Design Management Institute, pp 1361–1373. https://www.dmi.org/page/ADMC2018
Van Eck N, Waltman L (2010) Software survey: VOSviewer, a computer program for bibliometric mapping. Scientometrics 84(2):523–538. https://doi.org/10.1007/s11192-009-0146-3
Vancea M, Solé-Casals J (2016) Population aging in the European Information Societies: towards a comprehensive research agenda in eHealth innovations for elderly. Aging Dis 7(4):526. https://doi.org/10.14336/AD.2015.1214
Venkatesh V, Morris MG, Davis GB, Davis FD (2003) User acceptance of information technology: Toward a unified view. MIS Q 27(3):425–478. https://doi.org/10.2307/30036540
Wagner N, Hassanein K, Head M (2010) Computer use by older adults: A multi-disciplinary review. Comput Human Behav 26(5):870–882. https://doi.org/10.1016/j.chb.2010.03.029
Wahlroos N, Narsakka N, Stolt M, Suhonen R (2023) Physical environment maintaining independence and self-management of older people in long-term care settings—An integrative literature review. J Aging Environ 37(3):295–313. https://doi.org/10.1080/26892618.2022.2092927
Wang CL, Chen XJ, Yu T, Liu YD, Jing YH (2024a) Education reform and change driven by digital technology: a bibliometric study from a global perspective. Humanit Soc Sci Commun 11(1):1–17. https://doi.org/10.1057/s41599-024-02717-y
Wang CL, Dai J, Zhu KK, Yu T, Gu XQ (2023a) Understanding the Continuance Intention of College Students Toward New E-learning Spaces Based on an Integrated Model of the TAM and TTF. Int J Hum-comput Int 1–14. https://doi.org/10.1080/10447318.2023.2291609
Wang CL, Wang HM, Li YY, Dai J, Gu XQ, Yu T (2024b) Factors Influencing University Students’ Behavioral Intention to Use Generative Artificial Intelligence: Integrating the Theory of Planned Behavior and AI Literacy. Int J Hum-comput Int 1–23. https://doi.org/10.1080/10447318.2024.2383033
Wang J, Zhao W, Zhang Z, Liu X, Xie T, Wang L, Zhang Y (2024c) A journey of challenges and victories: a bibliometric worldview of nanomedicine since the 21st century. Adv Mater 36(15):2308915. https://doi.org/10.1002/adma.202308915
Wang J, Chen Y, Huo S, Mai L, Jia F (2023b) Research hotspots and trends of social robot interaction design: A bibliometric analysis. Sensors 23(23):9369. https://doi.org/10.3390/s23239369
Wang KH, Chen G, Chen HG (2017) A model of technology adoption by older adults. Soc Behav Personal 45(4):563–572. https://doi.org/10.2224/sbp.5778
Wang S, Bolling K, Mao W, Reichstadt J, Jeste D, Kim HC, Nebeker C (2019) Technology to Support Aging in Place: Older Adults’ Perspectives. Healthcare 7(2):60. https://doi.org/10.3390/healthcare7020060
Wang Z, Liu D, Sun Y, Pang X, Sun P, Lin F, Ren K (2022) A survey on IoT-enabled home automation systems: Attacks and defenses. IEEE Commun Surv Tutor 24(4):2292–2328. https://doi.org/10.1109/COMST.2022.3201557
Wilkowska W, Offermann J, Spinsante S, Poli A, Ziefle M (2022) Analyzing technology acceptance and perception of privacy in ambient assisted living for using sensor-based technologies. PloS One 17(7):e0269642. https://doi.org/10.1371/journal.pone.0269642
Wilson J, Heinsch M, Betts D, Booth D, Kay-Lambkin F (2021) Barriers and facilitators to the use of e-health by older adults: a scoping review. BMC Public Health 21:1–12. https://doi.org/10.1186/s12889-021-11623-w
Xia YQ, Deng YL, Tao XY, Zhang SN, Wang CL (2024) Digital art exhibitions and psychological well-being in Chinese Generation Z: An analysis based on the S-O-R framework. Humanit Soc Sci Commun 11:266. https://doi.org/10.1057/s41599-024-02718-x
Xie H, Zhang Y, Duan K (2020) Evolutionary overview of urban expansion based on bibliometric analysis in Web of Science from 1990 to 2019. Habitat Int 95:102100. https://doi.org/10.1016/j.habitatint.2019.10210
Xu Z, Ge Z, Wang X, Skare M (2021) Bibliometric analysis of technology adoption literature published from 1997 to 2020. Technol Forecast Soc Change 170:120896. https://doi.org/10.1016/j.techfore.2021.120896
Yap YY, Tan SH, Choon SW (2022) Elderly’s intention to use technologies: a systematic literature review. Heliyon 8(1). https://doi.org/10.1016/j.heliyon.2022.e08765
Yu T, Dai J, Wang CL (2023) Adoption of blended learning: Chinese university students’ perspectives. Humanit Soc Sci Commun 10:390. https://doi.org/10.1057/s41599-023-01904-7
Yusif S, Soar J, Hafeez-Baig A (2016) Older people, assistive technologies, and the barriers to adoption: A systematic review. Int J Med Inform 94:112–116. https://doi.org/10.1016/j.ijmedinf.2016.07.004
Zhang J, Zhu L (2022) Citation recommendation using semantic representation of cited papers’ relations and content. Expert Syst Appl 187:115826. https://doi.org/10.1016/j.eswa.2021.115826
Zhao Y, Li J (2024) Opportunities and challenges of integrating artificial intelligence in China’s elderly care services. Sci Rep 14(1):9254. https://doi.org/10.1038/s41598-024-60067-w
Article ADS MathSciNet PubMed PubMed Central Google Scholar
Download references
Acknowledgements
This research was supported by the Social Science Foundation of Shaanxi Province in China (Grant No. 2023J014).
Author information
Authors and affiliations.
School of Art and Design, Shaanxi University of Science and Technology, Xi’an, China
Xianru Shang, Zijian Liu, Chen Gong, Zhigang Hu & Yuexuan Wu
Department of Education Information Technology, Faculty of Education, East China Normal University, Shanghai, China
Chengliang Wang
You can also search for this author in PubMed Google Scholar
Contributions
Conceptualization, XS, YW, CW; methodology, XS, ZL, CG, CW; software, XS, CG, YW; writing-original draft preparation, XS, CW; writing-review and editing, XS, CG, ZH, CW; supervision, ZL, ZH, CW; project administration, ZL, ZH, CW; funding acquisition, XS, CG. All authors read and approved the final manuscript. All authors have read and approved the re-submission of the manuscript.
Corresponding author
Correspondence to Chengliang Wang .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Ethical approval
Ethical approval was not required as the study did not involve human participants.
Informed consent
Informed consent was not required as the study did not involve human participants.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Cite this article.
Shang, X., Liu, Z., Gong, C. et al. Knowledge mapping and evolution of research on older adults’ technology acceptance: a bibliometric study from 2013 to 2023. Humanit Soc Sci Commun 11 , 1115 (2024). https://doi.org/10.1057/s41599-024-03658-2
Download citation
Received : 20 June 2024
Accepted : 21 August 2024
Published : 31 August 2024
DOI : https://doi.org/10.1057/s41599-024-03658-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
- Northern Illinois University
- Thursday, September 12
2024 Lincoln Lecture - A discussion with award-winning author Clint Smith
Thursday, September 12, 2024 7:30 PM
- Share 2024 Lincoln Lecture - A discussion with award-winning author Clint Smith on Facebook
- Share 2024 Lincoln Lecture - A discussion with award-winning author Clint Smith on Twitter
- Share 2024 Lincoln Lecture - A discussion with award-winning author Clint Smith on LinkedIn

About this Event
595 College Ave, DeKalb, IL 60115
This conversation, moderated by Christina Abreu, Director of the Center for Latino and Latin American Studies, draws on Smith’s 2021 book , How the Word Is Passed: A Reckoning with the History of Slavery Across America, which was a #1 New York Times bestseller, winner of the National Book Critics Circle Award for Nonfiction and selected by the New York Times as one of the 10 best books of 2021.
Smith’s bestselling books include How the Word Is Passed , which Publishers Weekly called “an essential consideration of how America’s past informs its present.” It has won numerous awards, including the National Book Critics Circle Award for Nonfiction, and was named one of the best books of the year by TIME , The New York Times , The Economist and The Washington Post .
His latest book, Above Ground , was named to TIME magazine’s 100 Must-Read Books and NPR ‘s Books We Love. Smith’s first book, Counting Descent , won the 2017 Literary Award for Best Poetry Book from the Black Caucus of the American Library Association and was a finalist for an NAACP Image Award. In his forthcoming book, Just Beneath the Soil , he will explore the little-known stories behind World War II sites and discuss how they shape our collective memory of the war.
His essays, poems, and scholarly writing have been published in The New Yorker, The New York Times Magazine , The New Republic, Poetry Magazine, The Paris Review, the Harvard Educational Review and elsewhere. He is a staff writer at The Atlantic .
The W. Bruce Lincoln Endowed Lecture Series brings to campus distinguished scholars who address topics of interest to both the academic community and the general public. The lectures engage key issues and are often interdisciplinary, in the spirit of Professor Lincoln’s research, writing and teaching.
Event Details
Target Audience
Contact Name
Anne Hanley
Contact Email or Phone
Your browser does not support iframes.
See Who Is Interested

2 people are interested in this event
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
Research: How to Build Consensus Around a New Idea
- Devon Proudfoot
- Wayne Johnson

Strategies for overcoming the disagreements that can stymie innovation.
Previous research has found that new ideas are seen as risky and are often rejected. New research suggests that this rejection can be due to people’s lack of shared criteria or reference points when evaluating a potential innovation’s value. In a new paper, the authors find that the more novel the idea, the more people differ on their perception of its value. They also found that disagreement itself can make people view ideas as risky and make them less likely to support them, regardless of how novel the idea is. To help teams get on the same page when it comes to new ideas, they suggest gathering information about evaluator’s reference points and developing criteria that can lead to more focused discussions.
Picture yourself in a meeting where a new idea has just been pitched, representing a major departure from your company’s standard practices. The presenter is confident about moving forward, but their voice is quickly overtaken by a cacophony of opinions from firm opposition to enthusiastic support. How can you make sense of the noise? What weight do you give each of these opinions? And what does this disagreement say about the idea?
- DP Devon Proudfoot is an Associate Professor of Human Resource Studies at Cornell’s ILR School. She studies topics related to diversity and creativity at work.
- Wayne Johnson is a researcher at the Utah Eccles School of Business. He focuses on evaluations and decisions about new information, including persuasion regarding creative ideas and belief change.
Partner Center

IMAGES
VIDEO
COMMENTS
Introduction The Terrorism Research Initiative seeks to stimulate individual and collaborative research on terrorism and other forms of political violence that threatening human security. While some topics are 'fashionable" and obtain an extraordinary amount of attention (e.g. CBRN threats, radicalization, suicide terrorism, jihadist ...
40 Terrorism Research Paper Topics. Unfortunately, the theme of terrorism is now still very acute. The terroristic acts aren't history, they can happen in the centers of the peaceful cities of developed countries. No one is safe… but still it isn't the reason not to study terrorism and search ways to prevent it and, possibly, eliminate it ...
Researching of Morals of Terrorists. Terrorism attacks are a form of violence, and the moral implication is death in the form of revenge. Realism is a form of acceptance that everyone on the battlefield is a civilian with their families. The Structures, Motivations, and Qualities of Terrorist Groups.
These essay topic ideas and examples cover a wide range of issues related to terrorism, and can serve as a starting point for your research and writing. Whether you are interested in exploring the causes of terrorism, analyzing the impact of terrorist attacks on different populations, or evaluating the effectiveness of counterterrorism ...
For instance, government policies and characteristics (which ensue from the political. and institutional order) may also matter to terrorist activity. 2.4 Political transformation and instability ...
Terrorism Dissertation Topic Ideas. Published by Owen Ingram at January 5th, 2023 , Revised On May 21, 2024. Terrorism is a major global threat to public safety and security. It is an unlawful use of violence and intimidation to achieve political, ideological or religious goals. Terrorist attacks are always extremely devastating and have the ...
Terrorism as a Pressing Social Issue. Terrorism is a crime, the aim of which is a violation of public safety, which is expressed in encroachment on the life and health of citizens and infrastructure facilities. Modern Terrorism Regarding the Role of Media. Modern terrorism uses the media to report its threats and activities.
Response Paper(s) Students will be presented with a number of prompts and will choose one to write on. Undergraduates will do two small reseach papers. Graduate students will write a single long research paper. Papers must fully answer the prompt and provide a thoughtful response. Exams- 50%!! Exams will be based on the following components:
Critical Studies on Terrorism aims to create space for robust, innovative research on terrorism and political violence, and encourages fruitful intellectual engagement between critical and orthodox accounts of terrorism. In particular, the Editors are looking for empirical, theoretical and policy-oriented articles that recognise the inherently ...
This library resource provides authoritative periodical content addressing both historic and contemporary topics in the fields of war and terrorism. With more than 1.7 million articles, Gale OneFile: War and Terrorism gives researchers valuable insight into conflicts and their causes, impact, and perception on a global scale. Learn more ».
red the economic opportunities but also affected the infrastructure of Pakistan. Ali (2010) mentioned the worst impacts of terrorism on the domestic domain like an agricultural loss in Swat, economic deficiency with the increased budget deficit, low investments, milita. y spending, increased loans, and loss of domestic markets with negative expor.
Writing a terrorism research paper is easy in thoughts and tough on paper. Be very careful what you put where in the terrorism essay or research paper. Use strong arguments, supported by facts. One thing that will earn you whole marks or get your research an A, whatever the topic, is having strong and backed arguments.
The topic of terrorism is no stranger to difficulty, as not all students can find appropriate topics for essays. We understand how difficult it can be to find new and interesting ideas when other people have already explored the subject thoroughly in their essay papers. However, we've compiled a list of 10 popular research paper topics that ...
International Terrorism Research Paper Topics to Write About. Nowadays, acts of terrorism occur all over the world, spanning from the Middle East to Europe, Latin America, and literally every part of the globe. It's a day to day issue happening to innocent citizens of their states. Terrorism is different in its forms and affects different ...
sentence outline for your paper. The outline must include an abstract which indicates the topic focus of the paper to be examined. Then for each main body paragraph a thesis sentence and citations for the references that indicate the initial research for that point. Finally, a conclusion with 2-3 sentences of your initial findings. INSTRUCTIONS
Research Paper Topics On Terrorism: 15 Interesting Writing Ideas. If you are looking for an interesting writing idea for a research paper topic on terrorism consider the following: you can review current ethical implications associated with torture. You can explore personal freedoms and the use of terrorism. You can explore the limits between ...
️ Terrorism Essay Topics for High School Students. A Criminal Justice Approach to Suppressing Terrorism; A Research on Terrorism Before and After the September 11, 2001 Attacks Research; A Review of Greece's Effort to Thwart Terrorism
View sample Terrorism Research Paper. Browse other research paper examples and check the list of research paper topics for more inspiration. If you need a religion research paper written according to all the academic standards, you can always turn to our experienced writers for help. This is how your paper can get an A!
This sample terrorism research paper features: 7300 words (approx. 24 pages), an outline, and a bibliography with 57 sources. Browse other research paper exampl ... Since terrorism is a miltidisciplinary topic it depends on the interaction and collaboration of a number of disciplines. In the United States, most of the analyses on terrorism are ...
View our collection of terrorism essays. Find inspiration for topics, titles, outlines, & craft impactful terrorism papers. Read our terrorism papers today! Homework Help; Essay Examples; Writing Tools. ... Indian Council of Social Science Research. Haranand Publications. India, 2000. Essay Terrorism Is at This Point One of . Pages: 8 Words: 2444.
Conclusion. This research paper has illuminated several aspects of the form of political violence known as terrorism. The phenomenon differs from other forms of political violence. It has occurred within many different periods, regions, and cultures and has been executed under a variety of ideological auspices.
Research paper topics on terrorism to consider. The impact of 9/11 attacks on the Asians and browns living in New York and rest of United States Does any religion promote or encourage terrorism Why is there a biasness against a specific nation or religion for terrorism
Research Paper Topics on Math. If you're looking to explore the depth and applications of math, these research topics are both specific and engaging: Applications of fractal geometry in modeling natural phenomena. Mathematical approaches to solving complex optimization problems in logistics. Development of new algorithms for large-scale data ...
Policy Briefs Explore research-based overviews on vital policy topics. Working Papers Search IPR working papers for research insights. Grad RA Working Papers Read working papers by current and recent IPR graduate research assistants. Books Browse books and edited volumes by IPR faculty. Journal Articles Read the latest published articles by IPR ...
The present research paper aims to analyse the spatial patterns of literacy, employment, levels of socio-economic status of urban beggars, and the relationship between their rate of literacy and ...
The SEI Digital Library provides access to more than 6,000 documents from three decades of research into best practices in software engineering. These documents include technical reports, presentations, webcasts, podcasts and other materials searchable by user-supplied keywords and organized by topic, publication type, publication year, and author.
Research Paper Topics About Terrorism, Critically Discuss The Structure Conduct Performance Paradigm In A Short Essay, 2015 Ap English Synthesis Essay, Essay On Diwali In English Class 4, Popular Research Paper Writers Websites, Forensic Psychology Literature Review Examples, Garbage Problem Ielts Essay. Total orders: 7428.
Research method. In recent years, bibliometrics has become one of the crucial methods for analyzing literature reviews and is widely used in disciplinary and industrial intelligence analysis (Jing ...
This conversation, moderated by Christina Abreu, Director of the Center for Latino and Latin American Studies, draws on Smith's 2021 book, How the Word Is Passed: A Reckoning with the History of Slavery Across America, which was a #1 New York Times bestseller, winner of the National Book Critics Circle Award for Nonfiction and selected by the New York Times as one of the 10 best books of ...
New research suggests that this rejection can be due to people's lack of shared criteria or reference points when evaluating a potential innovation's value. In a new paper, the authors find ...